Contact Details
@@ -95,14 +95,14 @@Social Media
 -
+
-
+
 }}
### CyberSecurity Career Outlooks and Information
-#### [What Does a Cybersecurity Career Path Look Like?](https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/)
+#### [What Does a Cybersecurity Career Path Look Like?](https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/)
- Insights into the various career paths available in cybersecurity.
-#### [Cybersecurity Analyst Salaries: Entry Level to Pro](https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/)
+#### [Cybersecurity Analyst Salaries: Entry Level to Pro](https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/)
- Understanding the salary ranges for cybersecurity analysts.
-#### [What Does a Cybersecurity Expert Do?](https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/)
+#### [What Does a Cybersecurity Expert Do?](https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/)
- Explore the roles and responsibilities of cybersecurity experts.
@@ -81,33 +81,33 @@ When pursuing a career in cybersecurity, one important consideration is obtainin
### Degrees
-#### [Do I Need a Degree for a Cybersecurity Job?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/do-i-need-a-degree-for-a-cybersecurity-job/)
+#### [Do I Need a Degree for a Cybersecurity Job?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/do-i-need-a-degree-for-a-cybersecurity-job/)
- Find out whether having a degree is necessary to pursue a career in cybersecurity and learn about alternative paths.
-#### [Which Courses Should I Take for a Job in Cybersecurity?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/which-courses-should-i-take-for-a-job-in-cybersecurity/)
+#### [Which Courses Should I Take for a Job in Cybersecurity?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/which-courses-should-i-take-for-a-job-in-cybersecurity/)
- Discover recommended courses and educational resources to enhance your skills and knowledge in cybersecurity.
### Certifications
-#### [Are Certifications Needed for a Cybersecurity Career?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/)
+#### [Are Certifications Needed for a Cybersecurity Career?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/)
- Explore the importance of certifications in the cybersecurity field and their impact on career opportunities.
-#### [Performance-Based Questions (PBQs) and Cybersecurity Certifications](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/performance-based-questions-pbqs-and-cybersecurity-certifications/)
+#### [Performance-Based Questions (PBQs) and Cybersecurity Certifications](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/performance-based-questions-pbqs-and-cybersecurity-certifications/)
- Learn about performance-based questions (PBQs) in cybersecurity certifications and how to prepare for them.
-#### [CEUs in Cybersecurity: What They Are and Why You Need Them](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/ceus-in-cybersecurity-what-they-are-and-why-you-need-them/)
+#### [CEUs in Cybersecurity: What They Are and Why You Need Them](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/ceus-in-cybersecurity-what-they-are-and-why-you-need-them/)
- Understand the concept of Continuing Education Units (CEUs) in cybersecurity and their importance for professional development.
#### Certification Guides and Tips
We've included a few tips and tricks for these certifications below:
-- [Passing CompTIA's A+](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/)
-- [Passing CompTIA's Security+](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
-- [Passing CompTIA's Linux+](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/)
-- [Passing EC-Council's CEH](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [Passing ISC2's CISSP](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/)
+- [Passing CompTIA's A+](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/)
+- [Passing CompTIA's Security+](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [Passing CompTIA's Linux+](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/)
+- [Passing EC-Council's CEH](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [Passing ISC2's CISSP](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/)
##### Certification Practice Tests
@@ -132,11 +132,11 @@ We've included a few tips and tricks for these certifications below:
### Bootcamps
-#### [Are Cybersecurity Bootcamps Worth it?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it)
+#### [Are Cybersecurity Bootcamps Worth it?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it)
### Other Training Types
-#### [Army Cybersecurity Awareness Training: What You Need to Know](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/army-cybersecurity-awareness-training-what-you-need-to-know)
+#### [Army Cybersecurity Awareness Training: What You Need to Know](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/army-cybersecurity-awareness-training-what-you-need-to-know)
- Get insights into the cybersecurity awareness training provided by the army and its relevance in today's digital landscape.
{{< inarticle-dark >}}
@@ -145,61 +145,61 @@ We've included a few tips and tricks for these certifications below:
Securing a job in cybersecurity requires a combination of knowledge, experience, and preparation. In this section, you'll discover valuable resources and insights to help you navigate the job market, prepare for interviews, and increase your chances of landing an entry-level or remote cybersecurity position.
-- [Navigating Early Career Job Market: Overcoming Challenges and Securing Opportunities](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/addressing-the-challenges-in-the-early-career-job-market/)
+- [Navigating Early Career Job Market: Overcoming Challenges and Securing Opportunities](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/addressing-the-challenges-in-the-early-career-job-market/)
- Discover strategies to overcome challenges in the early career job market, acquire valuable skills, and secure desirable opportunities for success.
-- [Navigating the Changing Cybersecurity Landscape: Challenges and Strategies for Early Career Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-evolving-landscape-what-works-today-vs-what-worked-10-years-ago/)
+- [Navigating the Changing Cybersecurity Landscape: Challenges and Strategies for Early Career Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-evolving-landscape-what-works-today-vs-what-worked-10-years-ago/)
- Explore the evolving cybersecurity industry and its impact on early career professionals, with practical guidance on addressing challenges and thriving in today's landscape.
### Step-by-Step Into the Cyber Security Career Path
-- [Step-by-Step Into the Cyber Security Career Path](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/step-by-step-into-to-cyber-security-career-path/)
+- [Step-by-Step Into the Cyber Security Career Path](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/step-by-step-into-to-cyber-security-career-path/)
- Follow a comprehensive guide outlining the essential steps and milestones to pursue a career in cyber security.
### Interview Preparation
#### Cyber Security Interview Questions
-- [Cyber Security Interview Questions](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/)
+- [Cyber Security Interview Questions](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/)
- Familiarize yourself with common interview questions in the field of cybersecurity and prepare for successful interviews.
#### Resume Writing
-- [Resume Writing Tips for Cyber Security Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/)
+- [Resume Writing Tips for Cyber Security Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/)
- Enhance your chances of landing your dream job with these expert resume writing tips for cybersecurity, software development, and IT professionals.
#### Networking and Professional Connections
-- [Networking Tips for Landing a Job in Cyber Security](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/networking-tips-for-landing-a-job-in-cybersecurity/)
+- [Networking Tips for Landing a Job in Cyber Security](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/networking-tips-for-landing-a-job-in-cybersecurity/)
- Unlock valuable networking tips to secure your dream job in cybersecurity, connecting with professionals and discovering hidden opportunities.
### Transitioning to Cybersecurity
#### How to Transition from IT to Cybersecurity
-- [How to Transition from IT to Cybersecurity](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-transition-from-it-to-cybersecurity/)
+- [How to Transition from IT to Cybersecurity](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-transition-from-it-to-cybersecurity/)
- Learn about the steps and considerations involved in making a successful transition from IT to a career in cybersecurity.
#### Mastering Cybersecurity: The Role of Systems Administration and Practical Experience
-- [Mastering Cybersecurity: The Role of Systems Administration and Practical Experience](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/building-a-path-to-cybersecurity-and-the-benefit-of-practical-experience/)
+- [Mastering Cybersecurity: The Role of Systems Administration and Practical Experience](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/building-a-path-to-cybersecurity-and-the-benefit-of-practical-experience/)
- Gain insights into the role of systems administration and practical experience in building a successful career in cybersecurity.
### Best Locations for Cybersecurity Jobs
#### The 7 Top Locations for Cyber Security Jobs in the US 2023: Best Cities for Professionals
-- [The 7 Top Locations for Cyber Security Jobs in the US 2023: Best Cities for Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-in-the-united-states)
+- [The 7 Top Locations for Cyber Security Jobs in the US 2023: Best Cities for Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-in-the-united-states)
- Discover the best locations for cybersecurity jobs in the United States in 2023, from Washington, D.C. to San Francisco, with abundant opportunities and industry growth.
#### The Top 5 Locations Worldwide for Cybersecurity Jobs in 2023: Best Cities for Professionals
-- [The Top 5 Locations Worldwide for Cybersecurity Jobs in 2023: Best Cities for Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-worldwide)
+- [The Top 5 Locations Worldwide for Cybersecurity Jobs in 2023: Best Cities for Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-worldwide)
- Discover the best locations worldwide for cybersecurity jobs in 2023, from London to Singapore, with abundant opportunities and industry growth.
### Cybersecurity Internships
#### How to Find and Get Cybersecurity Internships
-- [How to Find and Get Cybersecurity Internships](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-how-to-get-cybersecurity-internships/)
+- [How to Find and Get Cybersecurity Internships](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-how-to-get-cybersecurity-internships/)
- Discover strategies and resources for finding and securing cybersecurity internships to gain practical experience.
### Entry-Level Cyber Security Jobs
#### Preparation and Resources for Entry-Level Cyber Security Jobs
-- [Preparation and Resources for Entry-Level Cyber Security Jobs](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/preparation-and-resources-for-entry-level-cyber-security-jobs/)
+- [Preparation and Resources for Entry-Level Cyber Security Jobs](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/preparation-and-resources-for-entry-level-cyber-security-jobs/)
- Get tips and resources to prepare for entry-level cyber security positions and increase your chances of landing a job.
### Remote Cybersecurity Jobs
#### How to Find and Get the Best Remote Cybersecurity Job
-- [How to Find and Get the Best Remote Cybersecurity Job](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-get-the-best-remote-cybersecurity-job/)
+- [How to Find and Get the Best Remote Cybersecurity Job](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-get-the-best-remote-cybersecurity-job/)
- Explore strategies and resources to find and secure remote cybersecurity jobs that align with your career goals.
{{< inarticle-dark >}}
@@ -209,35 +209,35 @@ Securing a job in cybersecurity requires a combination of knowledge, experience,
As a cybersecurity professional, continuous learning and growth are key to advancing your career. This section focuses on strategies for earning certifications, learning new skills, staying updated on emerging threats and vulnerabilities, and education on the regulations that define and regulate what you do, enabling you to progress and excel in your cybersecurity journey.
### New Skills and Certifications
-#### [Earning Certifications and Learning New Skills as a Cyber Security Professional](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/earning-certifications-and-learning-new-skills-as-a-cyber-security-professional/)
+#### [Earning Certifications and Learning New Skills as a Cyber Security Professional](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/earning-certifications-and-learning-new-skills-as-a-cyber-security-professional/)
- Discover the importance of earning certifications and continuously expanding your skills as a cybersecurity professional.
### Advanced Topics
-#### [How to Learn About CVEs and Threat Actors](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/how-to-learn-about-cves-and-threat-actors/)
+#### [How to Learn About CVEs and Threat Actors](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/how-to-learn-about-cves-and-threat-actors/)
- Gain insights into Common Vulnerabilities and Exposures (CVEs/) and threat actors, and learn how to stay updated on emerging threats.
-#### [Implementing the NICE Cybersecurity Framework: Best Practices for Enhanced Cyber Defense](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/implementing-the-nice-cybersecurity-framework/)
+#### [Implementing the NICE Cybersecurity Framework: Best Practices for Enhanced Cyber Defense](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/implementing-the-nice-cybersecurity-framework/)
- Discover the key steps to effectively implement the NICE Cybersecurity Framework and fortify your organization's defenses against cyber threats..
### Understanding Regulations, Acts, and Guidelines
-#### [Federal Information Security Management Act (FISMA) Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/)
-Learn about the [Federal Information Security Management Act (FISMA)](https://simeononsecurity.ch/articles/fisma-summarized/), a U.S. federal law that establishes cybersecurity requirements for government agencies.
+#### [Federal Information Security Management Act (FISMA) Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/)
+Learn about the [Federal Information Security Management Act (FISMA)](https://simeononsecurity.com/articles/fisma-summarized/), a U.S. federal law that establishes cybersecurity requirements for government agencies.
-#### [NIST SP 800-181 - Cyber Security Workforce Framework Overview and Comparison with the DCWF](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-sp-800-181-workforce-framework-for-cybersecurty-and-the-dod-dcwf/)
+#### [NIST SP 800-181 - Cyber Security Workforce Framework Overview and Comparison with the DCWF](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-sp-800-181-workforce-framework-for-cybersecurty-and-the-dod-dcwf/)
- Discover the comprehensive evaluation and development frameworks for cybersecurity workforce: NICE and DoD DCWF, empowering organizations with skilled professionals.
-#### [DoD 8140-03 - Cyberspace Workforce Qualifications and Management Program - Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-manual-8140.03-cyberspace-workforce-qualification-and-management-program/)
+#### [DoD 8140-03 - Cyberspace Workforce Qualifications and Management Program - Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-manual-8140.03-cyberspace-workforce-qualification-and-management-program/)
- Discover the key aspects of the Department of Defense (DoD) 8140-03 manual, which outlines qualifications and management for the cyberspace workforce.
-#### [Navigating Workforce Frameworks: Implications for Cybersecurity Pros](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/workforce-frameworks-and-the-challenges/)
+#### [Navigating Workforce Frameworks: Implications for Cybersecurity Pros](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/workforce-frameworks-and-the-challenges/)
- Explore the impact of changing workforce frameworks on cybersecurity professionals and the challenges they face in meeting new requirements.
-#### [DoD 5220.22-m - Data Sanitization - Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-5220.22-m-data-sanitization-summarized)
-- Explore the summary of [DoD 5220.22-m](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/), a directive that provides guidance on data sanitization.
+#### [DoD 5220.22-m - Data Sanitization - Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-5220.22-m-data-sanitization-summarized)
+- Explore the summary of [DoD 5220.22-m](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/), a directive that provides guidance on data sanitization.
-#### [NIST 800-88 - Guidelines for Media Sanitization - Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/)
+#### [NIST 800-88 - Guidelines for Media Sanitization - Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/)
- Learn about the summarized guidelines outlined in NIST 800-88 for media sanitization.
{{< inarticle-dark >}}
@@ -246,33 +246,33 @@ Learn about the [Federal Information Security Management Act (FISMA)](https://si
This section provides valuable resources and insights on managing a cyber security team, including tips for **building and managing a cybersecurity team** and best practices for **managing a cyber security team**.
-- [Building a Cyber Security Team](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/building-and-managing-a-cybersecurity-team/):
+- [Building a Cyber Security Team](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/building-and-managing-a-cybersecurity-team/):
- This resource offers guidance on building a cyber security team, covering topics such as team composition, skillsets, and recruitment strategies.
-- [Managing a Cyber Security Team](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/managing-a-cyber-security-team/):
+- [Managing a Cyber Security Team](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/managing-a-cyber-security-team/):
- Explore effective techniques and strategies for managing a cyber security team, including team leadership, performance management, and fostering a strong security culture.
### Outsourcing vs. In-house Cyber Security
When considering whether to outsource or keep cybersecurity tasks in-house, it is important to evaluate the advantages and drawbacks. These resources provide insights into the **outsourcing vs. in-house** decision-making process.
-- [Is Outsourcing Cyber Security Efforts a Good Idea?](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/):
- - This article discusses the pros and cons of [outsourcing cyber security](https://simeononsecurity.ch/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) efforts and provides guidance on making an informed decision.
+- [Is Outsourcing Cyber Security Efforts a Good Idea?](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/):
+ - This article discusses the pros and cons of [outsourcing cyber security](https://simeononsecurity.com/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) efforts and provides guidance on making an informed decision.
-- [Critical Cyber Security Roles that You Should Have In-House](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/cybersecurity-tasks-that-shouldnt-be-outsourced/):
+- [Critical Cyber Security Roles that You Should Have In-House](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/cybersecurity-tasks-that-shouldnt-be-outsourced/):
- Discover the **critical cyber security roles** that are best kept in-house to ensure control, expertise, and alignment with organizational objectives.
### Developing Plans and Programs
Developing robust cyber security plans and programs is essential for effective security management. These resources offer guidance on creating **cyber security policies, procedures, programs**, and **incident response programs**.
-- [How to Develop Cyber Security Policies, Procedures, and Programs](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/):
+- [How to Develop Cyber Security Policies, Procedures, and Programs](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/):
- Learn how to develop comprehensive cyber security policies, procedures, and programs to establish a strong security foundation within your organization.
-- [How to Build a Cyber Security Awareness and Training Program](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/):
+- [How to Build a Cyber Security Awareness and Training Program](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/):
- Learn how to build a comprehensive security awareness training program to protect your organization from cyber threats and empower employees.
-- [How to Develop an Incident Response Program](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/):
+- [How to Develop an Incident Response Program](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/):
- This resource provides guidance on building an effective incident response program, including planning, team roles, and incident handling best practices.
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook-start/pageschema.html b/content/cyber-security-career-playbook-start/pageschema.html
index e9b8399eff3f6..b7f11302468ef 100644
--- a/content/cyber-security-career-playbook-start/pageschema.html
+++ b/content/cyber-security-career-playbook-start/pageschema.html
@@ -19,7 +19,7 @@
"bestRating": "5",
"ratingCount": "100"
},
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook-start",
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook-start",
"author": {
"@type": "Person",
"name": "SimeonOnSecurity"
@@ -38,7 +38,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "Simplified explanations of cybersecurity concepts for beginners.",
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/"
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/"
}
},
{
@@ -47,7 +47,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "Cybersecurity is the practice of protecting computers, servers, networks, and data from digital attacks or unauthorized access.",
- "url": "https://simeononsecurity.ch/articles/what-is-cybersecurity/"
+ "url": "https://simeononsecurity.com/articles/what-is-cybersecurity/"
}
},
{
@@ -56,7 +56,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "Common cybersecurity threats include viruses, malware, phishing attacks, ransomware, and social engineering. These threats can compromise the security of systems, steal data, or cause other harmful effects.",
- "url": "https://simeononsecurity.ch/articles/cybersecurity-threats-to-watch-out-for-in-2023/"
+ "url": "https://simeononsecurity.com/articles/cybersecurity-threats-to-watch-out-for-in-2023/"
}
},
{
@@ -65,7 +65,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "To protect yourself from cybersecurity threats, you can follow best practices such as using strong and unique passwords, enabling two-factor authentication, keeping your software up to date, being cautious of suspicious emails or links, and using antivirus software.",
- "url": "https://simeononsecurity.ch/articles/safe-social-media-practices-and-protecting-your-privacy-online/"
+ "url": "https://simeononsecurity.com/articles/safe-social-media-practices-and-protecting-your-privacy-online/"
}
},
{
@@ -74,7 +74,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "A cybersecurity career involves working to protect computer systems, networks, and data from cyber threats. It includes roles such as cybersecurity analyst, penetration tester, incident responder, and security architect.",
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/"
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/"
}
},
{
@@ -83,7 +83,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "To start a career in cybersecurity, you can pursue education and certifications in the field, gain practical experience through internships or entry-level positions, participate in cybersecurity competitions and challenges, and stay updated with the latest industry trends and technologies.",
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook-start/"
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook-start/"
}
}
]
diff --git a/content/cyber-security-career-playbook/_index.en.md b/content/cyber-security-career-playbook/_index.en.md
index 17a7cc9effc80..af0021bbe5c0e 100644
--- a/content/cyber-security-career-playbook/_index.en.md
+++ b/content/cyber-security-career-playbook/_index.en.md
@@ -3,7 +3,7 @@ title: "Cyber Security Career Playbooks"
description: "Discover valuable insights, practical tips, and resources to embark on a successful cybersecurity career and make an impact in the ever-changing digital landscape."
tags: ["cybersecurity career", "beginner's guide to cybersecurity", "launching a cybersecurity career", "cybersecurity job prospects", "cybersecurity salary ranges", "cybersecurity training programs", "online cybersecurity courses", "video courses for cybersecurity", "cybersecurity books", "beginners cybersecurity courses", "explain cybersecurity to a 5-year-old", "ELI5 cybersecurity", "top programming languages for cybersecurity", "cybersecurity career path", "cybersecurity expert responsibilities", "soft skills for cybersecurity", "cybersecurity industry", "cybersecurity job market", "cybersecurity certifications", "cybersecurity job demand", "cybersecurity job growth", "cybersecurity skills", "cybersecurity professional", "cybersecurity analyst", "cybersecurity specialist", "cybersecurity consultant", "cybersecurity threats", "cybersecurity best practices", "cybersecurity strategies", "cybersecurity tools", "job opportunities", "cybersecurity internships", "remote cybersecurity jobs", "continuous learning", "emerging threats", "cybersecurity network", "cybersecurity laws", "professional growth", "cybersecurity guidance", "cybersecurity community", "cybersecurity resources", "career advancement", "cybersecurity landscape", "cybersecurity knowledge"]
categories: ["cyber-security-career-playbook"]
-project_url: "https://simeononsecurity.ch/cyber-security-career-playbook-start"
+project_url: "https://simeononsecurity.com/cyber-security-career-playbook-start"
sitemap:
priority : 0.7
---
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md
index c2f9a3e808640..610005ec999c8 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md
@@ -12,7 +12,7 @@ coverAlt: "A laptop with a graduation hat on the keyboard, surrounded by stacks
coverCaption: ""
---
-With the constantly changing job market and the need for up-to-date skills, many individuals are turning to bootcamps as a way to quickly acquire new knowledge and certifications. However, the question remains: [are bootcamps worth it](https://simeononsecurity.ch/articles/are-bootcamps-worth-it/)? In this article, we will explore the pros and cons of bootcamps and help you determine if they are the right choice for you.
+With the constantly changing job market and the need for up-to-date skills, many individuals are turning to bootcamps as a way to quickly acquire new knowledge and certifications. However, the question remains: [are bootcamps worth it](https://simeononsecurity.com/articles/are-bootcamps-worth-it/)? In this article, we will explore the pros and cons of bootcamps and help you determine if they are the right choice for you.
## [Home](/cyber-security-career-playbook-start/)
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md
index 0b1e094d7b85a..a258bc4c6dbe5 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md
@@ -51,9 +51,9 @@ ______
When pursuing certifications, it is important to consider your career goals, interests, and the specific requirements of your desired job roles. Here are some popular certifications in the cybersecurity field:
-1. [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): A foundational certification covering essential security concepts and best practices.
-2. [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/): A globally recognized certification for experienced cybersecurity professionals.
-3. [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): Focuses on ethical hacking techniques to identify and address vulnerabilities.
+1. [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): A foundational certification covering essential security concepts and best practices.
+2. [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/): A globally recognized certification for experienced cybersecurity professionals.
+3. [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): Focuses on ethical hacking techniques to identify and address vulnerabilities.
4. **Certified Information Security Manager (CISM)**: Designed for individuals managing, designing, and overseeing an enterprise's information security program.
5. **Certified Information Systems Auditor (CISA)**: Focuses on auditing, control, and security of information systems.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md
index 9d5aa6f6fe216..e5dd036f59d6f 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md
@@ -55,8 +55,8 @@ There are various study materials available to candidates, such as textbooks, on
- {{< youtube id="_nyZhYnCNLA" >}}
- [PluralSight (Preferred)](https://www.pluralsight.com/)
- [Official Study Guide and Practice Tests](https://amzn.to/3LAu3Ly)
-- [More Learning Resources](https://simeononsecurity.ch/recommendations/learning_resources)
-- [SimeonOnSecurity's CISSP Practice Test](https://simeononsecurity.ch/cissp-practice-test)
+- [More Learning Resources](https://simeononsecurity.com/recommendations/learning_resources)
+- [SimeonOnSecurity's CISSP Practice Test](https://simeononsecurity.com/cissp-practice-test)
### Step 4: Practice with practice exams
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md
index 1cc776117038b..2b7e69d534ceb 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md
@@ -184,7 +184,7 @@ In addition to studying the exam objectives and using the recommended materials,
4. **Practice, practice, practice**: Take as many practice exams and performance-based questions as possible. This will help you become familiar with the exam format and identify areas where you need to focus your study efforts.
-- [**SimeonOnSecurity's Security Plus Practice Test**](https://simeononsecurity.ch/security-plus-practice-test)
+- [**SimeonOnSecurity's Security Plus Practice Test**](https://simeononsecurity.com/security-plus-practice-test)
5. **Stay current with industry trends**: Stay up-to-date with current industry trends and news related to information security. This will help you contextualize the exam material and understand how it applies in real-world situations.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md
index 9424bb7f6cd3e..6f23dfde01925 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md
@@ -96,7 +96,7 @@ One of the best ways to prepare for the CompTIA A+ exams is to take practice exa
There are a variety of online resources available that offer practice exams for the CompTIA A+ exams. Some popular options include:
-- [**SimeonOnSecurity's A Plus Practice Test**](https://simeononsecurity.ch/a-plus-practice-test)
+- [**SimeonOnSecurity's A Plus Practice Test**](https://simeononsecurity.com/a-plus-practice-test)
- [**CertMaster Practice from CompTIA**](https://www.comptia.org/training/certmaster-practice/a): CertMaster Practice offers a range of practice exams and quizzes that are designed to help you prepare for the actual exam.
- [**ExamCompass**](https://www.examcompass.com/): ExamCompass offers a range of free practice exams for the CompTIA A+ exams, as well as other IT certifications.
- [**Udemy**](https://www.udemy.com/): Udemy offers a variety of paid courses and practice exams for the CompTIA A+ exams.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md
index 9a3d8a11e73e2..9edf6895f599d 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md
@@ -11,7 +11,7 @@ coverCaption: ""
---
**Tips and Tricks for Passing CompTIA's Linux+ XK0-005**
-CompTIA Linux+ certification is one of the most sought-after certifications in the field of IT. This certification is designed to validate the skills of IT professionals in working with Linux operating systems. The Linux+ certification exam [XK0-005](https://simeononsecurity.ch/articles/passing-comptias-linux-plus-xk0-005/) is the latest version of this exam and validates the skills and knowledge required to configure, monitor, and troubleshoot Linux systems. Here are some tips and tricks to help you pass the [CompTIA Linux+ XK0-005](https://simeononsecurity.ch/articles/passing-comptias-linux-plus-xk0-005/) exam.
+CompTIA Linux+ certification is one of the most sought-after certifications in the field of IT. This certification is designed to validate the skills of IT professionals in working with Linux operating systems. The Linux+ certification exam [XK0-005](https://simeononsecurity.com/articles/passing-comptias-linux-plus-xk0-005/) is the latest version of this exam and validates the skills and knowledge required to configure, monitor, and troubleshoot Linux systems. Here are some tips and tricks to help you pass the [CompTIA Linux+ XK0-005](https://simeononsecurity.com/articles/passing-comptias-linux-plus-xk0-005/) exam.
## [Home](/cyber-security-career-playbook-start/)
@@ -54,7 +54,7 @@ To gain hands-on experience, you can set up a lab environment where you can prac
- **Cloud Services**: You can also use cloud services such as Amazon Web Services (AWS) or Microsoft Azure to create virtual machines or containers running Linux. This can be a convenient option if you don't have the resources to set up a physical lab environment.
-- [**Home Lab**](https://simeononsecurity.ch/articles/what-is-a-homelab-and-should-you-have-one/): If you have the resources, you can set up a physical lab environment at home. This can include one or more physical servers or workstations running Linux, as well as networking equipment such as switches and routers.
+- [**Home Lab**](https://simeononsecurity.com/articles/what-is-a-homelab-and-should-you-have-one/): If you have the resources, you can set up a physical lab environment at home. This can include one or more physical servers or workstations running Linux, as well as networking equipment such as switches and routers.
By getting hands-on experience with Linux systems, you'll gain practical experience in configuring, monitoring, and troubleshooting Linux systems. This will help you prepare for the CompTIA Linux+ XK0-005 exam and also give you valuable skills that can be used in a professional setting.
@@ -103,7 +103,7 @@ Some examples of online resources for the CompTIA Linux+ XK0-005 exam include:
- [**YouTube Tutorials**](https://www.youtube.com/watch?v=niPWk7tgD2Q&list=PL78ppT-_wOmuwT9idLvuoKOn6UYurFKCp): There are many YouTube channels that provide video tutorials on various Linux-related topics, including some focused specifically on the Linux+ certification. {{< youtube id="YOomKJdLLEo" >}}
-- [**Our Guide on Learning Linux**](https://simeononsecurity.ch/articles/how-do-i-learn-linux/): This guide provides an overview of how to get started with Linux, including tips for learning both Debian and RHEL-based variants of Linux.
+- [**Our Guide on Learning Linux**](https://simeononsecurity.com/articles/how-do-i-learn-linux/): This guide provides an overview of how to get started with Linux, including tips for learning both Debian and RHEL-based variants of Linux.
By using online resources, you can access a wide range of study materials and get a better understanding of the exam objectives and sub-topics. Additionally, many online resources offer interactive elements such as forums or chat rooms where you can ask questions and get help from other Linux professionals.
@@ -113,7 +113,7 @@ Practice exams are a great way to prepare for the CompTIA Linux+ XK0-005 exam. T
Some examples of practice exams for the CompTIA Linux+ XK0-005 exam include:
-- [**SimeonOnSecurity's Linux Plus Practice Test**](https://simeononsecurity.ch/linux-plus-practice-test)
+- [**SimeonOnSecurity's Linux Plus Practice Test**](https://simeononsecurity.com/linux-plus-practice-test)
- [**CompTIA Linux+ Certification Practice Exams**](https://www.comptia.org/training/certmaster-practice/linux): This book includes four complete practice exams that are designed to simulate the format and difficulty of the actual exam.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md
index c29ba8cd529be..4a4fb2011506c 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md
@@ -11,7 +11,7 @@ coverCaption: ""
---
**Creating a Study Plan for Passing the CEH Certification Exam: Tips and Strategies for Success**
-If you're interested in pursuing a career in cybersecurity, obtaining a certification is a great way to validate your knowledge and expertise. One such certification is the [**Certified Ethical Hacker (CEH)**](https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/) certification, which is designed to test your understanding of various security threats and vulnerabilities. However, passing the [CEH exam](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can be challenging, and it's important to have a well-structured study plan to ensure success. In this article, we'll discuss some tips and strategies for creating an effective study plan to help you pass the [CEH certification exam](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/).
+If you're interested in pursuing a career in cybersecurity, obtaining a certification is a great way to validate your knowledge and expertise. One such certification is the [**Certified Ethical Hacker (CEH)**](https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/) certification, which is designed to test your understanding of various security threats and vulnerabilities. However, passing the [CEH exam](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can be challenging, and it's important to have a well-structured study plan to ensure success. In this article, we'll discuss some tips and strategies for creating an effective study plan to help you pass the [CEH certification exam](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/).
## [Home](/cyber-security-career-playbook-start/)
@@ -45,8 +45,8 @@ Once you've created a study schedule, the next step is to choose the right study
- {{< youtube id="maO8_0cA7W8" >}}
- [PluralSight (Preferred)](https://www.pluralsight.com/)
- [Official Study Guide and Practice Tests](https://amzn.to/42lr6pu)
-- [More Learning Resources](https://simeononsecurity.ch/recommendations/learning_resources)
-- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.ch/ceh-practice-test)
+- [More Learning Resources](https://simeononsecurity.com/recommendations/learning_resources)
+- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.com/ceh-practice-test)
### Focus on Weak Areas
@@ -58,7 +58,7 @@ As you begin studying, focus on your weak areas. This will help you make the mos
Taking practice exams is a great way to prepare for the CEH exam. You can find practice exams on the [**EC-Council's website**](https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/), as well as other online resources. Practice exams will help you identify areas where you need to improve and get you accustomed to the format and style of the exam.
-- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.ch/ceh-practice-test)
+- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.com/ceh-practice-test)
### Join Study Groups
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md
index f1c70c2165acd..17acbb8c4c738 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md
@@ -63,7 +63,7 @@ ______
Die Cybersicherheit ist ein sich ständig weiterentwickelnder Bereich, und es ist für Fachleute in diesem Bereich von entscheidender Bedeutung, über die neuesten Trends und Bedrohungen auf dem Laufenden zu bleiben. Hier sind einige Möglichkeiten, um informiert zu bleiben:
-- **Blogs und Websites**: Folgen Sie seriösen Cybersicherheitsblogs und -webseiten wie [simeononsecurity.ch](https://www.simeononsecurity.ch/) die aufschlussreiche Artikel und Analysen zu aktuellen Cyber-Bedrohungen und -Trends enthalten.
+- **Blogs und Websites**: Folgen Sie seriösen Cybersicherheitsblogs und -webseiten wie [simeononsecurity.com](https://www.simeononsecurity.com/) die aufschlussreiche Artikel und Analysen zu aktuellen Cyber-Bedrohungen und -Trends enthalten.
- **Branchenkonferenzen und Veranstaltungen**: Besuchen Sie Konferenzen und Veranstaltungen zur Cybersicherheit, um von Branchenexperten zu lernen und sich mit Gleichgesinnten zu vernetzen.
- **Berufsverbände**: Treten Sie Berufsverbänden und -gemeinschaften wie der Information Systems Security Association (ISSA) oder dem International Information System Security Certification Consortium (ISC)² bei, die Ressourcen, Zertifizierungen und Networking-Möglichkeiten bieten.
- **Kontinuierliches Lernen**: Lernen Sie kontinuierlich durch Online-Kurse, Webinare und Zertifizierungsprogramme, um Ihre Kenntnisse und Fähigkeiten zu erweitern.
@@ -109,6 +109,6 @@ ______
## Referenzen:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md
index 806a5b7aeb069..69bdf97268a7b 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md
@@ -67,7 +67,7 @@ ______
Cybersecurity is an ever-evolving field, and staying updated with the latest trends and threats is crucial for professionals in this field. Here are some ways to stay informed:
-- **Blogs and Websites**: Follow reputable cybersecurity blogs and websites such as [simeononsecurity.ch](https://www.simeononsecurity.ch/) that provide insightful articles and analysis of recent cyber threats and trends.
+- **Blogs and Websites**: Follow reputable cybersecurity blogs and websites such as [simeononsecurity.com](https://www.simeononsecurity.com/) that provide insightful articles and analysis of recent cyber threats and trends.
- **Industry Conferences and Events**: Attend cybersecurity conferences and events to learn from industry experts and network with peers.
- **Professional Associations**: Join professional associations and communities such as the Information Systems Security Association (ISSA) or the International Information System Security Certification Consortium (ISC)², which offer resources, certifications, and networking opportunities.
- **Continuous Learning**: Engage in continuous learning through online courses, webinars, and certification programs to enhance your knowledge and skills.
@@ -113,6 +113,6 @@ ______
## References:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md
index 124c9f213ce7d..26939aa35fb42 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md
@@ -63,7 +63,7 @@ ______
La ciberseguridad es un campo en constante evolución, y mantenerse al día de las últimas tendencias y amenazas es crucial para los profesionales de este ámbito. He aquí algunas formas de mantenerse informado:
-- **Blogs y sitios web**: Siga blogs y sitios web de ciberseguridad de confianza como [simeononsecurity.ch](https://www.simeononsecurity.ch/) que ofrecen artículos y análisis perspicaces de las últimas ciberamenazas y tendencias.
+- **Blogs y sitios web**: Siga blogs y sitios web de ciberseguridad de confianza como [simeononsecurity.com](https://www.simeononsecurity.com/) que ofrecen artículos y análisis perspicaces de las últimas ciberamenazas y tendencias.
- Conferencias y eventos del sector**: Asista a conferencias y eventos de ciberseguridad para aprender de expertos de la industria y establecer contactos con colegas.
- Asociaciones profesionales**: Únase a asociaciones y comunidades profesionales como la Information Systems Security Association (ISSA) o el International Information System Security Certification Consortium (ISC)², que ofrecen recursos, certificaciones y oportunidades para establecer contactos.
- Aprendizaje continuo**: Participe en el aprendizaje continuo a través de cursos en línea, seminarios web y programas de certificación para mejorar sus conocimientos y habilidades.
@@ -109,6 +109,6 @@ ______
## Referencias:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md
index 6f20e8bcc83e8..e4802a9543cc1 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md
@@ -63,7 +63,7 @@ ______
La cybersécurité est un domaine en constante évolution, et il est essentiel pour les professionnels de ce secteur de se tenir au courant des dernières tendances et menaces. Voici quelques moyens de rester informé :
-- **Blogs et sites web** : Suivez des blogs et des sites web réputés sur la cybersécurité, tels que [simeononsecurity.ch](https://www.simeononsecurity.ch/) qui fournissent des articles et des analyses perspicaces sur les menaces et les tendances récentes dans le domaine de la cybernétique.
+- **Blogs et sites web** : Suivez des blogs et des sites web réputés sur la cybersécurité, tels que [simeononsecurity.com](https://www.simeononsecurity.com/) qui fournissent des articles et des analyses perspicaces sur les menaces et les tendances récentes dans le domaine de la cybernétique.
- Conférences et événements du secteur** : Participez à des conférences et à des événements sur la cybersécurité pour vous informer auprès d'experts du secteur et nouer des contacts avec vos pairs.
- Associations professionnelles** : Rejoignez des associations et des communautés professionnelles telles que l'Information Systems Security Association (ISSA) ou l'International Information System Security Certification Consortium (ISC)², qui offrent des ressources, des certifications et des possibilités de mise en réseau.
- Apprentissage continu** : Participez à la formation continue en suivant des cours en ligne, des webinaires et des programmes de certification afin d'améliorer vos connaissances et vos compétences.
@@ -109,6 +109,6 @@ ______
## Références :
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md
index b21ae7ef0358d..ce48002b503eb 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md
@@ -63,7 +63,7 @@ ______
La cybersecurity è un campo in continua evoluzione e rimanere aggiornati sulle ultime tendenze e minacce è fondamentale per i professionisti del settore. Ecco alcuni modi per rimanere informati:
-- **Blog e siti web**: Seguire blog e siti web affidabili sulla sicurezza informatica, come ad esempio [simeononsecurity.ch](https://www.simeononsecurity.ch/) che forniscono articoli e analisi approfondite sulle recenti minacce e tendenze informatiche.
+- **Blog e siti web**: Seguire blog e siti web affidabili sulla sicurezza informatica, come ad esempio [simeononsecurity.com](https://www.simeononsecurity.com/) che forniscono articoli e analisi approfondite sulle recenti minacce e tendenze informatiche.
- Conferenze ed eventi del settore**: Partecipare a conferenze ed eventi sulla sicurezza informatica per imparare dagli esperti del settore e fare rete con i colleghi.
- Associazioni professionali**: Iscriversi ad associazioni e comunità professionali come l'Information Systems Security Association (ISSA) o l'International Information System Security Certification Consortium (ISC)², che offrono risorse, certificazioni e opportunità di networking.
- Apprendimento continuo**: Impegnarsi nell'apprendimento continuo attraverso corsi online, webinar e programmi di certificazione per migliorare le proprie conoscenze e competenze.
@@ -109,6 +109,6 @@ ______
## Riferimenti:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md
index 69401b49c4fb4..3af30e28f8a93 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md
@@ -63,7 +63,7 @@ ______
サイバーセキュリティは日進月歩の分野であり、この分野の専門家にとって、最新のトレンドや脅威を常に把握することは極めて重要です。ここでは、情報収集を怠らないための方法をいくつかご紹介します:
-- ブログとWebサイト**:ブログやウェブサイト**:以下のような評判の良いサイバーセキュリティ関連のブログやウェブサイトをフォローする。 [simeononsecurity.ch](https://www.simeononsecurity.ch/)サイバー脅威やトレンドに関する洞察に満ちた記事と分析を提供する「Skype」。
+- ブログとWebサイト**:ブログやウェブサイト**:以下のような評判の良いサイバーセキュリティ関連のブログやウェブサイトをフォローする。 [simeononsecurity.com](https://www.simeononsecurity.com/)サイバー脅威やトレンドに関する洞察に満ちた記事と分析を提供する「Skype」。
- **業界のカンファレンスとイベント**:サイバーセキュリティに関するカンファレンスやイベントに参加し、業界の専門家から学び、同業者とのネットワークを構築する。
- 専門家集団**:情報システムセキュリティ協会(ISSA)や国際情報システムセキュリティ認証コンソーシアム(ISC)²など、リソース、認証、ネットワーキングの機会を提供する専門家団体やコミュニティに参加する。
- 継続的な学習**:オンラインコース、ウェビナー、認定プログラムを通じて継続的に学習し、知識とスキルを向上させる。
@@ -109,6 +109,6 @@ ______
## 参考文献
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md
index 1a218cbd9f483..e63027d0ce85b 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md
@@ -63,7 +63,7 @@ ______
Cyberbeveiliging is een vakgebied dat voortdurend in beweging is, en op de hoogte blijven van de nieuwste trends en bedreigingen is cruciaal voor professionals op dit gebied. Hier zijn enkele manieren om op de hoogte te blijven:
-- **Blogs en websites**: Volg gerenommeerde cyberbeveiligingsblogs en -websites zoals [simeononsecurity.ch](https://www.simeononsecurity.ch/) die inzichtelijke artikelen en analyses bieden over recente cyberbedreigingen en -trends.
