-
-
Notifications
You must be signed in to change notification settings - Fork 33
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
C_Login CKR_FUNCTION_NOT_SUPPORTED #57
Comments
|
Within fortify can you send us the log of whe you use the fortify app to generate a CSR on this card? |
|
I suppose I didn't provide enough context as to how I am using pkcs11js exactly.. This code lives inside an Electron Angular app. I am not directly using Fortify, only it's .dll to provide the layer for communication with smart cards. I haven't found much information online on how exactly you get to these libraries, so that's why I used Fortify's dll, as it's the most relevant in my use case. I would love to get some more insights in how exactly I should go about this. |
|
The error you are having suggests there is something your smart card isn’t supporting related to login. It is easier for us to troubleshoot this if you use Fortify, enable logging, perform the CSR generation, send us a log. |
|
Thank you for the suggestion. Will do that as soon as possible and report back to you. |
|
While starting Fortify, I am presented with the notice that the smart card is not supported and if I'd like to request support.
{
"cards": [{
"atr": "3B7D96000080318065B0830201F383009000",
"name": "Token name",
"driver": "B1B9E460251886FDB4207F3D1D243AB05A6AF3D6"
}],
"drivers": [{
"id": "B1B9E460251886FDB4207F3D1D243AB05A6AF3D6",
"name": "Driver name",
"file": {
"windows": "path/to/pkcs11.dll",
"osx": "path/to/pkcs11.dylib"
}
}]
}Smart card ATR parsing 3B7D96000080318065B0830201F383009000 It is the same token as in the following issue: PeculiarVentures/fortify#120 |
|
The card itself appears to be aGemalto IDClassic 340 Is that correct? Or is this some other card that’s been provisioned onto this card? What PKCS11 library do you use with this card? Where on your system do you find that PKCS11 library? Does this card have a certificate on it already and read only (most National ID cards) or is it blank that you can arbitrary things to? |
|
You can add your token to Fortify config file Example |
|
This suggests (https://doc.nexusgroup.com/display/PUB/Personal+Desktop+Client+overview) that the nexus client includes a mini driver and a PKCS#11. As per @microshine's comment if you can specify which one to use in the fortify config file it should work. Once you confirm we can add it to the global config. |
|
It seems maybe this smart card is related to Swedish BankID (www.bankid.com)? According to this I've asked a knowlegable friend for more information here : https://twitter.com/rmhrisk/status/1202905241177542656?s=20 |
|
The smart card is issued by Halcom (http://www.halcom.si/en/) a Slovenian provider of digital certification software/products. I am not aware of any connection between them and the Swedish BankID. As suggested, I found the library which Nexus Personal is using (personal64.dll) and am trying it out at the moment. I will shorty report if there is any more information available through it. |
|
Actually I may have found it; according to this it is personal.dll. If so I think the configuration you need to test would be: |
|
Please try the above configuration and see if it works. |
|
I have tested the library with pkcs11js and I have successfully logged in with the correct PIN. The token info is now populated and shows the correct manufacturer and serial number, which means this is the correct one to be used. I am now presented with the error CKR_GENERAL_ERROR at crypto_final:637 on line: Any ideas as to how to check what causes this? |
|
We will need the fortify log associated with that transaction. |
|
Do you mean generating a CSR? I don't know how I would do the signing process with Fortify or how it is connected with it in any way, as I am using pkcs11js inside an Angular Electron application. Please advise on how to get some more information out of the error, as that is all I get: Do you know of any tool I could use to check if the signing process works manually (Windows)? |
|
I am aware of the process for enabling and checking the log and I have checked it after the signing process but nothing is logged inside it. And how would Fortify know of any signing process outside the app itself? I need some more explanation on that. Note: I am using pkcs11js by itself, stand-alone inside an Electron app, not connected to Fortify in any way. |
Can you share a part of your source code where you are using It's interesting to see which mechanisms you are using for signing |
|
Here is the updated code from my initial issue comment: |
|
try to increase buffer for a signature object to 1024 |
Did so, no effect, the same error persists.. |
|
this is strange
|
|
@spanmatej Please try const { Crypto } = require("node-webcrypto-p11");
async function main() {
const crypto = new Crypto({
library: "personal64.dll",
slot: 1,
pin: "1234",
});
const alg = {
name: "RSASSA-PKCS1-v1_5",
hash: "SHA-256",
publicExponent: new Uint8Array([1, 0, 1]),
modulusLength: 2048,
}
const keys = await crypto.subtle.generateKey(alg, false, ["sign", "verify"])
const data = Buffer.from("some message to be signed");
const signature = await crypto.subtle.sign(alg, keys.privateKey, data);
const ok = await crypto.subtle.verify(alg, keys.publicKey, signature, data);
console.log("Signature:", ok);
}
main().catch((e) => console.error(e)); |
|
@microshine I'm sorry for the late response. Error still persists, even though now instead of pointing to crypto_final, it points to crypto_update. |
Can you, as requested earlier, add support for your smart card to fortify with the above details, use fortify to create a CSR, and send the log.
This may tell us something new. Alternatively maybe you can contact your middleware provider for examples of how to perform a working transaction with their middleware. Each P11 unfortunately behaves a little different, some more than others. This is made worse by the middleware returning awesome errors like GENERAL ERROR. Some offer additional logging that can be enabled to see what it was doing when the error was encountered which can help tease out why the middleware is not happy. |
|
@spanmatej What about |
|
I found some information about https://blog.goranrakic.com/uploads/pkcs11_putanje.pdf
https://doc.nexusgroup.com/display/PUB/Personal+Desktop+Client+user%27s+guide Nexus desktop client |
|
@microshine My previous comment is from using the node-webcrypto-p11 module. It also produces that error. Thank you for finding that! I will try enabling the logging and get back to you with more info. @rmhrisk I added the suggested data inside the config file, done the CSR generation and this is the log. |
|
@microshine The logging/diagnostics was actually already enabled and the log file was present. As there is no functional difference between node-webcrypto-p11 and pkcs11js, except for it adding an additional layer, I'm going forward with pkcs11js at this moment, so all logging is relevant to that code. I've checked the log and I can't find anything relevant myself, except for this message (logged after SignFinal starts): Would this mean that I would need to provide the PIN again for the signing process, even though the login was a success? Is there any case with such a procedure? |
|
Have you tried to use another hash mechanism? Try |
@microshine Unfortunately, the same thing happens. |
@spanmatej Please try to get |
|
|
@microshine I am not sure how to get the CKA_ALWAYS_AUTHENTICATE attribute exactly. I got it once before but I switched between graphene, node-webcrypto, pkcs11js so many times that I forgot and I'm lost..
I'd like to note that I messed up in my code at opening the session, instead of (suggested in documentation): Without knowing the value of CKA_ALWAYS_AUTHENTICATE, I went ahead and did as suggested, calling login immediately after SignInit with CKU_CONTEXT_SPECIFIC user: That causes: I'm sorry for the dumb questions at times.. I'm doing my best to get a deeper understanding of all this and it's a lot to take in. I really do appreciate all the help. |
|
I'll create a script. ~10 minutes |
|
You need update const pkcs11js = require("pkcs11js");
const lib = '/usr/local/Cellar/softhsm/2.5.0/lib/softhsm/libsofthsm2.so';
const pin = '12345';
const slotIndex = 0;
const pkcs11 = new pkcs11js.PKCS11();
pkcs11.load(lib);
pkcs11.C_Initialize();
const slots = pkcs11.C_GetSlotList(true);
const slot = slots[slotIndex];
const session = pkcs11.C_OpenSession(slot, pkcs11js.CKF_SERIAL_SESSION);
pkcs11.C_Login(session, pkcs11js.CKU_USER, pin); // GEMALTO UNSUPPORTED?
const publicKeyTemplate = [
{ type: pkcs11js.CKA_CLASS, value: pkcs11js.CKO_PUBLIC_KEY },
{ type: pkcs11js.CKA_TOKEN, value: false },
{ type: pkcs11js.CKA_LABEL, value: 'My RSA Public Key' },
{ type: pkcs11js.CKA_PUBLIC_EXPONENT, value: Buffer.from([1, 0, 1]) },
{ type: pkcs11js.CKA_MODULUS_BITS, value: 2048 },
{ type: pkcs11js.CKA_VERIFY, value: true }
];
const privateKeyTemplate = [
{ type: pkcs11js.CKA_CLASS, value: pkcs11js.CKO_PRIVATE_KEY },
{ type: pkcs11js.CKA_TOKEN, value: false },
{ type: pkcs11js.CKA_LABEL, value: 'My RSA Private Key' },
{ type: pkcs11js.CKA_SIGN, value: true },
];
const keys = pkcs11.C_GenerateKeyPair(session, { mechanism: pkcs11js.CKM_RSA_PKCS_KEY_PAIR_GEN }, publicKeyTemplate, privateKeyTemplate);
pkcs11.C_SignInit(session, { mechanism: pkcs11js.CKM_SHA256_RSA_PKCS }, keys.privateKey);
// Check private key attribute
const alwaysAuthenticate = pkcs11.C_GetAttributeValue(session, keys.privateKey, [{ type: pkcs11js.CKA_ALWAYS_AUTHENTICATE }])[0].value;
if (alwaysAuthenticate.length && alwaysAuthenticate[0]) {
pkcs11.C_Login(session, pkcs11js.CKU_CONTEXT_SPECIFIC, pin);
}
const pdfBinary = decodeFromBase64(bytesToSign); // data to sign
pkcs11.C_SignUpdate(session, new Buffer(pdfBinary));
const signature = pkcs11.C_SignFinal(session, new Buffer(256));
pkcs11.C_VerifyInit(session, { mechanism: pkcs11js.CKM_SHA256_RSA_PKCS }, keys.publicKey);
pkcs11.C_VerifyUpdate(session, new Buffer(pdfBinary));
const verify = pkcs11.C_VerifyFinal(session, signature);
// pkcs11.C_Logout(session); // GEMALTO UNSUPPORTED?
pkcs11.C_CloseSession(session); |
|
logged: |
|
Please comment this attr getting and call your app again. It must login to session with |
|
I mean to call |
const session = pkcs11.C_OpenSession(slot, pkcs11js.CKF_RW_SESSION | pkcs11js.CKF_SERIAL_SESSION); |
Changing to that gives |
|
Can we move our chat to Skype? Please contact me via email microshine@mail.ru |
|
The issue has been resolved. I will update this comment shortly and describe the solution. |
|
@spanmatej Can you elaborate on what solved your issue? |







I am trying to sign a PDF signature using a Gemalto USB Key Smart Card. I am able to find the slot, open session and generally access it, but I am not able to Login with PIN.
Usually you have to enter the PIN during the signing process, for example you select the certificate from the list in Adobe Reader, then choose to sign with it after which you are shown the window to enter the PIN.
C_Login & C_Logout both return CKR_FUNCTION_NOT_SUPPORTED.
Here is some info and the code.
Using pvpkcs11.dll as library (from Fortify app).
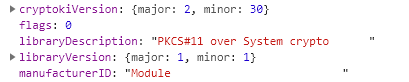
C_GetInfo
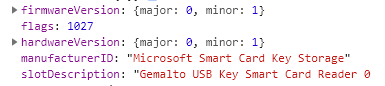
C_GetSlotInfo
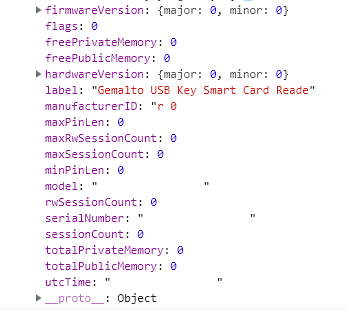
C_GetTokenInfo (seems to be lacking data)
While trying to login, I receive the following error:
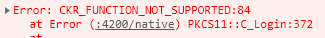
**pkcs11.C_Login(session, 1, 1234);**HOWEVER if I comment out the login, the rest of the signing process successfully completes and the verfication of the signature returns as true. Afterwards I attach this signature to an actual PDF document on the server side (C# .NET Core), where it shows as invalid.
The text was updated successfully, but these errors were encountered: