The way the Firewall works is quite simple. It creates a barrier between trustworthy and untrustworthy networks so your system can be safe from malicious packets.
IPTables can be used for personal computing or can also be applied to the entire network. Using IPTables, we will be defining a set of rules by which we can monitor, allow or block incoming or outgoing network packets.
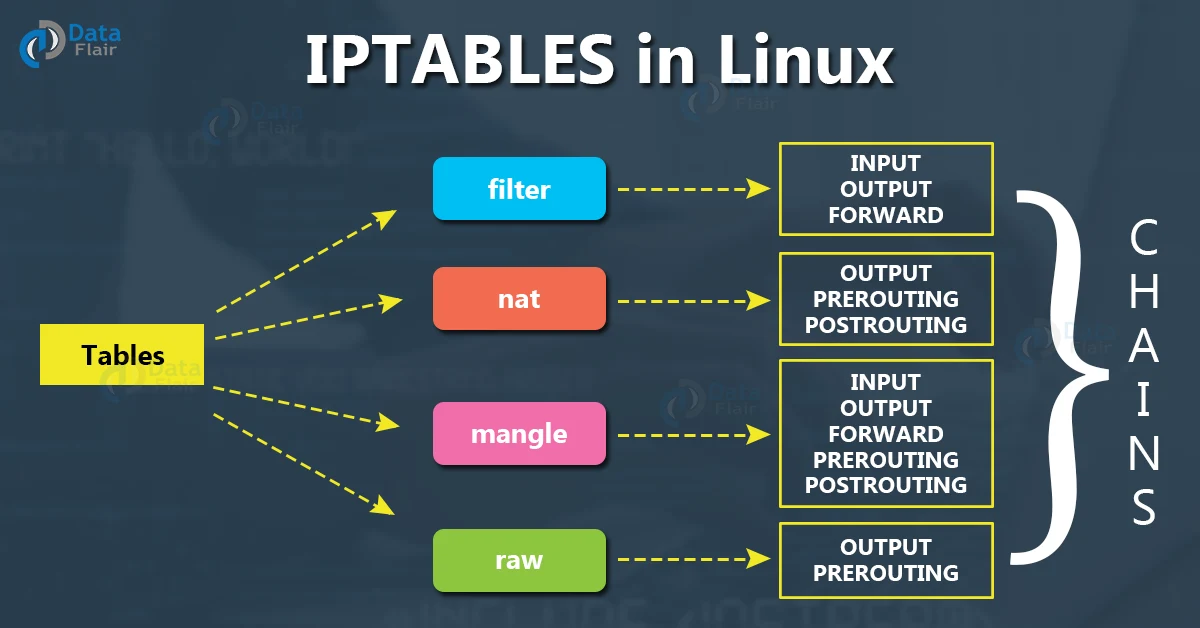
While discussing IPTables, we must understand 3 terms: Tables, Chains, and Rules.
Tables are the top-level structure in IPTables. There are 5 types of tables in IPTables and each has different rules applied. The tables are:
- Filter: This is the default table in IPTables. It is used to filter packets based on the rules defined.
- NAT: This table is used for Network Address Translation. It is used to translate the source or destination IP address of packets.
- Mangle: This table is used to alter the IP packets. For example, it can change the TTL value of the packet.
- Raw: This table is used to configure exemptions from connection tracking.
- Security: This table is used to configure SELinux security policies.
Chains are the second-level structure in IPTables. Chains are used to define the rules for packets. There are 5 types of chains in IPTables:
- PREROUTING: This chain is applied to any incoming packets before a routing decision is made regarding the final destination of the packet.
- INPUT: It is the point where the packet is received by the network stack.
- FORWARD: This chain is applied to packets that are being routed through the system.
- OUTPUT: The output chain is applied to packets generated by the system and going out of the system.
- POSTROUTING: This chain is applied to packets after they have been routed.
Rules are nothing but the set or individual commands by which users manipulate network traffic. Once each chain will come into action, the packet will be checked against defined rules.
Each rule has two components: Match and Target.
- Match: They are different conditions to define rules which can be matched by protocol, IP address, port, interface, header, etc.
- Target: It is the action to be taken if the packet matches the rule.
The format of IPTables is as follows:
iptables -t table -A chain -j targetThe row named “[matching options]” is where you give a condition. If the condition is true, it will take the action, else it will move to the next rule in the chain. This detail provides the main function to filter the firewall. There is a huge list of parameters used for matching. But, broadly speaking, the parameters are divided into 3 types: generic parameters, implicit parameters, and explicit parameters.
a. Generic parameters:
- -p: Protocol
- -s: Source IP address
- -d: Destination IP address
- -i: Input interface
- -o: Output interface
- -A: Append a rule to the end of the chain.
- -C: Checks for rule whether it satisfies the chain's requirements.
- -D: Delete a rule from the chain.
- -I: Insert a rule at the specified position in the chain.
- -F: Flush the chain.
- -N: Create a new chain.
- -X: Delete a chain.
The row named “[target]” is where you give the action to be taken if the condition is true. The action can be one of the following:
- ACCEPT: Accept the packet.
- DROP: This target does not allow the connection, but send error message.
- REJECT: This target blocks the connection.
- RETURN: This target is used to stop the processing of the rules in the current chain for the packet.
iptables -A INPUT -p tcp --dport 22 -j ACCEPTiptables -A INPUT -p tcp --dport 22 -j DROPiptables -A INPUT -s 192.268.07.45 -j DROPIf you don’t want your system to send emails, you can block the SMTP ports 25, 465, and 587.
iptables -A OUTPUT -p tcp --dport 25, 465, 587 -j REJECTIf you have too many connections established from a single IP address on a given port (say SSH 22), you can limit the number of connections.
iptables -A INPUT -p tcp --syn --dport 22 -m connlimit --connlimit-above 3 -j REJECTThe connlimit module is used to limit the number of parallel connections to a server per client IP address or per client IP address block.
iptables -A INPUT -p icmp -j DROPiptables -A INPUT -j LOG --log-prefix "Dropped: "If you want to forward the incoming traffic from port 80 to port 8080, you can use the following command:
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 8080iptables -A OUTPUT -o eth0 -d www.example.com -j DROPTo allow it, you can use the following command:
iptables -A OUTPUT -o eth0 -d www.example.com -j ACCEPT