+- **Blogs en websites**: Volg gerenommeerde cyberbeveiligingsblogs en -websites zoals [simeononsecurity.com](https://www.simeononsecurity.com/) die inzichtelijke artikelen en analyses bieden over recente cyberbedreigingen en -trends.
- **Industrieconferenties en evenementen**: Woon cyberbeveiligingsconferenties en -evenementen bij om te leren van industrie-experts en te netwerken met collega's.
- Professionele verenigingen**: Sluit u aan bij professionele verenigingen en gemeenschappen zoals de Information Systems Security Association (ISSA) of het International Information System Security Certification Consortium (ISC)², die hulpmiddelen, certificeringen en netwerkmogelijkheden bieden.
- **Doorlopend leren**: Doe aan permanente educatie via online cursussen, webinars en certificeringsprogramma's om uw kennis en vaardigheden te verbeteren.
@@ -109,6 +109,6 @@ ______
## Referenties:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md
index bea917d44178b..7d7b161c32e65 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md
@@ -63,7 +63,7 @@ ______
Cyberbezpieczeństwo to stale rozwijająca się dziedzina, a bycie na bieżąco z najnowszymi trendami i zagrożeniami ma kluczowe znaczenie dla profesjonalistów w tej dziedzinie. Oto kilka sposobów na bycie na bieżąco:
-- **Blogi i strony internetowe**: Śledź renomowane blogi i strony internetowe poświęcone cyberbezpieczeństwu, takie jak [simeononsecurity.ch](https://www.simeononsecurity.ch/) które dostarczają wnikliwych artykułów i analiz najnowszych zagrożeń i trendów cybernetycznych.
+- **Blogi i strony internetowe**: Śledź renomowane blogi i strony internetowe poświęcone cyberbezpieczeństwu, takie jak [simeononsecurity.com](https://www.simeononsecurity.com/) które dostarczają wnikliwych artykułów i analiz najnowszych zagrożeń i trendów cybernetycznych.
- **Konferencje i wydarzenia branżowe**: Bierz udział w konferencjach i wydarzeniach związanych z cyberbezpieczeństwem, aby uczyć się od ekspertów branżowych i nawiązywać kontakty z rówieśnikami.
- **Zrzeszenia zawodowe**: Dołącz do profesjonalnych stowarzyszeń i społeczności, takich jak Information Systems Security Association (ISSA) lub International Information System Security Certification Consortium (ISC)², które oferują zasoby, certyfikaty i możliwości nawiązywania kontaktów.
- **Ciągła nauka**: Zaangażuj się w ciągłe uczenie się poprzez kursy online, webinaria i programy certyfikacyjne, aby poszerzyć swoją wiedzę i umiejętności.
@@ -109,6 +109,6 @@ ______
## Referencje:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md
index e6a90fee28f4d..6b4c2be2f3f08 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md
@@ -75,7 +75,7 @@ ______
In conclusion, crafting an effective resume is crucial for cybersecurity, software development, and IT professionals looking to advance their careers. By tailoring your resume to the job description, showcasing your technical skills and achievements, emphasizing cybersecurity and privacy awareness, highlighting problem-solving abilities, maintaining clarity and conciseness, using action verbs and quantifiable results, and staying updated with industry trends, you can create a resume that stands out to potential employers.
-For more general tips on resume writing, you can also refer to [this article](https://simeononsecurity.ch/other/tips-for-writing-a-great-resume/) on simeononsecurity.ch, which provides valuable insights and and additional guidance.
+For more general tips on resume writing, you can also refer to [this article](https://simeononsecurity.com/other/tips-for-writing-a-great-resume/) on simeononsecurity.com, which provides valuable insights and and additional guidance.
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md
index 4b4d382a62fe1..de36b9888d6dd 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md
@@ -29,7 +29,7 @@ Experience and expertise are critical determinants of **cybersecurity analyst sa
{{< inarticle-dark >}}
### 2. Education and Certifications
-The level of education and relevant certifications also impact **cybersecurity analyst salaries**. A bachelor's degree in **computer science**, **cybersecurity**, or a related field is often the minimum requirement for entry-level positions. However, earning advanced degrees, such as a master's degree or a Ph.D., can provide a competitive edge and potentially lead to higher-paying positions. Additionally, certifications such as [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/), [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/), or [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can enhance an analyst's marketability and salary potential.
+The level of education and relevant certifications also impact **cybersecurity analyst salaries**. A bachelor's degree in **computer science**, **cybersecurity**, or a related field is often the minimum requirement for entry-level positions. However, earning advanced degrees, such as a master's degree or a Ph.D., can provide a competitive edge and potentially lead to higher-paying positions. Additionally, certifications such as [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/), [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/), or [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can enhance an analyst's marketability and salary potential.
### 3. Industry and Organization Size
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md
index 2c1c73576a3a0..9fa03338c9cb2 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) ist ein beliebter Online-Lernmarktplatz, der eine breite Palette von Cybersecurity-Kursen anbietet, die sowohl von Fachleuten aus der Branche als auch von unabhängigen Dozenten erstellt werden. Die große Auswahl an Udemy-Kursen deckt verschiedene Bereiche der Cybersicherheit ab und ermöglicht es den Lernenden, Kurse nach ihren Interessen und Fähigkeiten zu wählen.
-Erfahren Sie mehr über [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Erfahren Sie mehr über [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Empfohlene Bücher für Cybersecurity-Training
@@ -83,7 +83,7 @@ Neben Online-Programmen und Videokursen sind Bücher eine hervorragende Ressourc
Diese Bücher bieten vertieftes Wissen und praktische Einblicke in Themen der Cybersicherheit. Sie können als wertvolle Ressourcen zur Ergänzung von Online-Schulungen dienen und Ihr Verständnis für diesen Bereich erweitern.
-Erfahren Sie mehr über [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Erfahren Sie mehr über [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md
index 133365ef80a1d..be800c28c15e4 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) is a popular online marketplace for learning, offering a wide range of cybersecurity courses created by both industry professionals and independent instructors. Udemy's vast selection of courses covers various cybersecurity domains, allowing learners to choose courses based on their interests and skill levels.
-Learn about more [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources).
+Learn about more [online training platforms](https://simeononsecurity.com/recommendations/learning_resources).
## Recommended Books for Cybersecurity Training
@@ -83,7 +83,7 @@ In addition to online programs and video courses, books are an excellent resourc
These books offer in-depth knowledge and practical insights into cybersecurity topics. They can serve as valuable resources to complement online training and expand your understanding of the field.
-Learn about more [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books).
+Learn about more [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books).
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md
index 0e0d82b121802..8f720df5e8c8c 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) es un popular mercado en línea para el aprendizaje, que ofrece una amplia gama de cursos de ciberseguridad creados tanto por profesionales del sector como por instructores independientes. La amplia selección de cursos de Udemy abarca diversos ámbitos de la ciberseguridad, lo que permite a los alumnos elegir los cursos en función de sus intereses y niveles de habilidad.
-Más información [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Más información [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Libros recomendados para la formación en ciberseguridad
@@ -83,7 +83,7 @@ Además de los programas en línea y los cursos en vídeo, los libros son un rec
Estos libros ofrecen conocimientos profundos y perspectivas prácticas sobre temas de ciberseguridad. Pueden servir como valiosos recursos para complementar la formación en línea y ampliar sus conocimientos en este campo.
-Más información [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Más información [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md
index a8dbfc7f57df9..d989958933d02 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) Udemy est un marché en ligne populaire pour l'apprentissage, offrant un large éventail de cours de cybersécurité créés par des professionnels de l'industrie et des instructeurs indépendants. La vaste sélection de cours d'Udemy couvre divers domaines de la cybersécurité, ce qui permet aux apprenants de choisir des cours en fonction de leurs intérêts et de leurs niveaux de compétence.
-En savoir plus [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+En savoir plus [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Livres recommandés pour la formation à la cybersécurité
@@ -83,7 +83,7 @@ Outre les programmes en ligne et les cours vidéo, les livres constituent une ex
Ces ouvrages offrent des connaissances approfondies et des aperçus pratiques sur des sujets liés à la cybersécurité. Ils peuvent constituer des ressources précieuses pour compléter la formation en ligne et élargir votre compréhension du domaine.
-En savoir plus [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+En savoir plus [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md
index e70db849ff544..20e74885aca32 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) è un popolare mercato online per l'apprendimento, che offre un'ampia gamma di corsi di sicurezza informatica creati da professionisti del settore e da istruttori indipendenti. La vasta selezione di corsi di Udemy copre vari settori della sicurezza informatica, consentendo agli studenti di scegliere i corsi in base ai loro interessi e livelli di competenza.
-Per saperne di più [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Per saperne di più [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Libri consigliati per la formazione sulla sicurezza informatica
@@ -83,7 +83,7 @@ Oltre ai programmi online e ai videocorsi, i libri sono una risorsa eccellente p
Questi libri offrono conoscenze approfondite e spunti pratici sugli argomenti di cybersecurity. Possono servire come preziose risorse per integrare la formazione online e ampliare la comprensione del settore.
-Per saperne di più [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Per saperne di più [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md
index 6f3171657e48c..816ea10386585 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/)は、業界専門家と独立した講師の両方によって作成された幅広いサイバーセキュリティコースを提供する、人気のあるオンライン学習マーケットプレイスです。Udemyの膨大な数のコースは、様々なサイバーセキュリティ領域をカバーしており、学習者は自分の興味やスキルレベルに応じてコースを選択することができます。
-もっと詳しく知る [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+もっと詳しく知る [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## サイバーセキュリティ研修におすすめの書籍のご紹介です。
@@ -83,7 +83,7 @@ ______
これらの書籍は、サイバーセキュリティに関する深い知識と実践的な洞察力を提供します。オンライントレーニングを補完し、この分野への理解を深めるための貴重な資料となります。
-もっと詳しく知る [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+もっと詳しく知る [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md
index 6119adba8b540..ff7461cff0cad 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) is een populaire online marktplaats voor leren en biedt een breed scala aan cursussen op het gebied van cyberbeveiliging, gemaakt door zowel professionals uit de branche als onafhankelijke docenten. De uitgebreide selectie cursussen van Udemy omvat verschillende cyberbeveiligingsdomeinen, zodat leerlingen cursussen kunnen kiezen op basis van hun interesses en vaardigheidsniveaus.
-Meer informatie [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Meer informatie [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Aanbevolen boeken voor cyberbeveiligingstraining
@@ -83,7 +83,7 @@ Naast online programma's en videocursussen zijn boeken een uitstekende bron om u
Deze boeken bieden diepgaande kennis en praktische inzichten in onderwerpen op het gebied van cyberbeveiliging. Ze kunnen dienen als waardevolle bronnen om online training aan te vullen en je inzicht in het vakgebied te vergroten.
-Meer informatie [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Meer informatie [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md
index 605c40618fbc2..78e51992eef6a 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) to popularny internetowy rynek edukacyjny, oferujący szeroką gamę kursów z zakresu cyberbezpieczeństwa stworzonych zarówno przez profesjonalistów z branży, jak i niezależnych instruktorów. Szeroki wybór kursów Udemy obejmuje różne dziedziny cyberbezpieczeństwa, umożliwiając uczestnikom wybór kursów w oparciu o ich zainteresowania i poziom umiejętności.
-Dowiedz się więcej [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Dowiedz się więcej [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Zalecane książki do szkolenia w zakresie cyberbezpieczeństwa
@@ -83,7 +83,7 @@ Oprócz programów online i kursów wideo, książki są doskonałym źródłem
Książki te oferują dogłębną wiedzę i praktyczne spojrzenie na tematy związane z cyberbezpieczeństwem. Mogą one służyć jako cenne zasoby uzupełniające szkolenia online i poszerzające wiedzę w tej dziedzinie.
-Dowiedz się więcej [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Dowiedz się więcej [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md
index 3fc953fe98824..63b0e74afb07c 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md
@@ -24,23 +24,23 @@ Stellen Sie sich vor, Sie wachen eines Tages auf und stellen fest, dass alle Ihr
Cybersicherheitsexperten sind so etwas wie die Superhelden der digitalen Welt. Sie haben besondere Fähigkeiten, um unsere digitalen Informationen vor den Bösewichten zu schützen. Aber nicht alle Cybersicherheitsexperten machen das Gleiche. Es ist wie bei Ärzten: Sie haben alle eine gemeinsame Ausbildung, spezialisieren sich dann aber auf verschiedene Bereiche. Einige Fachleute für Cybersicherheit werden zu Experten für das Auffinden und Beheben von Schwachstellen in Computersystemen, während andere sich auf die Entwicklung starker Verteidigungsmaßnahmen konzentrieren, um die Bösewichte fernzuhalten. Sie arbeiten in Teams und lernen und verbessern ständig ihre Fähigkeiten, um den Bösewichten einen Schritt voraus zu sein.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Auch wenn Sie kein Cybersecurity-Profi werden, können Sie dennoch einiges tun, um sich und Ihre Familie vor den bösen Jungs im Internet zu schützen. Lernen Sie einige grundlegende persönliche Sicherheitspraktiken kennen, die Ihnen helfen können, sich zu schützen:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Beim Phishing versuchen die Bösewichte, Sie mit einem Trick dazu zu bringen, ihnen Ihre persönlichen Daten wie Passwörter oder Kreditkartennummern zu geben. Sie schicken Ihnen möglicherweise E-Mails oder Nachrichten, die echt aussehen, aber in Wirklichkeit gefälscht sind. Sie wollen, dass Sie auf Links klicken, die Sie zu gefälschten Websites führen, wo sie Ihre Daten stehlen können. Seien Sie also vorsichtig und klicken Sie nicht auf verdächtige Links. Wenn etwas seltsam aussieht oder zu gut ist, um wahr zu sein, handelt es sich wahrscheinlich um einen Betrüger, der versucht, Sie auszutricksen.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
So wie Sie neue Spielzeuge oder Kleidung bekommen, brauchen auch Ihre Geräte, wie Ihr Telefon oder Ihr Computer, Updates. Mit diesen Updates werden Probleme oder Sicherheitslücken behoben, die Bösewichte nutzen könnten, um in Ihre Geräte einzudringen. Installieren Sie also unbedingt die Updates, wenn Sie dazu aufgefordert werden. Das ist so, als würden Sie ein Schloss an Ihre Schlafzimmertür machen, um die bösen Jungs draußen zu halten.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Ein sicheres Passwort ist wie ein Geheimcode, den nur Sie kennen. Es sollte lang und komplex sein, mit einer Mischung aus Buchstaben, Zahlen und Sonderzeichen. Vermeiden Sie gebräuchliche Wörter oder persönliche Informationen, die jemand leicht erraten könnte. Es ist außerdem wichtig, für verschiedene Websites oder Konten unterschiedliche Passwörter zu verwenden. Wenn ein Kennwort gehackt wird, können die Bösewichte nicht auf alle anderen Konten zugreifen. Wenn es schwierig ist, sich all diese Passwörter zu merken, können Sie einen Passwortmanager verwenden, um Ihre Passwörter sicher zu speichern und zu verwalten.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Die Multi-Faktor-Authentifizierung (MFA) bietet eine zusätzliche Sicherheitsebene für Ihre Online-Konten. Das ist so, als hätten Sie zwei Schlösser an Ihrer Tür. Mit MFA müssen Sie neben Ihrem Passwort zusätzliche Informationen angeben, z. B. einen speziellen Code, der an Ihr Telefon gesendet wird, um auf Ihr Konto zuzugreifen. Das macht es für die Bösewichte viel schwieriger, sich Zugang zu verschaffen, selbst wenn sie Ihr Passwort kennen. Wann immer eine Website oder App MFA anbietet, sollten Sie diese Funktion aktivieren, um zusätzlichen Schutz zu erhalten.
@@ -52,8 +52,8 @@ Cybersicherheit ist wie ein Superheld, der unsere digitale Welt vor den Bösewic
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md
index 5135a46788691..e235ebea52772 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md
@@ -25,23 +25,23 @@ Imagine waking up one day and finding out that all your messages, photos, and fi
Cybersecurity professionals are like the superheroes of the digital world. They have special skills to protect our digital information from the bad guys. But not all cybersecurity professionals do the same thing. It's like doctors: they all have a common education but then specialize in different areas. Some cybersecurity professionals become experts in finding and fixing vulnerabilities in computer systems, while others focus on creating strong defenses to keep the bad guys out. They work in teams and constantly learn and improve their skills to stay ahead of the bad guys.
{{< inarticle-dark >}}
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Even if you don't become a cybersecurity professional, you can still do some things to protect yourself and your family from the bad guys on the internet. Let's learn some basic personal security hygiene practices that can help keep you safe:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing is when the bad guys try to trick you into giving them your personal information, like passwords or credit card numbers. They may send you emails or messages that look real but are actually fake. They want you to click on links that take you to fake websites where they can steal your information. So, be careful and don't click on any suspicious links. If something looks strange or too good to be true, it's probably a bad guy trying to trick you.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Just like you get new toys or clothes, your devices, like your phone or computer, also need updates. These updates help fix any problems or security flaws that the bad guys might use to break into your devices. So, make sure to install the updates when you're prompted to do so. It's like putting a lock on your bedroom door to keep the bad guys out.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
A strong password is like a secret code that only you know. It should be long and complex, with a mix of letters, numbers, and special characters. Avoid using common words or personal information that someone could easily guess. It's also important to use different passwords for different websites or accounts. This way, if one password gets hacked, the bad guys won't be able to access all your other accounts. If remembering all those passwords sounds difficult, you can use a password manager to securely store and manage your passwords.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Multi-Factor Authentication (MFA) adds an extra layer of security to your online accounts. It's like having double locks on your door. With MFA, you need to provide additional information, like a special code sent to your phone, along with your password to access your account. This makes it much harder for the bad guys to get in, even if they know your password. So, whenever a website or app offers MFA, make sure to turn it on for added protection.
@@ -54,8 +54,8 @@ Cybersecurity is like a superhero that protects our digital world from the bad g
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md
index a1e138e608e84..1f3beac2e0e2d 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md
@@ -24,23 +24,23 @@ Imagine despertarse un día y descubrir que todos sus mensajes, fotos y archivos
Los profesionales de la ciberseguridad son como los superhéroes del mundo digital. Tienen habilidades especiales para proteger nuestra información digital de los malos. Pero no todos los profesionales de la ciberseguridad hacen lo mismo. Es como los médicos: todos tienen una formación común, pero luego se especializan en distintas áreas. Algunos profesionales de la ciberseguridad se convierten en expertos en encontrar y corregir vulnerabilidades en los sistemas informáticos, mientras que otros se centran en crear defensas sólidas para mantener alejados a los malos. Trabajan en equipo y aprenden y mejoran constantemente sus habilidades para ir por delante de los malos.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Aunque no te conviertas en un profesional de la ciberseguridad, puedes hacer algunas cosas para protegerte a ti y a tu familia de los malos de Internet. Conozcamos algunas prácticas básicas de higiene de seguridad personal que pueden ayudarle a mantenerse a salvo:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing es cuando los malos intentan engañarte para que les des tu información personal, como contraseñas o números de tarjetas de crédito. Pueden enviarle correos electrónicos o mensajes que parecen reales, pero que en realidad son falsos. Quieren que hagas clic en enlaces que te llevan a sitios web falsos donde pueden robar tu información. Así que tenga cuidado y no haga clic en ningún enlace sospechoso. Si algo parece extraño o demasiado bueno para ser verdad, probablemente sea un malhechor intentando engañarte.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Al igual que los juguetes o la ropa, los dispositivos, como el teléfono o el ordenador, también necesitan actualizaciones. Estas actualizaciones ayudan a solucionar cualquier problema o fallo de seguridad que los malos puedan utilizar para entrar en tus dispositivos. Así que asegúrate de instalar las actualizaciones cuando te lo pidan. Es como poner una cerradura en la puerta de tu habitación para evitar que entren los malos.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Una contraseña segura es como un código secreto que sólo tú conoces. Debe ser larga y compleja, con una mezcla de letras, números y caracteres especiales. Evite utilizar palabras comunes o información personal que alguien pueda adivinar fácilmente. También es importante utilizar contraseñas distintas para sitios web o cuentas diferentes. De este modo, si piratean una contraseña, los delincuentes no podrán acceder al resto de tus cuentas. Si recordar todas esas contraseñas te resulta difícil, puedes utilizar un gestor de contraseñas para almacenarlas y gestionarlas de forma segura.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
La autenticación multifactor (AMF) añade una capa adicional de seguridad a sus cuentas en línea. Es como tener doble cerradura en la puerta. Con la AMF, para acceder a tu cuenta tienes que proporcionar información adicional, como un código especial enviado a tu teléfono, junto con tu contraseña. Esto hace que sea mucho más difícil para los malos entrar, incluso si conocen tu contraseña. Así que, siempre que un sitio web o una aplicación ofrezca MFA, asegúrate de activarlo para una mayor protección.
@@ -52,8 +52,8 @@ La ciberseguridad es como un superhéroe que protege nuestro mundo digital de lo
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md
index 65d0be28985b1..4749e9b1e6632 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md
@@ -24,23 +24,23 @@ Imaginez que vous vous réveillez un jour et que vous découvrez que tous vos me
Les professionnels de la cybersécurité sont en quelque sorte les super-héros du monde numérique. Ils possèdent des compétences particulières pour protéger nos informations numériques contre les malfaiteurs. Mais tous les professionnels de la cybersécurité ne font pas la même chose. C'est comme les médecins : ils ont tous une formation commune, mais se spécialisent ensuite dans des domaines différents. Certains professionnels de la cybersécurité deviennent experts dans la recherche et la correction des failles des systèmes informatiques, tandis que d'autres se concentrent sur la création de défenses solides pour empêcher les malfaiteurs d'entrer. Ils travaillent en équipe et ne cessent d'apprendre et d'améliorer leurs compétences pour garder une longueur d'avance sur les malfaiteurs.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Même si vous ne devenez pas un professionnel de la cybersécurité, vous pouvez prendre certaines mesures pour vous protéger, vous et votre famille, des méchants sur Internet. Voici quelques règles d'hygiène de base en matière de sécurité personnelle qui peuvent vous aider à rester en sécurité :
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
On parle de phishing lorsque des personnes mal intentionnées tentent de vous inciter à leur fournir des informations personnelles, comme des mots de passe ou des numéros de carte de crédit. Ils peuvent vous envoyer des courriels ou des messages qui semblent réels mais qui sont en fait faux. Ils veulent que vous cliquiez sur des liens qui vous conduisent à de faux sites web où ils peuvent voler vos informations. Soyez donc prudent et ne cliquez sur aucun lien suspect. Si quelque chose vous semble étrange ou trop beau pour être vrai, il s'agit probablement d'une personne malveillante qui essaie de vous piéger.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Tout comme vous recevez de nouveaux jouets ou vêtements, vos appareils, comme votre téléphone ou votre ordinateur, ont également besoin de mises à jour. Ces mises à jour permettent de résoudre les problèmes ou les failles de sécurité que les malfaiteurs pourraient utiliser pour s'introduire dans vos appareils. Veillez donc à installer les mises à jour lorsque vous y êtes invité. C'est comme si vous mettiez un verrou sur la porte de votre chambre pour empêcher les malfaiteurs d'entrer.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Un mot de passe fort est comme un code secret que vous êtes le seul à connaître. Il doit être long et complexe, avec un mélange de lettres, de chiffres et de caractères spéciaux. Évitez d'utiliser des mots courants ou des informations personnelles que quelqu'un pourrait facilement deviner. Il est également important d'utiliser des mots de passe différents pour des sites web ou des comptes différents. Ainsi, si un mot de passe est piraté, les malfaiteurs ne pourront pas accéder à tous vos autres comptes. S'il vous semble difficile de vous souvenir de tous ces mots de passe, vous pouvez utiliser un gestionnaire de mots de passe pour stocker et gérer vos mots de passe en toute sécurité.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
L'authentification multifactorielle (AMF) ajoute une couche de sécurité supplémentaire à vos comptes en ligne. C'est comme avoir une double serrure sur votre porte. Avec l'AFM, vous devez fournir des informations supplémentaires, comme un code spécial envoyé sur votre téléphone, en plus de votre mot de passe pour accéder à votre compte. Il est donc beaucoup plus difficile pour les malfaiteurs d'accéder à votre compte, même s'ils connaissent votre mot de passe. Par conséquent, chaque fois qu'un site web ou une application propose l'option MFA, veillez à l'activer pour une protection accrue.
@@ -52,8 +52,8 @@ La cybersécurité est comme un super-héros qui protège notre monde numérique
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md
index 3770a056f512c..7833b590af3d8 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md
@@ -24,23 +24,23 @@ Immaginate di svegliarvi un giorno e di scoprire che tutti i vostri messaggi, fo
I professionisti della sicurezza informatica sono come i supereroi del mondo digitale. Hanno competenze speciali per proteggere le nostre informazioni digitali dai malintenzionati. Ma non tutti i professionisti della sicurezza informatica fanno la stessa cosa. È come per i medici: hanno tutti una formazione comune, ma poi si specializzano in aree diverse. Alcuni professionisti della sicurezza informatica diventano esperti nel trovare e risolvere le vulnerabilità dei sistemi informatici, mentre altri si concentrano sulla creazione di difese forti per tenere lontani i malintenzionati. Lavorano in team e imparano e migliorano costantemente le loro competenze per stare davanti ai malintenzionati.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Anche se non diventate professionisti della sicurezza informatica, potete comunque fare qualcosa per proteggere voi stessi e la vostra famiglia dai malintenzionati di Internet. Scopriamo alcune pratiche di base per l'igiene della sicurezza personale che possono aiutarvi a stare al sicuro:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Il phishing è quando i malintenzionati cercano di indurvi a fornire loro le vostre informazioni personali, come password o numeri di carta di credito. Possono inviarvi e-mail o messaggi che sembrano reali ma in realtà sono falsi. Vogliono che clicchiate su link che vi portano a siti web falsi dove possono rubare le vostre informazioni. Quindi, fate attenzione e non cliccate su nessun link sospetto. Se qualcosa sembra strano o troppo bello per essere vero, probabilmente si tratta di un malintenzionato che sta cercando di ingannarvi.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Proprio come i giocattoli o i vestiti nuovi, anche i dispositivi, come il telefono o il computer, hanno bisogno di aggiornamenti. Questi aggiornamenti aiutano a risolvere eventuali problemi o falle di sicurezza che i malintenzionati potrebbero utilizzare per introdursi nei vostri dispositivi. Assicuratevi quindi di installare gli aggiornamenti quando vi viene richiesto. È come mettere un lucchetto alla porta della camera da letto per tenere lontani i malintenzionati.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Una password forte è come un codice segreto che solo voi conoscete. Deve essere lunga e complessa, con un mix di lettere, numeri e caratteri speciali. Evitate di usare parole comuni o informazioni personali che qualcuno potrebbe facilmente indovinare. È anche importante utilizzare password diverse per siti web o account diversi. In questo modo, se una password viene violata, i malintenzionati non potranno accedere a tutti gli altri account. Se ricordare tutte le password sembra difficile, potete utilizzare un gestore di password per memorizzare e gestire in modo sicuro le vostre password.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
L'autenticazione a più fattori (MFA) aggiunge un ulteriore livello di sicurezza ai vostri account online. È come avere una doppia serratura alla porta. Con l'MFA, per accedere al vostro account dovete fornire informazioni aggiuntive, come un codice speciale inviato al vostro telefono, insieme alla password. In questo modo è molto più difficile per i malintenzionati entrare, anche se conoscono la password. Quindi, ogni volta che un sito web o un'app offrono l'MFA, assicuratevi di attivarlo per una maggiore protezione.
@@ -52,8 +52,8 @@ La sicurezza informatica è come un supereroe che protegge il nostro mondo digit
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md
index 774d94e7fef21..0dc5ce3c2f428 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md
@@ -24,23 +24,23 @@ coverCaption: ""
サイバーセキュリティの専門家は、デジタル世界のスーパーヒーローのような存在です。彼らは、私たちのデジタル情報を悪者から守る特別なスキルを持っています。しかし、すべてのサイバーセキュリティの専門家が同じことをするわけではありません。医者と同じで、共通の教育を受けた後、異なる分野に特化するのです。あるサイバーセキュリティの専門家は、コンピュータシステムの脆弱性を見つけて修正する専門家になり、またある専門家は、悪者を排除するための強力な防御を作ることに専念する。彼らはチームで仕事をし、常に学び、スキルを向上させ、悪者の前に立ちはだかるのです。
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
サイバーセキュリティの専門家にならなくても、インターネット上の悪者から自分と家族を守るためにできることがあります。あなたの安全を守るために役立つ、基本的な個人のセキュリティ衛生習慣を学びましょう:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
フィッシングとは、悪者があなたを騙して、パスワードやクレジットカード番号などの個人情報を与えようとすることです。フィッシングは、本物に見えるが実は偽物であるメールやメッセージを送ってくることがあります。フィッシング業者は、あなたの情報を盗むために、偽のウェブサイトへ誘導するリンクをクリックさせようとします。だから、気をつけて、怪しいリンクはクリックしないようにしましょう。もし、何かが奇妙に見えたり、あまりにも真実味がない場合は、おそらくあなたを騙そうとしている悪者でしょう。
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
おもちゃや洋服が新しくなるように、携帯電話やパソコンなどのデバイスもアップデートが必要です。これらのアップデートは、悪者があなたのデバイスに侵入するために使用するかもしれない問題やセキュリティ上の欠陥を修正するのに役立ちます。だから、アップデートをインストールするように指示されたら、必ずインストールしてください。これは、寝室のドアに鍵をかけて悪者を排除するようなものです。
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
強力なパスワードは、あなただけが知っている秘密の暗号のようなものです。文字、数字、特殊文字を組み合わせて、長く複雑なものにする必要があります。誰かが簡単に推測できるような一般的な言葉や個人情報を使うのは避けましょう。また、ウェブサイトやアカウントごとに異なるパスワードを使用することも重要です。そうすれば、1つのパスワードがハッキングされても、悪者はあなたの他のすべてのアカウントにアクセスすることができません。パスワードを覚えるのが大変そうなら、パスワードマネージャーを使って、パスワードを安全に保存・管理することもできます。
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
多要素認証(MFA)は、あなたのオンラインアカウントにさらなるセキュリティ層を追加します。これは、ドアに二重ロックをかけるようなものです。MFAでは、アカウントにアクセスするために、パスワードと一緒に、携帯電話に送信される特別なコードのような追加情報を提供する必要があります。これによって、たとえパスワードを知っていたとしても、悪者が侵入するのはずっと難しくなります。ですから、ウェブサイトやアプリがMFAを提供している場合は、必ずMFAをオンにして、保護を強化するようにしましょう。
@@ -52,8 +52,8 @@ coverCaption: ""
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md
index 3994a13a56d1f..d84e46e013faa 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md
@@ -24,23 +24,23 @@ Stel je voor dat je op een dag wakker wordt en ontdekt dat al je berichten, foto
Cyberbeveiligingsprofessionals zijn als de superhelden van de digitale wereld. Ze hebben speciale vaardigheden om onze digitale informatie te beschermen tegen de slechteriken. Maar niet alle cyberbeveiligingsprofessionals doen hetzelfde. Het is net als bij artsen: ze hebben allemaal een gemeenschappelijke opleiding, maar specialiseren zich vervolgens in verschillende gebieden. Sommige cyberbeveiligingsprofessionals worden experts in het vinden en repareren van zwakke plekken in computersystemen, terwijl anderen zich richten op het creëren van een sterke verdediging om de slechteriken buiten te houden. Ze werken in teams en leren en verbeteren hun vaardigheden voortdurend om de slechteriken voor te blijven.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Zelfs als je geen cyberbeveiligingsprofessional wordt, kun je nog steeds een aantal dingen doen om jezelf en je familie te beschermen tegen de slechteriken op internet. Laten we eens kijken naar een aantal basispraktijken voor persoonlijke veiligheidshygiëne die kunnen helpen om je veilig te houden:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing is wanneer de slechteriken je proberen te verleiden tot het geven van persoonlijke informatie, zoals wachtwoorden of creditcardnummers. Ze kunnen je e-mails of berichten sturen die er echt uitzien, maar eigenlijk nep zijn. Ze willen dat je op links klikt die je naar valse websites brengen waar ze je gegevens kunnen stelen. Wees dus voorzichtig en klik niet op verdachte links. Als iets er vreemd uitziet of te mooi is om waar te zijn, is het waarschijnlijk een slechterik die je probeert te misleiden.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Net zoals je nieuw speelgoed of nieuwe kleren krijgt, hebben je apparaten, zoals je telefoon of computer, ook updates nodig. Deze updates helpen bij het oplossen van problemen of beveiligingslekken die de slechteriken kunnen gebruiken om in te breken op je apparaten. Zorg er dus voor dat je de updates installeert wanneer daarom wordt gevraagd. Het is alsof je een slot op je slaapkamerdeur doet om de slechteriken buiten te houden.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Een sterk wachtwoord is als een geheime code die alleen jij kent. Het moet lang en complex zijn, met een mix van letters, cijfers en speciale tekens. Vermijd het gebruik van gewone woorden of persoonlijke informatie die iemand makkelijk kan raden. Het is ook belangrijk om verschillende wachtwoorden te gebruiken voor verschillende websites of accounts. Op deze manier, als één wachtwoord wordt gekraakt, hebben de slechteriken geen toegang tot al je andere accounts. Als het onthouden van al die wachtwoorden moeilijk klinkt, kun je een wachtwoordmanager gebruiken om je wachtwoorden veilig op te slaan en te beheren.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Multi-Factor Authenticatie (MFA) voegt een extra beveiligingslaag toe aan je online accounts. Het is alsof je dubbele sloten op je deur hebt. Met MFA moet je extra informatie opgeven, zoals een speciale code die naar je telefoon wordt gestuurd, samen met je wachtwoord om toegang te krijgen tot je account. Dit maakt het veel moeilijker voor de slechteriken om binnen te komen, zelfs als ze je wachtwoord weten. Dus als een website of app MFA aanbiedt, zorg er dan voor dat je het inschakelt voor extra bescherming.
@@ -52,8 +52,8 @@ Cyberbeveiliging is als een superheld die onze digitale wereld beschermt tegen d
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md
index 452ee427e0d86..3e889a3cd5b23 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md
@@ -24,23 +24,23 @@ Wyobraź sobie, że pewnego dnia budzisz się i odkrywasz, że wszystkie twoje w
Specjaliści ds. cyberbezpieczeństwa są jak superbohaterowie cyfrowego świata. Posiadają specjalne umiejętności, aby chronić nasze cyfrowe informacje przed złymi ludźmi. Ale nie wszyscy specjaliści ds. cyberbezpieczeństwa robią to samo. To jak lekarze: wszyscy mają wspólne wykształcenie, ale specjalizują się w różnych dziedzinach. Niektórzy specjaliści ds. cyberbezpieczeństwa stają się ekspertami w znajdowaniu i naprawianiu luk w systemach komputerowych, podczas gdy inni koncentrują się na tworzeniu silnej obrony, aby powstrzymać złoczyńców. Pracują w zespołach i stale uczą się i doskonalą swoje umiejętności, aby wyprzedzić złoczyńców.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Nawet jeśli nie zostaniesz specjalistą ds. cyberbezpieczeństwa, nadal możesz zrobić kilka rzeczy, aby chronić siebie i swoją rodzinę przed złymi ludźmi w Internecie. Zapoznajmy się z kilkoma podstawowymi praktykami higieny osobistej, które mogą pomóc w zapewnieniu bezpieczeństwa:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing ma miejsce wtedy, gdy przestępcy próbują nakłonić użytkownika do podania danych osobowych, takich jak hasła lub numery kart kredytowych. Mogą wysyłać e-maile lub wiadomości, które wyglądają na prawdziwe, ale w rzeczywistości są fałszywe. Chcą, abyś kliknął na linki, które prowadzą do fałszywych stron internetowych, gdzie mogą ukraść twoje informacje. Bądź więc ostrożny i nie klikaj żadnych podejrzanych linków. Jeśli coś wygląda dziwnie lub zbyt dobrze, by mogło być prawdziwe, prawdopodobnie jest to oszustwo.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Podobnie jak nowe zabawki czy ubrania, urządzenia takie jak telefon czy komputer również wymagają aktualizacji. Aktualizacje te pomagają naprawić wszelkie problemy lub luki w zabezpieczeniach, które złoczyńcy mogą wykorzystać do włamania się do urządzeń. Upewnij się więc, że instalujesz aktualizacje, gdy zostaniesz o to poproszony. To jak założenie zamka na drzwiach sypialni, aby uniemożliwić złoczyńcom dostęp.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Silne hasło jest jak tajny kod, który znasz tylko Ty. Powinno być długie i złożone, z kombinacją liter, cyfr i znaków specjalnych. Unikaj używania popularnych słów lub danych osobowych, które ktoś mógłby łatwo odgadnąć. Ważne jest również, aby używać różnych haseł do różnych witryn lub kont. W ten sposób, jeśli jedno hasło zostanie zhakowane, złoczyńcy nie będą mogli uzyskać dostępu do wszystkich innych kont. Jeśli zapamiętanie wszystkich tych haseł wydaje się trudne, możesz użyć menedżera haseł, aby bezpiecznie przechowywać hasła i zarządzać nimi.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Uwierzytelnianie wieloskładnikowe (MFA) dodaje dodatkową warstwę zabezpieczeń do kont online. To jak podwójne zamki w drzwiach. Dzięki MFA musisz podać dodatkowe informacje, takie jak specjalny kod wysłany na Twój telefon, wraz z hasłem, aby uzyskać dostęp do konta. To znacznie utrudnia złoczyńcom dostęp do konta, nawet jeśli znają oni hasło. Tak więc, za każdym razem, gdy witryna lub aplikacja oferuje MFA, pamiętaj, aby ją włączyć w celu dodatkowej ochrony.
@@ -52,8 +52,8 @@ Cyberbezpieczeństwo jest jak superbohater, który chroni nasz cyfrowy świat pr
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md
index 3931e4d676500..a5806134b12fb 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md
@@ -24,15 +24,15 @@ In den letzten Jahren ist die Cybersicherheit zu einem wichtigen Aspekt unseres
Bevor Sie in die Welt der Cybersicherheit eintauchen, ist es wichtig, ein solides Fundament an Wissen zu schaffen. Hier sind einige wichtige Bereiche, auf die Sie sich konzentrieren sollten:
-1. **Netzwerke**: Das Verstehen der Grundlagen der Netzwerktechnik ist für die Cybersicherheit von entscheidender Bedeutung. Machen Sie sich mit Netzwerkprotokollen, IP-Adressierung, Routing und [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Ziehen Sie in Erwägung, eine Zertifizierung wie CompTIA Network+ zu erwerben, um Ihre Netzwerkkenntnisse zu bestätigen.
+1. **Netzwerke**: Das Verstehen der Grundlagen der Netzwerktechnik ist für die Cybersicherheit von entscheidender Bedeutung. Machen Sie sich mit Netzwerkprotokollen, IP-Adressierung, Routing und [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Ziehen Sie in Erwägung, eine Zertifizierung wie CompTIA Network+ zu erwerben, um Ihre Netzwerkkenntnisse zu bestätigen.
2. **Betriebssysteme**: Erwerben Sie Kenntnisse in den Betriebssystemen Linux und Windows. Lernen Sie, wie man in der Befehlszeile navigiert, Systemeinstellungen konfiguriert und Benutzerkonten verwaltet. Die Zertifizierungen CompTIA A+ und Linux+ sind ausgezeichnete Ausgangspunkte, um Ihr Verständnis von Betriebssystemen zu verbessern.
3. **Grundlegende Konzepte der Informatik**: Erwerben Sie ein grundlegendes Verständnis für die Prinzipien der Informatik, einschließlich Algorithmen, Datenstrukturen und Programmiersprachen. Dieses Wissen wird Ihnen helfen, Schwachstellen zu analysieren und sichere Softwareanwendungen zu entwickeln.
-4. **Kodierfähigkeiten**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) kann bei der Automatisierung von Sicherheitsaufgaben von Vorteil sein.
+4. **Kodierfähigkeiten**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) kann bei der Automatisierung von Sicherheitsaufgaben von Vorteil sein.
-5. **Unternehmenssystemverwaltung**: Wenn Sie Erfahrungen in der Verwaltung von Unternehmenssystemen gesammelt haben, erhalten Sie Einblicke in die Verwaltung komplexer IT-Infrastrukturen. Machen Sie sich vertraut mit Active Directory, Gruppenrichtlinien und [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Unternehmenssystemverwaltung**: Wenn Sie Erfahrungen in der Verwaltung von Unternehmenssystemen gesammelt haben, erhalten Sie Einblicke in die Verwaltung komplexer IT-Infrastrukturen. Machen Sie sich vertraut mit Active Directory, Gruppenrichtlinien und [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Cybersecurity-Domänen erforschen
@@ -40,7 +40,7 @@ Die Cybersicherheit umfasst verschiedene Bereiche, die jeweils ihren eigenen Sch
1. **Blaues Team**: Fachleute des Blue Teams konzentrieren sich auf die Verteidigung von Systemen und Netzwerken gegen Cyber-Bedrohungen. Sie entwerfen und implementieren Sicherheitsmaßnahmen, überwachen den Netzwerkverkehr und reagieren auf Vorfälle. Sie erwerben Kenntnisse über Sicherheitstools, Technologien und bewährte Verfahren für eine wirksame Verteidigung.
-2. **Red Team**: Red Team-Profis, die auch als ethische Hacker bezeichnet werden, sind auf die Bewertung von Systemschwachstellen durch simulierte Angriffe spezialisiert. Sie ermitteln Schwachstellen in Sicherheitssystemen, führen Penetrationstests durch und helfen Unternehmen bei der Stärkung ihrer Verteidigungsmaßnahmen. Entwickeln Sie praktische Fertigkeiten in ethischen Hacking-Techniken und machen Sie sich mit Tools wie [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: Red Team-Profis, die auch als ethische Hacker bezeichnet werden, sind auf die Bewertung von Systemschwachstellen durch simulierte Angriffe spezialisiert. Sie ermitteln Schwachstellen in Sicherheitssystemen, führen Penetrationstests durch und helfen Unternehmen bei der Stärkung ihrer Verteidigungsmaßnahmen. Entwickeln Sie praktische Fertigkeiten in ethischen Hacking-Techniken und machen Sie sich mit Tools wie [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Lila Team**: Das violette Team kombiniert Elemente des blauen und des roten Teams. Sie arbeiten zusammen, um die allgemeine Sicherheitslage zu verbessern, indem sie realistische Angriffsszenarien simulieren, Verteidigungsmaßnahmen bewerten und Erkenntnisse austauschen. Diese Rolle erfordert die Beherrschung sowohl defensiver als auch offensiver Techniken.
@@ -48,9 +48,9 @@ Die Cybersicherheit umfasst verschiedene Bereiche, die jeweils ihren eigenen Sch
Zertifizierungen sind zwar nicht obligatorisch, können aber Ihre Beschäftigungsfähigkeit erheblich verbessern und Ihr Engagement in diesem Bereich demonstrieren. Erwägen Sie, die folgenden Zertifizierungen anzustreben:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Diese Einstiegszertifizierung bestätigt Ihr Verständnis von Sicherheitskonzepten, Netzwerksicherheit und Sicherheitspraktiken.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Diese Zertifizierung konzentriert sich auf ethische Hacking-Techniken und -Methoden, die Sie in die Lage versetzen, Schwachstellen zu bewerten und zu entschärfen.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP ist eine weltweit anerkannte Zertifizierung, die Ihr Fachwissen in verschiedenen Bereichen der Sicherheit bestätigt.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Diese Einstiegszertifizierung bestätigt Ihr Verständnis von Sicherheitskonzepten, Netzwerksicherheit und Sicherheitspraktiken.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Diese Zertifizierung konzentriert sich auf ethische Hacking-Techniken und -Methoden, die Sie in die Lage versetzen, Schwachstellen zu bewerten und zu entschärfen.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP ist eine weltweit anerkannte Zertifizierung, die Ihr Fachwissen in verschiedenen Bereichen der Sicherheit bestätigt.
Im Bereich der Cybersicherheit ist es wichtig, sich ständig weiterzubilden und über die neuesten Trends, Tools und Techniken auf dem Laufenden zu bleiben. Verfolgen Sie Branchenblogs, nehmen Sie an Online-Communities teil und besuchen Sie Cybersecurity-Konferenzen, um Ihr Wissen zu erweitern und sich mit Fachleuten zu vernetzen.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md
index 55022f1b906c1..baf481e387e4b 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md
@@ -26,15 +26,15 @@ In recent years, cybersecurity has become a critical aspect of our digital lives
Before diving into the world of cybersecurity, it's important to lay a solid foundation of knowledge. Here are some essential areas to focus on:
-1. **Networking**: Understanding the fundamentals of networking is crucial in cybersecurity. Familiarize yourself with network protocols, IP addressing, routing, and [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/). Consider obtaining a certification such as CompTIA Network+ to validate your networking knowledge.
+1. **Networking**: Understanding the fundamentals of networking is crucial in cybersecurity. Familiarize yourself with network protocols, IP addressing, routing, and [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/). Consider obtaining a certification such as CompTIA Network+ to validate your networking knowledge.
2. **Operating Systems**: Gain proficiency in both Linux and Windows operating systems. Learn how to navigate the command line, configure system settings, and manage user accounts. CompTIA A+ and Linux+ certifications are excellent starting points to enhance your understanding of operating systems.
3. **Basic Computer Science Concepts**: Acquire a basic understanding of computer science principles, including algorithms, data structures, and programming languages. This knowledge will help you analyze vulnerabilities and develop secure software applications.
-4. **Coding Skills**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) can be advantageous in automating security tasks.
+4. **Coding Skills**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) can be advantageous in automating security tasks.
-5. **Enterprise System Administration**: Gaining experience in enterprise system administration will provide you with insights into managing complex IT infrastructures. Familiarize yourself with Active Directory, Group Policy, and [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/).
+5. **Enterprise System Administration**: Gaining experience in enterprise system administration will provide you with insights into managing complex IT infrastructures. Familiarize yourself with Active Directory, Group Policy, and [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/).
{{< inarticle-dark >}}
### Exploring Cybersecurity Domains
@@ -43,7 +43,7 @@ Cybersecurity encompasses various domains, each with its own unique focus. It's
1. **Blue Team**: Blue Team professionals focus on defending systems and networks from cyber threats. They design and implement security measures, monitor network traffic, and respond to incidents. Acquire knowledge of security tools, technologies, and best practices for effective defense.
-2. **Red Team**: Red Team professionals, also known as ethical hackers, specialize in assessing system vulnerabilities through simulated attacks. They identify weaknesses in security systems, conduct penetration testing, and help organizations strengthen their defenses. Develop hands-on skills in ethical hacking techniques and familiarize yourself with tools like [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/).
+2. **Red Team**: Red Team professionals, also known as ethical hackers, specialize in assessing system vulnerabilities through simulated attacks. They identify weaknesses in security systems, conduct penetration testing, and help organizations strengthen their defenses. Develop hands-on skills in ethical hacking techniques and familiarize yourself with tools like [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/).
3. **Purple Team**: The Purple Team combines elements of both Blue and Red Teams. They collaborate to enhance overall security posture by simulating realistic attack scenarios, evaluating defenses, and sharing insights. This role requires proficiency in both defensive and offensive techniques.
@@ -51,9 +51,9 @@ Cybersecurity encompasses various domains, each with its own unique focus. It's
While certifications are not mandatory, they can significantly enhance your employability and demonstrate your commitment to the field. Consider pursuing the following certifications:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): This entry-level certification validates your understanding of security concepts, network security, and security practices.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): This certification focuses on ethical hacking techniques and methodologies, enabling you to assess and mitigate vulnerabilities.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/): CISSP is a globally recognized certification that validates your expertise in various security domains.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): This entry-level certification validates your understanding of security concepts, network security, and security practices.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): This certification focuses on ethical hacking techniques and methodologies, enabling you to assess and mitigate vulnerabilities.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/): CISSP is a globally recognized certification that validates your expertise in various security domains.
Continuously learning and staying updated with the latest trends, tools, and techniques is crucial in cybersecurity. Follow industry blogs, participate in online communities, and attend cybersecurity conferences to expand your knowledge and network with professionals.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md
index c7ec1c590afcc..2f7a52ed2da10 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md
@@ -24,15 +24,15 @@ En los últimos años, la ciberseguridad se ha convertido en un aspecto fundamen
Antes de sumergirse en el mundo de la ciberseguridad, es importante sentar unas bases sólidas de conocimiento. He aquí algunas áreas esenciales en las que centrarse:
-1. **Redes**: Comprender los fundamentos de las redes es crucial en ciberseguridad. Familiarícese con los protocolos de red, direccionamiento IP, enrutamiento y [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Considere la posibilidad de obtener una certificación como CompTIA Network+ para validar sus conocimientos de redes.
+1. **Redes**: Comprender los fundamentos de las redes es crucial en ciberseguridad. Familiarícese con los protocolos de red, direccionamiento IP, enrutamiento y [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Considere la posibilidad de obtener una certificación como CompTIA Network+ para validar sus conocimientos de redes.
2. **Sistemas operativos**: Adquiera destreza en los sistemas operativos Linux y Windows. Aprenda a navegar por la línea de comandos, configurar los ajustes del sistema y gestionar las cuentas de usuario. Las certificaciones CompTIA A+ y Linux+ son excelentes puntos de partida para mejorar su comprensión de los sistemas operativos.
3. **Conceptos básicos de informática**: Adquirir una comprensión básica de los principios de la informática, incluyendo algoritmos, estructuras de datos y lenguajes de programación. Estos conocimientos le ayudarán a analizar vulnerabilidades y a desarrollar aplicaciones de software seguras.
-4. **Habilidades de codificación [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) puede ser ventajoso para automatizar las tareas de seguridad.
+4. **Habilidades de codificación [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) puede ser ventajoso para automatizar las tareas de seguridad.
-5. **Administración de sistemas empresariales**: Adquirir experiencia en la administración de sistemas empresariales le proporcionará conocimientos sobre la gestión de infraestructuras informáticas complejas. Familiarícese con Active Directory, Group Policy y [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Administración de sistemas empresariales**: Adquirir experiencia en la administración de sistemas empresariales le proporcionará conocimientos sobre la gestión de infraestructuras informáticas complejas. Familiarícese con Active Directory, Group Policy y [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Explorando los dominios de la ciberseguridad
@@ -40,7 +40,7 @@ La ciberseguridad abarca varios ámbitos, cada uno con su propio enfoque. Es ese
1. **Equipo Azul**: Los profesionales del Equipo Azul se centran en defender los sistemas y redes de las ciberamenazas. Diseñan y aplican medidas de seguridad, supervisan el tráfico de la red y responden a los incidentes. Adquieren conocimientos sobre herramientas de seguridad, tecnologías y mejores prácticas para una defensa eficaz.
-2. **Equipo Rojo**: Los profesionales del Equipo Rojo, también conocidos como hackers éticos, están especializados en evaluar las vulnerabilidades de los sistemas mediante ataques simulados. Identifican los puntos débiles de los sistemas de seguridad, realizan pruebas de penetración y ayudan a las organizaciones a reforzar sus defensas. Desarrolla habilidades prácticas en técnicas de hacking ético y familiarízate con herramientas como [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Equipo Rojo**: Los profesionales del Equipo Rojo, también conocidos como hackers éticos, están especializados en evaluar las vulnerabilidades de los sistemas mediante ataques simulados. Identifican los puntos débiles de los sistemas de seguridad, realizan pruebas de penetración y ayudan a las organizaciones a reforzar sus defensas. Desarrolla habilidades prácticas en técnicas de hacking ético y familiarízate con herramientas como [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Equipo morado**: El Equipo Púrpura combina elementos de los Equipos Azul y Rojo. Colaboran para mejorar la postura global de seguridad mediante la simulación de escenarios de ataque realistas, la evaluación de las defensas y el intercambio de información. Esta función requiere competencia en técnicas defensivas y ofensivas.
@@ -48,9 +48,9 @@ La ciberseguridad abarca varios ámbitos, cada uno con su propio enfoque. Es ese
Aunque las certificaciones no son obligatorias, pueden mejorar significativamente sus posibilidades de empleo y demostrar su compromiso con este campo. Considere la posibilidad de obtener las siguientes certificaciones:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Esta certificación de nivel básico valida su comprensión de los conceptos de seguridad, seguridad de redes y prácticas de seguridad.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Esta certificación se centra en las técnicas y metodologías de hacking ético, permitiéndole evaluar y mitigar vulnerabilidades.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP es una certificación reconocida en todo el mundo que valida su experiencia en diversos ámbitos de la seguridad.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Esta certificación de nivel básico valida su comprensión de los conceptos de seguridad, seguridad de redes y prácticas de seguridad.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Esta certificación se centra en las técnicas y metodologías de hacking ético, permitiéndole evaluar y mitigar vulnerabilidades.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP es una certificación reconocida en todo el mundo que valida su experiencia en diversos ámbitos de la seguridad.
En el ámbito de la ciberseguridad, es fundamental aprender continuamente y mantenerse al día de las últimas tendencias, herramientas y técnicas. Siga los blogs del sector, participe en comunidades en línea y asista a conferencias sobre ciberseguridad para ampliar sus conocimientos y establecer contactos con profesionales.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md
index fcf6f449ed67d..1bb3ff3c539a1 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md
@@ -24,15 +24,15 @@ Ces dernières années, la cybersécurité est devenue un aspect essentiel de no
Avant de plonger dans le monde de la cybersécurité, il est important de poser des bases solides. Voici quelques domaines essentiels sur lesquels il convient de se concentrer :
-1. **Les réseaux** : En matière de cybersécurité, il est essentiel de comprendre les principes fondamentaux des réseaux. Familiarisez-vous avec les protocoles de réseau, l'adressage IP, le routage et les réseaux de communication. [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Envisagez d'obtenir une certification telle que CompTIA Network+ pour valider vos connaissances en matière de réseaux.
+1. **Les réseaux** : En matière de cybersécurité, il est essentiel de comprendre les principes fondamentaux des réseaux. Familiarisez-vous avec les protocoles de réseau, l'adressage IP, le routage et les réseaux de communication. [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Envisagez d'obtenir une certification telle que CompTIA Network+ pour valider vos connaissances en matière de réseaux.
2. **Systèmes d'exploitation** : Acquérir des compétences dans les systèmes d'exploitation Linux et Windows. Apprenez à naviguer dans la ligne de commande, à configurer les paramètres du système et à gérer les comptes d'utilisateurs. Les certifications CompTIA A+ et Linux+ sont d'excellents points de départ pour améliorer votre compréhension des systèmes d'exploitation.
3. **Concepts informatiques de base** : Acquérir une compréhension de base des principes de l'informatique, y compris les algorithmes, les structures de données et les langages de programmation. Ces connaissances vous aideront à analyser les vulnérabilités et à développer des applications logicielles sécurisées.
-4. **Compétence en codage** : [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) peut s'avérer utile pour automatiser les tâches liées à la sécurité.
+4. **Compétence en codage** : [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) peut s'avérer utile pour automatiser les tâches liées à la sécurité.
-5. **Administration de systèmes d'entreprise** : L'acquisition d'une expérience dans l'administration de systèmes d'entreprise vous permettra de mieux comprendre la gestion d'infrastructures informatiques complexes. Familiarisez-vous avec Active Directory, Group Policy et [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Administration de systèmes d'entreprise** : L'acquisition d'une expérience dans l'administration de systèmes d'entreprise vous permettra de mieux comprendre la gestion d'infrastructures informatiques complexes. Familiarisez-vous avec Active Directory, Group Policy et [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Explorer les domaines de la cybersécurité
@@ -40,7 +40,7 @@ La cybersécurité englobe différents domaines, chacun ayant son propre intér
1. **Équipe bleue** : Les professionnels de l'équipe bleue se concentrent sur la défense des systèmes et des réseaux contre les cybermenaces. Ils conçoivent et mettent en œuvre des mesures de sécurité, surveillent le trafic réseau et réagissent aux incidents. Acquérir des connaissances sur les outils de sécurité, les technologies et les meilleures pratiques pour une défense efficace.
-2. **Équipe rouge** : Les professionnels de l'équipe rouge, également connus sous le nom de hackers éthiques, sont spécialisés dans l'évaluation des vulnérabilités des systèmes par le biais d'attaques simulées. Ils identifient les faiblesses des systèmes de sécurité, effectuent des tests de pénétration et aident les organisations à renforcer leurs défenses. Développez des compétences pratiques dans les techniques de piratage éthique et familiarisez-vous avec des outils tels que [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Équipe rouge** : Les professionnels de l'équipe rouge, également connus sous le nom de hackers éthiques, sont spécialisés dans l'évaluation des vulnérabilités des systèmes par le biais d'attaques simulées. Ils identifient les faiblesses des systèmes de sécurité, effectuent des tests de pénétration et aident les organisations à renforcer leurs défenses. Développez des compétences pratiques dans les techniques de piratage éthique et familiarisez-vous avec des outils tels que [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **L'équipe violette** : L'équipe violette combine des éléments des équipes bleue et rouge. Elle collabore à l'amélioration du dispositif de sécurité global en simulant des scénarios d'attaque réalistes, en évaluant les défenses et en partageant des informations. Ce rôle exige une maîtrise des techniques défensives et offensives.
@@ -48,9 +48,9 @@ La cybersécurité englobe différents domaines, chacun ayant son propre intér
Bien que les certifications ne soient pas obligatoires, elles peuvent considérablement améliorer votre employabilité et démontrer votre engagement dans le domaine. Envisagez d'obtenir les certifications suivantes :
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Cette certification de niveau débutant valide votre compréhension des concepts de sécurité, de la sécurité des réseaux et des pratiques de sécurité.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Cette certification se concentre sur les techniques et méthodologies de piratage éthique, vous permettant d'évaluer et d'atténuer les vulnérabilités.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) Le CISSP est une certification mondialement reconnue qui valide votre expertise dans différents domaines de la sécurité.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Cette certification de niveau débutant valide votre compréhension des concepts de sécurité, de la sécurité des réseaux et des pratiques de sécurité.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Cette certification se concentre sur les techniques et méthodologies de piratage éthique, vous permettant d'évaluer et d'atténuer les vulnérabilités.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) Le CISSP est une certification mondialement reconnue qui valide votre expertise dans différents domaines de la sécurité.
Dans le domaine de la cybersécurité, il est essentiel de se former en permanence et de se tenir au courant des dernières tendances, des outils et des techniques les plus récents. Suivez les blogs du secteur, participez à des communautés en ligne et assistez à des conférences sur la cybersécurité afin d'élargir vos connaissances et de nouer des contacts avec des professionnels.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md
index f522c07f11055..983d82115cca6 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md
@@ -24,15 +24,15 @@ Negli ultimi anni, la cybersecurity è diventata un aspetto critico della nostra
Prima di tuffarsi nel mondo della cybersecurity, è importante creare una solida base di conoscenze. Ecco alcune aree essenziali su cui concentrarsi:
-1. **Rete**: Comprendere i fondamenti del networking è fondamentale per la cybersecurity. Familiarizzate con i protocolli di rete, l'indirizzamento IP, l'instradamento e i protocolli di rete. [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Considerate la possibilità di ottenere una certificazione come CompTIA Network+ per convalidare le vostre conoscenze di networking.
+1. **Rete**: Comprendere i fondamenti del networking è fondamentale per la cybersecurity. Familiarizzate con i protocolli di rete, l'indirizzamento IP, l'instradamento e i protocolli di rete. [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Considerate la possibilità di ottenere una certificazione come CompTIA Network+ per convalidare le vostre conoscenze di networking.
2. **Sistemi operativi**: Acquisire competenze sui sistemi operativi Linux e Windows. Imparate a navigare nella riga di comando, a configurare le impostazioni di sistema e a gestire gli account utente. Le certificazioni CompTIA A+ e Linux+ sono ottimi punti di partenza per migliorare la comprensione dei sistemi operativi.
3. **Concetti di base di informatica**: Acquisire una conoscenza di base dei principi dell'informatica, compresi algoritmi, strutture di dati e linguaggi di programmazione. Queste conoscenze vi aiuteranno ad analizzare le vulnerabilità e a sviluppare applicazioni software sicure.
-4. **Competenze di codifica**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) può essere vantaggioso per automatizzare le attività di sicurezza.
+4. **Competenze di codifica**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) può essere vantaggioso per automatizzare le attività di sicurezza.
-5. **Amministrazione di sistemi aziendali**: L'esperienza nell'amministrazione di sistemi aziendali vi fornirà informazioni sulla gestione di infrastrutture IT complesse. Acquisire dimestichezza con Active Directory, Group Policy e [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Amministrazione di sistemi aziendali**: L'esperienza nell'amministrazione di sistemi aziendali vi fornirà informazioni sulla gestione di infrastrutture IT complesse. Acquisire dimestichezza con Active Directory, Group Policy e [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Esplorazione dei domini della sicurezza informatica
@@ -40,7 +40,7 @@ La cybersecurity comprende vari domini, ognuno dei quali ha un proprio obiettivo
1. **Blue Team**: I professionisti del Blue Team si concentrano sulla difesa dei sistemi e delle reti dalle minacce informatiche. Progettano e implementano misure di sicurezza, monitorano il traffico di rete e rispondono agli incidenti. Acquisiscono la conoscenza degli strumenti di sicurezza, delle tecnologie e delle best practice per una difesa efficace.
-2. **Red Team**: I professionisti del Red Team, noti anche come hacker etici, sono specializzati nella valutazione delle vulnerabilità dei sistemi attraverso attacchi simulati. Identificano i punti deboli dei sistemi di sicurezza, conducono test di penetrazione e aiutano le organizzazioni a rafforzare le loro difese. Sviluppate competenze pratiche nelle tecniche di hacking etico e familiarizzate con strumenti quali [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: I professionisti del Red Team, noti anche come hacker etici, sono specializzati nella valutazione delle vulnerabilità dei sistemi attraverso attacchi simulati. Identificano i punti deboli dei sistemi di sicurezza, conducono test di penetrazione e aiutano le organizzazioni a rafforzare le loro difese. Sviluppate competenze pratiche nelle tecniche di hacking etico e familiarizzate con strumenti quali [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Squadra viola**: Il team viola combina elementi dei team blu e rossi. Collaborano per migliorare la sicurezza generale simulando scenari di attacco realistici, valutando le difese e condividendo le intuizioni. Questo ruolo richiede la conoscenza di tecniche sia difensive che offensive.
@@ -48,9 +48,9 @@ La cybersecurity comprende vari domini, ognuno dei quali ha un proprio obiettivo
Anche se le certificazioni non sono obbligatorie, possono migliorare significativamente la vostra occupabilità e dimostrare il vostro impegno nel settore. Considerate la possibilità di conseguire le seguenti certificazioni:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Questa certificazione entry-level convalida la comprensione dei concetti di sicurezza, sicurezza di rete e pratiche di sicurezza.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Questa certificazione si concentra sulle tecniche e sulle metodologie di ethical hacking, consentendo di valutare e mitigare le vulnerabilità.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) Il CISSP è una certificazione riconosciuta a livello mondiale che convalida le vostre competenze in vari settori della sicurezza.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Questa certificazione entry-level convalida la comprensione dei concetti di sicurezza, sicurezza di rete e pratiche di sicurezza.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Questa certificazione si concentra sulle tecniche e sulle metodologie di ethical hacking, consentendo di valutare e mitigare le vulnerabilità.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) Il CISSP è una certificazione riconosciuta a livello mondiale che convalida le vostre competenze in vari settori della sicurezza.
L'apprendimento continuo e l'aggiornamento sulle ultime tendenze, strumenti e tecniche è fondamentale per la sicurezza informatica. Seguite i blog di settore, partecipate alle comunità online e frequentate le conferenze sulla sicurezza informatica per ampliare le vostre conoscenze e fare rete con i professionisti.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md
index fbaad5d6c3895..92c8d6f195718 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md
@@ -24,15 +24,15 @@ coverCaption: "サイバーセキュリティの専門家集団が一丸とな
サイバーセキュリティの世界に飛び込む前に、しっかりとした知識の土台を築くことが重要です。ここでは、重点的に学ぶべき重要な分野をいくつか紹介します:
-1.**ネットワーク**:ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて極めて重要です。ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて非常に重要である。 [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/)ネットワークに関する知識を証明するために、CompTIA Network+などの資格取得を検討する。
+1.**ネットワーク**:ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて極めて重要です。ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて非常に重要である。 [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/)ネットワークに関する知識を証明するために、CompTIA Network+などの資格取得を検討する。
2.**オペレーティングシステム**:LinuxとWindowsの両方のオペレーティングシステムに習熟する。コマンドラインの操作方法、システム設定の方法、ユーザーアカウントの管理方法などを学びます。CompTIA A+とLinux+の資格は、オペレーティングシステムの理解を深めるための素晴らしい出発点です。
3.**コンピュータサイエンスの基本的な概念**:アルゴリズム、データ構造、プログラミング言語など、コンピュータサイエンスの原理を基本的に理解する。この知識は、脆弱性を分析し、安全なソフトウェアアプリケーションを開発するために役立ちます。
-4.**コーディングスキル**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/)は、セキュリティタスクの自動化に有利に働くことがあります。
+4.**コーディングスキル**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/)は、セキュリティタスクの自動化に有利に働くことがあります。
-5.**エンタープライズ・システム・アドミニストレーション**:企業システム管理の経験を積むことで、複雑なITインフラストラクチャを管理するための見識を得ることができます。Active Directory、Group Policy、およびSecurityに精通する。 [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5.**エンタープライズ・システム・アドミニストレーション**:企業システム管理の経験を積むことで、複雑なITインフラストラクチャを管理するための見識を得ることができます。Active Directory、Group Policy、およびSecurityに精通する。 [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### サイバーセキュリティの領域を探る
@@ -40,7 +40,7 @@ coverCaption: "サイバーセキュリティの専門家集団が一丸とな
1.1. **ブルーチーム**:ブルーチームの専門家は、システムやネットワークをサイバー脅威から守ることに重点を置いています。セキュリティ対策の設計と実装、ネットワークトラフィックの監視、インシデントへの対応などを行います。効果的な防御のためのセキュリティツール、技術、ベストプラクティスに関する知識を習得する。
-2.**レッドチーム**:倫理的ハッカーとして知られるレッドチームの専門家は、模擬攻撃を通じてシステムの脆弱性を評価することに特化しています。セキュリティシステムの弱点を特定し、侵入テストを実施し、組織の防御力強化を支援する。倫理的ハッキング技術の実践的なスキルを身につけ、以下のようなツールに精通する。 [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2.**レッドチーム**:倫理的ハッカーとして知られるレッドチームの専門家は、模擬攻撃を通じてシステムの脆弱性を評価することに特化しています。セキュリティシステムの弱点を特定し、侵入テストを実施し、組織の防御力強化を支援する。倫理的ハッキング技術の実践的なスキルを身につけ、以下のようなツールに精通する。 [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3.**パープルチーム**:Purple Teamは、Blue TeamとRed Teamの両方の要素を兼ね備えています。現実的な攻撃シナリオをシミュレートし、防御を評価し、洞察を共有することによって、全体的なセキュリティ態勢を強化するために協力する。この役割には、防御と攻撃の両方の技術に精通していることが必要です。
@@ -48,9 +48,9 @@ coverCaption: "サイバーセキュリティの専門家集団が一丸とな
認定資格は必須ではありませんが、取得することで雇用可能性が大幅に向上し、この分野へのコミットメントを示すことができます。以下の資格の取得を検討してください:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)このエントリーレベルの認定は、セキュリティの概念、ネットワークセキュリティ、およびセキュリティの実践についての理解を証明するものです。
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)この資格は、倫理的なハッキング技術と方法論に焦点を当て、脆弱性の評価と緩和を可能にします。
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)CISSPは、さまざまなセキュリティ領域における専門知識を証明する世界的に認められた資格です。
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)このエントリーレベルの認定は、セキュリティの概念、ネットワークセキュリティ、およびセキュリティの実践についての理解を証明するものです。
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)この資格は、倫理的なハッキング技術と方法論に焦点を当て、脆弱性の評価と緩和を可能にします。
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)CISSPは、さまざまなセキュリティ領域における専門知識を証明する世界的に認められた資格です。
サイバーセキュリティでは、継続的に学習し、最新のトレンド、ツール、テクニックを常に把握することが重要です。業界のブログをフォローし、オンラインコミュニティに参加し、サイバーセキュリティのカンファレンスに参加して、知識を深め、専門家とのネットワークを広げましょう。
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md
index 01c41f230934d..1cc86376f88e6 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md
@@ -24,15 +24,15 @@ In de afgelopen jaren is cyberbeveiliging een cruciaal aspect van ons digitale l
Voordat u zich in de wereld van cyberbeveiliging stort, is het belangrijk om een solide fundament van kennis te leggen. Hier zijn enkele essentiële gebieden waarop u zich moet richten:
-1. **Netwerken**: Inzicht in de grondbeginselen van netwerken is cruciaal voor cyberbeveiliging. Maak jezelf vertrouwd met netwerkprotocollen, IP-adressering, routing en [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Overweeg het behalen van een certificering zoals CompTIA Network+ om je netwerkkennis te valideren.
+1. **Netwerken**: Inzicht in de grondbeginselen van netwerken is cruciaal voor cyberbeveiliging. Maak jezelf vertrouwd met netwerkprotocollen, IP-adressering, routing en [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Overweeg het behalen van een certificering zoals CompTIA Network+ om je netwerkkennis te valideren.
2. **Besturingssystemen**: Krijg vaardigheid in zowel Linux als Windows besturingssystemen. Leer navigeren met de opdrachtregel, systeeminstellingen configureren en gebruikersaccounts beheren. CompTIA A+ en Linux+ certificeringen zijn uitstekende startpunten om je kennis van besturingssystemen te vergroten.
3. **Basisbegrippen uit de informatica**: Verwerf een basiskennis van de principes van computerwetenschappen, waaronder algoritmen, gegevensstructuren en programmeertalen. Deze kennis helpt je bij het analyseren van kwetsbaarheden en het ontwikkelen van veilige softwaretoepassingen.
-4. **Codeervaardigheden**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) kan voordelig zijn bij het automatiseren van beveiligingstaken.
+4. **Codeervaardigheden**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) kan voordelig zijn bij het automatiseren van beveiligingstaken.
-5. **Systeembeheer**: Ervaring opdoen met enterprise systeembeheer geeft je inzicht in het beheren van complexe IT-infrastructuren. Maak jezelf vertrouwd met Active Directory, Groepsbeleid en [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Systeembeheer**: Ervaring opdoen met enterprise systeembeheer geeft je inzicht in het beheren van complexe IT-infrastructuren. Maak jezelf vertrouwd met Active Directory, Groepsbeleid en [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Cyberbeveiligingsdomeinen verkennen
@@ -40,7 +40,7 @@ Cyberbeveiliging omvat verschillende domeinen, elk met zijn eigen unieke focus.
1. **Blauw team**: Blue Team-professionals richten zich op de verdediging van systemen en netwerken tegen cyberbedreigingen. Ze ontwerpen en implementeren beveiligingsmaatregelen, monitoren netwerkverkeer en reageren op incidenten. Ze verwerven kennis van beveiligingstools, technologieën en best practices voor een effectieve verdediging.
-2. **Red Team**: Red Team professionals, ook bekend als ethische hackers, zijn gespecialiseerd in het beoordelen van zwakke plekken in systemen door middel van gesimuleerde aanvallen. Ze identificeren zwakke plekken in beveiligingssystemen, voeren penetratietests uit en helpen organisaties hun verdediging te versterken. Ontwikkel praktische vaardigheden in ethische hacktechnieken en maak jezelf vertrouwd met tools zoals [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: Red Team professionals, ook bekend als ethische hackers, zijn gespecialiseerd in het beoordelen van zwakke plekken in systemen door middel van gesimuleerde aanvallen. Ze identificeren zwakke plekken in beveiligingssystemen, voeren penetratietests uit en helpen organisaties hun verdediging te versterken. Ontwikkel praktische vaardigheden in ethische hacktechnieken en maak jezelf vertrouwd met tools zoals [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Paars Team**: Het Purple Team combineert elementen van zowel het Blue als het Red Team. Ze werken samen om de algemene beveiliging te verbeteren door realistische aanvalsscenario's te simuleren, verdedigingen te evalueren en inzichten te delen. Deze rol vereist vaardigheid in zowel defensieve als offensieve technieken.
@@ -48,9 +48,9 @@ Cyberbeveiliging omvat verschillende domeinen, elk met zijn eigen unieke focus.
Hoewel certificeringen niet verplicht zijn, kunnen ze uw inzetbaarheid aanzienlijk vergroten en uw betrokkenheid bij het vak aantonen. Overweeg de volgende certificeringen te behalen:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Deze certificering op instapniveau valideert je begrip van beveiligingsconcepten, netwerkbeveiliging en beveiligingspraktijken.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Deze certificering richt zich op ethische hackingtechnieken en -methodologieën, waarmee je kwetsbaarheden kunt beoordelen en beperken.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP is een wereldwijd erkende certificering die je expertise in verschillende beveiligingsdomeinen valideert.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Deze certificering op instapniveau valideert je begrip van beveiligingsconcepten, netwerkbeveiliging en beveiligingspraktijken.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Deze certificering richt zich op ethische hackingtechnieken en -methodologieën, waarmee je kwetsbaarheden kunt beoordelen en beperken.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP is een wereldwijd erkende certificering die je expertise in verschillende beveiligingsdomeinen valideert.
Voortdurend leren en op de hoogte blijven van de nieuwste trends, tools en technieken is cruciaal in cyberbeveiliging. Volg industrieblogs, neem deel aan online communities en woon cyberbeveiligingsconferenties bij om uw kennis uit te breiden en te netwerken met professionals.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md
index 4266cb372d933..3af139dbd69ba 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md
@@ -24,15 +24,15 @@ W ostatnich latach cyberbezpieczeństwo stało się krytycznym aspektem naszego
Przed zanurzeniem się w świat cyberbezpieczeństwa ważne jest, aby położyć solidne fundamenty wiedzy. Oto kilka istotnych obszarów, na których należy się skupić:
-1. **Sieć**: Zrozumienie podstaw sieci ma kluczowe znaczenie dla cyberbezpieczeństwa. Zapoznanie się z protokołami sieciowymi, adresowaniem IP, routingiem i [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Rozważ uzyskanie certyfikatu, takiego jak CompTIA Network+, aby potwierdzić swoją wiedzę na temat sieci.
+1. **Sieć**: Zrozumienie podstaw sieci ma kluczowe znaczenie dla cyberbezpieczeństwa. Zapoznanie się z protokołami sieciowymi, adresowaniem IP, routingiem i [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Rozważ uzyskanie certyfikatu, takiego jak CompTIA Network+, aby potwierdzić swoją wiedzę na temat sieci.
2. **Systemy operacyjne**: Zdobądź biegłość w systemach operacyjnych Linux i Windows. Dowiedz się, jak poruszać się po wierszu poleceń, konfigurować ustawienia systemowe i zarządzać kontami użytkowników. Certyfikaty CompTIA A+ i Linux+ są doskonałymi punktami wyjścia do lepszego zrozumienia systemów operacyjnych.
3. **Podstawowe koncepcje informatyki**: Zdobądź podstawowe zrozumienie zasad informatyki, w tym algorytmów, struktur danych i języków programowania. Wiedza ta pomoże ci analizować luki w zabezpieczeniach i tworzyć bezpieczne aplikacje.
-4. **Umiejętności kodowania**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) może być korzystna w automatyzacji zadań związanych z bezpieczeństwem.
+4. **Umiejętności kodowania**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) może być korzystna w automatyzacji zadań związanych z bezpieczeństwem.
-5. **Administracja systemami korporacyjnymi**: Zdobycie doświadczenia w administracji systemami korporacyjnymi zapewni ci wgląd w zarządzanie złożonymi infrastrukturami IT. Zapoznanie się z usługami Active Directory, Group Policy i [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Administracja systemami korporacyjnymi**: Zdobycie doświadczenia w administracji systemami korporacyjnymi zapewni ci wgląd w zarządzanie złożonymi infrastrukturami IT. Zapoznanie się z usługami Active Directory, Group Policy i [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Odkrywanie domen cyberbezpieczeństwa
@@ -40,7 +40,7 @@ Cyberbezpieczeństwo obejmuje różne domeny, z których każda ma swój własny
1. **Blue Team**: Specjaliści Blue Team koncentrują się na obronie systemów i sieci przed cyberzagrożeniami. Projektują i wdrażają środki bezpieczeństwa, monitorują ruch sieciowy i reagują na incydenty. Zdobywają wiedzę na temat narzędzi bezpieczeństwa, technologii i najlepszych praktyk w celu skutecznej obrony.
-2. **Red Team**: Specjaliści Red Team, znani również jako etyczni hakerzy, specjalizują się w ocenie słabych punktów systemu poprzez symulowane ataki. Identyfikują słabe punkty w systemach bezpieczeństwa, przeprowadzają testy penetracyjne i pomagają organizacjom wzmocnić ich obronę. Rozwijaj praktyczne umiejętności w zakresie technik etycznego hakowania i zapoznaj się z narzędziami takimi jak [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: Specjaliści Red Team, znani również jako etyczni hakerzy, specjalizują się w ocenie słabych punktów systemu poprzez symulowane ataki. Identyfikują słabe punkty w systemach bezpieczeństwa, przeprowadzają testy penetracyjne i pomagają organizacjom wzmocnić ich obronę. Rozwijaj praktyczne umiejętności w zakresie technik etycznego hakowania i zapoznaj się z narzędziami takimi jak [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Purple Team**: Purpurowy zespół łączy w sobie elementy zespołów niebieskiego i czerwonego. Współpracują w celu poprawy ogólnego stanu bezpieczeństwa poprzez symulowanie realistycznych scenariuszy ataków, ocenę obrony i dzielenie się spostrzeżeniami. Rola ta wymaga biegłości zarówno w technikach defensywnych, jak i ofensywnych.
@@ -48,9 +48,9 @@ Cyberbezpieczeństwo obejmuje różne domeny, z których każda ma swój własny
Chociaż certyfikaty nie są obowiązkowe, mogą znacznie zwiększyć szanse na zatrudnienie i wykazać zaangażowanie w tę dziedzinę. Warto rozważyć uzyskanie następujących certyfikatów:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Ten podstawowy certyfikat potwierdza zrozumienie koncepcji bezpieczeństwa, bezpieczeństwa sieci i praktyk bezpieczeństwa.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Certyfikacja ta koncentruje się na technikach i metodologiach etycznego hakowania, umożliwiając ocenę i łagodzenie luk w zabezpieczeniach.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP to uznawany na całym świecie certyfikat, który potwierdza wiedzę specjalistyczną w różnych dziedzinach bezpieczeństwa.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Ten podstawowy certyfikat potwierdza zrozumienie koncepcji bezpieczeństwa, bezpieczeństwa sieci i praktyk bezpieczeństwa.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Certyfikacja ta koncentruje się na technikach i metodologiach etycznego hakowania, umożliwiając ocenę i łagodzenie luk w zabezpieczeniach.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP to uznawany na całym świecie certyfikat, który potwierdza wiedzę specjalistyczną w różnych dziedzinach bezpieczeństwa.
Ciągłe uczenie się i bycie na bieżąco z najnowszymi trendami, narzędziami i technikami ma kluczowe znaczenie w cyberbezpieczeństwie. Śledź blogi branżowe, uczestnicz w społecznościach internetowych i bierz udział w konferencjach dotyczących cyberbezpieczeństwa, aby poszerzyć swoją wiedzę i nawiązać kontakty z profesjonalistami.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md
index 292b8030460b8..986d1d709ae7e 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md
@@ -71,9 +71,9 @@ Um als **Cybersicherheitsexperte** erfolgreich zu sein, muss man über eine Reih
Einschlägige Zertifizierungen sind für Fachleute im Bereich der Cybersicherheit ebenfalls von entscheidender Bedeutung, um ihre Fähigkeiten und ihr Fachwissen zu bestätigen. Einige weithin anerkannte Zertifizierungen sind:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Schlussfolgerung
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md
index dabe667671f62..343d8561f3f1c 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md
@@ -73,9 +73,9 @@ To succeed as a **cybersecurity expert**, one must possess a range of technical
Obtaining relevant certifications is also crucial for cybersecurity professionals to validate their skills and expertise. Some widely recognized certifications include:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
{{< inarticle-dark >}}
## Conclusion
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md
index f487b3baf28db..86b6732b21f89 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md
@@ -71,9 +71,9 @@ Para tener éxito como **experto en ciberseguridad**, hay que poseer una serie d
Obtener las certificaciones pertinentes también es crucial para que los profesionales de la ciberseguridad validen sus habilidades y conocimientos. Algunas certificaciones ampliamente reconocidas son:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusión
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md
index f97ab75a88ac6..b1dbf52e6d4e4 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md
@@ -71,9 +71,9 @@ Pour réussir en tant qu'**expert en cybersécurité**, il faut posséder un év
L'obtention de certifications pertinentes est également cruciale pour les professionnels de la cybersécurité afin de valider leurs compétences et leur expertise. Parmi les certifications largement reconnues, citons
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusion
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md
index e01ead9d4864a..d1ac037cd04e1 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md
@@ -71,9 +71,9 @@ Gli **esperti di cybersecurity** lavorano spesso in conformità a varie normativ
Anche l'ottenimento di certificazioni pertinenti è fondamentale per i professionisti della cybersicurezza per convalidare le proprie capacità e competenze. Alcune certificazioni ampiamente riconosciute sono:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusione
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md
index 03c87d6110605..1d7588a905d99 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md
@@ -71,9 +71,9 @@ coverCaption: "知識とツールで武装したサイバーセキュリティ
サイバーセキュリティの専門家にとって、関連する認定資格を取得することも、スキルや専門知識を証明するために重要です。広く認知されている認定資格には、次のようなものがあります:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## 結論
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md
index d0e345ce2ae0f..37e36bbdca1a5 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md
@@ -71,9 +71,9 @@ Om als cyberbeveiligingsdeskundige** te slagen, moet iemand over een reeks techn
Het behalen van relevante certificeringen is ook cruciaal voor cyberbeveiligingsprofessionals om hun vaardigheden en expertise te valideren. Enkele algemeen erkende certificeringen zijn:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusie
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md
index 8fef07c115ca3..3f2fffb74e496 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md
@@ -71,9 +71,9 @@ Aby odnieść sukces jako **ekspert ds. bezpieczeństwa cybernetycznego**, nale
Uzyskanie odpowiednich certyfikatów ma również kluczowe znaczenie dla specjalistów ds. cyberbezpieczeństwa w celu potwierdzenia ich umiejętności i wiedzy specjalistycznej. Niektóre powszechnie uznawane certyfikaty obejmują:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Wnioski
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md
index b5b95e9ea56c1..210f510d62e93 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md
@@ -36,7 +36,7 @@ Implementing a security awareness training program offers several benefits:
5. **Addressing insider threats:** Security awareness training helps employees recognize and report insider threats, such as malicious actions by employees or contractors. This ensures the organization remains vigilant against internal risks.
-6. **Improving password security:** Training employees on best practices for creating and managing [strong passwords](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/) enhances the overall password security posture of the organization, reducing the risk of unauthorized access.
+6. **Improving password security:** Training employees on best practices for creating and managing [strong passwords](https://simeononsecurity.com/articles/how-to-create-strong-passwords/) enhances the overall password security posture of the organization, reducing the risk of unauthorized access.
7. **Mitigating phishing and social engineering attacks:** Security awareness training equips employees with the knowledge to identify and report phishing emails and social engineering attempts, protecting the organization from these common attack vectors.
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md
index 626c8c4afc1b2..d0d935d4022c6 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md
@@ -75,7 +75,7 @@ The third stage focuses on **containment and eradication**. Once an incident is
3. **System Restoration**: Restore affected systems to their normal state, ensuring that they are free from any malicious artifacts or backdoors. This may involve rebuilding systems from trusted sources or restoring them from clean backups.
-4. **Threat Hunting**: Conduct [proactive **threat hunting**](https://simeononsecurity.ch/articles/the-role-of-threat-hunting-in-proactive-cybersecurity/) activities to identify any remnants of the attacker's presence and ensure complete eradication. This includes thorough analysis of system logs, network traffic, and other relevant data sources.
+4. **Threat Hunting**: Conduct [proactive **threat hunting**](https://simeononsecurity.com/articles/the-role-of-threat-hunting-in-proactive-cybersecurity/) activities to identify any remnants of the attacker's presence and ensure complete eradication. This includes thorough analysis of system logs, network traffic, and other relevant data sources.
### Stage 4: Post-Incident Recovery
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md
index bfc0b6bae0023..84671133c4414 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md
@@ -17,7 +17,7 @@ coverCaption: "Secure Your Network: Defend Against Cyber Threats with Effective
### Introduction
-In today's digital landscape, **cybersecurity** is of paramount importance for organizations across industries. Developing a **comprehensive cybersecurity policy** is essential to protect sensitive information, mitigate risks, and maintain regulatory compliance. In this article, we will explore the key steps involved in developing a robust cybersecurity policy that aligns with industry best practices and regulatory requirements. We will also highlight the significance of industry standards such as the [**Risk Management Framework (RMF)**](https://simeononsecurity.ch/articles/mastering-risk-management-framework-cybersecurity/), **National Institute of Standards and Technology (NIST) Standards**, [**Payment Card Industry Data Security Standard (PCI-DSS)**](https://simeononsecurity.ch/articles/pci-dss-explained-card-transaction-security/), **Health Insurance Portability and Accountability Act (HIPAA)**, and [**Federal Information Security Modernization Act (FISMA)**](https://simeononsecurity.ch/articles/fisma-summarized/) in shaping cybersecurity policies.
+In today's digital landscape, **cybersecurity** is of paramount importance for organizations across industries. Developing a **comprehensive cybersecurity policy** is essential to protect sensitive information, mitigate risks, and maintain regulatory compliance. In this article, we will explore the key steps involved in developing a robust cybersecurity policy that aligns with industry best practices and regulatory requirements. We will also highlight the significance of industry standards such as the [**Risk Management Framework (RMF)**](https://simeononsecurity.com/articles/mastering-risk-management-framework-cybersecurity/), **National Institute of Standards and Technology (NIST) Standards**, [**Payment Card Industry Data Security Standard (PCI-DSS)**](https://simeononsecurity.com/articles/pci-dss-explained-card-transaction-security/), **Health Insurance Portability and Accountability Act (HIPAA)**, and [**Federal Information Security Modernization Act (FISMA)**](https://simeononsecurity.com/articles/fisma-summarized/) in shaping cybersecurity policies.
{{< youtube id="bsNzeJjFaAo" >}}
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md
index 0a205f51679c5..b727d893a345a 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md
@@ -15,7 +15,7 @@ coverCaption: "Unleash the Power of Collaborative Cybersecurity Protection."
## Should I Outsource Any Part of Cybersecurity?
-In today's digital landscape, where **data breaches** and **cyber threats** are on the rise, businesses often face the dilemma of whether to outsource their cybersecurity operations. While having an in-house cybersecurity team may seem like the safer option, [outsourcing cybersecurity](https://simeononsecurity.ch/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) can offer several benefits, including a **unified cybersecurity strategy**. In this article, we will explore the factors to consider when deciding whether to outsource any part of cybersecurity, discuss the pros and cons, and provide best practices for effective outsourcing.
+In today's digital landscape, where **data breaches** and **cyber threats** are on the rise, businesses often face the dilemma of whether to outsource their cybersecurity operations. While having an in-house cybersecurity team may seem like the safer option, [outsourcing cybersecurity](https://simeononsecurity.com/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) can offer several benefits, including a **unified cybersecurity strategy**. In this article, we will explore the factors to consider when deciding whether to outsource any part of cybersecurity, discuss the pros and cons, and provide best practices for effective outsourcing.
{{< youtube id="iProPvIGVIY" >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md
index bca90928e93b9..5928b0e35db66 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md
@@ -16,13 +16,13 @@ coverCaption: ""
## Introduction
-The [Federal Information Security Modernization Act (FISMA)](https://simeononsecurity.ch/articles/fisma-summarized/) is a US law enacted in 2002 that requires federal agencies to establish and maintain information security programs to protect their information and information systems. This act was passed in response to the growing need for improved information security in the federal government, and it has since been updated several times to keep pace with the changing threat landscape.
+The [Federal Information Security Modernization Act (FISMA)](https://simeononsecurity.com/articles/fisma-summarized/) is a US law enacted in 2002 that requires federal agencies to establish and maintain information security programs to protect their information and information systems. This act was passed in response to the growing need for improved information security in the federal government, and it has since been updated several times to keep pace with the changing threat landscape.
{{< youtube id="adxnNStDskA" >}}
-## [What is FISMA?](https://simeononsecurity.ch/articles/fisma-summarized/)
+## [What is FISMA?](https://simeononsecurity.com/articles/fisma-summarized/)
-[FISMA](https://simeononsecurity.ch/articles/fisma-summarized/) is a set of standards and guidelines for information security that apply to federal agencies and their contractors. The purpose of FISMA is to ensure that sensitive information is protected from unauthorized access, use, disclosure, disruption, modification, or destruction. FISMA requires that federal agencies implement a risk-based approach to information security, which involves identifying and assessing potential security risks, implementing security controls to mitigate those risks, and continuously monitoring the effectiveness of those controls.
+[FISMA](https://simeononsecurity.com/articles/fisma-summarized/) is a set of standards and guidelines for information security that apply to federal agencies and their contractors. The purpose of FISMA is to ensure that sensitive information is protected from unauthorized access, use, disclosure, disruption, modification, or destruction. FISMA requires that federal agencies implement a risk-based approach to information security, which involves identifying and assessing potential security risks, implementing security controls to mitigate those risks, and continuously monitoring the effectiveness of those controls.
{{< inarticle-dark >}}
## Key Components of FISMA
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md
index 5dee4d4b86016..2cb5ff989bd5d 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md
@@ -28,11 +28,11 @@ Das National Institute of Standards and Technology (NIST) hat eine Richtlinie f
### Löschen
-Beim Löschen werden die Daten auf einem Gerät mit einer Reihe von Binärwerten überschrieben. Diese Methode ist weniger sicher als die physische Zerstörung, aber immer noch wirksam bei der Säuberung der meisten Wechseldatenträger. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die vom Verteidigungsministerium (DoD) festgelegten Standards erfüllt. [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) Spezifikation.
+Beim Löschen werden die Daten auf einem Gerät mit einer Reihe von Binärwerten überschrieben. Diese Methode ist weniger sicher als die physische Zerstörung, aber immer noch wirksam bei der Säuberung der meisten Wechseldatenträger. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die vom Verteidigungsministerium (DoD) festgelegten Standards erfüllt. [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) Spezifikation.
### Spülen
-Beim Bereinigen werden die Daten auf einem Gerät mehrfach mit einem Muster binärer Werte überschrieben. Diese Methode ist sicherer als das Löschen und wird für die Säuberung sensibler Daten empfohlen. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die von der NIST festgelegten Standards erfüllt. [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+Beim Bereinigen werden die Daten auf einem Gerät mehrfach mit einem Muster binärer Werte überschrieben. Diese Methode ist sicherer als das Löschen und wird für die Säuberung sensibler Daten empfohlen. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die von der NIST festgelegten Standards erfüllt. [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md
index b0cfcc10995e7..85eae61faaeca 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md
@@ -18,7 +18,7 @@ Removable media, such as hard drives, solid state drives (SSD), USB flash drives
**Sanitizing removable media is essential because the data stored on these devices can be easily recovered, even if the data has been deleted.** This is because when data is deleted, only the reference to the data is removed, but the actual data remains on the disk until it is overwritten. This makes it possible for malicious actors to recover sensitive data using data recovery software.
-## [NIST 800-88](https://simeononsecurity.ch/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 Types Of Destruction
+## [NIST 800-88](https://simeononsecurity.com/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 Types Of Destruction
The National Institute of Standards and Technology (NIST) has published a guideline for sanitizing removable media, known as NIST Special Publication 800-88 Revision 1. The guideline outlines several methods for sanitizing removable media, including physical destruction, clearing, and purging.
@@ -28,11 +28,11 @@ The National Institute of Standards and Technology (NIST) has published a guidel
### Clearing
-Clearing is the process of overwriting the data on a device with a series of binary values. This method is less secure than physical destruction but is still effective in sanitizing most removable media. [NIST 800-88](https://simeononsecurity.ch/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 recommends using a software tool that meets the standards set by the Department of Defense (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+Clearing is the process of overwriting the data on a device with a series of binary values. This method is less secure than physical destruction but is still effective in sanitizing most removable media. [NIST 800-88](https://simeononsecurity.com/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 recommends using a software tool that meets the standards set by the Department of Defense (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
### Purging
-Purging is the process of overwriting the data on a device multiple times with a pattern of binary values. This method is more secure than clearing and is recommended for sanitizing sensitive data. NIST 800-88 Revision 1 recommends using a software tool that meets the standards set by the [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+Purging is the process of overwriting the data on a device multiple times with a pattern of binary values. This method is more secure than clearing and is recommended for sanitizing sensitive data. NIST 800-88 Revision 1 recommends using a software tool that meets the standards set by the [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md
index 55d84419fa2c3..685f93b5688be 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md
@@ -28,11 +28,11 @@ El Instituto Nacional de Estándares y Tecnología (NIST) ha publicado una direc
### Borrado
-El borrado es el proceso de sobrescribir los datos de un dispositivo con una serie de valores binarios. Este método es menos seguro que la destrucción física, pero sigue siendo eficaz para desinfectar la mayoría de los soportes extraíbles. NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el Departamento de Defensa (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
+El borrado es el proceso de sobrescribir los datos de un dispositivo con una serie de valores binarios. Este método es menos seguro que la destrucción física, pero sigue siendo eficaz para desinfectar la mayoría de los soportes extraíbles. NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el Departamento de Defensa (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
### Purga
-La purga es el proceso de sobrescribir los datos de un dispositivo varias veces con un patrón de valores binarios. Este método es más seguro que el borrado y se recomienda para sanear datos sensibles. El NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
+La purga es el proceso de sobrescribir los datos de un dispositivo varias veces con un patrón de valores binarios. Este método es más seguro que el borrado y se recomienda para sanear datos sensibles. El NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md
index 7f40f0823d5ff..10e235553ec00 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md
@@ -28,11 +28,11 @@ Le National Institute of Standards and Technology (NIST) a publié une directive
### Nettoyage
-L'effacement consiste à remplacer les données d'un appareil par une série de valeurs binaires. Cette méthode est moins sûre que la destruction physique, mais reste efficace pour assainir la plupart des supports amovibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par le Département de la Défense (DoD). [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) spécification.
+L'effacement consiste à remplacer les données d'un appareil par une série de valeurs binaires. Cette méthode est moins sûre que la destruction physique, mais reste efficace pour assainir la plupart des supports amovibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par le Département de la Défense (DoD). [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) spécification.
### Purge
-La purge consiste à écraser plusieurs fois les données d'un dispositif avec un modèle de valeurs binaires. Cette méthode est plus sûre que l'effacement et est recommandée pour assainir les données sensibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par la [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+La purge consiste à écraser plusieurs fois les données d'un dispositif avec un modèle de valeurs binaires. Cette méthode est plus sûre que l'effacement et est recommandée pour assainir les données sensibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par la [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md
index 7877f6ac506d8..a9bf209c47eb8 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md
@@ -28,11 +28,11 @@ Il National Institute of Standards and Technology (NIST) ha pubblicato una linea
### Cancellazione
-La cancellazione è il processo di sovrascrittura dei dati su un dispositivo con una serie di valori binari. Questo metodo è meno sicuro della distruzione fisica, ma è comunque efficace per sanificare la maggior parte dei supporti rimovibili. NIST 800-88 Revisione 1 raccomanda di utilizzare uno strumento software che soddisfi gli standard stabiliti dal Dipartimento della Difesa (DoD). [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
+La cancellazione è il processo di sovrascrittura dei dati su un dispositivo con una serie di valori binari. Questo metodo è meno sicuro della distruzione fisica, ma è comunque efficace per sanificare la maggior parte dei supporti rimovibili. NIST 800-88 Revisione 1 raccomanda di utilizzare uno strumento software che soddisfi gli standard stabiliti dal Dipartimento della Difesa (DoD). [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
### Spurgo
-L'epurazione è il processo di sovrascrittura dei dati su un dispositivo più volte con uno schema di valori binari. Questo metodo è più sicuro della cancellazione ed è consigliato per la sanificazione dei dati sensibili. Il NIST 800-88 Revisione 1 raccomanda l'utilizzo di uno strumento software che soddisfi gli standard stabiliti dall'Agenzia per la Sicurezza Nazionale (NIST). [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
+L'epurazione è il processo di sovrascrittura dei dati su un dispositivo più volte con uno schema di valori binari. Questo metodo è più sicuro della cancellazione ed è consigliato per la sanificazione dei dati sensibili. Il NIST 800-88 Revisione 1 raccomanda l'utilizzo di uno strumento software che soddisfi gli standard stabiliti dall'Agenzia per la Sicurezza Nazionale (NIST). [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md
index 28bbfd064d78f..804ca3b26d2d3 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md
@@ -28,11 +28,11 @@ coverCaption: ""
### クリアリング
-クリアとは、デバイス上のデータを一連のバイナリ値で上書きするプロセスです。この方法は、物理的な破壊よりも安全性に劣るが、ほとんどのリムーバブル・メディアをサニタイズするには効果的である。NIST 800-88 Revision 1 では、国防総省(DoD)が定めた基準を満たすソフトウェアツールの使用を推奨しています。 [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
+クリアとは、デバイス上のデータを一連のバイナリ値で上書きするプロセスです。この方法は、物理的な破壊よりも安全性に劣るが、ほとんどのリムーバブル・メディアをサニタイズするには効果的である。NIST 800-88 Revision 1 では、国防総省(DoD)が定めた基準を満たすソフトウェアツールの使用を推奨しています。 [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
### パージ
-パージとは、デバイス上のデータをバイナリ値のパターンで複数回上書きする処理である。この方法はクリアよりも安全であり、機密データのサニタイズに推奨される。NIST 800-88 Revision 1 では、NIST 800-88 Revision 1 で設定された基準を満たすソフトウェア・ツールの使用を推奨しています。 [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
+パージとは、デバイス上のデータをバイナリ値のパターンで複数回上書きする処理である。この方法はクリアよりも安全であり、機密データのサニタイズに推奨される。NIST 800-88 Revision 1 では、NIST 800-88 Revision 1 で設定された基準を満たすソフトウェア・ツールの使用を推奨しています。 [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md
index 0112e9331ed8c..9c7ca02600ab7 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md
@@ -28,11 +28,11 @@ Het National Institute of Standards and Technology (NIST) heeft een richtlijn ge
### Schoonmaken
-Clearing is het proces waarbij de gegevens op een apparaat overschreven worden met een reeks binaire waarden. Deze methode is minder veilig dan fysieke vernietiging, maar is nog steeds effectief in het opschonen van de meeste verwijderbare media. NIST 800-88 Revisie 1 raadt aan een softwaretool te gebruiken dat voldoet aan de standaarden van het Ministerie van Defensie (DoD). [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
+Clearing is het proces waarbij de gegevens op een apparaat overschreven worden met een reeks binaire waarden. Deze methode is minder veilig dan fysieke vernietiging, maar is nog steeds effectief in het opschonen van de meeste verwijderbare media. NIST 800-88 Revisie 1 raadt aan een softwaretool te gebruiken dat voldoet aan de standaarden van het Ministerie van Defensie (DoD). [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
### Zuivering
-Zuiveren is het proces waarbij de gegevens op een apparaat meerdere keren worden overschreven met een patroon van binaire waarden. Deze methode is veiliger dan wissen en wordt aanbevolen voor het opschonen van gevoelige gegevens. NIST 800-88 Revisie 1 raadt aan om een softwaretool te gebruiken dat voldoet aan de normen van de [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
+Zuiveren is het proces waarbij de gegevens op een apparaat meerdere keren worden overschreven met een patroon van binaire waarden. Deze methode is veiliger dan wissen en wordt aanbevolen voor het opschonen van gevoelige gegevens. NIST 800-88 Revisie 1 raadt aan om een softwaretool te gebruiken dat voldoet aan de normen van de [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md
index dbbd5cfd371d8..a9addf5f7a936 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md
@@ -28,11 +28,11 @@ National Institute of Standards and Technology (NIST) opublikował wytyczne doty
### Czyszczenie
-Czyszczenie to proces nadpisywania danych na urządzeniu serią wartości binarnych. Metoda ta jest mniej bezpieczna niż fizyczne niszczenie, ale nadal jest skuteczna w oczyszczaniu większości nośników wymiennych. NIST 800-88 Rev. 1 zaleca korzystanie z oprogramowania, które spełnia standardy określone przez Departament Obrony (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
+Czyszczenie to proces nadpisywania danych na urządzeniu serią wartości binarnych. Metoda ta jest mniej bezpieczna niż fizyczne niszczenie, ale nadal jest skuteczna w oczyszczaniu większości nośników wymiennych. NIST 800-88 Rev. 1 zaleca korzystanie z oprogramowania, które spełnia standardy określone przez Departament Obrony (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
### Czyszczenie
-Czyszczenie to proces wielokrotnego nadpisywania danych na urządzeniu wzorcem wartości binarnych. Metoda ta jest bezpieczniejsza niż czyszczenie i jest zalecana do oczyszczania wrażliwych danych. NIST 800-88 Rev. 1 zaleca użycie narzędzia programowego, które spełnia standardy określone przez [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
+Czyszczenie to proces wielokrotnego nadpisywania danych na urządzeniu wzorcem wartości binarnych. Metoda ta jest bezpieczniejsza niż czyszczenie i jest zalecana do oczyszczania wrażliwych danych. NIST 800-88 Rev. 1 zaleca użycie narzędzia programowego, które spełnia standardy określone przez [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md
index de97a4d675e9b..6c12f029cecb2 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md
@@ -28,11 +28,11 @@ Institutul Național de Standarde și Tehnologie (NIST) a publicat un ghid de ig
### Clearing
-Curățarea este procesul de suprascriere a datelor de pe un dispozitiv cu o serie de valori binare. Această metodă este mai puțin sigură decât distrugerea fizică, dar este totuși eficientă pentru igienizarea majorității suporturilor detașabile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care respectă standardele stabilite de Departamentul Apărării (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
+Curățarea este procesul de suprascriere a datelor de pe un dispozitiv cu o serie de valori binare. Această metodă este mai puțin sigură decât distrugerea fizică, dar este totuși eficientă pentru igienizarea majorității suporturilor detașabile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care respectă standardele stabilite de Departamentul Apărării (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
### Purgare
-Purjarea este procesul de suprascriere de mai multe ori a datelor de pe un dispozitiv cu un model de valori binare. Această metodă este mai sigură decât ștergerea și este recomandată pentru curățarea datelor sensibile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care să respecte standardele stabilite de către [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
+Purjarea este procesul de suprascriere de mai multe ori a datelor de pe un dispozitiv cu un model de valori binare. Această metodă este mai sigură decât ștergerea și este recomandată pentru curățarea datelor sensibile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care să respecte standardele stabilite de către [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md
index 9b5cd789aa5b9..a9fa0b708f972 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md
@@ -28,11 +28,11 @@ coverCaption: ""
### Очистка
-Очистка - это процесс перезаписи данных на устройстве серией двоичных значений. Этот метод менее безопасен, чем физическое уничтожение, но все же эффективен для обезвреживания большинства съемных носителей. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным Министерством обороны (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
+Очистка - это процесс перезаписи данных на устройстве серией двоичных значений. Этот метод менее безопасен, чем физическое уничтожение, но все же эффективен для обезвреживания большинства съемных носителей. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным Министерством обороны (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
### Очистка
-Очистка - это процесс многократной перезаписи данных на устройстве с помощью шаблона двоичных значений. Этот метод более безопасен, чем очистка, и рекомендуется для обезвреживания конфиденциальных данных. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
+Очистка - это процесс многократной перезаписи данных на устройстве с помощью шаблона двоичных значений. Этот метод более безопасен, чем очистка, и рекомендуется для обезвреживания конфиденциальных данных. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md
index 93a915c7906ef..8c208cc2077e8 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md
@@ -28,11 +28,11 @@ coverCaption: ""
### 清除
-清除是用一系列二进制值覆盖设备上数据的过程。这种方法不如物理销毁方法安全,但仍能有效清除大多数可移动媒体。NIST 800-88 Revision 1 建议使用符合国防部 (DoD) 标准的软件工具。 [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
+清除是用一系列二进制值覆盖设备上数据的过程。这种方法不如物理销毁方法安全,但仍能有效清除大多数可移动媒体。NIST 800-88 Revision 1 建议使用符合国防部 (DoD) 标准的软件工具。 [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
### 清除
-清除是用二进制值模式多次覆盖设备上数据的过程。这种方法比清除更安全,建议用于清除敏感数据。NIST 800-88 Revision 1 建议使用符合 NIST 800-88 Revision 1 标准的软件工具。 [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
+清除是用二进制值模式多次覆盖设备上数据的过程。这种方法比清除更安全,建议用于清除敏感数据。NIST 800-88 Revision 1 建议使用符合 NIST 800-88 Revision 1 标准的软件工具。 [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/github/Automate-Sysmon/index.bn.md b/content/github/Automate-Sysmon/index.bn.md
index 92213e93a57f2..c930afeb44eb1 100644
--- a/content/github/Automate-Sysmon/index.bn.md
+++ b/content/github/Automate-Sysmon/index.bn.md
@@ -27,7 +27,7 @@ Automate-Sysmon ব্যবহার করার দুটি উপায়
স্বয়ংক্রিয় ইনস্টলেশন ব্যবহার করতে, PowerShell-এ কেবল নিম্নলিখিত কমান্ডটি চালান:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ca.md b/content/github/Automate-Sysmon/index.ca.md
index 9731571e7edf2..7e7a370408083 100644
--- a/content/github/Automate-Sysmon/index.ca.md
+++ b/content/github/Automate-Sysmon/index.ca.md
@@ -27,7 +27,7 @@ Hi ha dues maneres d'utilitzar Automate-Sysmon:
Per utilitzar la instal·lació automatitzada, només cal que executeu l'ordre següent a PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.de.md b/content/github/Automate-Sysmon/index.de.md
index c387737f63c82..97f8c62fd5756 100644
--- a/content/github/Automate-Sysmon/index.de.md
+++ b/content/github/Automate-Sysmon/index.de.md
@@ -27,7 +27,7 @@ Es gibt zwei Möglichkeiten, Automate-Sysmon zu verwenden:
Um die automatische Installation zu verwenden, führen Sie einfach den folgenden Befehl in PowerShell aus:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Dadurch wird das Automate-Sysmon-Skript automatisch heruntergeladen und ausgeführt.
diff --git a/content/github/Automate-Sysmon/index.en.md b/content/github/Automate-Sysmon/index.en.md
index cb5b3bdc98157..7a99a1d2f486c 100644
--- a/content/github/Automate-Sysmon/index.en.md
+++ b/content/github/Automate-Sysmon/index.en.md
@@ -27,7 +27,7 @@ There are two ways to use Automate-Sysmon:
To use the automated installation, simply run the following command in PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.es.md b/content/github/Automate-Sysmon/index.es.md
index 239e101328499..b2e7e89d44169 100644
--- a/content/github/Automate-Sysmon/index.es.md
+++ b/content/github/Automate-Sysmon/index.es.md
@@ -27,7 +27,7 @@ Hay dos formas de utilizar Automate-Sysmon:
Para utilizar la instalación automatizada, simplemente ejecute el siguiente comando en PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Esto descargará y ejecutará automáticamente el script Automate-Sysmon.
diff --git a/content/github/Automate-Sysmon/index.fr.md b/content/github/Automate-Sysmon/index.fr.md
index 864c1b0b92bb8..a4e4d317bdc09 100644
--- a/content/github/Automate-Sysmon/index.fr.md
+++ b/content/github/Automate-Sysmon/index.fr.md
@@ -27,7 +27,7 @@ Il y a deux façons d'utiliser Automate-Sysmon :
Pour utiliser l'installation automatisée, il suffit d'exécuter la commande suivante dans PowerShell :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Ceci téléchargera et exécutera automatiquement le script Automate-Sysmon.
diff --git a/content/github/Automate-Sysmon/index.it.md b/content/github/Automate-Sysmon/index.it.md
index f3366d29571ef..73cdbf8ca1fb4 100644
--- a/content/github/Automate-Sysmon/index.it.md
+++ b/content/github/Automate-Sysmon/index.it.md
@@ -27,7 +27,7 @@ Esistono due modi per utilizzare Automate-Sysmon:
Per utilizzare l'installazione automatica, esegui semplicemente il seguente comando in PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ja.md b/content/github/Automate-Sysmon/index.ja.md
index 61842744848b4..4dbb0a14e0a58 100644
--- a/content/github/Automate-Sysmon/index.ja.md
+++ b/content/github/Automate-Sysmon/index.ja.md
@@ -27,7 +27,7 @@ Automate-Sysmon を使用するには 2 つの方法があります。
自動インストールを使用するには、PowerShell で次のコマンドを実行するだけです。
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.nl.md b/content/github/Automate-Sysmon/index.nl.md
index a749560246496..2507cd14fdbd2 100644
--- a/content/github/Automate-Sysmon/index.nl.md
+++ b/content/github/Automate-Sysmon/index.nl.md
@@ -27,7 +27,7 @@ Er zijn twee manieren om Automate-Sysmon te gebruiken:
Om de geautomatiseerde installatie te gebruiken, voert u gewoon de volgende opdracht uit in PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Dit zal automatisch het Automate-Sysmon script downloaden en uitvoeren.
diff --git a/content/github/Automate-Sysmon/index.pa.md b/content/github/Automate-Sysmon/index.pa.md
index 894fcd21cca18..fd26b2b169a4e 100644
--- a/content/github/Automate-Sysmon/index.pa.md
+++ b/content/github/Automate-Sysmon/index.pa.md
@@ -27,7 +27,7 @@ tags: ["ਸਿਸਮੋਨ ਨੂੰ ਆਟੋਮੈਟਿਕ ਕਰੋ", "ਸ
ਆਟੋਮੈਟਿਕ ਇੰਸਟਾਲੇਸ਼ਨ ਦੀ ਵਰਤੋਂ ਕਰਨ ਲਈ, PowerShell ਵਿੱਚ ਸਿਰਫ਼ ਹੇਠ ਦਿੱਤੀ ਕਮਾਂਡ ਚਲਾਓ:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.pl.md b/content/github/Automate-Sysmon/index.pl.md
index 3f50b06a7d201..dc080c99d0e7d 100644
--- a/content/github/Automate-Sysmon/index.pl.md
+++ b/content/github/Automate-Sysmon/index.pl.md
@@ -27,7 +27,7 @@ Istnieją dwa sposoby korzystania z Automate-Sysmon:
Aby użyć automatycznej instalacji, wystarczy uruchomić następujące polecenie w PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Spowoduje to automatyczne pobranie i uruchomienie skryptu Automate-Sysmon.
diff --git a/content/github/Automate-Sysmon/index.pt.md b/content/github/Automate-Sysmon/index.pt.md
index 480bd76af30d6..426df8096f8eb 100644
--- a/content/github/Automate-Sysmon/index.pt.md
+++ b/content/github/Automate-Sysmon/index.pt.md
@@ -27,7 +27,7 @@ Existem duas maneiras de usar o Automate-Sysmon:
Para usar a instalação automatizada, basta executar o seguinte comando no PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ro.md b/content/github/Automate-Sysmon/index.ro.md
index a1845cbbf29e3..eb5f9bf5a52ff 100644
--- a/content/github/Automate-Sysmon/index.ro.md
+++ b/content/github/Automate-Sysmon/index.ro.md
@@ -27,7 +27,7 @@ Există două moduri de a utiliza Automate-Sysmon:
Pentru a utiliza instalarea automată, pur și simplu rulați următoarea comandă în PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ru.md b/content/github/Automate-Sysmon/index.ru.md
index 2e97a0a804a09..f8f4ee3466260 100644
--- a/content/github/Automate-Sysmon/index.ru.md
+++ b/content/github/Automate-Sysmon/index.ru.md
@@ -27,7 +27,7 @@ Sysmon — это инструмент мониторинга системы, к
Чтобы использовать автоматическую установку, просто выполните следующую команду в PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.zh.md b/content/github/Automate-Sysmon/index.zh.md
index 8b98d3882004e..3fc6284097f60 100644
--- a/content/github/Automate-Sysmon/index.zh.md
+++ b/content/github/Automate-Sysmon/index.zh.md
@@ -27,7 +27,7 @@ Automate-Sysmon 有两种使用方式:
要使用自动安装,只需在 PowerShell 中运行以下命令:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Offline-PS-ActiveDirectory-Install/index.en.md b/content/github/Offline-PS-ActiveDirectory-Install/index.en.md
index 25bb6f338c692..d6d5b1a2aba50 100644
--- a/content/github/Offline-PS-ActiveDirectory-Install/index.en.md
+++ b/content/github/Offline-PS-ActiveDirectory-Install/index.en.md
@@ -42,15 +42,15 @@ The script will perform the following actions:
- Copy the necessary files and modules to the appropriate locations on your system.
- Unblock the new PowerShell modules and DLLs.
-- [Import the Active Directory module](https://simeononsecurity.ch/articles/active-directory-module-powershell-installation-usage-guide/) and DLLs using the `Import-Module` command.
+- [Import the Active Directory module](https://simeononsecurity.com/articles/active-directory-module-powershell-installation-usage-guide/) and DLLs using the `Import-Module` command.
- Once the script execution is complete, you will have the Active Directory PowerShell module installed on your Windows 10 machine.
**Verifying the Installation**
-To verify that the [Active Directory PowerShell module](https://simeononsecurity.ch/articles/active-directory-module-powershell-installation-usage-guide/) is installed correctly, follow these steps:
+To verify that the [Active Directory PowerShell module](https://simeononsecurity.com/articles/active-directory-module-powershell-installation-usage-guide/) is installed correctly, follow these steps:
1. Open a PowerShell terminal.
-2. Run the command [`Import-Module ActiveDirectory`](https://simeononsecurity.ch/articles/active-directory-module-powershell-installation-usage-guide/).
+2. Run the command [`Import-Module ActiveDirectory`](https://simeononsecurity.com/articles/active-directory-module-powershell-installation-usage-guide/).
3. If no errors are displayed, the module is successfully installed.
**Conclusion**
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.de.md b/content/github/System-Wide-Windows-Ad-Blocker/index.de.md
index 552ea999fcf74..4d352e01eba6e 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.de.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.de.md
@@ -27,6 +27,6 @@ Dieses Skript ist ein Windows PowerShell-Skript, das die Datei "StevenBlack/host
#### Automatisch installieren:
Führen Sie die neueste Version des Skripts automatisch aus:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.en.md b/content/github/System-Wide-Windows-Ad-Blocker/index.en.md
index a6e57ae2db373..f35dc453e179d 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.en.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.en.md
@@ -27,6 +27,6 @@ This script is a Windows PowerShell script that downloads and applies the "Steve
#### Automated install:
Run the latest version of the script automatically:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.es.md b/content/github/System-Wide-Windows-Ad-Blocker/index.es.md
index 624255540c3e5..8295d150fa959 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.es.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.es.md
@@ -27,6 +27,6 @@ Este script es un script de Windows PowerShell que descarga y aplica el archivo
#### Instalación automática:
Ejecuta automáticamente la última versión del script:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md b/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md
index 02be56decffe9..6fdf41ece8052 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md
@@ -27,6 +27,6 @@ Ce script est un script Windows PowerShell qui télécharge et applique le fichi
#### Installation automatisée :
Exécutez automatiquement la dernière version du script :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/Windows-Branding-Script/index.de.md b/content/github/Windows-Branding-Script/index.de.md
index cedc3ab80e5c7..fb97f77b2a5c3 100644
--- a/content/github/Windows-Branding-Script/index.de.md
+++ b/content/github/Windows-Branding-Script/index.de.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automatisierte Installation:
Das Skript kann aus dem extrahierten GitHub-Download wie folgt gestartet werden:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.en.md b/content/github/Windows-Branding-Script/index.en.md
index c14ab2cd126c2..f954496cbffb3 100644
--- a/content/github/Windows-Branding-Script/index.en.md
+++ b/content/github/Windows-Branding-Script/index.en.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.es.md b/content/github/Windows-Branding-Script/index.es.md
index 2b7ce802ce37c..b14fbd49d1728 100644
--- a/content/github/Windows-Branding-Script/index.es.md
+++ b/content/github/Windows-Branding-Script/index.es.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.fr.md b/content/github/Windows-Branding-Script/index.fr.md
index bdd545a79fc24..3e512ec658a40 100644
--- a/content/github/Windows-Branding-Script/index.fr.md
+++ b/content/github/Windows-Branding-Script/index.fr.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.it.md b/content/github/Windows-Branding-Script/index.it.md
index efeb90537ced7..619255411d275 100644
--- a/content/github/Windows-Branding-Script/index.it.md
+++ b/content/github/Windows-Branding-Script/index.it.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installazione automatica:
Lo script può essere lanciato dal download estratto da GitHub in questo modo:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.ja.md b/content/github/Windows-Branding-Script/index.ja.md
index 237e3f0c868ac..fb29a8c8cca68 100644
--- a/content/github/Windows-Branding-Script/index.ja.md
+++ b/content/github/Windows-Branding-Script/index.ja.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### 自動インストール:
スクリプトは、GitHubからダウンロードしたものを次のように起動することができます:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.nl.md b/content/github/Windows-Branding-Script/index.nl.md
index 4ccb0ca491a5e..1709e5b100df7 100644
--- a/content/github/Windows-Branding-Script/index.nl.md
+++ b/content/github/Windows-Branding-Script/index.nl.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Geautomatiseerde installatie:
Het script kan vanaf de uitgepakte GitHub-download als volgt worden gestart:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.pl.md b/content/github/Windows-Branding-Script/index.pl.md
index ef09a923330dc..dd77f482d7730 100644
--- a/content/github/Windows-Branding-Script/index.pl.md
+++ b/content/github/Windows-Branding-Script/index.pl.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automatyczna instalacja:
Skrypt można uruchomić z wyodrębnionego pliku do pobrania z GitHub w następujący sposób:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.ro.md b/content/github/Windows-Branding-Script/index.ro.md
index b99e4c22fdc48..30a7197886367 100644
--- a/content/github/Windows-Branding-Script/index.ro.md
+++ b/content/github/Windows-Branding-Script/index.ro.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
Scriptul poate fi lansat din descărcarea extrasă de pe GitHub astfel:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.ru.md b/content/github/Windows-Branding-Script/index.ru.md
index 56bdb8772e171..e53b2b89185aa 100644
--- a/content/github/Windows-Branding-Script/index.ru.md
+++ b/content/github/Windows-Branding-Script/index.ru.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Автоматическая установка:
Скрипт может быть запущен из распакованной загрузки с GitHub следующим образом:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.zh.md b/content/github/Windows-Branding-Script/index.zh.md
index 55fa87ecc0e59..3840e47199187 100644
--- a/content/github/Windows-Branding-Script/index.zh.md
+++ b/content/github/Windows-Branding-Script/index.zh.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
#### 自动安装:
可以像这样从 GitHub 下载的提取文件中启动脚本:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Defender-Application-Control-Hardening/index.en.md b/content/github/Windows-Defender-Application-Control-Hardening/index.en.md
index 68e444914de4b..9c99e35c1b738 100644
--- a/content/github/Windows-Defender-Application-Control-Hardening/index.en.md
+++ b/content/github/Windows-Defender-Application-Control-Hardening/index.en.md
@@ -11,7 +11,7 @@ tags: ["Windows Defender Application Control WDAC Hardening", "PowerShell", "Pow
## Notes:
- Windows Server 2016/2019 or anything before version 1903 only support a single legacy policy at a time.
-- Windows Server Core edition supports [WDAC](https://simeononsecurity.ch/til/2022-05-18/) but some components that depend on AppLocker won’t work
+- Windows Server Core edition supports [WDAC](https://simeononsecurity.com/til/2022-05-18/) but some components that depend on AppLocker won’t work
- Please read the [Recommended Reading](https://github.com/simeononsecurity/Windows-Defender-Application-Control-Hardening#recommended-reading) before implementing or even testing.
## A list of scripts and tools this collection utilizes:
diff --git a/content/github/Windows-Hardening-CTF/index.en.md b/content/github/Windows-Hardening-CTF/index.en.md
index 5e1662de9ba34..f6a18cc3d89dc 100644
--- a/content/github/Windows-Hardening-CTF/index.en.md
+++ b/content/github/Windows-Hardening-CTF/index.en.md
@@ -19,7 +19,7 @@ A windows hardening script that makes it difficult and more annoying to compromi
- Disables SMB v2
- Disables TCP Timestamps
- Disables WSMAN and PSRemoting
-- [Enables AppLocker with NSA Recommended Policies](https://simeononsecurity.ch/github/applocker-hardening/)
+- [Enables AppLocker with NSA Recommended Policies](https://simeononsecurity.com/github/applocker-hardening/)
- Enables Best practice Windows Logging and Security Controls
- Enables DEP
- Enables EMET Configurations (Only applies to systems with EMET installed)
diff --git a/content/github/Windows-Optimize-Debloat/index.de.md b/content/github/Windows-Optimize-Debloat/index.de.md
index 05242aa5bac7e..c168134413f1d 100644
--- a/content/github/Windows-Optimize-Debloat/index.de.md
+++ b/content/github/Windows-Optimize-Debloat/index.de.md
@@ -59,7 +59,7 @@ Wenn Sie diese Dienste dennoch nutzen möchten, finden Sie die Lösung in den fo
### Automatisierte Installation:
Das Skript kann wie folgt aus dem extrahierten GitHub-Download gestartet werden:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Manuelle Installation:
Wenn das Skript manuell heruntergeladen wird, muss es von einer administrativen Powershell in dem Verzeichnis gestartet werden, das alle Dateien aus dem [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.en.md b/content/github/Windows-Optimize-Debloat/index.en.md
index 2a55ae6eaa3ef..36e11c45c60e3 100644
--- a/content/github/Windows-Optimize-Debloat/index.en.md
+++ b/content/github/Windows-Optimize-Debloat/index.en.md
@@ -59,7 +59,7 @@ However, if you still wish to use these services see the following issue tickets
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Manual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.es.md b/content/github/Windows-Optimize-Debloat/index.es.md
index de87f05eecb42..0d10421242953 100644
--- a/content/github/Windows-Optimize-Debloat/index.es.md
+++ b/content/github/Windows-Optimize-Debloat/index.es.md
@@ -59,7 +59,7 @@ Sin embargo, si usted todavía desea utilizar estos servicios ver los siguientes
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Instalación manual:
Si se descarga manualmente, el script debe ser lanzado desde un powershell administrativo en el directorio que contiene todos los archivos del [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.fr.md b/content/github/Windows-Optimize-Debloat/index.fr.md
index 5e00b09d02f47..73144d6a13e55 100644
--- a/content/github/Windows-Optimize-Debloat/index.fr.md
+++ b/content/github/Windows-Optimize-Debloat/index.fr.md
@@ -59,7 +59,7 @@ Cependant, si vous souhaitez toujours utiliser ces services, consultez les ticke
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Installation manuelle :
S'il est téléchargé manuellement, le script doit être lancé à partir d'un powerhell d'administration dans le répertoire contenant tous les fichiers du fichier [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.it.md b/content/github/Windows-Optimize-Debloat/index.it.md
index ab32e5fa2bebd..cffc9f82e20ef 100644
--- a/content/github/Windows-Optimize-Debloat/index.it.md
+++ b/content/github/Windows-Optimize-Debloat/index.it.md
@@ -59,7 +59,7 @@ Tuttavia, se si desidera utilizzare questi servizi, consultare i seguenti ticket
### Installazione automatica:
Lo script può essere lanciato dal download estratto da GitHub in questo modo:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Installazione manuale:
Se scaricato manualmente, lo script deve essere lanciato da una powershell amministrativa nella directory contenente tutti i file del file [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.ja.md b/content/github/Windows-Optimize-Debloat/index.ja.md
index d7486df8cdf13..39fb88ff5d9a3 100644
--- a/content/github/Windows-Optimize-Debloat/index.ja.md
+++ b/content/github/Windows-Optimize-Debloat/index.ja.md
@@ -59,7 +59,7 @@ Windows 10 と 11 は、箱から出したままでは侵略的で安全でな
### 自動インストール:
自動インストール:GitHubからダウンロードしたスクリプトを、以下のように起動します:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### 手動でインストールします:
手動でダウンロードした場合、スクリプトは、管理用パワーシェルから、以下のすべてのファイルが含まれるディレクトリで起動する必要があります。 [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.nl.md b/content/github/Windows-Optimize-Debloat/index.nl.md
index 38720aea48e83..6034676de78f8 100644
--- a/content/github/Windows-Optimize-Debloat/index.nl.md
+++ b/content/github/Windows-Optimize-Debloat/index.nl.md
@@ -59,7 +59,7 @@ Als u deze diensten toch wilt gebruiken, zie dan de volgende issue tickets voor
### Geautomatiseerde installatie:
Het script kan vanaf de uitgepakte GitHub-download als volgt worden gestart:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Handmatige installatie:
Indien handmatig gedownload, moet het script worden gestart vanuit een administratieve powershell in de directory die alle bestanden van de [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.pl.md b/content/github/Windows-Optimize-Debloat/index.pl.md
index 394b953160009..86db842a25f57 100644
--- a/content/github/Windows-Optimize-Debloat/index.pl.md
+++ b/content/github/Windows-Optimize-Debloat/index.pl.md
@@ -59,7 +59,7 @@ Jeśli jednak nadal chcesz korzystać z tych usług, zapoznaj się z poniższymi
### Automatyczna instalacja:
Skrypt można uruchomić z wyodrębnionego pliku do pobrania z GitHub w następujący sposób:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Instalacja ręczna:
W przypadku ręcznego pobrania skrypt należy uruchomić z poziomu administracyjnego powershell w katalogu zawierającym wszystkie pliki z pliku [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.ro.md b/content/github/Windows-Optimize-Debloat/index.ro.md
index 5689713444d6b..c4411b16a2f18 100644
--- a/content/github/Windows-Optimize-Debloat/index.ro.md
+++ b/content/github/Windows-Optimize-Debloat/index.ro.md
@@ -59,7 +59,7 @@ Cu toate acestea, dacă doriți totuși să utilizați aceste servicii, consulta
### Automated Install:
Scriptul poate fi lansat din descărcarea extrasă de pe GitHub, astfel:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Instalare manuală:
Dacă este descărcat manual, scriptul trebuie lansat dintr-un powershell administrativ în directorul care conține toate fișierele din fișierul [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.ru.md b/content/github/Windows-Optimize-Debloat/index.ru.md
index df0beed6abc39..3aa8020efa491 100644
--- a/content/github/Windows-Optimize-Debloat/index.ru.md
+++ b/content/github/Windows-Optimize-Debloat/index.ru.md
@@ -59,7 +59,7 @@ Windows 10 и 11 - это инвазивные и небезопасные оп
### Автоматическая установка:
Скрипт может быть запущен из распакованной загрузки с GitHub следующим образом:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Установка вручную:
При ручной загрузке скрипт должен быть запущен из административного powershell в директории, содержащей все файлы из файла [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.zh.md b/content/github/Windows-Optimize-Debloat/index.zh.md
index ab0dd0fe0bf8d..5977f4b4a802b 100644
--- a/content/github/Windows-Optimize-Debloat/index.zh.md
+++ b/content/github/Windows-Optimize-Debloat/index.zh.md
@@ -59,7 +59,7 @@ tags: ["视窗-优化-去毛刺", "Windows 优化", "浮动窗口", "加速 Wind
#### 自动安装:
可以像这样从 GitHub 下载的提取文件中启动脚本:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
#### 手动安装:
如果是手动下载,则必须在包含来自 [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Harden-Debloat/index.ar.md b/content/github/Windows-Optimize-Harden-Debloat/index.ar.md
index 8f0d9a431a3e2..e63bf912a9ef5 100644
--- a/content/github/Windows-Optimize-Harden-Debloat/index.ar.md
+++ b/content/github/Windows-Optimize-Harden-Debloat/index.ar.md
@@ -175,7 +175,7 @@ tags: ["تحسين Windows", "تصلب النوافذ", "الويندوز الم
### واجهة المستخدم الرسومية - التثبيت الموجه:
قم بتنزيل أحدث إصدار[here](https://github.com/simeononsecurity/Windows-Optimize-Harden-Debloat-GUI/releases/)اختر الخيارات التي تريدها واضغط على تنفيذ.
}}
### CyberSecurity Career Outlooks and Information
-#### [What Does a Cybersecurity Career Path Look Like?](https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/)
+#### [What Does a Cybersecurity Career Path Look Like?](https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/)
- Insights into the various career paths available in cybersecurity.
-#### [Cybersecurity Analyst Salaries: Entry Level to Pro](https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/)
+#### [Cybersecurity Analyst Salaries: Entry Level to Pro](https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/)
- Understanding the salary ranges for cybersecurity analysts.
-#### [What Does a Cybersecurity Expert Do?](https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/)
+#### [What Does a Cybersecurity Expert Do?](https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/)
- Explore the roles and responsibilities of cybersecurity experts.
@@ -81,33 +81,33 @@ When pursuing a career in cybersecurity, one important consideration is obtainin
### Degrees
-#### [Do I Need a Degree for a Cybersecurity Job?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/do-i-need-a-degree-for-a-cybersecurity-job/)
+#### [Do I Need a Degree for a Cybersecurity Job?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/do-i-need-a-degree-for-a-cybersecurity-job/)
- Find out whether having a degree is necessary to pursue a career in cybersecurity and learn about alternative paths.
-#### [Which Courses Should I Take for a Job in Cybersecurity?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/which-courses-should-i-take-for-a-job-in-cybersecurity/)
+#### [Which Courses Should I Take for a Job in Cybersecurity?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/which-courses-should-i-take-for-a-job-in-cybersecurity/)
- Discover recommended courses and educational resources to enhance your skills and knowledge in cybersecurity.
### Certifications
-#### [Are Certifications Needed for a Cybersecurity Career?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/)
+#### [Are Certifications Needed for a Cybersecurity Career?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/)
- Explore the importance of certifications in the cybersecurity field and their impact on career opportunities.
-#### [Performance-Based Questions (PBQs) and Cybersecurity Certifications](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/performance-based-questions-pbqs-and-cybersecurity-certifications/)
+#### [Performance-Based Questions (PBQs) and Cybersecurity Certifications](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/performance-based-questions-pbqs-and-cybersecurity-certifications/)
- Learn about performance-based questions (PBQs) in cybersecurity certifications and how to prepare for them.
-#### [CEUs in Cybersecurity: What They Are and Why You Need Them](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/ceus-in-cybersecurity-what-they-are-and-why-you-need-them/)
+#### [CEUs in Cybersecurity: What They Are and Why You Need Them](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/ceus-in-cybersecurity-what-they-are-and-why-you-need-them/)
- Understand the concept of Continuing Education Units (CEUs) in cybersecurity and their importance for professional development.
#### Certification Guides and Tips
We've included a few tips and tricks for these certifications below:
-- [Passing CompTIA's A+](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/)
-- [Passing CompTIA's Security+](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
-- [Passing CompTIA's Linux+](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/)
-- [Passing EC-Council's CEH](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [Passing ISC2's CISSP](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/)
+- [Passing CompTIA's A+](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/)
+- [Passing CompTIA's Security+](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [Passing CompTIA's Linux+](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/)
+- [Passing EC-Council's CEH](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [Passing ISC2's CISSP](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/)
##### Certification Practice Tests
@@ -132,11 +132,11 @@ We've included a few tips and tricks for these certifications below:
### Bootcamps
-#### [Are Cybersecurity Bootcamps Worth it?](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it)
+#### [Are Cybersecurity Bootcamps Worth it?](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it)
### Other Training Types
-#### [Army Cybersecurity Awareness Training: What You Need to Know](https://simeononsecurity.ch/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/army-cybersecurity-awareness-training-what-you-need-to-know)
+#### [Army Cybersecurity Awareness Training: What You Need to Know](https://simeononsecurity.com/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/army-cybersecurity-awareness-training-what-you-need-to-know)
- Get insights into the cybersecurity awareness training provided by the army and its relevance in today's digital landscape.
{{< inarticle-dark >}}
@@ -145,61 +145,61 @@ We've included a few tips and tricks for these certifications below:
Securing a job in cybersecurity requires a combination of knowledge, experience, and preparation. In this section, you'll discover valuable resources and insights to help you navigate the job market, prepare for interviews, and increase your chances of landing an entry-level or remote cybersecurity position.
-- [Navigating Early Career Job Market: Overcoming Challenges and Securing Opportunities](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/addressing-the-challenges-in-the-early-career-job-market/)
+- [Navigating Early Career Job Market: Overcoming Challenges and Securing Opportunities](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/addressing-the-challenges-in-the-early-career-job-market/)
- Discover strategies to overcome challenges in the early career job market, acquire valuable skills, and secure desirable opportunities for success.
-- [Navigating the Changing Cybersecurity Landscape: Challenges and Strategies for Early Career Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-evolving-landscape-what-works-today-vs-what-worked-10-years-ago/)
+- [Navigating the Changing Cybersecurity Landscape: Challenges and Strategies for Early Career Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-evolving-landscape-what-works-today-vs-what-worked-10-years-ago/)
- Explore the evolving cybersecurity industry and its impact on early career professionals, with practical guidance on addressing challenges and thriving in today's landscape.
### Step-by-Step Into the Cyber Security Career Path
-- [Step-by-Step Into the Cyber Security Career Path](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/step-by-step-into-to-cyber-security-career-path/)
+- [Step-by-Step Into the Cyber Security Career Path](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/step-by-step-into-to-cyber-security-career-path/)
- Follow a comprehensive guide outlining the essential steps and milestones to pursue a career in cyber security.
### Interview Preparation
#### Cyber Security Interview Questions
-- [Cyber Security Interview Questions](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/)
+- [Cyber Security Interview Questions](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/)
- Familiarize yourself with common interview questions in the field of cybersecurity and prepare for successful interviews.
#### Resume Writing
-- [Resume Writing Tips for Cyber Security Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/)
+- [Resume Writing Tips for Cyber Security Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/)
- Enhance your chances of landing your dream job with these expert resume writing tips for cybersecurity, software development, and IT professionals.
#### Networking and Professional Connections
-- [Networking Tips for Landing a Job in Cyber Security](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/networking-tips-for-landing-a-job-in-cybersecurity/)
+- [Networking Tips for Landing a Job in Cyber Security](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/networking-tips-for-landing-a-job-in-cybersecurity/)
- Unlock valuable networking tips to secure your dream job in cybersecurity, connecting with professionals and discovering hidden opportunities.
### Transitioning to Cybersecurity
#### How to Transition from IT to Cybersecurity
-- [How to Transition from IT to Cybersecurity](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-transition-from-it-to-cybersecurity/)
+- [How to Transition from IT to Cybersecurity](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-transition-from-it-to-cybersecurity/)
- Learn about the steps and considerations involved in making a successful transition from IT to a career in cybersecurity.
#### Mastering Cybersecurity: The Role of Systems Administration and Practical Experience
-- [Mastering Cybersecurity: The Role of Systems Administration and Practical Experience](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/building-a-path-to-cybersecurity-and-the-benefit-of-practical-experience/)
+- [Mastering Cybersecurity: The Role of Systems Administration and Practical Experience](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/building-a-path-to-cybersecurity-and-the-benefit-of-practical-experience/)
- Gain insights into the role of systems administration and practical experience in building a successful career in cybersecurity.
### Best Locations for Cybersecurity Jobs
#### The 7 Top Locations for Cyber Security Jobs in the US 2023: Best Cities for Professionals
-- [The 7 Top Locations for Cyber Security Jobs in the US 2023: Best Cities for Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-in-the-united-states)
+- [The 7 Top Locations for Cyber Security Jobs in the US 2023: Best Cities for Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-in-the-united-states)
- Discover the best locations for cybersecurity jobs in the United States in 2023, from Washington, D.C. to San Francisco, with abundant opportunities and industry growth.
#### The Top 5 Locations Worldwide for Cybersecurity Jobs in 2023: Best Cities for Professionals
-- [The Top 5 Locations Worldwide for Cybersecurity Jobs in 2023: Best Cities for Professionals](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-worldwide)
+- [The Top 5 Locations Worldwide for Cybersecurity Jobs in 2023: Best Cities for Professionals](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/the-best-locations-for-cybersecurity-jobs-worldwide)
- Discover the best locations worldwide for cybersecurity jobs in 2023, from London to Singapore, with abundant opportunities and industry growth.
### Cybersecurity Internships
#### How to Find and Get Cybersecurity Internships
-- [How to Find and Get Cybersecurity Internships](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-how-to-get-cybersecurity-internships/)
+- [How to Find and Get Cybersecurity Internships](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-how-to-get-cybersecurity-internships/)
- Discover strategies and resources for finding and securing cybersecurity internships to gain practical experience.
### Entry-Level Cyber Security Jobs
#### Preparation and Resources for Entry-Level Cyber Security Jobs
-- [Preparation and Resources for Entry-Level Cyber Security Jobs](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/preparation-and-resources-for-entry-level-cyber-security-jobs/)
+- [Preparation and Resources for Entry-Level Cyber Security Jobs](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/preparation-and-resources-for-entry-level-cyber-security-jobs/)
- Get tips and resources to prepare for entry-level cyber security positions and increase your chances of landing a job.
### Remote Cybersecurity Jobs
#### How to Find and Get the Best Remote Cybersecurity Job
-- [How to Find and Get the Best Remote Cybersecurity Job](https://simeononsecurity.ch/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-get-the-best-remote-cybersecurity-job/)
+- [How to Find and Get the Best Remote Cybersecurity Job](https://simeononsecurity.com/cyber-security-career-playbook/getting-a-job-in-cyber-security/how-to-find-and-get-the-best-remote-cybersecurity-job/)
- Explore strategies and resources to find and secure remote cybersecurity jobs that align with your career goals.
{{< inarticle-dark >}}
@@ -209,35 +209,35 @@ Securing a job in cybersecurity requires a combination of knowledge, experience,
As a cybersecurity professional, continuous learning and growth are key to advancing your career. This section focuses on strategies for earning certifications, learning new skills, staying updated on emerging threats and vulnerabilities, and education on the regulations that define and regulate what you do, enabling you to progress and excel in your cybersecurity journey.
### New Skills and Certifications
-#### [Earning Certifications and Learning New Skills as a Cyber Security Professional](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/earning-certifications-and-learning-new-skills-as-a-cyber-security-professional/)
+#### [Earning Certifications and Learning New Skills as a Cyber Security Professional](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/earning-certifications-and-learning-new-skills-as-a-cyber-security-professional/)
- Discover the importance of earning certifications and continuously expanding your skills as a cybersecurity professional.
### Advanced Topics
-#### [How to Learn About CVEs and Threat Actors](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/how-to-learn-about-cves-and-threat-actors/)
+#### [How to Learn About CVEs and Threat Actors](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/how-to-learn-about-cves-and-threat-actors/)
- Gain insights into Common Vulnerabilities and Exposures (CVEs/) and threat actors, and learn how to stay updated on emerging threats.
-#### [Implementing the NICE Cybersecurity Framework: Best Practices for Enhanced Cyber Defense](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/implementing-the-nice-cybersecurity-framework/)
+#### [Implementing the NICE Cybersecurity Framework: Best Practices for Enhanced Cyber Defense](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/implementing-the-nice-cybersecurity-framework/)
- Discover the key steps to effectively implement the NICE Cybersecurity Framework and fortify your organization's defenses against cyber threats..
### Understanding Regulations, Acts, and Guidelines
-#### [Federal Information Security Management Act (FISMA) Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/)
-Learn about the [Federal Information Security Management Act (FISMA)](https://simeononsecurity.ch/articles/fisma-summarized/), a U.S. federal law that establishes cybersecurity requirements for government agencies.
+#### [Federal Information Security Management Act (FISMA) Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/)
+Learn about the [Federal Information Security Management Act (FISMA)](https://simeononsecurity.com/articles/fisma-summarized/), a U.S. federal law that establishes cybersecurity requirements for government agencies.
-#### [NIST SP 800-181 - Cyber Security Workforce Framework Overview and Comparison with the DCWF](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-sp-800-181-workforce-framework-for-cybersecurty-and-the-dod-dcwf/)
+#### [NIST SP 800-181 - Cyber Security Workforce Framework Overview and Comparison with the DCWF](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-sp-800-181-workforce-framework-for-cybersecurty-and-the-dod-dcwf/)
- Discover the comprehensive evaluation and development frameworks for cybersecurity workforce: NICE and DoD DCWF, empowering organizations with skilled professionals.
-#### [DoD 8140-03 - Cyberspace Workforce Qualifications and Management Program - Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-manual-8140.03-cyberspace-workforce-qualification-and-management-program/)
+#### [DoD 8140-03 - Cyberspace Workforce Qualifications and Management Program - Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-manual-8140.03-cyberspace-workforce-qualification-and-management-program/)
- Discover the key aspects of the Department of Defense (DoD) 8140-03 manual, which outlines qualifications and management for the cyberspace workforce.
-#### [Navigating Workforce Frameworks: Implications for Cybersecurity Pros](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/workforce-frameworks-and-the-challenges/)
+#### [Navigating Workforce Frameworks: Implications for Cybersecurity Pros](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/workforce-frameworks-and-the-challenges/)
- Explore the impact of changing workforce frameworks on cybersecurity professionals and the challenges they face in meeting new requirements.
-#### [DoD 5220.22-m - Data Sanitization - Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-5220.22-m-data-sanitization-summarized)
-- Explore the summary of [DoD 5220.22-m](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/), a directive that provides guidance on data sanitization.
+#### [DoD 5220.22-m - Data Sanitization - Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/dod-5220.22-m-data-sanitization-summarized)
+- Explore the summary of [DoD 5220.22-m](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/), a directive that provides guidance on data sanitization.
-#### [NIST 800-88 - Guidelines for Media Sanitization - Summarized](https://simeononsecurity.ch/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/)
+#### [NIST 800-88 - Guidelines for Media Sanitization - Summarized](https://simeononsecurity.com/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/)
- Learn about the summarized guidelines outlined in NIST 800-88 for media sanitization.
{{< inarticle-dark >}}
@@ -246,33 +246,33 @@ Learn about the [Federal Information Security Management Act (FISMA)](https://si
This section provides valuable resources and insights on managing a cyber security team, including tips for **building and managing a cybersecurity team** and best practices for **managing a cyber security team**.
-- [Building a Cyber Security Team](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/building-and-managing-a-cybersecurity-team/):
+- [Building a Cyber Security Team](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/building-and-managing-a-cybersecurity-team/):
- This resource offers guidance on building a cyber security team, covering topics such as team composition, skillsets, and recruitment strategies.
-- [Managing a Cyber Security Team](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/managing-a-cyber-security-team/):
+- [Managing a Cyber Security Team](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/managing-a-cyber-security-team/):
- Explore effective techniques and strategies for managing a cyber security team, including team leadership, performance management, and fostering a strong security culture.
### Outsourcing vs. In-house Cyber Security
When considering whether to outsource or keep cybersecurity tasks in-house, it is important to evaluate the advantages and drawbacks. These resources provide insights into the **outsourcing vs. in-house** decision-making process.
-- [Is Outsourcing Cyber Security Efforts a Good Idea?](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/):
- - This article discusses the pros and cons of [outsourcing cyber security](https://simeononsecurity.ch/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) efforts and provides guidance on making an informed decision.
+- [Is Outsourcing Cyber Security Efforts a Good Idea?](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/):
+ - This article discusses the pros and cons of [outsourcing cyber security](https://simeononsecurity.com/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) efforts and provides guidance on making an informed decision.
-- [Critical Cyber Security Roles that You Should Have In-House](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/cybersecurity-tasks-that-shouldnt-be-outsourced/):
+- [Critical Cyber Security Roles that You Should Have In-House](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/cybersecurity-tasks-that-shouldnt-be-outsourced/):
- Discover the **critical cyber security roles** that are best kept in-house to ensure control, expertise, and alignment with organizational objectives.
### Developing Plans and Programs
Developing robust cyber security plans and programs is essential for effective security management. These resources offer guidance on creating **cyber security policies, procedures, programs**, and **incident response programs**.
-- [How to Develop Cyber Security Policies, Procedures, and Programs](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/):
+- [How to Develop Cyber Security Policies, Procedures, and Programs](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/):
- Learn how to develop comprehensive cyber security policies, procedures, and programs to establish a strong security foundation within your organization.
-- [How to Build a Cyber Security Awareness and Training Program](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/):
+- [How to Build a Cyber Security Awareness and Training Program](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/):
- Learn how to build a comprehensive security awareness training program to protect your organization from cyber threats and empower employees.
-- [How to Develop an Incident Response Program](https://simeononsecurity.ch/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/):
+- [How to Develop an Incident Response Program](https://simeononsecurity.com/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/):
- This resource provides guidance on building an effective incident response program, including planning, team roles, and incident handling best practices.
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook-start/pageschema.html b/content/cyber-security-career-playbook-start/pageschema.html
index e9b8399eff3f6..b7f11302468ef 100644
--- a/content/cyber-security-career-playbook-start/pageschema.html
+++ b/content/cyber-security-career-playbook-start/pageschema.html
@@ -19,7 +19,7 @@
"bestRating": "5",
"ratingCount": "100"
},
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook-start",
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook-start",
"author": {
"@type": "Person",
"name": "SimeonOnSecurity"
@@ -38,7 +38,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "Simplified explanations of cybersecurity concepts for beginners.",
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/"
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/"
}
},
{
@@ -47,7 +47,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "Cybersecurity is the practice of protecting computers, servers, networks, and data from digital attacks or unauthorized access.",
- "url": "https://simeononsecurity.ch/articles/what-is-cybersecurity/"
+ "url": "https://simeononsecurity.com/articles/what-is-cybersecurity/"
}
},
{
@@ -56,7 +56,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "Common cybersecurity threats include viruses, malware, phishing attacks, ransomware, and social engineering. These threats can compromise the security of systems, steal data, or cause other harmful effects.",
- "url": "https://simeononsecurity.ch/articles/cybersecurity-threats-to-watch-out-for-in-2023/"
+ "url": "https://simeononsecurity.com/articles/cybersecurity-threats-to-watch-out-for-in-2023/"
}
},
{
@@ -65,7 +65,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "To protect yourself from cybersecurity threats, you can follow best practices such as using strong and unique passwords, enabling two-factor authentication, keeping your software up to date, being cautious of suspicious emails or links, and using antivirus software.",
- "url": "https://simeononsecurity.ch/articles/safe-social-media-practices-and-protecting-your-privacy-online/"
+ "url": "https://simeononsecurity.com/articles/safe-social-media-practices-and-protecting-your-privacy-online/"
}
},
{
@@ -74,7 +74,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "A cybersecurity career involves working to protect computer systems, networks, and data from cyber threats. It includes roles such as cybersecurity analyst, penetration tester, incident responder, and security architect.",
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/"
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-career-path-look-like/"
}
},
{
@@ -83,7 +83,7 @@
"acceptedAnswer": {
"@type": "Answer",
"text": "To start a career in cybersecurity, you can pursue education and certifications in the field, gain practical experience through internships or entry-level positions, participate in cybersecurity competitions and challenges, and stay updated with the latest industry trends and technologies.",
- "url": "https://simeononsecurity.ch/cyber-security-career-playbook-start/"
+ "url": "https://simeononsecurity.com/cyber-security-career-playbook-start/"
}
}
]
diff --git a/content/cyber-security-career-playbook/_index.en.md b/content/cyber-security-career-playbook/_index.en.md
index 17a7cc9effc80..af0021bbe5c0e 100644
--- a/content/cyber-security-career-playbook/_index.en.md
+++ b/content/cyber-security-career-playbook/_index.en.md
@@ -3,7 +3,7 @@ title: "Cyber Security Career Playbooks"
description: "Discover valuable insights, practical tips, and resources to embark on a successful cybersecurity career and make an impact in the ever-changing digital landscape."
tags: ["cybersecurity career", "beginner's guide to cybersecurity", "launching a cybersecurity career", "cybersecurity job prospects", "cybersecurity salary ranges", "cybersecurity training programs", "online cybersecurity courses", "video courses for cybersecurity", "cybersecurity books", "beginners cybersecurity courses", "explain cybersecurity to a 5-year-old", "ELI5 cybersecurity", "top programming languages for cybersecurity", "cybersecurity career path", "cybersecurity expert responsibilities", "soft skills for cybersecurity", "cybersecurity industry", "cybersecurity job market", "cybersecurity certifications", "cybersecurity job demand", "cybersecurity job growth", "cybersecurity skills", "cybersecurity professional", "cybersecurity analyst", "cybersecurity specialist", "cybersecurity consultant", "cybersecurity threats", "cybersecurity best practices", "cybersecurity strategies", "cybersecurity tools", "job opportunities", "cybersecurity internships", "remote cybersecurity jobs", "continuous learning", "emerging threats", "cybersecurity network", "cybersecurity laws", "professional growth", "cybersecurity guidance", "cybersecurity community", "cybersecurity resources", "career advancement", "cybersecurity landscape", "cybersecurity knowledge"]
categories: ["cyber-security-career-playbook"]
-project_url: "https://simeononsecurity.ch/cyber-security-career-playbook-start"
+project_url: "https://simeononsecurity.com/cyber-security-career-playbook-start"
sitemap:
priority : 0.7
---
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md
index c2f9a3e808640..610005ec999c8 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-bootcamps-worth-it/index.en.md
@@ -12,7 +12,7 @@ coverAlt: "A laptop with a graduation hat on the keyboard, surrounded by stacks
coverCaption: ""
---
-With the constantly changing job market and the need for up-to-date skills, many individuals are turning to bootcamps as a way to quickly acquire new knowledge and certifications. However, the question remains: [are bootcamps worth it](https://simeononsecurity.ch/articles/are-bootcamps-worth-it/)? In this article, we will explore the pros and cons of bootcamps and help you determine if they are the right choice for you.
+With the constantly changing job market and the need for up-to-date skills, many individuals are turning to bootcamps as a way to quickly acquire new knowledge and certifications. However, the question remains: [are bootcamps worth it](https://simeononsecurity.com/articles/are-bootcamps-worth-it/)? In this article, we will explore the pros and cons of bootcamps and help you determine if they are the right choice for you.
## [Home](/cyber-security-career-playbook-start/)
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md
index 0b1e094d7b85a..a258bc4c6dbe5 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/are-certifications-needed-for-a-cybersecurity-career/index.en.md
@@ -51,9 +51,9 @@ ______
When pursuing certifications, it is important to consider your career goals, interests, and the specific requirements of your desired job roles. Here are some popular certifications in the cybersecurity field:
-1. [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): A foundational certification covering essential security concepts and best practices.
-2. [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/): A globally recognized certification for experienced cybersecurity professionals.
-3. [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): Focuses on ethical hacking techniques to identify and address vulnerabilities.
+1. [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): A foundational certification covering essential security concepts and best practices.
+2. [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/): A globally recognized certification for experienced cybersecurity professionals.
+3. [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): Focuses on ethical hacking techniques to identify and address vulnerabilities.
4. **Certified Information Security Manager (CISM)**: Designed for individuals managing, designing, and overseeing an enterprise's information security program.
5. **Certified Information Systems Auditor (CISA)**: Focuses on auditing, control, and security of information systems.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md
index 9d5aa6f6fe216..e5dd036f59d6f 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/a-guide-to-earning-the-ISC2-cissp-certification/index.en.md
@@ -55,8 +55,8 @@ There are various study materials available to candidates, such as textbooks, on
- {{< youtube id="_nyZhYnCNLA" >}}
- [PluralSight (Preferred)](https://www.pluralsight.com/)
- [Official Study Guide and Practice Tests](https://amzn.to/3LAu3Ly)
-- [More Learning Resources](https://simeononsecurity.ch/recommendations/learning_resources)
-- [SimeonOnSecurity's CISSP Practice Test](https://simeononsecurity.ch/cissp-practice-test)
+- [More Learning Resources](https://simeononsecurity.com/recommendations/learning_resources)
+- [SimeonOnSecurity's CISSP Practice Test](https://simeononsecurity.com/cissp-practice-test)
### Step 4: Practice with practice exams
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md
index 1cc776117038b..2b7e69d534ceb 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/comptias-security-plus-sy0-601-what-do-you-need-to-know/index.en.md
@@ -184,7 +184,7 @@ In addition to studying the exam objectives and using the recommended materials,
4. **Practice, practice, practice**: Take as many practice exams and performance-based questions as possible. This will help you become familiar with the exam format and identify areas where you need to focus your study efforts.
-- [**SimeonOnSecurity's Security Plus Practice Test**](https://simeononsecurity.ch/security-plus-practice-test)
+- [**SimeonOnSecurity's Security Plus Practice Test**](https://simeononsecurity.com/security-plus-practice-test)
5. **Stay current with industry trends**: Stay up-to-date with current industry trends and news related to information security. This will help you contextualize the exam material and understand how it applies in real-world situations.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md
index 9424bb7f6cd3e..6f23dfde01925 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-a-plus-exams-220-1101-and-220-1102/index.en.md
@@ -96,7 +96,7 @@ One of the best ways to prepare for the CompTIA A+ exams is to take practice exa
There are a variety of online resources available that offer practice exams for the CompTIA A+ exams. Some popular options include:
-- [**SimeonOnSecurity's A Plus Practice Test**](https://simeononsecurity.ch/a-plus-practice-test)
+- [**SimeonOnSecurity's A Plus Practice Test**](https://simeononsecurity.com/a-plus-practice-test)
- [**CertMaster Practice from CompTIA**](https://www.comptia.org/training/certmaster-practice/a): CertMaster Practice offers a range of practice exams and quizzes that are designed to help you prepare for the actual exam.
- [**ExamCompass**](https://www.examcompass.com/): ExamCompass offers a range of free practice exams for the CompTIA A+ exams, as well as other IT certifications.
- [**Udemy**](https://www.udemy.com/): Udemy offers a variety of paid courses and practice exams for the CompTIA A+ exams.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md
index 9a3d8a11e73e2..9edf6895f599d 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/passing-comptias-linux-plus-XK0-005/index.en.md
@@ -11,7 +11,7 @@ coverCaption: ""
---
**Tips and Tricks for Passing CompTIA's Linux+ XK0-005**
-CompTIA Linux+ certification is one of the most sought-after certifications in the field of IT. This certification is designed to validate the skills of IT professionals in working with Linux operating systems. The Linux+ certification exam [XK0-005](https://simeononsecurity.ch/articles/passing-comptias-linux-plus-xk0-005/) is the latest version of this exam and validates the skills and knowledge required to configure, monitor, and troubleshoot Linux systems. Here are some tips and tricks to help you pass the [CompTIA Linux+ XK0-005](https://simeononsecurity.ch/articles/passing-comptias-linux-plus-xk0-005/) exam.
+CompTIA Linux+ certification is one of the most sought-after certifications in the field of IT. This certification is designed to validate the skills of IT professionals in working with Linux operating systems. The Linux+ certification exam [XK0-005](https://simeononsecurity.com/articles/passing-comptias-linux-plus-xk0-005/) is the latest version of this exam and validates the skills and knowledge required to configure, monitor, and troubleshoot Linux systems. Here are some tips and tricks to help you pass the [CompTIA Linux+ XK0-005](https://simeononsecurity.com/articles/passing-comptias-linux-plus-xk0-005/) exam.
## [Home](/cyber-security-career-playbook-start/)
@@ -54,7 +54,7 @@ To gain hands-on experience, you can set up a lab environment where you can prac
- **Cloud Services**: You can also use cloud services such as Amazon Web Services (AWS) or Microsoft Azure to create virtual machines or containers running Linux. This can be a convenient option if you don't have the resources to set up a physical lab environment.
-- [**Home Lab**](https://simeononsecurity.ch/articles/what-is-a-homelab-and-should-you-have-one/): If you have the resources, you can set up a physical lab environment at home. This can include one or more physical servers or workstations running Linux, as well as networking equipment such as switches and routers.
+- [**Home Lab**](https://simeononsecurity.com/articles/what-is-a-homelab-and-should-you-have-one/): If you have the resources, you can set up a physical lab environment at home. This can include one or more physical servers or workstations running Linux, as well as networking equipment such as switches and routers.
