-
Notifications
You must be signed in to change notification settings - Fork 434
Home
PE-sieve is a light-weight tool that helps to detect malware running on the system, as well as to collect the potentially malicious material for further analysis.
Recognizes and dumps variety of implants within the scanned process, such as:
- replaced/injected PEs
- shellcodes
- hooks, and other in-memory patches.
Detects inline hooks, Process Hollowing, Process Doppelgänging, Reflective DLL Injection, etc.
It can be used for dynamic malware unpacking (see examples here).
PE-sieve works on Windows, the lowest supported version is XP.
This tool is intended to help malware analysts, malware hunters, and incident responders in their daily work.
Having a new sample to be analyzed, we can unpack it with PE-sieve very fast, extracting the payload that can be then easily identified and used for further analysis.
When we want to collect material from an infected system of a client. HollowsHunter (an extended PE-sieve based scanner) can scan full system, dumping the injected code from each and every accessible process.
It can also help in cases when the infected client don't know what is the sample that started the infection. PE-sieve/Hollows hunter will search injected material in running processes, and then dump the malicious PE.
Not really. PE-sieve hints about suspicious indicators, however it does not give a final judgment if the process was in fact malicious. For example, it detects hooks - but it cannot judge if the hook was done for malicious or for legitimate purpose. So, it's role is rather to supply a raw material for further processing/analysis, and to hint what are the processes you should examine closer.
You can download the latest stable release from releases.
Fresh test builds (ahead of the official release) can be found here:
If you want to build it by yourself from the sources, follow this small guide.
See the following slides for the detailed explanation
In order to perform a basic scan, you just need to supply the PID of the target process:
pe-sieve.exe /pid <target_pid>
For example, if I suspect that the process svchost.exe is infected, and I want to scan it:
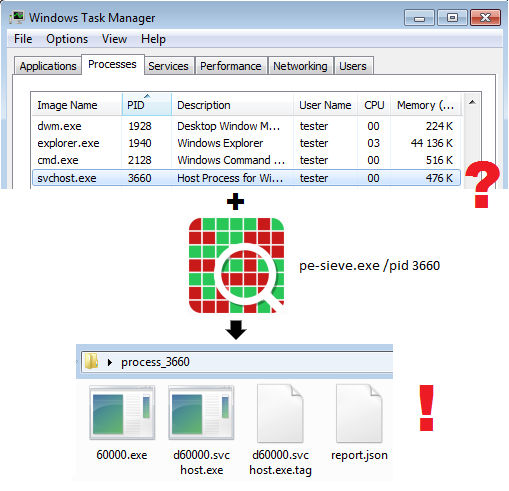
If the process was indeed infected, malware has injected its implants inside. PE-sieve will detect them and dump into a dedicated folder, along with a JSON report describing details of the detected material. The implanted PE files will be automatically unmapped, reconstructed, and ready to be analyzed by other tools. If any of the modules within the process was hooked or patched, PE-sieve will generate a TAG file, helpful in investigating the changes.
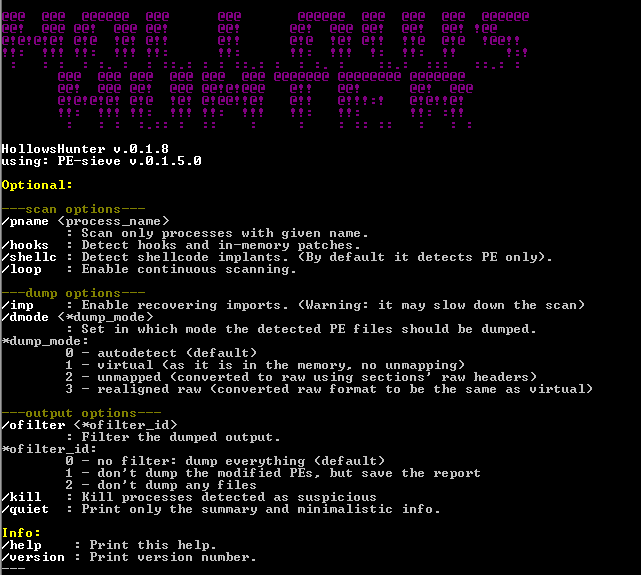
PE-sieve comes with a simple command-line interface. The parameters allows to extend the functionality beyond the default scan. To see the full list of commands, you can deploy it without any parameters.
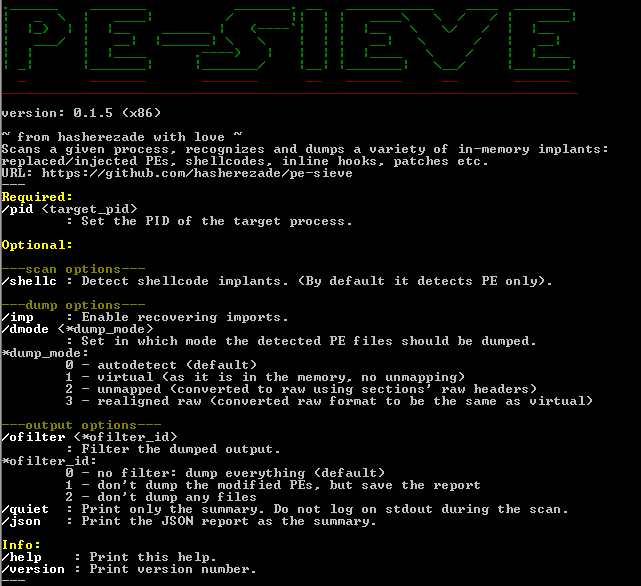
PE-sieve is meant to be a light-weight engine dedicated to scan a single process. It can be built as an EXE or as a DLL. The DLL version exposes a simple API and can be easily integrated with other applications.
If instead of scanning a particular process you want to scan your full system with PE-sieve, you can use HollowsHunter. It contains PE-sieve (a DLL version), but offers also some other features and filters on the top of this base.
Hollows Hunter is a command-line application with an interface similar to PE-sieve: