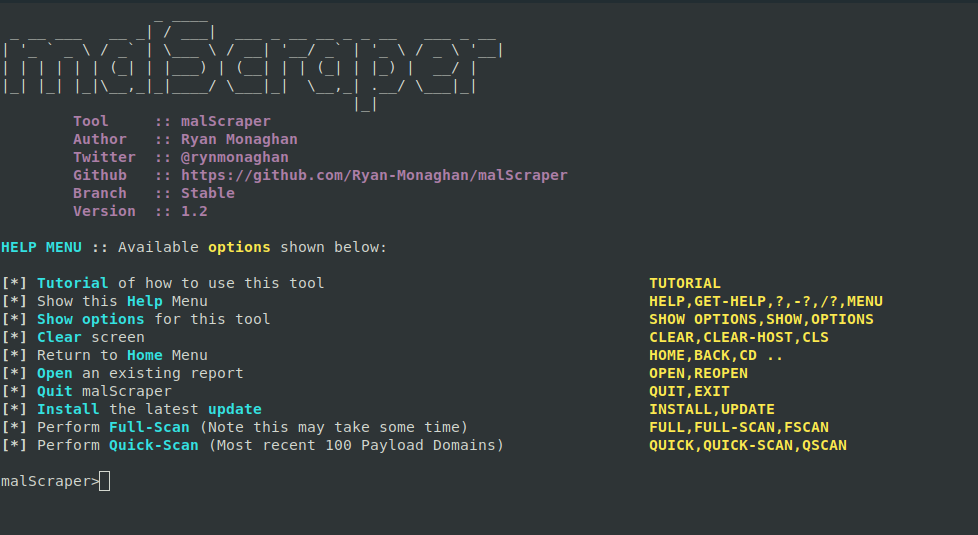
- malScraper is a modular tool that streamlines the process of scraping and managing lists of Payload Domains, IOC's & C2 IPs from various feeds. It simplifies the task of blacklisting for security and threat intelligence purposes.
- Modular Design: Easily extendable with additional modules.
- Version Checking: Verify if you are using the latest version on startup.
- Reopen Functionality: Ability to reopen a previously composed report.
-
1.3 - Initial Python Conversion
- The tool has been converted to Python for improved functionality.
-
1.2 - Version Checking
- malScraper now verifies if you are using the latest version on startup.
-
1.1 - Reopen Functionality
- Added the ability to reopen a previously composed report.
-
1.0 - Initial Implementation
- Core functionality was implemented in the first release.
- Clone the repository.
git clone https://github.com/rynmon/malScraper
- Navigate to the project directory.
cd malScraper
- Install dependencies.
pip install -r requirements.txt
- To use malScraper, follow these steps:
- Run the tool.
python malScraper.py
- Follow the on-screen instructions to configure and use the tool.
- Contributions are welcome! If you find a bug or have an enhancement in mind, feel free to open an issue or submit a pull request.
- malScraper will automatically check for updates on startup. Make sure you are using the latest version to benefit from new features and improvements.
- This project is licensed under the MIT License.