By getting hands-on experience with Linux systems, you'll gain practical experience in configuring, monitoring, and troubleshooting Linux systems. This will help you prepare for the CompTIA Linux+ XK0-005 exam and also give you valuable skills that can be used in a professional setting.
@@ -103,7 +103,7 @@ Some examples of online resources for the CompTIA Linux+ XK0-005 exam include:
- [**YouTube Tutorials**](https://www.youtube.com/watch?v=niPWk7tgD2Q&list=PL78ppT-_wOmuwT9idLvuoKOn6UYurFKCp): There are many YouTube channels that provide video tutorials on various Linux-related topics, including some focused specifically on the Linux+ certification. {{< youtube id="YOomKJdLLEo" >}}
-- [**Our Guide on Learning Linux**](https://simeononsecurity.ch/articles/how-do-i-learn-linux/): This guide provides an overview of how to get started with Linux, including tips for learning both Debian and RHEL-based variants of Linux.
+- [**Our Guide on Learning Linux**](https://simeononsecurity.com/articles/how-do-i-learn-linux/): This guide provides an overview of how to get started with Linux, including tips for learning both Debian and RHEL-based variants of Linux.
By using online resources, you can access a wide range of study materials and get a better understanding of the exam objectives and sub-topics. Additionally, many online resources offer interactive elements such as forums or chat rooms where you can ask questions and get help from other Linux professionals.
@@ -113,7 +113,7 @@ Practice exams are a great way to prepare for the CompTIA Linux+ XK0-005 exam. T
Some examples of practice exams for the CompTIA Linux+ XK0-005 exam include:
-- [**SimeonOnSecurity's Linux Plus Practice Test**](https://simeononsecurity.ch/linux-plus-practice-test)
+- [**SimeonOnSecurity's Linux Plus Practice Test**](https://simeononsecurity.com/linux-plus-practice-test)
- [**CompTIA Linux+ Certification Practice Exams**](https://www.comptia.org/training/certmaster-practice/linux): This book includes four complete practice exams that are designed to simulate the format and difficulty of the actual exam.
diff --git a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md
index c29ba8cd529be..4a4fb2011506c 100644
--- a/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md
+++ b/content/cyber-security-career-playbook/cyber-security-certifications-degrees-and-certificates/certifications/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/index.en.md
@@ -11,7 +11,7 @@ coverCaption: ""
---
**Creating a Study Plan for Passing the CEH Certification Exam: Tips and Strategies for Success**
-If you're interested in pursuing a career in cybersecurity, obtaining a certification is a great way to validate your knowledge and expertise. One such certification is the [**Certified Ethical Hacker (CEH)**](https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/) certification, which is designed to test your understanding of various security threats and vulnerabilities. However, passing the [CEH exam](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can be challenging, and it's important to have a well-structured study plan to ensure success. In this article, we'll discuss some tips and strategies for creating an effective study plan to help you pass the [CEH certification exam](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/).
+If you're interested in pursuing a career in cybersecurity, obtaining a certification is a great way to validate your knowledge and expertise. One such certification is the [**Certified Ethical Hacker (CEH)**](https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/) certification, which is designed to test your understanding of various security threats and vulnerabilities. However, passing the [CEH exam](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can be challenging, and it's important to have a well-structured study plan to ensure success. In this article, we'll discuss some tips and strategies for creating an effective study plan to help you pass the [CEH certification exam](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/).
## [Home](/cyber-security-career-playbook-start/)
@@ -45,8 +45,8 @@ Once you've created a study schedule, the next step is to choose the right study
- {{< youtube id="maO8_0cA7W8" >}}
- [PluralSight (Preferred)](https://www.pluralsight.com/)
- [Official Study Guide and Practice Tests](https://amzn.to/42lr6pu)
-- [More Learning Resources](https://simeononsecurity.ch/recommendations/learning_resources)
-- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.ch/ceh-practice-test)
+- [More Learning Resources](https://simeononsecurity.com/recommendations/learning_resources)
+- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.com/ceh-practice-test)
### Focus on Weak Areas
@@ -58,7 +58,7 @@ As you begin studying, focus on your weak areas. This will help you make the mos
Taking practice exams is a great way to prepare for the CEH exam. You can find practice exams on the [**EC-Council's website**](https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/), as well as other online resources. Practice exams will help you identify areas where you need to improve and get you accustomed to the format and style of the exam.
-- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.ch/ceh-practice-test)
+- [**SimeonOnSecurity's CEH Practice Test**](https://simeononsecurity.com/ceh-practice-test)
### Join Study Groups
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md
index f1c70c2165acd..17acbb8c4c738 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.de.md
@@ -63,7 +63,7 @@ ______
Die Cybersicherheit ist ein sich ständig weiterentwickelnder Bereich, und es ist für Fachleute in diesem Bereich von entscheidender Bedeutung, über die neuesten Trends und Bedrohungen auf dem Laufenden zu bleiben. Hier sind einige Möglichkeiten, um informiert zu bleiben:
-- **Blogs und Websites**: Folgen Sie seriösen Cybersicherheitsblogs und -webseiten wie [simeononsecurity.ch](https://www.simeononsecurity.ch/) die aufschlussreiche Artikel und Analysen zu aktuellen Cyber-Bedrohungen und -Trends enthalten.
+- **Blogs und Websites**: Folgen Sie seriösen Cybersicherheitsblogs und -webseiten wie [simeononsecurity.com](https://www.simeononsecurity.com/) die aufschlussreiche Artikel und Analysen zu aktuellen Cyber-Bedrohungen und -Trends enthalten.
- **Branchenkonferenzen und Veranstaltungen**: Besuchen Sie Konferenzen und Veranstaltungen zur Cybersicherheit, um von Branchenexperten zu lernen und sich mit Gleichgesinnten zu vernetzen.
- **Berufsverbände**: Treten Sie Berufsverbänden und -gemeinschaften wie der Information Systems Security Association (ISSA) oder dem International Information System Security Certification Consortium (ISC)² bei, die Ressourcen, Zertifizierungen und Networking-Möglichkeiten bieten.
- **Kontinuierliches Lernen**: Lernen Sie kontinuierlich durch Online-Kurse, Webinare und Zertifizierungsprogramme, um Ihre Kenntnisse und Fähigkeiten zu erweitern.
@@ -109,6 +109,6 @@ ______
## Referenzen:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md
index 806a5b7aeb069..69bdf97268a7b 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.en.md
@@ -67,7 +67,7 @@ ______
Cybersecurity is an ever-evolving field, and staying updated with the latest trends and threats is crucial for professionals in this field. Here are some ways to stay informed:
-- **Blogs and Websites**: Follow reputable cybersecurity blogs and websites such as [simeononsecurity.ch](https://www.simeononsecurity.ch/) that provide insightful articles and analysis of recent cyber threats and trends.
+- **Blogs and Websites**: Follow reputable cybersecurity blogs and websites such as [simeononsecurity.com](https://www.simeononsecurity.com/) that provide insightful articles and analysis of recent cyber threats and trends.
- **Industry Conferences and Events**: Attend cybersecurity conferences and events to learn from industry experts and network with peers.
- **Professional Associations**: Join professional associations and communities such as the Information Systems Security Association (ISSA) or the International Information System Security Certification Consortium (ISC)², which offer resources, certifications, and networking opportunities.
- **Continuous Learning**: Engage in continuous learning through online courses, webinars, and certification programs to enhance your knowledge and skills.
@@ -113,6 +113,6 @@ ______
## References:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md
index 124c9f213ce7d..26939aa35fb42 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.es.md
@@ -63,7 +63,7 @@ ______
La ciberseguridad es un campo en constante evolución, y mantenerse al día de las últimas tendencias y amenazas es crucial para los profesionales de este ámbito. He aquí algunas formas de mantenerse informado:
-- **Blogs y sitios web**: Siga blogs y sitios web de ciberseguridad de confianza como [simeononsecurity.ch](https://www.simeononsecurity.ch/) que ofrecen artículos y análisis perspicaces de las últimas ciberamenazas y tendencias.
+- **Blogs y sitios web**: Siga blogs y sitios web de ciberseguridad de confianza como [simeononsecurity.com](https://www.simeononsecurity.com/) que ofrecen artículos y análisis perspicaces de las últimas ciberamenazas y tendencias.
- Conferencias y eventos del sector**: Asista a conferencias y eventos de ciberseguridad para aprender de expertos de la industria y establecer contactos con colegas.
- Asociaciones profesionales**: Únase a asociaciones y comunidades profesionales como la Information Systems Security Association (ISSA) o el International Information System Security Certification Consortium (ISC)², que ofrecen recursos, certificaciones y oportunidades para establecer contactos.
- Aprendizaje continuo**: Participe en el aprendizaje continuo a través de cursos en línea, seminarios web y programas de certificación para mejorar sus conocimientos y habilidades.
@@ -109,6 +109,6 @@ ______
## Referencias:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md
index 6f20e8bcc83e8..e4802a9543cc1 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.fr.md
@@ -63,7 +63,7 @@ ______
La cybersécurité est un domaine en constante évolution, et il est essentiel pour les professionnels de ce secteur de se tenir au courant des dernières tendances et menaces. Voici quelques moyens de rester informé :
-- **Blogs et sites web** : Suivez des blogs et des sites web réputés sur la cybersécurité, tels que [simeononsecurity.ch](https://www.simeononsecurity.ch/) qui fournissent des articles et des analyses perspicaces sur les menaces et les tendances récentes dans le domaine de la cybernétique.
+- **Blogs et sites web** : Suivez des blogs et des sites web réputés sur la cybersécurité, tels que [simeononsecurity.com](https://www.simeononsecurity.com/) qui fournissent des articles et des analyses perspicaces sur les menaces et les tendances récentes dans le domaine de la cybernétique.
- Conférences et événements du secteur** : Participez à des conférences et à des événements sur la cybersécurité pour vous informer auprès d'experts du secteur et nouer des contacts avec vos pairs.
- Associations professionnelles** : Rejoignez des associations et des communautés professionnelles telles que l'Information Systems Security Association (ISSA) ou l'International Information System Security Certification Consortium (ISC)², qui offrent des ressources, des certifications et des possibilités de mise en réseau.
- Apprentissage continu** : Participez à la formation continue en suivant des cours en ligne, des webinaires et des programmes de certification afin d'améliorer vos connaissances et vos compétences.
@@ -109,6 +109,6 @@ ______
## Références :
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md
index b21ae7ef0358d..ce48002b503eb 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.it.md
@@ -63,7 +63,7 @@ ______
La cybersecurity è un campo in continua evoluzione e rimanere aggiornati sulle ultime tendenze e minacce è fondamentale per i professionisti del settore. Ecco alcuni modi per rimanere informati:
-- **Blog e siti web**: Seguire blog e siti web affidabili sulla sicurezza informatica, come ad esempio [simeononsecurity.ch](https://www.simeononsecurity.ch/) che forniscono articoli e analisi approfondite sulle recenti minacce e tendenze informatiche.
+- **Blog e siti web**: Seguire blog e siti web affidabili sulla sicurezza informatica, come ad esempio [simeononsecurity.com](https://www.simeononsecurity.com/) che forniscono articoli e analisi approfondite sulle recenti minacce e tendenze informatiche.
- Conferenze ed eventi del settore**: Partecipare a conferenze ed eventi sulla sicurezza informatica per imparare dagli esperti del settore e fare rete con i colleghi.
- Associazioni professionali**: Iscriversi ad associazioni e comunità professionali come l'Information Systems Security Association (ISSA) o l'International Information System Security Certification Consortium (ISC)², che offrono risorse, certificazioni e opportunità di networking.
- Apprendimento continuo**: Impegnarsi nell'apprendimento continuo attraverso corsi online, webinar e programmi di certificazione per migliorare le proprie conoscenze e competenze.
@@ -109,6 +109,6 @@ ______
## Riferimenti:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md
index 69401b49c4fb4..3af30e28f8a93 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.ja.md
@@ -63,7 +63,7 @@ ______
サイバーセキュリティは日進月歩の分野であり、この分野の専門家にとって、最新のトレンドや脅威を常に把握することは極めて重要です。ここでは、情報収集を怠らないための方法をいくつかご紹介します:
-- ブログとWebサイト**:ブログやウェブサイト**:以下のような評判の良いサイバーセキュリティ関連のブログやウェブサイトをフォローする。 [simeononsecurity.ch](https://www.simeononsecurity.ch/)サイバー脅威やトレンドに関する洞察に満ちた記事と分析を提供する「Skype」。
+- ブログとWebサイト**:ブログやウェブサイト**:以下のような評判の良いサイバーセキュリティ関連のブログやウェブサイトをフォローする。 [simeononsecurity.com](https://www.simeononsecurity.com/)サイバー脅威やトレンドに関する洞察に満ちた記事と分析を提供する「Skype」。
- **業界のカンファレンスとイベント**:サイバーセキュリティに関するカンファレンスやイベントに参加し、業界の専門家から学び、同業者とのネットワークを構築する。
- 専門家集団**:情報システムセキュリティ協会(ISSA)や国際情報システムセキュリティ認証コンソーシアム(ISC)²など、リソース、認証、ネットワーキングの機会を提供する専門家団体やコミュニティに参加する。
- 継続的な学習**:オンラインコース、ウェビナー、認定プログラムを通じて継続的に学習し、知識とスキルを向上させる。
@@ -109,6 +109,6 @@ ______
## 参考文献
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md
index 1a218cbd9f483..e63027d0ce85b 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.nl.md
@@ -63,7 +63,7 @@ ______
Cyberbeveiliging is een vakgebied dat voortdurend in beweging is, en op de hoogte blijven van de nieuwste trends en bedreigingen is cruciaal voor professionals op dit gebied. Hier zijn enkele manieren om op de hoogte te blijven:
-- **Blogs en websites**: Volg gerenommeerde cyberbeveiligingsblogs en -websites zoals [simeononsecurity.ch](https://www.simeononsecurity.ch/) die inzichtelijke artikelen en analyses bieden over recente cyberbedreigingen en -trends.
+- **Blogs en websites**: Volg gerenommeerde cyberbeveiligingsblogs en -websites zoals [simeononsecurity.com](https://www.simeononsecurity.com/) die inzichtelijke artikelen en analyses bieden over recente cyberbedreigingen en -trends.
- **Industrieconferenties en evenementen**: Woon cyberbeveiligingsconferenties en -evenementen bij om te leren van industrie-experts en te netwerken met collega's.
- Professionele verenigingen**: Sluit u aan bij professionele verenigingen en gemeenschappen zoals de Information Systems Security Association (ISSA) of het International Information System Security Certification Consortium (ISC)², die hulpmiddelen, certificeringen en netwerkmogelijkheden bieden.
- **Doorlopend leren**: Doe aan permanente educatie via online cursussen, webinars en certificeringsprogramma's om uw kennis en vaardigheden te verbeteren.
@@ -109,6 +109,6 @@ ______
## Referenties:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md
index bea917d44178b..7d7b161c32e65 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/cyber-security-interview-questions/index.pl.md
@@ -63,7 +63,7 @@ ______
Cyberbezpieczeństwo to stale rozwijająca się dziedzina, a bycie na bieżąco z najnowszymi trendami i zagrożeniami ma kluczowe znaczenie dla profesjonalistów w tej dziedzinie. Oto kilka sposobów na bycie na bieżąco:
-- **Blogi i strony internetowe**: Śledź renomowane blogi i strony internetowe poświęcone cyberbezpieczeństwu, takie jak [simeononsecurity.ch](https://www.simeononsecurity.ch/) które dostarczają wnikliwych artykułów i analiz najnowszych zagrożeń i trendów cybernetycznych.
+- **Blogi i strony internetowe**: Śledź renomowane blogi i strony internetowe poświęcone cyberbezpieczeństwu, takie jak [simeononsecurity.com](https://www.simeononsecurity.com/) które dostarczają wnikliwych artykułów i analiz najnowszych zagrożeń i trendów cybernetycznych.
- **Konferencje i wydarzenia branżowe**: Bierz udział w konferencjach i wydarzeniach związanych z cyberbezpieczeństwem, aby uczyć się od ekspertów branżowych i nawiązywać kontakty z rówieśnikami.
- **Zrzeszenia zawodowe**: Dołącz do profesjonalnych stowarzyszeń i społeczności, takich jak Information Systems Security Association (ISSA) lub International Information System Security Certification Consortium (ISC)², które oferują zasoby, certyfikaty i możliwości nawiązywania kontaktów.
- **Ciągła nauka**: Zaangażuj się w ciągłe uczenie się poprzez kursy online, webinaria i programy certyfikacyjne, aby poszerzyć swoją wiedzę i umiejętności.
@@ -109,6 +109,6 @@ ______
## Referencje:
-1. [simeononsecurity.ch - Cybersecurity Blog](https://www.simeononsecurity.ch/)
+1. [simeononsecurity.com - Cybersecurity Blog](https://www.simeononsecurity.com/)
2. [Information Systems Security Association (ISSA)](https://www.issa.org/)
3. [International Information System Security Certification Consortium (ISC)²](https://www.isc2.org/)
diff --git a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md
index e6a90fee28f4d..6b4c2be2f3f08 100644
--- a/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md
+++ b/content/cyber-security-career-playbook/getting-a-job-in-cyber-security/resume-writing-tips-for-cybersecurity-professionals/index.en.md
@@ -75,7 +75,7 @@ ______
In conclusion, crafting an effective resume is crucial for cybersecurity, software development, and IT professionals looking to advance their careers. By tailoring your resume to the job description, showcasing your technical skills and achievements, emphasizing cybersecurity and privacy awareness, highlighting problem-solving abilities, maintaining clarity and conciseness, using action verbs and quantifiable results, and staying updated with industry trends, you can create a resume that stands out to potential employers.
-For more general tips on resume writing, you can also refer to [this article](https://simeononsecurity.ch/other/tips-for-writing-a-great-resume/) on simeononsecurity.ch, which provides valuable insights and and additional guidance.
+For more general tips on resume writing, you can also refer to [this article](https://simeononsecurity.com/other/tips-for-writing-a-great-resume/) on simeononsecurity.com, which provides valuable insights and and additional guidance.
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md
index 4b4d382a62fe1..de36b9888d6dd 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-analyst-salaries-entry-level-to-pro/index.en.md
@@ -29,7 +29,7 @@ Experience and expertise are critical determinants of **cybersecurity analyst sa
{{< inarticle-dark >}}
### 2. Education and Certifications
-The level of education and relevant certifications also impact **cybersecurity analyst salaries**. A bachelor's degree in **computer science**, **cybersecurity**, or a related field is often the minimum requirement for entry-level positions. However, earning advanced degrees, such as a master's degree or a Ph.D., can provide a competitive edge and potentially lead to higher-paying positions. Additionally, certifications such as [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/), [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/), or [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can enhance an analyst's marketability and salary potential.
+The level of education and relevant certifications also impact **cybersecurity analyst salaries**. A bachelor's degree in **computer science**, **cybersecurity**, or a related field is often the minimum requirement for entry-level positions. However, earning advanced degrees, such as a master's degree or a Ph.D., can provide a competitive edge and potentially lead to higher-paying positions. Additionally, certifications such as [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/), [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/), or [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) can enhance an analyst's marketability and salary potential.
### 3. Industry and Organization Size
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md
index 2c1c73576a3a0..9fa03338c9cb2 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.de.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) ist ein beliebter Online-Lernmarktplatz, der eine breite Palette von Cybersecurity-Kursen anbietet, die sowohl von Fachleuten aus der Branche als auch von unabhängigen Dozenten erstellt werden. Die große Auswahl an Udemy-Kursen deckt verschiedene Bereiche der Cybersicherheit ab und ermöglicht es den Lernenden, Kurse nach ihren Interessen und Fähigkeiten zu wählen.
-Erfahren Sie mehr über [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Erfahren Sie mehr über [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Empfohlene Bücher für Cybersecurity-Training
@@ -83,7 +83,7 @@ Neben Online-Programmen und Videokursen sind Bücher eine hervorragende Ressourc
Diese Bücher bieten vertieftes Wissen und praktische Einblicke in Themen der Cybersicherheit. Sie können als wertvolle Ressourcen zur Ergänzung von Online-Schulungen dienen und Ihr Verständnis für diesen Bereich erweitern.
-Erfahren Sie mehr über [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Erfahren Sie mehr über [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md
index 133365ef80a1d..be800c28c15e4 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.en.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) is a popular online marketplace for learning, offering a wide range of cybersecurity courses created by both industry professionals and independent instructors. Udemy's vast selection of courses covers various cybersecurity domains, allowing learners to choose courses based on their interests and skill levels.
-Learn about more [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources).
+Learn about more [online training platforms](https://simeononsecurity.com/recommendations/learning_resources).
## Recommended Books for Cybersecurity Training
@@ -83,7 +83,7 @@ In addition to online programs and video courses, books are an excellent resourc
These books offer in-depth knowledge and practical insights into cybersecurity topics. They can serve as valuable resources to complement online training and expand your understanding of the field.
-Learn about more [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books).
+Learn about more [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books).
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md
index 0e0d82b121802..8f720df5e8c8c 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.es.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) es un popular mercado en línea para el aprendizaje, que ofrece una amplia gama de cursos de ciberseguridad creados tanto por profesionales del sector como por instructores independientes. La amplia selección de cursos de Udemy abarca diversos ámbitos de la ciberseguridad, lo que permite a los alumnos elegir los cursos en función de sus intereses y niveles de habilidad.
-Más información [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Más información [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Libros recomendados para la formación en ciberseguridad
@@ -83,7 +83,7 @@ Además de los programas en línea y los cursos en vídeo, los libros son un rec
Estos libros ofrecen conocimientos profundos y perspectivas prácticas sobre temas de ciberseguridad. Pueden servir como valiosos recursos para complementar la formación en línea y ampliar sus conocimientos en este campo.
-Más información [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Más información [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md
index a8dbfc7f57df9..d989958933d02 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.fr.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) Udemy est un marché en ligne populaire pour l'apprentissage, offrant un large éventail de cours de cybersécurité créés par des professionnels de l'industrie et des instructeurs indépendants. La vaste sélection de cours d'Udemy couvre divers domaines de la cybersécurité, ce qui permet aux apprenants de choisir des cours en fonction de leurs intérêts et de leurs niveaux de compétence.
-En savoir plus [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+En savoir plus [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Livres recommandés pour la formation à la cybersécurité
@@ -83,7 +83,7 @@ Outre les programmes en ligne et les cours vidéo, les livres constituent une ex
Ces ouvrages offrent des connaissances approfondies et des aperçus pratiques sur des sujets liés à la cybersécurité. Ils peuvent constituer des ressources précieuses pour compléter la formation en ligne et élargir votre compréhension du domaine.
-En savoir plus [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+En savoir plus [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md
index e70db849ff544..20e74885aca32 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.it.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) è un popolare mercato online per l'apprendimento, che offre un'ampia gamma di corsi di sicurezza informatica creati da professionisti del settore e da istruttori indipendenti. La vasta selezione di corsi di Udemy copre vari settori della sicurezza informatica, consentendo agli studenti di scegliere i corsi in base ai loro interessi e livelli di competenza.
-Per saperne di più [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Per saperne di più [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Libri consigliati per la formazione sulla sicurezza informatica
@@ -83,7 +83,7 @@ Oltre ai programmi online e ai videocorsi, i libri sono una risorsa eccellente p
Questi libri offrono conoscenze approfondite e spunti pratici sugli argomenti di cybersecurity. Possono servire come preziose risorse per integrare la formazione online e ampliare la comprensione del settore.
-Per saperne di più [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Per saperne di più [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md
index 6f3171657e48c..816ea10386585 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.ja.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/)は、業界専門家と独立した講師の両方によって作成された幅広いサイバーセキュリティコースを提供する、人気のあるオンライン学習マーケットプレイスです。Udemyの膨大な数のコースは、様々なサイバーセキュリティ領域をカバーしており、学習者は自分の興味やスキルレベルに応じてコースを選択することができます。
-もっと詳しく知る [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+もっと詳しく知る [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## サイバーセキュリティ研修におすすめの書籍のご紹介です。
@@ -83,7 +83,7 @@ ______
これらの書籍は、サイバーセキュリティに関する深い知識と実践的な洞察力を提供します。オンライントレーニングを補完し、この分野への理解を深めるための貴重な資料となります。
-もっと詳しく知る [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+もっと詳しく知る [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md
index 6119adba8b540..ff7461cff0cad 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.nl.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) is een populaire online marktplaats voor leren en biedt een breed scala aan cursussen op het gebied van cyberbeveiliging, gemaakt door zowel professionals uit de branche als onafhankelijke docenten. De uitgebreide selectie cursussen van Udemy omvat verschillende cyberbeveiligingsdomeinen, zodat leerlingen cursussen kunnen kiezen op basis van hun interesses en vaardigheidsniveaus.
-Meer informatie [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Meer informatie [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Aanbevolen boeken voor cyberbeveiligingstraining
@@ -83,7 +83,7 @@ Naast online programma's en videocursussen zijn boeken een uitstekende bron om u
Deze boeken bieden diepgaande kennis en praktische inzichten in onderwerpen op het gebied van cyberbeveiliging. Ze kunnen dienen als waardevolle bronnen om online training aan te vullen en je inzicht in het vakgebied te vergroten.
-Meer informatie [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Meer informatie [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md
index 605c40618fbc2..78e51992eef6a 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/cybersecurity-training-online-programs-video-courses-and-books/index.pl.md
@@ -63,7 +63,7 @@ ______
[**Udemy**](https://www.udemy.com/) to popularny internetowy rynek edukacyjny, oferujący szeroką gamę kursów z zakresu cyberbezpieczeństwa stworzonych zarówno przez profesjonalistów z branży, jak i niezależnych instruktorów. Szeroki wybór kursów Udemy obejmuje różne dziedziny cyberbezpieczeństwa, umożliwiając uczestnikom wybór kursów w oparciu o ich zainteresowania i poziom umiejętności.
-Dowiedz się więcej [online training platforms](https://simeononsecurity.ch/recommendations/learning_resources)
+Dowiedz się więcej [online training platforms](https://simeononsecurity.com/recommendations/learning_resources)
## Zalecane książki do szkolenia w zakresie cyberbezpieczeństwa
@@ -83,7 +83,7 @@ Oprócz programów online i kursów wideo, książki są doskonałym źródłem
Książki te oferują dogłębną wiedzę i praktyczne spojrzenie na tematy związane z cyberbezpieczeństwem. Mogą one służyć jako cenne zasoby uzupełniające szkolenia online i poszerzające wiedzę w tej dziedzinie.
-Dowiedz się więcej [SimeonOnSecurity's Recommended Books](https://simeononsecurity.ch/recommendations/books)
+Dowiedz się więcej [SimeonOnSecurity's Recommended Books](https://simeononsecurity.com/recommendations/books)
______
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md
index 3fc953fe98824..63b0e74afb07c 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.de.md
@@ -24,23 +24,23 @@ Stellen Sie sich vor, Sie wachen eines Tages auf und stellen fest, dass alle Ihr
Cybersicherheitsexperten sind so etwas wie die Superhelden der digitalen Welt. Sie haben besondere Fähigkeiten, um unsere digitalen Informationen vor den Bösewichten zu schützen. Aber nicht alle Cybersicherheitsexperten machen das Gleiche. Es ist wie bei Ärzten: Sie haben alle eine gemeinsame Ausbildung, spezialisieren sich dann aber auf verschiedene Bereiche. Einige Fachleute für Cybersicherheit werden zu Experten für das Auffinden und Beheben von Schwachstellen in Computersystemen, während andere sich auf die Entwicklung starker Verteidigungsmaßnahmen konzentrieren, um die Bösewichte fernzuhalten. Sie arbeiten in Teams und lernen und verbessern ständig ihre Fähigkeiten, um den Bösewichten einen Schritt voraus zu sein.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Auch wenn Sie kein Cybersecurity-Profi werden, können Sie dennoch einiges tun, um sich und Ihre Familie vor den bösen Jungs im Internet zu schützen. Lernen Sie einige grundlegende persönliche Sicherheitspraktiken kennen, die Ihnen helfen können, sich zu schützen:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Beim Phishing versuchen die Bösewichte, Sie mit einem Trick dazu zu bringen, ihnen Ihre persönlichen Daten wie Passwörter oder Kreditkartennummern zu geben. Sie schicken Ihnen möglicherweise E-Mails oder Nachrichten, die echt aussehen, aber in Wirklichkeit gefälscht sind. Sie wollen, dass Sie auf Links klicken, die Sie zu gefälschten Websites führen, wo sie Ihre Daten stehlen können. Seien Sie also vorsichtig und klicken Sie nicht auf verdächtige Links. Wenn etwas seltsam aussieht oder zu gut ist, um wahr zu sein, handelt es sich wahrscheinlich um einen Betrüger, der versucht, Sie auszutricksen.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
So wie Sie neue Spielzeuge oder Kleidung bekommen, brauchen auch Ihre Geräte, wie Ihr Telefon oder Ihr Computer, Updates. Mit diesen Updates werden Probleme oder Sicherheitslücken behoben, die Bösewichte nutzen könnten, um in Ihre Geräte einzudringen. Installieren Sie also unbedingt die Updates, wenn Sie dazu aufgefordert werden. Das ist so, als würden Sie ein Schloss an Ihre Schlafzimmertür machen, um die bösen Jungs draußen zu halten.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Ein sicheres Passwort ist wie ein Geheimcode, den nur Sie kennen. Es sollte lang und komplex sein, mit einer Mischung aus Buchstaben, Zahlen und Sonderzeichen. Vermeiden Sie gebräuchliche Wörter oder persönliche Informationen, die jemand leicht erraten könnte. Es ist außerdem wichtig, für verschiedene Websites oder Konten unterschiedliche Passwörter zu verwenden. Wenn ein Kennwort gehackt wird, können die Bösewichte nicht auf alle anderen Konten zugreifen. Wenn es schwierig ist, sich all diese Passwörter zu merken, können Sie einen Passwortmanager verwenden, um Ihre Passwörter sicher zu speichern und zu verwalten.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Die Multi-Faktor-Authentifizierung (MFA) bietet eine zusätzliche Sicherheitsebene für Ihre Online-Konten. Das ist so, als hätten Sie zwei Schlösser an Ihrer Tür. Mit MFA müssen Sie neben Ihrem Passwort zusätzliche Informationen angeben, z. B. einen speziellen Code, der an Ihr Telefon gesendet wird, um auf Ihr Konto zuzugreifen. Das macht es für die Bösewichte viel schwieriger, sich Zugang zu verschaffen, selbst wenn sie Ihr Passwort kennen. Wann immer eine Website oder App MFA anbietet, sollten Sie diese Funktion aktivieren, um zusätzlichen Schutz zu erhalten.
@@ -52,8 +52,8 @@ Cybersicherheit ist wie ein Superheld, der unsere digitale Welt vor den Bösewic
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md
index 5135a46788691..e235ebea52772 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.en.md
@@ -25,23 +25,23 @@ Imagine waking up one day and finding out that all your messages, photos, and fi
Cybersecurity professionals are like the superheroes of the digital world. They have special skills to protect our digital information from the bad guys. But not all cybersecurity professionals do the same thing. It's like doctors: they all have a common education but then specialize in different areas. Some cybersecurity professionals become experts in finding and fixing vulnerabilities in computer systems, while others focus on creating strong defenses to keep the bad guys out. They work in teams and constantly learn and improve their skills to stay ahead of the bad guys.
{{< inarticle-dark >}}
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Even if you don't become a cybersecurity professional, you can still do some things to protect yourself and your family from the bad guys on the internet. Let's learn some basic personal security hygiene practices that can help keep you safe:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing is when the bad guys try to trick you into giving them your personal information, like passwords or credit card numbers. They may send you emails or messages that look real but are actually fake. They want you to click on links that take you to fake websites where they can steal your information. So, be careful and don't click on any suspicious links. If something looks strange or too good to be true, it's probably a bad guy trying to trick you.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Just like you get new toys or clothes, your devices, like your phone or computer, also need updates. These updates help fix any problems or security flaws that the bad guys might use to break into your devices. So, make sure to install the updates when you're prompted to do so. It's like putting a lock on your bedroom door to keep the bad guys out.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
A strong password is like a secret code that only you know. It should be long and complex, with a mix of letters, numbers, and special characters. Avoid using common words or personal information that someone could easily guess. It's also important to use different passwords for different websites or accounts. This way, if one password gets hacked, the bad guys won't be able to access all your other accounts. If remembering all those passwords sounds difficult, you can use a password manager to securely store and manage your passwords.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Multi-Factor Authentication (MFA) adds an extra layer of security to your online accounts. It's like having double locks on your door. With MFA, you need to provide additional information, like a special code sent to your phone, along with your password to access your account. This makes it much harder for the bad guys to get in, even if they know your password. So, whenever a website or app offers MFA, make sure to turn it on for added protection.
@@ -54,8 +54,8 @@ Cybersecurity is like a superhero that protects our digital world from the bad g
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md
index a1e138e608e84..1f3beac2e0e2d 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.es.md
@@ -24,23 +24,23 @@ Imagine despertarse un día y descubrir que todos sus mensajes, fotos y archivos
Los profesionales de la ciberseguridad son como los superhéroes del mundo digital. Tienen habilidades especiales para proteger nuestra información digital de los malos. Pero no todos los profesionales de la ciberseguridad hacen lo mismo. Es como los médicos: todos tienen una formación común, pero luego se especializan en distintas áreas. Algunos profesionales de la ciberseguridad se convierten en expertos en encontrar y corregir vulnerabilidades en los sistemas informáticos, mientras que otros se centran en crear defensas sólidas para mantener alejados a los malos. Trabajan en equipo y aprenden y mejoran constantemente sus habilidades para ir por delante de los malos.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Aunque no te conviertas en un profesional de la ciberseguridad, puedes hacer algunas cosas para protegerte a ti y a tu familia de los malos de Internet. Conozcamos algunas prácticas básicas de higiene de seguridad personal que pueden ayudarle a mantenerse a salvo:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing es cuando los malos intentan engañarte para que les des tu información personal, como contraseñas o números de tarjetas de crédito. Pueden enviarle correos electrónicos o mensajes que parecen reales, pero que en realidad son falsos. Quieren que hagas clic en enlaces que te llevan a sitios web falsos donde pueden robar tu información. Así que tenga cuidado y no haga clic en ningún enlace sospechoso. Si algo parece extraño o demasiado bueno para ser verdad, probablemente sea un malhechor intentando engañarte.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Al igual que los juguetes o la ropa, los dispositivos, como el teléfono o el ordenador, también necesitan actualizaciones. Estas actualizaciones ayudan a solucionar cualquier problema o fallo de seguridad que los malos puedan utilizar para entrar en tus dispositivos. Así que asegúrate de instalar las actualizaciones cuando te lo pidan. Es como poner una cerradura en la puerta de tu habitación para evitar que entren los malos.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Una contraseña segura es como un código secreto que sólo tú conoces. Debe ser larga y compleja, con una mezcla de letras, números y caracteres especiales. Evite utilizar palabras comunes o información personal que alguien pueda adivinar fácilmente. También es importante utilizar contraseñas distintas para sitios web o cuentas diferentes. De este modo, si piratean una contraseña, los delincuentes no podrán acceder al resto de tus cuentas. Si recordar todas esas contraseñas te resulta difícil, puedes utilizar un gestor de contraseñas para almacenarlas y gestionarlas de forma segura.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
La autenticación multifactor (AMF) añade una capa adicional de seguridad a sus cuentas en línea. Es como tener doble cerradura en la puerta. Con la AMF, para acceder a tu cuenta tienes que proporcionar información adicional, como un código especial enviado a tu teléfono, junto con tu contraseña. Esto hace que sea mucho más difícil para los malos entrar, incluso si conocen tu contraseña. Así que, siempre que un sitio web o una aplicación ofrezca MFA, asegúrate de activarlo para una mayor protección.
@@ -52,8 +52,8 @@ La ciberseguridad es como un superhéroe que protege nuestro mundo digital de lo
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md
index 65d0be28985b1..4749e9b1e6632 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.fr.md
@@ -24,23 +24,23 @@ Imaginez que vous vous réveillez un jour et que vous découvrez que tous vos me
Les professionnels de la cybersécurité sont en quelque sorte les super-héros du monde numérique. Ils possèdent des compétences particulières pour protéger nos informations numériques contre les malfaiteurs. Mais tous les professionnels de la cybersécurité ne font pas la même chose. C'est comme les médecins : ils ont tous une formation commune, mais se spécialisent ensuite dans des domaines différents. Certains professionnels de la cybersécurité deviennent experts dans la recherche et la correction des failles des systèmes informatiques, tandis que d'autres se concentrent sur la création de défenses solides pour empêcher les malfaiteurs d'entrer. Ils travaillent en équipe et ne cessent d'apprendre et d'améliorer leurs compétences pour garder une longueur d'avance sur les malfaiteurs.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Même si vous ne devenez pas un professionnel de la cybersécurité, vous pouvez prendre certaines mesures pour vous protéger, vous et votre famille, des méchants sur Internet. Voici quelques règles d'hygiène de base en matière de sécurité personnelle qui peuvent vous aider à rester en sécurité :
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
On parle de phishing lorsque des personnes mal intentionnées tentent de vous inciter à leur fournir des informations personnelles, comme des mots de passe ou des numéros de carte de crédit. Ils peuvent vous envoyer des courriels ou des messages qui semblent réels mais qui sont en fait faux. Ils veulent que vous cliquiez sur des liens qui vous conduisent à de faux sites web où ils peuvent voler vos informations. Soyez donc prudent et ne cliquez sur aucun lien suspect. Si quelque chose vous semble étrange ou trop beau pour être vrai, il s'agit probablement d'une personne malveillante qui essaie de vous piéger.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Tout comme vous recevez de nouveaux jouets ou vêtements, vos appareils, comme votre téléphone ou votre ordinateur, ont également besoin de mises à jour. Ces mises à jour permettent de résoudre les problèmes ou les failles de sécurité que les malfaiteurs pourraient utiliser pour s'introduire dans vos appareils. Veillez donc à installer les mises à jour lorsque vous y êtes invité. C'est comme si vous mettiez un verrou sur la porte de votre chambre pour empêcher les malfaiteurs d'entrer.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Un mot de passe fort est comme un code secret que vous êtes le seul à connaître. Il doit être long et complexe, avec un mélange de lettres, de chiffres et de caractères spéciaux. Évitez d'utiliser des mots courants ou des informations personnelles que quelqu'un pourrait facilement deviner. Il est également important d'utiliser des mots de passe différents pour des sites web ou des comptes différents. Ainsi, si un mot de passe est piraté, les malfaiteurs ne pourront pas accéder à tous vos autres comptes. S'il vous semble difficile de vous souvenir de tous ces mots de passe, vous pouvez utiliser un gestionnaire de mots de passe pour stocker et gérer vos mots de passe en toute sécurité.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
L'authentification multifactorielle (AMF) ajoute une couche de sécurité supplémentaire à vos comptes en ligne. C'est comme avoir une double serrure sur votre porte. Avec l'AFM, vous devez fournir des informations supplémentaires, comme un code spécial envoyé sur votre téléphone, en plus de votre mot de passe pour accéder à votre compte. Il est donc beaucoup plus difficile pour les malfaiteurs d'accéder à votre compte, même s'ils connaissent votre mot de passe. Par conséquent, chaque fois qu'un site web ou une application propose l'option MFA, veillez à l'activer pour une protection accrue.
