- Filtering
- Password hash synchronization
- Password writeback
- Device writeback
- Accidental deletes prevention
- Automatic Upgrade
- Self Service
- User ID and password auth
- Federation
- Single Sign-ON (SSO)
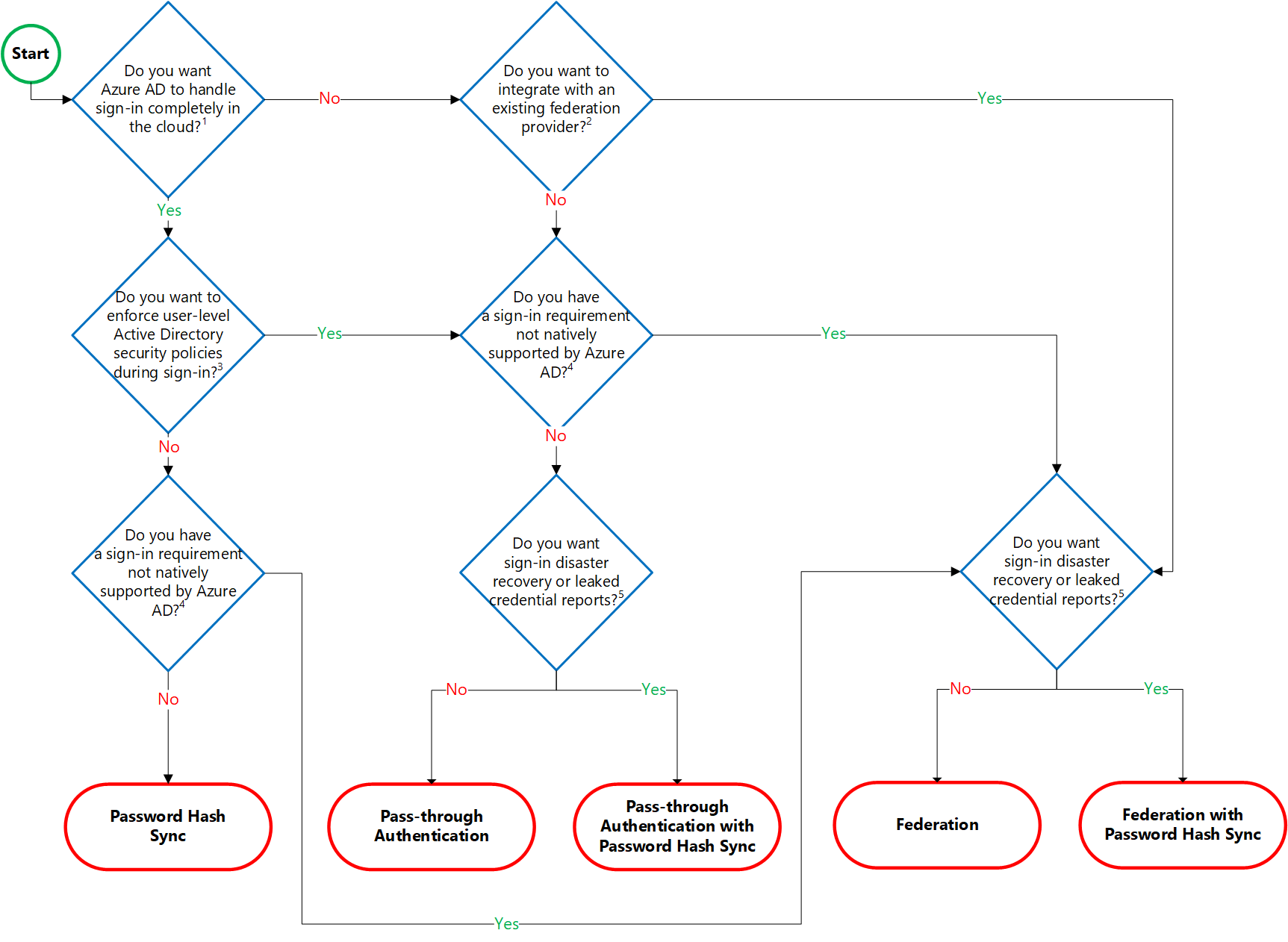
- Cloud-Only
- Password Hash Sync + Seamless SSO (Hybrid)
- Pass-Through Authentication (Hybrid)
- Federation
- Federation with Password hash Sync
- IPSec
- Authentication Headers (AH)
- TLS/SSL
- Multi-factor Authentication
- methods
- register process
- implementation strategy
- Define Access levels
- Define granularity
- Credential checkpoints
- Impersonation/ Delegating of authentication
- Role-based Access Control
- Conditional Access
- Secret Holding Delegation
- Risk mapping
- Catalog Frequency and Size
- Define Patching strategy
- Financial Costs
- Data Loss
- Denial of Service (DoS)
- Image Risk (Loss of Trust
- Customer Confidence Impact
- Government and Corporate Compliance
- Expired users
- High permission
- Physical access
- Access Reviews
- Least Privilege principle
- Policies
- Health Checks
- Compliance to standards
- Training
- Layers of Security
- Toolset: Firewall/antivirus
- *Advanced threat Protection (ATP)
- Define Metrics
- Alert/Notification strategy
- Privileged Identity Management (PIM)
- Stage 1 (24-48 hours): Critical items that we recommend you do right away
- Stage 2 (2-4 weeks): Mitigate the most frequently used attack techniques
- Stage 3 (1-3 months): Build visibility and build full control of admin activity
- Stage 4 (six months and beyond): Continue building defenses to further harden your security platform