Well ,sir ,I just found a Stored-XSS bug here.
The report link to the wordpress-form is missing, because the manager do not wish to put the public in danger ,I'll just write some details here.
When I login into the wordpress panel, assume I have a low privilege role like a contributor user.
Because the admin user has turned on the option of the wp-plugin simple-download-monitor, a normal user like me can also use it.
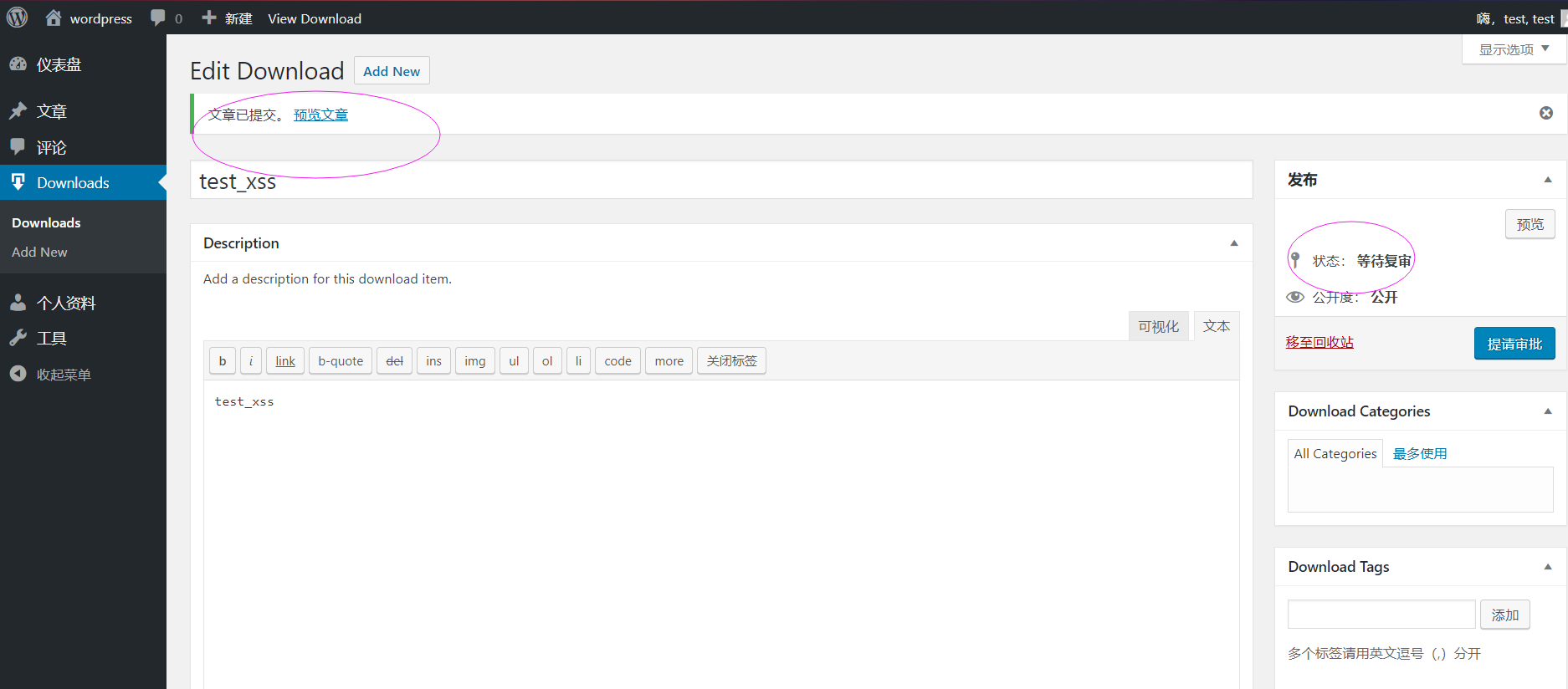
Now I can write something in the function "Edit Download":
http://localhost/wordpress/wp-admin/post.php?post=x&action=edit