@@ -52,8 +52,8 @@ La cybersécurité est comme un super-héros qui protège notre monde numérique
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md
index 3770a056f512c..7833b590af3d8 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.it.md
@@ -24,23 +24,23 @@ Immaginate di svegliarvi un giorno e di scoprire che tutti i vostri messaggi, fo
I professionisti della sicurezza informatica sono come i supereroi del mondo digitale. Hanno competenze speciali per proteggere le nostre informazioni digitali dai malintenzionati. Ma non tutti i professionisti della sicurezza informatica fanno la stessa cosa. È come per i medici: hanno tutti una formazione comune, ma poi si specializzano in aree diverse. Alcuni professionisti della sicurezza informatica diventano esperti nel trovare e risolvere le vulnerabilità dei sistemi informatici, mentre altri si concentrano sulla creazione di difese forti per tenere lontani i malintenzionati. Lavorano in team e imparano e migliorano costantemente le loro competenze per stare davanti ai malintenzionati.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Anche se non diventate professionisti della sicurezza informatica, potete comunque fare qualcosa per proteggere voi stessi e la vostra famiglia dai malintenzionati di Internet. Scopriamo alcune pratiche di base per l'igiene della sicurezza personale che possono aiutarvi a stare al sicuro:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Il phishing è quando i malintenzionati cercano di indurvi a fornire loro le vostre informazioni personali, come password o numeri di carta di credito. Possono inviarvi e-mail o messaggi che sembrano reali ma in realtà sono falsi. Vogliono che clicchiate su link che vi portano a siti web falsi dove possono rubare le vostre informazioni. Quindi, fate attenzione e non cliccate su nessun link sospetto. Se qualcosa sembra strano o troppo bello per essere vero, probabilmente si tratta di un malintenzionato che sta cercando di ingannarvi.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Proprio come i giocattoli o i vestiti nuovi, anche i dispositivi, come il telefono o il computer, hanno bisogno di aggiornamenti. Questi aggiornamenti aiutano a risolvere eventuali problemi o falle di sicurezza che i malintenzionati potrebbero utilizzare per introdursi nei vostri dispositivi. Assicuratevi quindi di installare gli aggiornamenti quando vi viene richiesto. È come mettere un lucchetto alla porta della camera da letto per tenere lontani i malintenzionati.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Una password forte è come un codice segreto che solo voi conoscete. Deve essere lunga e complessa, con un mix di lettere, numeri e caratteri speciali. Evitate di usare parole comuni o informazioni personali che qualcuno potrebbe facilmente indovinare. È anche importante utilizzare password diverse per siti web o account diversi. In questo modo, se una password viene violata, i malintenzionati non potranno accedere a tutti gli altri account. Se ricordare tutte le password sembra difficile, potete utilizzare un gestore di password per memorizzare e gestire in modo sicuro le vostre password.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
L'autenticazione a più fattori (MFA) aggiunge un ulteriore livello di sicurezza ai vostri account online. È come avere una doppia serratura alla porta. Con l'MFA, per accedere al vostro account dovete fornire informazioni aggiuntive, come un codice speciale inviato al vostro telefono, insieme alla password. In questo modo è molto più difficile per i malintenzionati entrare, anche se conoscono la password. Quindi, ogni volta che un sito web o un'app offrono l'MFA, assicuratevi di attivarlo per una maggiore protezione.
@@ -52,8 +52,8 @@ La sicurezza informatica è come un supereroe che protegge il nostro mondo digit
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md
index 774d94e7fef21..0dc5ce3c2f428 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.ja.md
@@ -24,23 +24,23 @@ coverCaption: ""
サイバーセキュリティの専門家は、デジタル世界のスーパーヒーローのような存在です。彼らは、私たちのデジタル情報を悪者から守る特別なスキルを持っています。しかし、すべてのサイバーセキュリティの専門家が同じことをするわけではありません。医者と同じで、共通の教育を受けた後、異なる分野に特化するのです。あるサイバーセキュリティの専門家は、コンピュータシステムの脆弱性を見つけて修正する専門家になり、またある専門家は、悪者を排除するための強力な防御を作ることに専念する。彼らはチームで仕事をし、常に学び、スキルを向上させ、悪者の前に立ちはだかるのです。
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
サイバーセキュリティの専門家にならなくても、インターネット上の悪者から自分と家族を守るためにできることがあります。あなたの安全を守るために役立つ、基本的な個人のセキュリティ衛生習慣を学びましょう:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
フィッシングとは、悪者があなたを騙して、パスワードやクレジットカード番号などの個人情報を与えようとすることです。フィッシングは、本物に見えるが実は偽物であるメールやメッセージを送ってくることがあります。フィッシング業者は、あなたの情報を盗むために、偽のウェブサイトへ誘導するリンクをクリックさせようとします。だから、気をつけて、怪しいリンクはクリックしないようにしましょう。もし、何かが奇妙に見えたり、あまりにも真実味がない場合は、おそらくあなたを騙そうとしている悪者でしょう。
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
おもちゃや洋服が新しくなるように、携帯電話やパソコンなどのデバイスもアップデートが必要です。これらのアップデートは、悪者があなたのデバイスに侵入するために使用するかもしれない問題やセキュリティ上の欠陥を修正するのに役立ちます。だから、アップデートをインストールするように指示されたら、必ずインストールしてください。これは、寝室のドアに鍵をかけて悪者を排除するようなものです。
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
強力なパスワードは、あなただけが知っている秘密の暗号のようなものです。文字、数字、特殊文字を組み合わせて、長く複雑なものにする必要があります。誰かが簡単に推測できるような一般的な言葉や個人情報を使うのは避けましょう。また、ウェブサイトやアカウントごとに異なるパスワードを使用することも重要です。そうすれば、1つのパスワードがハッキングされても、悪者はあなたの他のすべてのアカウントにアクセスすることができません。パスワードを覚えるのが大変そうなら、パスワードマネージャーを使って、パスワードを安全に保存・管理することもできます。
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
多要素認証(MFA)は、あなたのオンラインアカウントにさらなるセキュリティ層を追加します。これは、ドアに二重ロックをかけるようなものです。MFAでは、アカウントにアクセスするために、パスワードと一緒に、携帯電話に送信される特別なコードのような追加情報を提供する必要があります。これによって、たとえパスワードを知っていたとしても、悪者が侵入するのはずっと難しくなります。ですから、ウェブサイトやアプリがMFAを提供している場合は、必ずMFAをオンにして、保護を強化するようにしましょう。
@@ -52,8 +52,8 @@ coverCaption: ""
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md
index 3994a13a56d1f..d84e46e013faa 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.nl.md
@@ -24,23 +24,23 @@ Stel je voor dat je op een dag wakker wordt en ontdekt dat al je berichten, foto
Cyberbeveiligingsprofessionals zijn als de superhelden van de digitale wereld. Ze hebben speciale vaardigheden om onze digitale informatie te beschermen tegen de slechteriken. Maar niet alle cyberbeveiligingsprofessionals doen hetzelfde. Het is net als bij artsen: ze hebben allemaal een gemeenschappelijke opleiding, maar specialiseren zich vervolgens in verschillende gebieden. Sommige cyberbeveiligingsprofessionals worden experts in het vinden en repareren van zwakke plekken in computersystemen, terwijl anderen zich richten op het creëren van een sterke verdediging om de slechteriken buiten te houden. Ze werken in teams en leren en verbeteren hun vaardigheden voortdurend om de slechteriken voor te blijven.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Zelfs als je geen cyberbeveiligingsprofessional wordt, kun je nog steeds een aantal dingen doen om jezelf en je familie te beschermen tegen de slechteriken op internet. Laten we eens kijken naar een aantal basispraktijken voor persoonlijke veiligheidshygiëne die kunnen helpen om je veilig te houden:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing is wanneer de slechteriken je proberen te verleiden tot het geven van persoonlijke informatie, zoals wachtwoorden of creditcardnummers. Ze kunnen je e-mails of berichten sturen die er echt uitzien, maar eigenlijk nep zijn. Ze willen dat je op links klikt die je naar valse websites brengen waar ze je gegevens kunnen stelen. Wees dus voorzichtig en klik niet op verdachte links. Als iets er vreemd uitziet of te mooi is om waar te zijn, is het waarschijnlijk een slechterik die je probeert te misleiden.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Net zoals je nieuw speelgoed of nieuwe kleren krijgt, hebben je apparaten, zoals je telefoon of computer, ook updates nodig. Deze updates helpen bij het oplossen van problemen of beveiligingslekken die de slechteriken kunnen gebruiken om in te breken op je apparaten. Zorg er dus voor dat je de updates installeert wanneer daarom wordt gevraagd. Het is alsof je een slot op je slaapkamerdeur doet om de slechteriken buiten te houden.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Een sterk wachtwoord is als een geheime code die alleen jij kent. Het moet lang en complex zijn, met een mix van letters, cijfers en speciale tekens. Vermijd het gebruik van gewone woorden of persoonlijke informatie die iemand makkelijk kan raden. Het is ook belangrijk om verschillende wachtwoorden te gebruiken voor verschillende websites of accounts. Op deze manier, als één wachtwoord wordt gekraakt, hebben de slechteriken geen toegang tot al je andere accounts. Als het onthouden van al die wachtwoorden moeilijk klinkt, kun je een wachtwoordmanager gebruiken om je wachtwoorden veilig op te slaan en te beheren.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Multi-Factor Authenticatie (MFA) voegt een extra beveiligingslaag toe aan je online accounts. Het is alsof je dubbele sloten op je deur hebt. Met MFA moet je extra informatie opgeven, zoals een speciale code die naar je telefoon wordt gestuurd, samen met je wachtwoord om toegang te krijgen tot je account. Dit maakt het veel moeilijker voor de slechteriken om binnen te komen, zelfs als ze je wachtwoord weten. Dus als een website of app MFA aanbiedt, zorg er dan voor dat je het inschakelt voor extra bescherming.
@@ -52,8 +52,8 @@ Cyberbeveiliging is als een superheld die onze digitale wereld beschermt tegen d
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md
index 452ee427e0d86..3e889a3cd5b23 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/explain-cybersecurity-like-i-am-5-eli5/index.pl.md
@@ -24,23 +24,23 @@ Wyobraź sobie, że pewnego dnia budzisz się i odkrywasz, że wszystkie twoje w
Specjaliści ds. cyberbezpieczeństwa są jak superbohaterowie cyfrowego świata. Posiadają specjalne umiejętności, aby chronić nasze cyfrowe informacje przed złymi ludźmi. Ale nie wszyscy specjaliści ds. cyberbezpieczeństwa robią to samo. To jak lekarze: wszyscy mają wspólne wykształcenie, ale specjalizują się w różnych dziedzinach. Niektórzy specjaliści ds. cyberbezpieczeństwa stają się ekspertami w znajdowaniu i naprawianiu luk w systemach komputerowych, podczas gdy inni koncentrują się na tworzeniu silnej obrony, aby powstrzymać złoczyńców. Pracują w zespołach i stale uczą się i doskonalą swoje umiejętności, aby wyprzedzić złoczyńców.
-## [Personal Security Hygiene](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
+## [Personal Security Hygiene](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
Nawet jeśli nie zostaniesz specjalistą ds. cyberbezpieczeństwa, nadal możesz zrobić kilka rzeczy, aby chronić siebie i swoją rodzinę przed złymi ludźmi w Internecie. Zapoznajmy się z kilkoma podstawowymi praktykami higieny osobistej, które mogą pomóc w zapewnieniu bezpieczeństwa:
-### [Phishing: Don't Get Hooked](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+### [Phishing: Don't Get Hooked](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
Phishing ma miejsce wtedy, gdy przestępcy próbują nakłonić użytkownika do podania danych osobowych, takich jak hasła lub numery kart kredytowych. Mogą wysyłać e-maile lub wiadomości, które wyglądają na prawdziwe, ale w rzeczywistości są fałszywe. Chcą, abyś kliknął na linki, które prowadzą do fałszywych stron internetowych, gdzie mogą ukraść twoje informacje. Bądź więc ostrożny i nie klikaj żadnych podejrzanych linków. Jeśli coś wygląda dziwnie lub zbyt dobrze, by mogło być prawdziwe, prawdopodobnie jest to oszustwo.
-### [Software Updates: Stay Updated and Protected](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+### [Software Updates: Stay Updated and Protected](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
Podobnie jak nowe zabawki czy ubrania, urządzenia takie jak telefon czy komputer również wymagają aktualizacji. Aktualizacje te pomagają naprawić wszelkie problemy lub luki w zabezpieczeniach, które złoczyńcy mogą wykorzystać do włamania się do urządzeń. Upewnij się więc, że instalujesz aktualizacje, gdy zostaniesz o to poproszony. To jak założenie zamka na drzwiach sypialni, aby uniemożliwić złoczyńcom dostęp.
-### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
+### [Strong Passwords: Secret Codes for Safety](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
Silne hasło jest jak tajny kod, który znasz tylko Ty. Powinno być długie i złożone, z kombinacją liter, cyfr i znaków specjalnych. Unikaj używania popularnych słów lub danych osobowych, które ktoś mógłby łatwo odgadnąć. Ważne jest również, aby używać różnych haseł do różnych witryn lub kont. W ten sposób, jeśli jedno hasło zostanie zhakowane, złoczyńcy nie będą mogli uzyskać dostępu do wszystkich innych kont. Jeśli zapamiętanie wszystkich tych haseł wydaje się trudne, możesz użyć menedżera haseł, aby bezpiecznie przechowywać hasła i zarządzać nimi.
-### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+### [Multi-Factor Authentication: Double Locks for Extra Security](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
Uwierzytelnianie wieloskładnikowe (MFA) dodaje dodatkową warstwę zabezpieczeń do kont online. To jak podwójne zamki w drzwiach. Dzięki MFA musisz podać dodatkowe informacje, takie jak specjalny kod wysłany na Twój telefon, wraz z hasłem, aby uzyskać dostęp do konta. To znacznie utrudnia złoczyńcom dostęp do konta, nawet jeśli znają oni hasło. Tak więc, za każdym razem, gdy witryna lub aplikacja oferuje MFA, pamiętaj, aby ją włączyć w celu dodatkowej ochrony.
@@ -52,8 +52,8 @@ Cyberbezpieczeństwo jest jak superbohater, który chroni nasz cyfrowy świat pr
1. [Stay Safe Online: Software Updates](https://www.staysafeonline.org/stay-safe-online/keep-a-clean-machine/software-updates/)
2. [Creating a Strong Password](https://www.us-cert.gov/ncas/tips/ST04-002)
-3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
-4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
-5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/)
-6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.ch/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
-7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.ch/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
+3. [A Guide to Multi-Factor Authentication: Types and Best Practices](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/)
+4. [Streamline Windows Package Management with Chocolatey: Simplify Updates and Enhance Security](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/)
+5. [Creating Strong Passwords: A Guide to Security and Password Management](https://simeononsecurity.com/articles/how-to-create-strong-passwords/)
+6. [Recognizing Phishing Attempts: Common Indicators and Safety Tips](https://simeononsecurity.com/articles/what-is-a-common-indicator-of-a-phishing-attempt/)
+7. [Assume Every Device Is Already Compromised: Strengthening Digital Security in an Interconnected World](https://simeononsecurity.com/articles/why-you-should-assume-every-device-you-touch-is-compromised/)
\ No newline at end of file
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md
index 3931e4d676500..a5806134b12fb 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.de.md
@@ -24,15 +24,15 @@ In den letzten Jahren ist die Cybersicherheit zu einem wichtigen Aspekt unseres
Bevor Sie in die Welt der Cybersicherheit eintauchen, ist es wichtig, ein solides Fundament an Wissen zu schaffen. Hier sind einige wichtige Bereiche, auf die Sie sich konzentrieren sollten:
-1. **Netzwerke**: Das Verstehen der Grundlagen der Netzwerktechnik ist für die Cybersicherheit von entscheidender Bedeutung. Machen Sie sich mit Netzwerkprotokollen, IP-Adressierung, Routing und [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Ziehen Sie in Erwägung, eine Zertifizierung wie CompTIA Network+ zu erwerben, um Ihre Netzwerkkenntnisse zu bestätigen.
+1. **Netzwerke**: Das Verstehen der Grundlagen der Netzwerktechnik ist für die Cybersicherheit von entscheidender Bedeutung. Machen Sie sich mit Netzwerkprotokollen, IP-Adressierung, Routing und [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Ziehen Sie in Erwägung, eine Zertifizierung wie CompTIA Network+ zu erwerben, um Ihre Netzwerkkenntnisse zu bestätigen.
2. **Betriebssysteme**: Erwerben Sie Kenntnisse in den Betriebssystemen Linux und Windows. Lernen Sie, wie man in der Befehlszeile navigiert, Systemeinstellungen konfiguriert und Benutzerkonten verwaltet. Die Zertifizierungen CompTIA A+ und Linux+ sind ausgezeichnete Ausgangspunkte, um Ihr Verständnis von Betriebssystemen zu verbessern.
3. **Grundlegende Konzepte der Informatik**: Erwerben Sie ein grundlegendes Verständnis für die Prinzipien der Informatik, einschließlich Algorithmen, Datenstrukturen und Programmiersprachen. Dieses Wissen wird Ihnen helfen, Schwachstellen zu analysieren und sichere Softwareanwendungen zu entwickeln.
-4. **Kodierfähigkeiten**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) kann bei der Automatisierung von Sicherheitsaufgaben von Vorteil sein.
+4. **Kodierfähigkeiten**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) kann bei der Automatisierung von Sicherheitsaufgaben von Vorteil sein.
-5. **Unternehmenssystemverwaltung**: Wenn Sie Erfahrungen in der Verwaltung von Unternehmenssystemen gesammelt haben, erhalten Sie Einblicke in die Verwaltung komplexer IT-Infrastrukturen. Machen Sie sich vertraut mit Active Directory, Gruppenrichtlinien und [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Unternehmenssystemverwaltung**: Wenn Sie Erfahrungen in der Verwaltung von Unternehmenssystemen gesammelt haben, erhalten Sie Einblicke in die Verwaltung komplexer IT-Infrastrukturen. Machen Sie sich vertraut mit Active Directory, Gruppenrichtlinien und [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Cybersecurity-Domänen erforschen
@@ -40,7 +40,7 @@ Die Cybersicherheit umfasst verschiedene Bereiche, die jeweils ihren eigenen Sch
1. **Blaues Team**: Fachleute des Blue Teams konzentrieren sich auf die Verteidigung von Systemen und Netzwerken gegen Cyber-Bedrohungen. Sie entwerfen und implementieren Sicherheitsmaßnahmen, überwachen den Netzwerkverkehr und reagieren auf Vorfälle. Sie erwerben Kenntnisse über Sicherheitstools, Technologien und bewährte Verfahren für eine wirksame Verteidigung.
-2. **Red Team**: Red Team-Profis, die auch als ethische Hacker bezeichnet werden, sind auf die Bewertung von Systemschwachstellen durch simulierte Angriffe spezialisiert. Sie ermitteln Schwachstellen in Sicherheitssystemen, führen Penetrationstests durch und helfen Unternehmen bei der Stärkung ihrer Verteidigungsmaßnahmen. Entwickeln Sie praktische Fertigkeiten in ethischen Hacking-Techniken und machen Sie sich mit Tools wie [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: Red Team-Profis, die auch als ethische Hacker bezeichnet werden, sind auf die Bewertung von Systemschwachstellen durch simulierte Angriffe spezialisiert. Sie ermitteln Schwachstellen in Sicherheitssystemen, führen Penetrationstests durch und helfen Unternehmen bei der Stärkung ihrer Verteidigungsmaßnahmen. Entwickeln Sie praktische Fertigkeiten in ethischen Hacking-Techniken und machen Sie sich mit Tools wie [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Lila Team**: Das violette Team kombiniert Elemente des blauen und des roten Teams. Sie arbeiten zusammen, um die allgemeine Sicherheitslage zu verbessern, indem sie realistische Angriffsszenarien simulieren, Verteidigungsmaßnahmen bewerten und Erkenntnisse austauschen. Diese Rolle erfordert die Beherrschung sowohl defensiver als auch offensiver Techniken.
@@ -48,9 +48,9 @@ Die Cybersicherheit umfasst verschiedene Bereiche, die jeweils ihren eigenen Sch
Zertifizierungen sind zwar nicht obligatorisch, können aber Ihre Beschäftigungsfähigkeit erheblich verbessern und Ihr Engagement in diesem Bereich demonstrieren. Erwägen Sie, die folgenden Zertifizierungen anzustreben:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Diese Einstiegszertifizierung bestätigt Ihr Verständnis von Sicherheitskonzepten, Netzwerksicherheit und Sicherheitspraktiken.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Diese Zertifizierung konzentriert sich auf ethische Hacking-Techniken und -Methoden, die Sie in die Lage versetzen, Schwachstellen zu bewerten und zu entschärfen.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP ist eine weltweit anerkannte Zertifizierung, die Ihr Fachwissen in verschiedenen Bereichen der Sicherheit bestätigt.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Diese Einstiegszertifizierung bestätigt Ihr Verständnis von Sicherheitskonzepten, Netzwerksicherheit und Sicherheitspraktiken.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Diese Zertifizierung konzentriert sich auf ethische Hacking-Techniken und -Methoden, die Sie in die Lage versetzen, Schwachstellen zu bewerten und zu entschärfen.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP ist eine weltweit anerkannte Zertifizierung, die Ihr Fachwissen in verschiedenen Bereichen der Sicherheit bestätigt.
Im Bereich der Cybersicherheit ist es wichtig, sich ständig weiterzubilden und über die neuesten Trends, Tools und Techniken auf dem Laufenden zu bleiben. Verfolgen Sie Branchenblogs, nehmen Sie an Online-Communities teil und besuchen Sie Cybersecurity-Konferenzen, um Ihr Wissen zu erweitern und sich mit Fachleuten zu vernetzen.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md
index 55022f1b906c1..baf481e387e4b 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.en.md
@@ -26,15 +26,15 @@ In recent years, cybersecurity has become a critical aspect of our digital lives
Before diving into the world of cybersecurity, it's important to lay a solid foundation of knowledge. Here are some essential areas to focus on:
-1. **Networking**: Understanding the fundamentals of networking is crucial in cybersecurity. Familiarize yourself with network protocols, IP addressing, routing, and [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/). Consider obtaining a certification such as CompTIA Network+ to validate your networking knowledge.
+1. **Networking**: Understanding the fundamentals of networking is crucial in cybersecurity. Familiarize yourself with network protocols, IP addressing, routing, and [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/). Consider obtaining a certification such as CompTIA Network+ to validate your networking knowledge.
2. **Operating Systems**: Gain proficiency in both Linux and Windows operating systems. Learn how to navigate the command line, configure system settings, and manage user accounts. CompTIA A+ and Linux+ certifications are excellent starting points to enhance your understanding of operating systems.
3. **Basic Computer Science Concepts**: Acquire a basic understanding of computer science principles, including algorithms, data structures, and programming languages. This knowledge will help you analyze vulnerabilities and develop secure software applications.
-4. **Coding Skills**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) can be advantageous in automating security tasks.
+4. **Coding Skills**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) can be advantageous in automating security tasks.
-5. **Enterprise System Administration**: Gaining experience in enterprise system administration will provide you with insights into managing complex IT infrastructures. Familiarize yourself with Active Directory, Group Policy, and [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/).
+5. **Enterprise System Administration**: Gaining experience in enterprise system administration will provide you with insights into managing complex IT infrastructures. Familiarize yourself with Active Directory, Group Policy, and [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/).
{{< inarticle-dark >}}
### Exploring Cybersecurity Domains
@@ -43,7 +43,7 @@ Cybersecurity encompasses various domains, each with its own unique focus. It's
1. **Blue Team**: Blue Team professionals focus on defending systems and networks from cyber threats. They design and implement security measures, monitor network traffic, and respond to incidents. Acquire knowledge of security tools, technologies, and best practices for effective defense.
-2. **Red Team**: Red Team professionals, also known as ethical hackers, specialize in assessing system vulnerabilities through simulated attacks. They identify weaknesses in security systems, conduct penetration testing, and help organizations strengthen their defenses. Develop hands-on skills in ethical hacking techniques and familiarize yourself with tools like [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/).
+2. **Red Team**: Red Team professionals, also known as ethical hackers, specialize in assessing system vulnerabilities through simulated attacks. They identify weaknesses in security systems, conduct penetration testing, and help organizations strengthen their defenses. Develop hands-on skills in ethical hacking techniques and familiarize yourself with tools like [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/).
3. **Purple Team**: The Purple Team combines elements of both Blue and Red Teams. They collaborate to enhance overall security posture by simulating realistic attack scenarios, evaluating defenses, and sharing insights. This role requires proficiency in both defensive and offensive techniques.
@@ -51,9 +51,9 @@ Cybersecurity encompasses various domains, each with its own unique focus. It's
While certifications are not mandatory, they can significantly enhance your employability and demonstrate your commitment to the field. Consider pursuing the following certifications:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): This entry-level certification validates your understanding of security concepts, network security, and security practices.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): This certification focuses on ethical hacking techniques and methodologies, enabling you to assess and mitigate vulnerabilities.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/): CISSP is a globally recognized certification that validates your expertise in various security domains.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/): This entry-level certification validates your understanding of security concepts, network security, and security practices.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/): This certification focuses on ethical hacking techniques and methodologies, enabling you to assess and mitigate vulnerabilities.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/): CISSP is a globally recognized certification that validates your expertise in various security domains.
Continuously learning and staying updated with the latest trends, tools, and techniques is crucial in cybersecurity. Follow industry blogs, participate in online communities, and attend cybersecurity conferences to expand your knowledge and network with professionals.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md
index c7ec1c590afcc..2f7a52ed2da10 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.es.md
@@ -24,15 +24,15 @@ En los últimos años, la ciberseguridad se ha convertido en un aspecto fundamen
Antes de sumergirse en el mundo de la ciberseguridad, es importante sentar unas bases sólidas de conocimiento. He aquí algunas áreas esenciales en las que centrarse:
-1. **Redes**: Comprender los fundamentos de las redes es crucial en ciberseguridad. Familiarícese con los protocolos de red, direccionamiento IP, enrutamiento y [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Considere la posibilidad de obtener una certificación como CompTIA Network+ para validar sus conocimientos de redes.
+1. **Redes**: Comprender los fundamentos de las redes es crucial en ciberseguridad. Familiarícese con los protocolos de red, direccionamiento IP, enrutamiento y [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Considere la posibilidad de obtener una certificación como CompTIA Network+ para validar sus conocimientos de redes.
2. **Sistemas operativos**: Adquiera destreza en los sistemas operativos Linux y Windows. Aprenda a navegar por la línea de comandos, configurar los ajustes del sistema y gestionar las cuentas de usuario. Las certificaciones CompTIA A+ y Linux+ son excelentes puntos de partida para mejorar su comprensión de los sistemas operativos.
3. **Conceptos básicos de informática**: Adquirir una comprensión básica de los principios de la informática, incluyendo algoritmos, estructuras de datos y lenguajes de programación. Estos conocimientos le ayudarán a analizar vulnerabilidades y a desarrollar aplicaciones de software seguras.
-4. **Habilidades de codificación [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) puede ser ventajoso para automatizar las tareas de seguridad.
+4. **Habilidades de codificación [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) puede ser ventajoso para automatizar las tareas de seguridad.
-5. **Administración de sistemas empresariales**: Adquirir experiencia en la administración de sistemas empresariales le proporcionará conocimientos sobre la gestión de infraestructuras informáticas complejas. Familiarícese con Active Directory, Group Policy y [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Administración de sistemas empresariales**: Adquirir experiencia en la administración de sistemas empresariales le proporcionará conocimientos sobre la gestión de infraestructuras informáticas complejas. Familiarícese con Active Directory, Group Policy y [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Explorando los dominios de la ciberseguridad
@@ -40,7 +40,7 @@ La ciberseguridad abarca varios ámbitos, cada uno con su propio enfoque. Es ese
1. **Equipo Azul**: Los profesionales del Equipo Azul se centran en defender los sistemas y redes de las ciberamenazas. Diseñan y aplican medidas de seguridad, supervisan el tráfico de la red y responden a los incidentes. Adquieren conocimientos sobre herramientas de seguridad, tecnologías y mejores prácticas para una defensa eficaz.
-2. **Equipo Rojo**: Los profesionales del Equipo Rojo, también conocidos como hackers éticos, están especializados en evaluar las vulnerabilidades de los sistemas mediante ataques simulados. Identifican los puntos débiles de los sistemas de seguridad, realizan pruebas de penetración y ayudan a las organizaciones a reforzar sus defensas. Desarrolla habilidades prácticas en técnicas de hacking ético y familiarízate con herramientas como [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Equipo Rojo**: Los profesionales del Equipo Rojo, también conocidos como hackers éticos, están especializados en evaluar las vulnerabilidades de los sistemas mediante ataques simulados. Identifican los puntos débiles de los sistemas de seguridad, realizan pruebas de penetración y ayudan a las organizaciones a reforzar sus defensas. Desarrolla habilidades prácticas en técnicas de hacking ético y familiarízate con herramientas como [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Equipo morado**: El Equipo Púrpura combina elementos de los Equipos Azul y Rojo. Colaboran para mejorar la postura global de seguridad mediante la simulación de escenarios de ataque realistas, la evaluación de las defensas y el intercambio de información. Esta función requiere competencia en técnicas defensivas y ofensivas.
@@ -48,9 +48,9 @@ La ciberseguridad abarca varios ámbitos, cada uno con su propio enfoque. Es ese
Aunque las certificaciones no son obligatorias, pueden mejorar significativamente sus posibilidades de empleo y demostrar su compromiso con este campo. Considere la posibilidad de obtener las siguientes certificaciones:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Esta certificación de nivel básico valida su comprensión de los conceptos de seguridad, seguridad de redes y prácticas de seguridad.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Esta certificación se centra en las técnicas y metodologías de hacking ético, permitiéndole evaluar y mitigar vulnerabilidades.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP es una certificación reconocida en todo el mundo que valida su experiencia en diversos ámbitos de la seguridad.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Esta certificación de nivel básico valida su comprensión de los conceptos de seguridad, seguridad de redes y prácticas de seguridad.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Esta certificación se centra en las técnicas y metodologías de hacking ético, permitiéndole evaluar y mitigar vulnerabilidades.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP es una certificación reconocida en todo el mundo que valida su experiencia en diversos ámbitos de la seguridad.
En el ámbito de la ciberseguridad, es fundamental aprender continuamente y mantenerse al día de las últimas tendencias, herramientas y técnicas. Siga los blogs del sector, participe en comunidades en línea y asista a conferencias sobre ciberseguridad para ampliar sus conocimientos y establecer contactos con profesionales.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md
index fcf6f449ed67d..1bb3ff3c539a1 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.fr.md
@@ -24,15 +24,15 @@ Ces dernières années, la cybersécurité est devenue un aspect essentiel de no
Avant de plonger dans le monde de la cybersécurité, il est important de poser des bases solides. Voici quelques domaines essentiels sur lesquels il convient de se concentrer :
-1. **Les réseaux** : En matière de cybersécurité, il est essentiel de comprendre les principes fondamentaux des réseaux. Familiarisez-vous avec les protocoles de réseau, l'adressage IP, le routage et les réseaux de communication. [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Envisagez d'obtenir une certification telle que CompTIA Network+ pour valider vos connaissances en matière de réseaux.
+1. **Les réseaux** : En matière de cybersécurité, il est essentiel de comprendre les principes fondamentaux des réseaux. Familiarisez-vous avec les protocoles de réseau, l'adressage IP, le routage et les réseaux de communication. [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Envisagez d'obtenir une certification telle que CompTIA Network+ pour valider vos connaissances en matière de réseaux.
2. **Systèmes d'exploitation** : Acquérir des compétences dans les systèmes d'exploitation Linux et Windows. Apprenez à naviguer dans la ligne de commande, à configurer les paramètres du système et à gérer les comptes d'utilisateurs. Les certifications CompTIA A+ et Linux+ sont d'excellents points de départ pour améliorer votre compréhension des systèmes d'exploitation.
3. **Concepts informatiques de base** : Acquérir une compréhension de base des principes de l'informatique, y compris les algorithmes, les structures de données et les langages de programmation. Ces connaissances vous aideront à analyser les vulnérabilités et à développer des applications logicielles sécurisées.
-4. **Compétence en codage** : [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) peut s'avérer utile pour automatiser les tâches liées à la sécurité.
+4. **Compétence en codage** : [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) peut s'avérer utile pour automatiser les tâches liées à la sécurité.
-5. **Administration de systèmes d'entreprise** : L'acquisition d'une expérience dans l'administration de systèmes d'entreprise vous permettra de mieux comprendre la gestion d'infrastructures informatiques complexes. Familiarisez-vous avec Active Directory, Group Policy et [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Administration de systèmes d'entreprise** : L'acquisition d'une expérience dans l'administration de systèmes d'entreprise vous permettra de mieux comprendre la gestion d'infrastructures informatiques complexes. Familiarisez-vous avec Active Directory, Group Policy et [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Explorer les domaines de la cybersécurité
@@ -40,7 +40,7 @@ La cybersécurité englobe différents domaines, chacun ayant son propre intér
1. **Équipe bleue** : Les professionnels de l'équipe bleue se concentrent sur la défense des systèmes et des réseaux contre les cybermenaces. Ils conçoivent et mettent en œuvre des mesures de sécurité, surveillent le trafic réseau et réagissent aux incidents. Acquérir des connaissances sur les outils de sécurité, les technologies et les meilleures pratiques pour une défense efficace.
-2. **Équipe rouge** : Les professionnels de l'équipe rouge, également connus sous le nom de hackers éthiques, sont spécialisés dans l'évaluation des vulnérabilités des systèmes par le biais d'attaques simulées. Ils identifient les faiblesses des systèmes de sécurité, effectuent des tests de pénétration et aident les organisations à renforcer leurs défenses. Développez des compétences pratiques dans les techniques de piratage éthique et familiarisez-vous avec des outils tels que [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Équipe rouge** : Les professionnels de l'équipe rouge, également connus sous le nom de hackers éthiques, sont spécialisés dans l'évaluation des vulnérabilités des systèmes par le biais d'attaques simulées. Ils identifient les faiblesses des systèmes de sécurité, effectuent des tests de pénétration et aident les organisations à renforcer leurs défenses. Développez des compétences pratiques dans les techniques de piratage éthique et familiarisez-vous avec des outils tels que [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **L'équipe violette** : L'équipe violette combine des éléments des équipes bleue et rouge. Elle collabore à l'amélioration du dispositif de sécurité global en simulant des scénarios d'attaque réalistes, en évaluant les défenses et en partageant des informations. Ce rôle exige une maîtrise des techniques défensives et offensives.
@@ -48,9 +48,9 @@ La cybersécurité englobe différents domaines, chacun ayant son propre intér
Bien que les certifications ne soient pas obligatoires, elles peuvent considérablement améliorer votre employabilité et démontrer votre engagement dans le domaine. Envisagez d'obtenir les certifications suivantes :
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Cette certification de niveau débutant valide votre compréhension des concepts de sécurité, de la sécurité des réseaux et des pratiques de sécurité.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Cette certification se concentre sur les techniques et méthodologies de piratage éthique, vous permettant d'évaluer et d'atténuer les vulnérabilités.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) Le CISSP est une certification mondialement reconnue qui valide votre expertise dans différents domaines de la sécurité.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Cette certification de niveau débutant valide votre compréhension des concepts de sécurité, de la sécurité des réseaux et des pratiques de sécurité.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Cette certification se concentre sur les techniques et méthodologies de piratage éthique, vous permettant d'évaluer et d'atténuer les vulnérabilités.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) Le CISSP est une certification mondialement reconnue qui valide votre expertise dans différents domaines de la sécurité.
Dans le domaine de la cybersécurité, il est essentiel de se former en permanence et de se tenir au courant des dernières tendances, des outils et des techniques les plus récents. Suivez les blogs du secteur, participez à des communautés en ligne et assistez à des conférences sur la cybersécurité afin d'élargir vos connaissances et de nouer des contacts avec des professionnels.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md
index f522c07f11055..983d82115cca6 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.it.md
@@ -24,15 +24,15 @@ Negli ultimi anni, la cybersecurity è diventata un aspetto critico della nostra
Prima di tuffarsi nel mondo della cybersecurity, è importante creare una solida base di conoscenze. Ecco alcune aree essenziali su cui concentrarsi:
-1. **Rete**: Comprendere i fondamenti del networking è fondamentale per la cybersecurity. Familiarizzate con i protocolli di rete, l'indirizzamento IP, l'instradamento e i protocolli di rete. [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Considerate la possibilità di ottenere una certificazione come CompTIA Network+ per convalidare le vostre conoscenze di networking.
+1. **Rete**: Comprendere i fondamenti del networking è fondamentale per la cybersecurity. Familiarizzate con i protocolli di rete, l'indirizzamento IP, l'instradamento e i protocolli di rete. [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Considerate la possibilità di ottenere una certificazione come CompTIA Network+ per convalidare le vostre conoscenze di networking.
2. **Sistemi operativi**: Acquisire competenze sui sistemi operativi Linux e Windows. Imparate a navigare nella riga di comando, a configurare le impostazioni di sistema e a gestire gli account utente. Le certificazioni CompTIA A+ e Linux+ sono ottimi punti di partenza per migliorare la comprensione dei sistemi operativi.
3. **Concetti di base di informatica**: Acquisire una conoscenza di base dei principi dell'informatica, compresi algoritmi, strutture di dati e linguaggi di programmazione. Queste conoscenze vi aiuteranno ad analizzare le vulnerabilità e a sviluppare applicazioni software sicure.
-4. **Competenze di codifica**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) può essere vantaggioso per automatizzare le attività di sicurezza.
+4. **Competenze di codifica**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) può essere vantaggioso per automatizzare le attività di sicurezza.
-5. **Amministrazione di sistemi aziendali**: L'esperienza nell'amministrazione di sistemi aziendali vi fornirà informazioni sulla gestione di infrastrutture IT complesse. Acquisire dimestichezza con Active Directory, Group Policy e [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Amministrazione di sistemi aziendali**: L'esperienza nell'amministrazione di sistemi aziendali vi fornirà informazioni sulla gestione di infrastrutture IT complesse. Acquisire dimestichezza con Active Directory, Group Policy e [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Esplorazione dei domini della sicurezza informatica
@@ -40,7 +40,7 @@ La cybersecurity comprende vari domini, ognuno dei quali ha un proprio obiettivo
1. **Blue Team**: I professionisti del Blue Team si concentrano sulla difesa dei sistemi e delle reti dalle minacce informatiche. Progettano e implementano misure di sicurezza, monitorano il traffico di rete e rispondono agli incidenti. Acquisiscono la conoscenza degli strumenti di sicurezza, delle tecnologie e delle best practice per una difesa efficace.
-2. **Red Team**: I professionisti del Red Team, noti anche come hacker etici, sono specializzati nella valutazione delle vulnerabilità dei sistemi attraverso attacchi simulati. Identificano i punti deboli dei sistemi di sicurezza, conducono test di penetrazione e aiutano le organizzazioni a rafforzare le loro difese. Sviluppate competenze pratiche nelle tecniche di hacking etico e familiarizzate con strumenti quali [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: I professionisti del Red Team, noti anche come hacker etici, sono specializzati nella valutazione delle vulnerabilità dei sistemi attraverso attacchi simulati. Identificano i punti deboli dei sistemi di sicurezza, conducono test di penetrazione e aiutano le organizzazioni a rafforzare le loro difese. Sviluppate competenze pratiche nelle tecniche di hacking etico e familiarizzate con strumenti quali [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Squadra viola**: Il team viola combina elementi dei team blu e rossi. Collaborano per migliorare la sicurezza generale simulando scenari di attacco realistici, valutando le difese e condividendo le intuizioni. Questo ruolo richiede la conoscenza di tecniche sia difensive che offensive.