But when I fuzz the parameters in this plugin, I found when I write something into these points, it does not filter well:
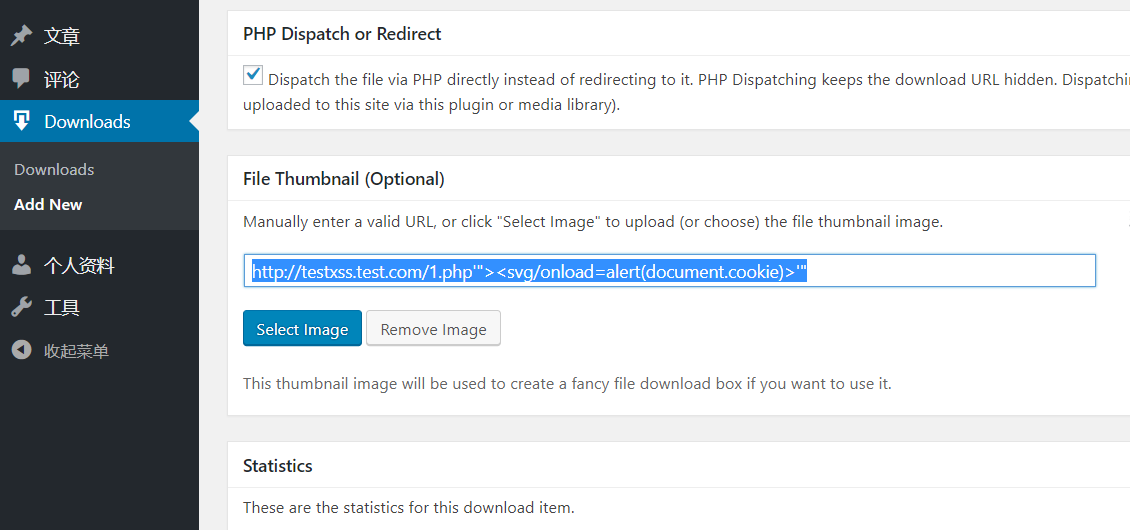
1. File Thumbnail (Optional)
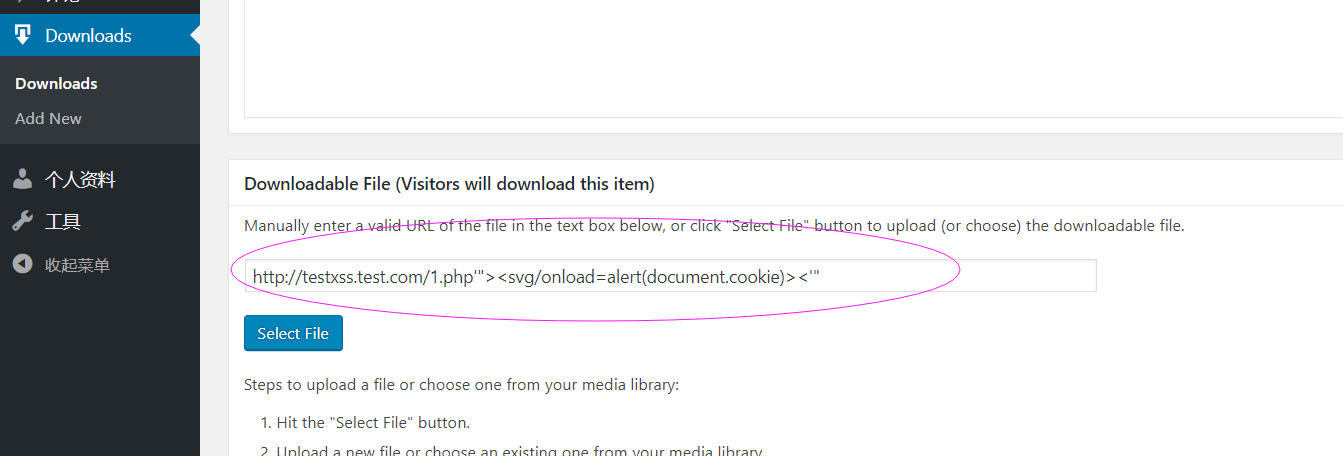
2. Downloadable File (Visitors will download this item)
While it tell us to enter a valid URL of the file in the text box below, I can write something with evil content like:
http://www.test.com/1.php'"><svg/onload=alert(document.cookie)><'"
Then we can publish the post or just submit it to the admin user for an audit.
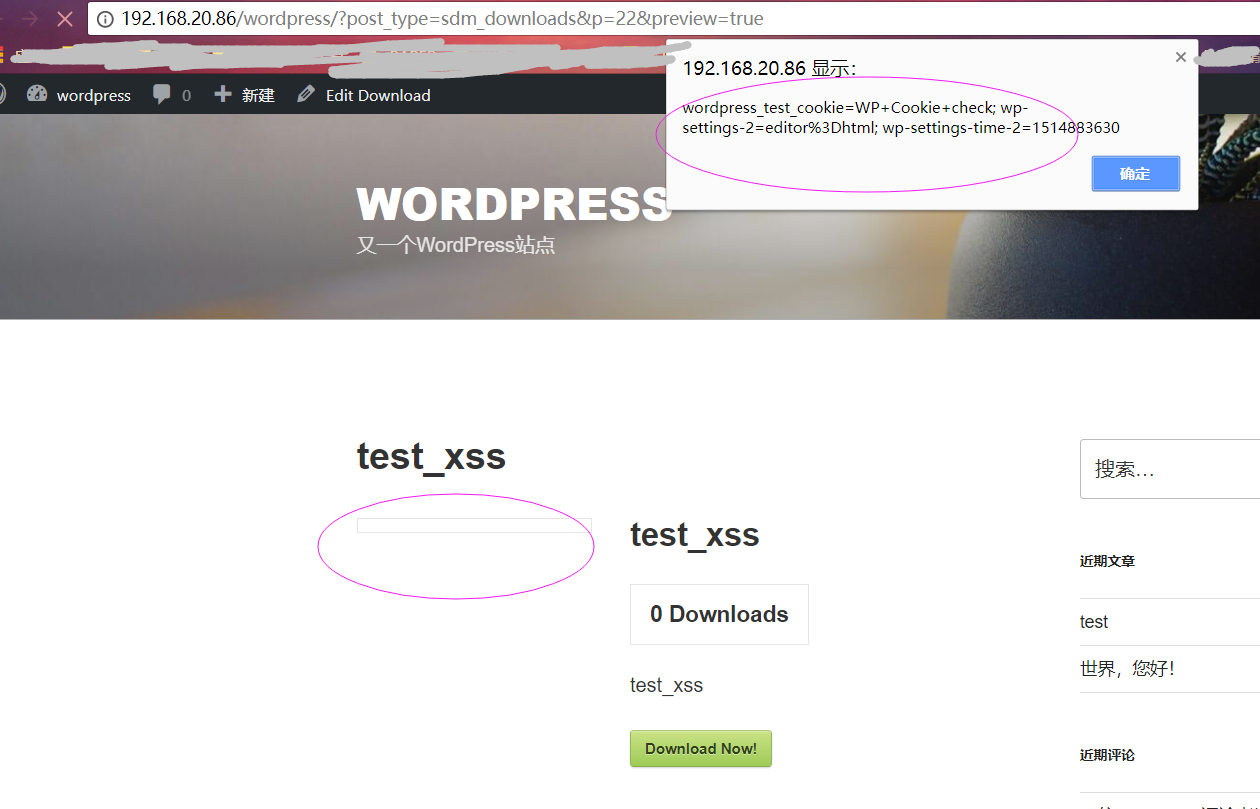
It won't be long beofore I get the other user, even the admin user's cookie or do something more evilly.
Well, by the way, I just test the bug in the wordpress 4.9.1 and the latest version of the wp-plugin simple-download-monitor.