@@ -48,9 +48,9 @@ La cybersecurity comprende vari domini, ognuno dei quali ha un proprio obiettivo
Anche se le certificazioni non sono obbligatorie, possono migliorare significativamente la vostra occupabilità e dimostrare il vostro impegno nel settore. Considerate la possibilità di conseguire le seguenti certificazioni:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Questa certificazione entry-level convalida la comprensione dei concetti di sicurezza, sicurezza di rete e pratiche di sicurezza.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Questa certificazione si concentra sulle tecniche e sulle metodologie di ethical hacking, consentendo di valutare e mitigare le vulnerabilità.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) Il CISSP è una certificazione riconosciuta a livello mondiale che convalida le vostre competenze in vari settori della sicurezza.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Questa certificazione entry-level convalida la comprensione dei concetti di sicurezza, sicurezza di rete e pratiche di sicurezza.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Questa certificazione si concentra sulle tecniche e sulle metodologie di ethical hacking, consentendo di valutare e mitigare le vulnerabilità.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) Il CISSP è una certificazione riconosciuta a livello mondiale che convalida le vostre competenze in vari settori della sicurezza.
L'apprendimento continuo e l'aggiornamento sulle ultime tendenze, strumenti e tecniche è fondamentale per la sicurezza informatica. Seguite i blog di settore, partecipate alle comunità online e frequentate le conferenze sulla sicurezza informatica per ampliare le vostre conoscenze e fare rete con i professionisti.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md
index fbaad5d6c3895..92c8d6f195718 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.ja.md
@@ -24,15 +24,15 @@ coverCaption: "サイバーセキュリティの専門家集団が一丸とな
サイバーセキュリティの世界に飛び込む前に、しっかりとした知識の土台を築くことが重要です。ここでは、重点的に学ぶべき重要な分野をいくつか紹介します:
-1.**ネットワーク**:ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて極めて重要です。ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて非常に重要である。 [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/)ネットワークに関する知識を証明するために、CompTIA Network+などの資格取得を検討する。
+1.**ネットワーク**:ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて極めて重要です。ネットワーク**:ネットワークの基礎を理解することは、サイバーセキュリティにおいて非常に重要である。 [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/)ネットワークに関する知識を証明するために、CompTIA Network+などの資格取得を検討する。
2.**オペレーティングシステム**:LinuxとWindowsの両方のオペレーティングシステムに習熟する。コマンドラインの操作方法、システム設定の方法、ユーザーアカウントの管理方法などを学びます。CompTIA A+とLinux+の資格は、オペレーティングシステムの理解を深めるための素晴らしい出発点です。
3.**コンピュータサイエンスの基本的な概念**:アルゴリズム、データ構造、プログラミング言語など、コンピュータサイエンスの原理を基本的に理解する。この知識は、脆弱性を分析し、安全なソフトウェアアプリケーションを開発するために役立ちます。
-4.**コーディングスキル**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/)は、セキュリティタスクの自動化に有利に働くことがあります。
+4.**コーディングスキル**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/)は、セキュリティタスクの自動化に有利に働くことがあります。
-5.**エンタープライズ・システム・アドミニストレーション**:企業システム管理の経験を積むことで、複雑なITインフラストラクチャを管理するための見識を得ることができます。Active Directory、Group Policy、およびSecurityに精通する。 [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5.**エンタープライズ・システム・アドミニストレーション**:企業システム管理の経験を積むことで、複雑なITインフラストラクチャを管理するための見識を得ることができます。Active Directory、Group Policy、およびSecurityに精通する。 [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### サイバーセキュリティの領域を探る
@@ -40,7 +40,7 @@ coverCaption: "サイバーセキュリティの専門家集団が一丸とな
1.1. **ブルーチーム**:ブルーチームの専門家は、システムやネットワークをサイバー脅威から守ることに重点を置いています。セキュリティ対策の設計と実装、ネットワークトラフィックの監視、インシデントへの対応などを行います。効果的な防御のためのセキュリティツール、技術、ベストプラクティスに関する知識を習得する。
-2.**レッドチーム**:倫理的ハッカーとして知られるレッドチームの専門家は、模擬攻撃を通じてシステムの脆弱性を評価することに特化しています。セキュリティシステムの弱点を特定し、侵入テストを実施し、組織の防御力強化を支援する。倫理的ハッキング技術の実践的なスキルを身につけ、以下のようなツールに精通する。 [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2.**レッドチーム**:倫理的ハッカーとして知られるレッドチームの専門家は、模擬攻撃を通じてシステムの脆弱性を評価することに特化しています。セキュリティシステムの弱点を特定し、侵入テストを実施し、組織の防御力強化を支援する。倫理的ハッキング技術の実践的なスキルを身につけ、以下のようなツールに精通する。 [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3.**パープルチーム**:Purple Teamは、Blue TeamとRed Teamの両方の要素を兼ね備えています。現実的な攻撃シナリオをシミュレートし、防御を評価し、洞察を共有することによって、全体的なセキュリティ態勢を強化するために協力する。この役割には、防御と攻撃の両方の技術に精通していることが必要です。
@@ -48,9 +48,9 @@ coverCaption: "サイバーセキュリティの専門家集団が一丸とな
認定資格は必須ではありませんが、取得することで雇用可能性が大幅に向上し、この分野へのコミットメントを示すことができます。以下の資格の取得を検討してください:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)このエントリーレベルの認定は、セキュリティの概念、ネットワークセキュリティ、およびセキュリティの実践についての理解を証明するものです。
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)この資格は、倫理的なハッキング技術と方法論に焦点を当て、脆弱性の評価と緩和を可能にします。
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)CISSPは、さまざまなセキュリティ領域における専門知識を証明する世界的に認められた資格です。
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)このエントリーレベルの認定は、セキュリティの概念、ネットワークセキュリティ、およびセキュリティの実践についての理解を証明するものです。
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)この資格は、倫理的なハッキング技術と方法論に焦点を当て、脆弱性の評価と緩和を可能にします。
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)CISSPは、さまざまなセキュリティ領域における専門知識を証明する世界的に認められた資格です。
サイバーセキュリティでは、継続的に学習し、最新のトレンド、ツール、テクニックを常に把握することが重要です。業界のブログをフォローし、オンラインコミュニティに参加し、サイバーセキュリティのカンファレンスに参加して、知識を深め、専門家とのネットワークを広げましょう。
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md
index 01c41f230934d..1cc86376f88e6 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.nl.md
@@ -24,15 +24,15 @@ In de afgelopen jaren is cyberbeveiliging een cruciaal aspect van ons digitale l
Voordat u zich in de wereld van cyberbeveiliging stort, is het belangrijk om een solide fundament van kennis te leggen. Hier zijn enkele essentiële gebieden waarop u zich moet richten:
-1. **Netwerken**: Inzicht in de grondbeginselen van netwerken is cruciaal voor cyberbeveiliging. Maak jezelf vertrouwd met netwerkprotocollen, IP-adressering, routing en [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Overweeg het behalen van een certificering zoals CompTIA Network+ om je netwerkkennis te valideren.
+1. **Netwerken**: Inzicht in de grondbeginselen van netwerken is cruciaal voor cyberbeveiliging. Maak jezelf vertrouwd met netwerkprotocollen, IP-adressering, routing en [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Overweeg het behalen van een certificering zoals CompTIA Network+ om je netwerkkennis te valideren.
2. **Besturingssystemen**: Krijg vaardigheid in zowel Linux als Windows besturingssystemen. Leer navigeren met de opdrachtregel, systeeminstellingen configureren en gebruikersaccounts beheren. CompTIA A+ en Linux+ certificeringen zijn uitstekende startpunten om je kennis van besturingssystemen te vergroten.
3. **Basisbegrippen uit de informatica**: Verwerf een basiskennis van de principes van computerwetenschappen, waaronder algoritmen, gegevensstructuren en programmeertalen. Deze kennis helpt je bij het analyseren van kwetsbaarheden en het ontwikkelen van veilige softwaretoepassingen.
-4. **Codeervaardigheden**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) kan voordelig zijn bij het automatiseren van beveiligingstaken.
+4. **Codeervaardigheden**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) kan voordelig zijn bij het automatiseren van beveiligingstaken.
-5. **Systeembeheer**: Ervaring opdoen met enterprise systeembeheer geeft je inzicht in het beheren van complexe IT-infrastructuren. Maak jezelf vertrouwd met Active Directory, Groepsbeleid en [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Systeembeheer**: Ervaring opdoen met enterprise systeembeheer geeft je inzicht in het beheren van complexe IT-infrastructuren. Maak jezelf vertrouwd met Active Directory, Groepsbeleid en [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Cyberbeveiligingsdomeinen verkennen
@@ -40,7 +40,7 @@ Cyberbeveiliging omvat verschillende domeinen, elk met zijn eigen unieke focus.
1. **Blauw team**: Blue Team-professionals richten zich op de verdediging van systemen en netwerken tegen cyberbedreigingen. Ze ontwerpen en implementeren beveiligingsmaatregelen, monitoren netwerkverkeer en reageren op incidenten. Ze verwerven kennis van beveiligingstools, technologieën en best practices voor een effectieve verdediging.
-2. **Red Team**: Red Team professionals, ook bekend als ethische hackers, zijn gespecialiseerd in het beoordelen van zwakke plekken in systemen door middel van gesimuleerde aanvallen. Ze identificeren zwakke plekken in beveiligingssystemen, voeren penetratietests uit en helpen organisaties hun verdediging te versterken. Ontwikkel praktische vaardigheden in ethische hacktechnieken en maak jezelf vertrouwd met tools zoals [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: Red Team professionals, ook bekend als ethische hackers, zijn gespecialiseerd in het beoordelen van zwakke plekken in systemen door middel van gesimuleerde aanvallen. Ze identificeren zwakke plekken in beveiligingssystemen, voeren penetratietests uit en helpen organisaties hun verdediging te versterken. Ontwikkel praktische vaardigheden in ethische hacktechnieken en maak jezelf vertrouwd met tools zoals [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Paars Team**: Het Purple Team combineert elementen van zowel het Blue als het Red Team. Ze werken samen om de algemene beveiliging te verbeteren door realistische aanvalsscenario's te simuleren, verdedigingen te evalueren en inzichten te delen. Deze rol vereist vaardigheid in zowel defensieve als offensieve technieken.
@@ -48,9 +48,9 @@ Cyberbeveiliging omvat verschillende domeinen, elk met zijn eigen unieke focus.
Hoewel certificeringen niet verplicht zijn, kunnen ze uw inzetbaarheid aanzienlijk vergroten en uw betrokkenheid bij het vak aantonen. Overweeg de volgende certificeringen te behalen:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Deze certificering op instapniveau valideert je begrip van beveiligingsconcepten, netwerkbeveiliging en beveiligingspraktijken.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Deze certificering richt zich op ethische hackingtechnieken en -methodologieën, waarmee je kwetsbaarheden kunt beoordelen en beperken.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP is een wereldwijd erkende certificering die je expertise in verschillende beveiligingsdomeinen valideert.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Deze certificering op instapniveau valideert je begrip van beveiligingsconcepten, netwerkbeveiliging en beveiligingspraktijken.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Deze certificering richt zich op ethische hackingtechnieken en -methodologieën, waarmee je kwetsbaarheden kunt beoordelen en beperken.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP is een wereldwijd erkende certificering die je expertise in verschillende beveiligingsdomeinen valideert.
Voortdurend leren en op de hoogte blijven van de nieuwste trends, tools en technieken is cruciaal in cyberbeveiliging. Volg industrieblogs, neem deel aan online communities en woon cyberbeveiligingsconferenties bij om uw kennis uit te breiden en te netwerken met professionals.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md
index 4266cb372d933..3af139dbd69ba 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/how-to-start-a-career-in-cyber-security/index.pl.md
@@ -24,15 +24,15 @@ W ostatnich latach cyberbezpieczeństwo stało się krytycznym aspektem naszego
Przed zanurzeniem się w świat cyberbezpieczeństwa ważne jest, aby położyć solidne fundamenty wiedzy. Oto kilka istotnych obszarów, na których należy się skupić:
-1. **Sieć**: Zrozumienie podstaw sieci ma kluczowe znaczenie dla cyberbezpieczeństwa. Zapoznanie się z protokołami sieciowymi, adresowaniem IP, routingiem i [subnetting](https://simeononsecurity.ch/articles/how-to-perform-network-segmentation-for-improved-security/) Rozważ uzyskanie certyfikatu, takiego jak CompTIA Network+, aby potwierdzić swoją wiedzę na temat sieci.
+1. **Sieć**: Zrozumienie podstaw sieci ma kluczowe znaczenie dla cyberbezpieczeństwa. Zapoznanie się z protokołami sieciowymi, adresowaniem IP, routingiem i [subnetting](https://simeononsecurity.com/articles/how-to-perform-network-segmentation-for-improved-security/) Rozważ uzyskanie certyfikatu, takiego jak CompTIA Network+, aby potwierdzić swoją wiedzę na temat sieci.
2. **Systemy operacyjne**: Zdobądź biegłość w systemach operacyjnych Linux i Windows. Dowiedz się, jak poruszać się po wierszu poleceń, konfigurować ustawienia systemowe i zarządzać kontami użytkowników. Certyfikaty CompTIA A+ i Linux+ są doskonałymi punktami wyjścia do lepszego zrozumienia systemów operacyjnych.
3. **Podstawowe koncepcje informatyki**: Zdobądź podstawowe zrozumienie zasad informatyki, w tym algorytmów, struktur danych i języków programowania. Wiedza ta pomoże ci analizować luki w zabezpieczeniach i tworzyć bezpieczne aplikacje.
-4. **Umiejętności kodowania**: [Learning a programming language](https://simeononsecurity.ch/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.ch/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.ch/articles/learning-powershell-scripting-for-beginners/) może być korzystna w automatyzacji zadań związanych z bezpieczeństwem.
+4. **Umiejętności kodowania**: [Learning a programming language](https://simeononsecurity.com/articles/should-i-learn-programming-for-cybersecurity-or-information-technology/) like [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is highly valuable in cybersecurity. [Python](https://simeononsecurity.com/articles/secure-coding-standards-for-python/) is versatile, widely used, and offers powerful libraries for security-related tasks. Additionally, knowledge of scripting languages like [PowerShell](https://simeononsecurity.com/articles/learning-powershell-scripting-for-beginners/) może być korzystna w automatyzacji zadań związanych z bezpieczeństwem.
-5. **Administracja systemami korporacyjnymi**: Zdobycie doświadczenia w administracji systemami korporacyjnymi zapewni ci wgląd w zarządzanie złożonymi infrastrukturami IT. Zapoznanie się z usługami Active Directory, Group Policy i [system hardening techniques](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/)
+5. **Administracja systemami korporacyjnymi**: Zdobycie doświadczenia w administracji systemami korporacyjnymi zapewni ci wgląd w zarządzanie złożonymi infrastrukturami IT. Zapoznanie się z usługami Active Directory, Group Policy i [system hardening techniques](https://simeononsecurity.com/github/windows-optimize-harden-debloat/)
### Odkrywanie domen cyberbezpieczeństwa
@@ -40,7 +40,7 @@ Cyberbezpieczeństwo obejmuje różne domeny, z których każda ma swój własny
1. **Blue Team**: Specjaliści Blue Team koncentrują się na obronie systemów i sieci przed cyberzagrożeniami. Projektują i wdrażają środki bezpieczeństwa, monitorują ruch sieciowy i reagują na incydenty. Zdobywają wiedzę na temat narzędzi bezpieczeństwa, technologii i najlepszych praktyk w celu skutecznej obrony.
-2. **Red Team**: Specjaliści Red Team, znani również jako etyczni hakerzy, specjalizują się w ocenie słabych punktów systemu poprzez symulowane ataki. Identyfikują słabe punkty w systemach bezpieczeństwa, przeprowadzają testy penetracyjne i pomagają organizacjom wzmocnić ich obronę. Rozwijaj praktyczne umiejętności w zakresie technik etycznego hakowania i zapoznaj się z narzędziami takimi jak [Metasploit](https://simeononsecurity.ch/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.ch/articles/the-role-of-penetration-testing-in-cybersecurity/)
+2. **Red Team**: Specjaliści Red Team, znani również jako etyczni hakerzy, specjalizują się w ocenie słabych punktów systemu poprzez symulowane ataki. Identyfikują słabe punkty w systemach bezpieczeństwa, przeprowadzają testy penetracyjne i pomagają organizacjom wzmocnić ich obronę. Rozwijaj praktyczne umiejętności w zakresie technik etycznego hakowania i zapoznaj się z narzędziami takimi jak [Metasploit](https://simeononsecurity.com/articles/what-is-metasploit/) and [Burp Suite](https://simeononsecurity.com/articles/the-role-of-penetration-testing-in-cybersecurity/)
3. **Purple Team**: Purpurowy zespół łączy w sobie elementy zespołów niebieskiego i czerwonego. Współpracują w celu poprawy ogólnego stanu bezpieczeństwa poprzez symulowanie realistycznych scenariuszy ataków, ocenę obrony i dzielenie się spostrzeżeniami. Rola ta wymaga biegłości zarówno w technikach defensywnych, jak i ofensywnych.
@@ -48,9 +48,9 @@ Cyberbezpieczeństwo obejmuje różne domeny, z których każda ma swój własny
Chociaż certyfikaty nie są obowiązkowe, mogą znacznie zwiększyć szanse na zatrudnienie i wykazać zaangażowanie w tę dziedzinę. Warto rozważyć uzyskanie następujących certyfikatów:
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Ten podstawowy certyfikat potwierdza zrozumienie koncepcji bezpieczeństwa, bezpieczeństwa sieci i praktyk bezpieczeństwa.
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Certyfikacja ta koncentruje się na technikach i metodologiach etycznego hakowania, umożliwiając ocenę i łagodzenie luk w zabezpieczeniach.
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP to uznawany na całym świecie certyfikat, który potwierdza wiedzę specjalistyczną w różnych dziedzinach bezpieczeństwa.
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/) Ten podstawowy certyfikat potwierdza zrozumienie koncepcji bezpieczeństwa, bezpieczeństwa sieci i praktyk bezpieczeństwa.
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/) Certyfikacja ta koncentruje się na technikach i metodologiach etycznego hakowania, umożliwiając ocenę i łagodzenie luk w zabezpieczeniach.
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/) CISSP to uznawany na całym świecie certyfikat, który potwierdza wiedzę specjalistyczną w różnych dziedzinach bezpieczeństwa.
Ciągłe uczenie się i bycie na bieżąco z najnowszymi trendami, narzędziami i technikami ma kluczowe znaczenie w cyberbezpieczeństwie. Śledź blogi branżowe, uczestnicz w społecznościach internetowych i bierz udział w konferencjach dotyczących cyberbezpieczeństwa, aby poszerzyć swoją wiedzę i nawiązać kontakty z profesjonalistami.
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md
index 292b8030460b8..986d1d709ae7e 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.de.md
@@ -71,9 +71,9 @@ Um als **Cybersicherheitsexperte** erfolgreich zu sein, muss man über eine Reih
Einschlägige Zertifizierungen sind für Fachleute im Bereich der Cybersicherheit ebenfalls von entscheidender Bedeutung, um ihre Fähigkeiten und ihr Fachwissen zu bestätigen. Einige weithin anerkannte Zertifizierungen sind:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Schlussfolgerung
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md
index dabe667671f62..343d8561f3f1c 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.en.md
@@ -73,9 +73,9 @@ To succeed as a **cybersecurity expert**, one must possess a range of technical
Obtaining relevant certifications is also crucial for cybersecurity professionals to validate their skills and expertise. Some widely recognized certifications include:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
{{< inarticle-dark >}}
## Conclusion
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md
index f487b3baf28db..86b6732b21f89 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.es.md
@@ -71,9 +71,9 @@ Para tener éxito como **experto en ciberseguridad**, hay que poseer una serie d
Obtener las certificaciones pertinentes también es crucial para que los profesionales de la ciberseguridad validen sus habilidades y conocimientos. Algunas certificaciones ampliamente reconocidas son:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusión
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md
index f97ab75a88ac6..b1dbf52e6d4e4 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.fr.md
@@ -71,9 +71,9 @@ Pour réussir en tant qu'**expert en cybersécurité**, il faut posséder un év
L'obtention de certifications pertinentes est également cruciale pour les professionnels de la cybersécurité afin de valider leurs compétences et leur expertise. Parmi les certifications largement reconnues, citons
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusion
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md
index e01ead9d4864a..d1ac037cd04e1 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.it.md
@@ -71,9 +71,9 @@ Gli **esperti di cybersecurity** lavorano spesso in conformità a varie normativ
Anche l'ottenimento di certificazioni pertinenti è fondamentale per i professionisti della cybersicurezza per convalidare le proprie capacità e competenze. Alcune certificazioni ampiamente riconosciute sono:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusione
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md
index 03c87d6110605..1d7588a905d99 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.ja.md
@@ -71,9 +71,9 @@ coverCaption: "知識とツールで武装したサイバーセキュリティ
サイバーセキュリティの専門家にとって、関連する認定資格を取得することも、スキルや専門知識を証明するために重要です。広く認知されている認定資格には、次のようなものがあります:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## 結論
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md
index d0e345ce2ae0f..37e36bbdca1a5 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.nl.md
@@ -71,9 +71,9 @@ Om als cyberbeveiligingsdeskundige** te slagen, moet iemand over een reeks techn
Het behalen van relevante certificeringen is ook cruciaal voor cyberbeveiligingsprofessionals om hun vaardigheden en expertise te valideren. Enkele algemeen erkende certificeringen zijn:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Conclusie
diff --git a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md
index 8fef07c115ca3..3f2fffb74e496 100644
--- a/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md
+++ b/content/cyber-security-career-playbook/getting-started-with-a-career-in-cybersecurity/what-does-a-cybersecurity-expert-do/index.pl.md
@@ -71,9 +71,9 @@ Aby odnieść sukces jako **ekspert ds. bezpieczeństwa cybernetycznego**, nale
Uzyskanie odpowiednich certyfikatów ma również kluczowe znaczenie dla specjalistów ds. cyberbezpieczeństwa w celu potwierdzenia ich umiejętności i wiedzy specjalistycznej. Niektóre powszechnie uznawane certyfikaty obejmują:
-- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.ch/articles/a-guide-to-earning-the-isc2-cissp-certification/)
-- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.ch/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
-- [**CompTIA Security+**](https://simeononsecurity.ch/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
+- [**Certified Information Systems Security Professional (CISSP)**](https://simeononsecurity.com/articles/a-guide-to-earning-the-isc2-cissp-certification/)
+- [**Certified Ethical Hacker (CEH)**](https://simeononsecurity.com/articles/preparing-for-the-ceh-certified-ethical-hacker-certification-exam/)
+- [**CompTIA Security+**](https://simeononsecurity.com/articles/comptias-security-plus-sy0-601-what-do-you-need-to-know/)
## Wnioski
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md
index b5b95e9ea56c1..210f510d62e93 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-a-security-training-and-awareness-program/index.en.md
@@ -36,7 +36,7 @@ Implementing a security awareness training program offers several benefits:
5. **Addressing insider threats:** Security awareness training helps employees recognize and report insider threats, such as malicious actions by employees or contractors. This ensures the organization remains vigilant against internal risks.
-6. **Improving password security:** Training employees on best practices for creating and managing [strong passwords](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/) enhances the overall password security posture of the organization, reducing the risk of unauthorized access.
+6. **Improving password security:** Training employees on best practices for creating and managing [strong passwords](https://simeononsecurity.com/articles/how-to-create-strong-passwords/) enhances the overall password security posture of the organization, reducing the risk of unauthorized access.
7. **Mitigating phishing and social engineering attacks:** Security awareness training equips employees with the knowledge to identify and report phishing emails and social engineering attempts, protecting the organization from these common attack vectors.
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md
index 626c8c4afc1b2..d0d935d4022c6 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-build-an-incident-responce-program/index.en.md
@@ -75,7 +75,7 @@ The third stage focuses on **containment and eradication**. Once an incident is
3. **System Restoration**: Restore affected systems to their normal state, ensuring that they are free from any malicious artifacts or backdoors. This may involve rebuilding systems from trusted sources or restoring them from clean backups.
-4. **Threat Hunting**: Conduct [proactive **threat hunting**](https://simeononsecurity.ch/articles/the-role-of-threat-hunting-in-proactive-cybersecurity/) activities to identify any remnants of the attacker's presence and ensure complete eradication. This includes thorough analysis of system logs, network traffic, and other relevant data sources.
+4. **Threat Hunting**: Conduct [proactive **threat hunting**](https://simeononsecurity.com/articles/the-role-of-threat-hunting-in-proactive-cybersecurity/) activities to identify any remnants of the attacker's presence and ensure complete eradication. This includes thorough analysis of system logs, network traffic, and other relevant data sources.
### Stage 4: Post-Incident Recovery
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md
index bfc0b6bae0023..84671133c4414 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/how-to-develop-cybersecurity-policies-and-procedures/index.en.md
@@ -17,7 +17,7 @@ coverCaption: "Secure Your Network: Defend Against Cyber Threats with Effective
### Introduction
-In today's digital landscape, **cybersecurity** is of paramount importance for organizations across industries. Developing a **comprehensive cybersecurity policy** is essential to protect sensitive information, mitigate risks, and maintain regulatory compliance. In this article, we will explore the key steps involved in developing a robust cybersecurity policy that aligns with industry best practices and regulatory requirements. We will also highlight the significance of industry standards such as the [**Risk Management Framework (RMF)**](https://simeononsecurity.ch/articles/mastering-risk-management-framework-cybersecurity/), **National Institute of Standards and Technology (NIST) Standards**, [**Payment Card Industry Data Security Standard (PCI-DSS)**](https://simeononsecurity.ch/articles/pci-dss-explained-card-transaction-security/), **Health Insurance Portability and Accountability Act (HIPAA)**, and [**Federal Information Security Modernization Act (FISMA)**](https://simeononsecurity.ch/articles/fisma-summarized/) in shaping cybersecurity policies.
+In today's digital landscape, **cybersecurity** is of paramount importance for organizations across industries. Developing a **comprehensive cybersecurity policy** is essential to protect sensitive information, mitigate risks, and maintain regulatory compliance. In this article, we will explore the key steps involved in developing a robust cybersecurity policy that aligns with industry best practices and regulatory requirements. We will also highlight the significance of industry standards such as the [**Risk Management Framework (RMF)**](https://simeononsecurity.com/articles/mastering-risk-management-framework-cybersecurity/), **National Institute of Standards and Technology (NIST) Standards**, [**Payment Card Industry Data Security Standard (PCI-DSS)**](https://simeononsecurity.com/articles/pci-dss-explained-card-transaction-security/), **Health Insurance Portability and Accountability Act (HIPAA)**, and [**Federal Information Security Modernization Act (FISMA)**](https://simeononsecurity.com/articles/fisma-summarized/) in shaping cybersecurity policies.
{{< youtube id="bsNzeJjFaAo" >}}
diff --git a/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md b/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md
index 0a205f51679c5..b727d893a345a 100644
--- a/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md
+++ b/content/cyber-security-career-playbook/managing-a-cyber-security-team/outsourcing-cybersecurity-efforts-is-it-a-good-idea/index.en.md
@@ -15,7 +15,7 @@ coverCaption: "Unleash the Power of Collaborative Cybersecurity Protection."
## Should I Outsource Any Part of Cybersecurity?
-In today's digital landscape, where **data breaches** and **cyber threats** are on the rise, businesses often face the dilemma of whether to outsource their cybersecurity operations. While having an in-house cybersecurity team may seem like the safer option, [outsourcing cybersecurity](https://simeononsecurity.ch/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) can offer several benefits, including a **unified cybersecurity strategy**. In this article, we will explore the factors to consider when deciding whether to outsource any part of cybersecurity, discuss the pros and cons, and provide best practices for effective outsourcing.
+In today's digital landscape, where **data breaches** and **cyber threats** are on the rise, businesses often face the dilemma of whether to outsource their cybersecurity operations. While having an in-house cybersecurity team may seem like the safer option, [outsourcing cybersecurity](https://simeononsecurity.com/articles/the-benefits-and-risks-of-oursourcing-cyberscurity-to-third-party-vendors/) can offer several benefits, including a **unified cybersecurity strategy**. In this article, we will explore the factors to consider when deciding whether to outsource any part of cybersecurity, discuss the pros and cons, and provide best practices for effective outsourcing.
{{< youtube id="iProPvIGVIY" >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md
index bca90928e93b9..5928b0e35db66 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/fisma-summarized/index.en.md
@@ -16,13 +16,13 @@ coverCaption: ""
## Introduction
-The [Federal Information Security Modernization Act (FISMA)](https://simeononsecurity.ch/articles/fisma-summarized/) is a US law enacted in 2002 that requires federal agencies to establish and maintain information security programs to protect their information and information systems. This act was passed in response to the growing need for improved information security in the federal government, and it has since been updated several times to keep pace with the changing threat landscape.
+The [Federal Information Security Modernization Act (FISMA)](https://simeononsecurity.com/articles/fisma-summarized/) is a US law enacted in 2002 that requires federal agencies to establish and maintain information security programs to protect their information and information systems. This act was passed in response to the growing need for improved information security in the federal government, and it has since been updated several times to keep pace with the changing threat landscape.
{{< youtube id="adxnNStDskA" >}}
-## [What is FISMA?](https://simeononsecurity.ch/articles/fisma-summarized/)
+## [What is FISMA?](https://simeononsecurity.com/articles/fisma-summarized/)
-[FISMA](https://simeononsecurity.ch/articles/fisma-summarized/) is a set of standards and guidelines for information security that apply to federal agencies and their contractors. The purpose of FISMA is to ensure that sensitive information is protected from unauthorized access, use, disclosure, disruption, modification, or destruction. FISMA requires that federal agencies implement a risk-based approach to information security, which involves identifying and assessing potential security risks, implementing security controls to mitigate those risks, and continuously monitoring the effectiveness of those controls.
+[FISMA](https://simeononsecurity.com/articles/fisma-summarized/) is a set of standards and guidelines for information security that apply to federal agencies and their contractors. The purpose of FISMA is to ensure that sensitive information is protected from unauthorized access, use, disclosure, disruption, modification, or destruction. FISMA requires that federal agencies implement a risk-based approach to information security, which involves identifying and assessing potential security risks, implementing security controls to mitigate those risks, and continuously monitoring the effectiveness of those controls.
{{< inarticle-dark >}}
## Key Components of FISMA
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md
index 5dee4d4b86016..2cb5ff989bd5d 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.de.md
@@ -28,11 +28,11 @@ Das National Institute of Standards and Technology (NIST) hat eine Richtlinie f
### Löschen
-Beim Löschen werden die Daten auf einem Gerät mit einer Reihe von Binärwerten überschrieben. Diese Methode ist weniger sicher als die physische Zerstörung, aber immer noch wirksam bei der Säuberung der meisten Wechseldatenträger. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die vom Verteidigungsministerium (DoD) festgelegten Standards erfüllt. [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) Spezifikation.
+Beim Löschen werden die Daten auf einem Gerät mit einer Reihe von Binärwerten überschrieben. Diese Methode ist weniger sicher als die physische Zerstörung, aber immer noch wirksam bei der Säuberung der meisten Wechseldatenträger. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die vom Verteidigungsministerium (DoD) festgelegten Standards erfüllt. [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) Spezifikation.
### Spülen
-Beim Bereinigen werden die Daten auf einem Gerät mehrfach mit einem Muster binärer Werte überschrieben. Diese Methode ist sicherer als das Löschen und wird für die Säuberung sensibler Daten empfohlen. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die von der NIST festgelegten Standards erfüllt. [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+Beim Bereinigen werden die Daten auf einem Gerät mehrfach mit einem Muster binärer Werte überschrieben. Diese Methode ist sicherer als das Löschen und wird für die Säuberung sensibler Daten empfohlen. NIST 800-88 Revision 1 empfiehlt die Verwendung eines Softwaretools, das die von der NIST festgelegten Standards erfüllt. [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md
index b0cfcc10995e7..85eae61faaeca 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.en.md
@@ -18,7 +18,7 @@ Removable media, such as hard drives, solid state drives (SSD), USB flash drives
**Sanitizing removable media is essential because the data stored on these devices can be easily recovered, even if the data has been deleted.** This is because when data is deleted, only the reference to the data is removed, but the actual data remains on the disk until it is overwritten. This makes it possible for malicious actors to recover sensitive data using data recovery software.
-## [NIST 800-88](https://simeononsecurity.ch/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 Types Of Destruction
+## [NIST 800-88](https://simeononsecurity.com/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 Types Of Destruction
The National Institute of Standards and Technology (NIST) has published a guideline for sanitizing removable media, known as NIST Special Publication 800-88 Revision 1. The guideline outlines several methods for sanitizing removable media, including physical destruction, clearing, and purging.
@@ -28,11 +28,11 @@ The National Institute of Standards and Technology (NIST) has published a guidel
### Clearing
-Clearing is the process of overwriting the data on a device with a series of binary values. This method is less secure than physical destruction but is still effective in sanitizing most removable media. [NIST 800-88](https://simeononsecurity.ch/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 recommends using a software tool that meets the standards set by the Department of Defense (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+Clearing is the process of overwriting the data on a device with a series of binary values. This method is less secure than physical destruction but is still effective in sanitizing most removable media. [NIST 800-88](https://simeononsecurity.com/articles/nist-800-88-ways-of-sanitizing-removable-media/) Revision 1 recommends using a software tool that meets the standards set by the Department of Defense (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
### Purging
-Purging is the process of overwriting the data on a device multiple times with a pattern of binary values. This method is more secure than clearing and is recommended for sanitizing sensitive data. NIST 800-88 Revision 1 recommends using a software tool that meets the standards set by the [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+Purging is the process of overwriting the data on a device multiple times with a pattern of binary values. This method is more secure than clearing and is recommended for sanitizing sensitive data. NIST 800-88 Revision 1 recommends using a software tool that meets the standards set by the [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md
index 55d84419fa2c3..685f93b5688be 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.es.md
@@ -28,11 +28,11 @@ El Instituto Nacional de Estándares y Tecnología (NIST) ha publicado una direc
### Borrado
-El borrado es el proceso de sobrescribir los datos de un dispositivo con una serie de valores binarios. Este método es menos seguro que la destrucción física, pero sigue siendo eficaz para desinfectar la mayoría de los soportes extraíbles. NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el Departamento de Defensa (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
+El borrado es el proceso de sobrescribir los datos de un dispositivo con una serie de valores binarios. Este método es menos seguro que la destrucción física, pero sigue siendo eficaz para desinfectar la mayoría de los soportes extraíbles. NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el Departamento de Defensa (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
### Purga
-La purga es el proceso de sobrescribir los datos de un dispositivo varias veces con un patrón de valores binarios. Este método es más seguro que el borrado y se recomienda para sanear datos sensibles. El NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
+La purga es el proceso de sobrescribir los datos de un dispositivo varias veces con un patrón de valores binarios. Este método es más seguro que el borrado y se recomienda para sanear datos sensibles. El NIST 800-88 Revisión 1 recomienda utilizar una herramienta de software que cumpla las normas establecidas por el [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) especificación.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md
index 7f40f0823d5ff..10e235553ec00 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.fr.md
@@ -28,11 +28,11 @@ Le National Institute of Standards and Technology (NIST) a publié une directive
### Nettoyage
-L'effacement consiste à remplacer les données d'un appareil par une série de valeurs binaires. Cette méthode est moins sûre que la destruction physique, mais reste efficace pour assainir la plupart des supports amovibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par le Département de la Défense (DoD). [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) spécification.
+L'effacement consiste à remplacer les données d'un appareil par une série de valeurs binaires. Cette méthode est moins sûre que la destruction physique, mais reste efficace pour assainir la plupart des supports amovibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par le Département de la Défense (DoD). [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) spécification.
### Purge
-La purge consiste à écraser plusieurs fois les données d'un dispositif avec un modèle de valeurs binaires. Cette méthode est plus sûre que l'effacement et est recommandée pour assainir les données sensibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par la [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
+La purge consiste à écraser plusieurs fois les données d'un dispositif avec un modèle de valeurs binaires. Cette méthode est plus sûre que l'effacement et est recommandée pour assainir les données sensibles. NIST 800-88 Revision 1 recommande l'utilisation d'un outil logiciel qui répond aux normes établies par la [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specification.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md
index 7877f6ac506d8..a9bf209c47eb8 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.it.md
@@ -28,11 +28,11 @@ Il National Institute of Standards and Technology (NIST) ha pubblicato una linea
### Cancellazione
-La cancellazione è il processo di sovrascrittura dei dati su un dispositivo con una serie di valori binari. Questo metodo è meno sicuro della distruzione fisica, ma è comunque efficace per sanificare la maggior parte dei supporti rimovibili. NIST 800-88 Revisione 1 raccomanda di utilizzare uno strumento software che soddisfi gli standard stabiliti dal Dipartimento della Difesa (DoD). [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
+La cancellazione è il processo di sovrascrittura dei dati su un dispositivo con una serie di valori binari. Questo metodo è meno sicuro della distruzione fisica, ma è comunque efficace per sanificare la maggior parte dei supporti rimovibili. NIST 800-88 Revisione 1 raccomanda di utilizzare uno strumento software che soddisfi gli standard stabiliti dal Dipartimento della Difesa (DoD). [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
### Spurgo
-L'epurazione è il processo di sovrascrittura dei dati su un dispositivo più volte con uno schema di valori binari. Questo metodo è più sicuro della cancellazione ed è consigliato per la sanificazione dei dati sensibili. Il NIST 800-88 Revisione 1 raccomanda l'utilizzo di uno strumento software che soddisfi gli standard stabiliti dall'Agenzia per la Sicurezza Nazionale (NIST). [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
+L'epurazione è il processo di sovrascrittura dei dati su un dispositivo più volte con uno schema di valori binari. Questo metodo è più sicuro della cancellazione ed è consigliato per la sanificazione dei dati sensibili. Il NIST 800-88 Revisione 1 raccomanda l'utilizzo di uno strumento software che soddisfi gli standard stabiliti dall'Agenzia per la Sicurezza Nazionale (NIST). [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specifiche.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md
index 28bbfd064d78f..804ca3b26d2d3 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ja.md
@@ -28,11 +28,11 @@ coverCaption: ""
### クリアリング
-クリアとは、デバイス上のデータを一連のバイナリ値で上書きするプロセスです。この方法は、物理的な破壊よりも安全性に劣るが、ほとんどのリムーバブル・メディアをサニタイズするには効果的である。NIST 800-88 Revision 1 では、国防総省(DoD)が定めた基準を満たすソフトウェアツールの使用を推奨しています。 [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
+クリアとは、デバイス上のデータを一連のバイナリ値で上書きするプロセスです。この方法は、物理的な破壊よりも安全性に劣るが、ほとんどのリムーバブル・メディアをサニタイズするには効果的である。NIST 800-88 Revision 1 では、国防総省(DoD)が定めた基準を満たすソフトウェアツールの使用を推奨しています。 [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
### パージ
-パージとは、デバイス上のデータをバイナリ値のパターンで複数回上書きする処理である。この方法はクリアよりも安全であり、機密データのサニタイズに推奨される。NIST 800-88 Revision 1 では、NIST 800-88 Revision 1 で設定された基準を満たすソフトウェア・ツールの使用を推奨しています。 [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
+パージとは、デバイス上のデータをバイナリ値のパターンで複数回上書きする処理である。この方法はクリアよりも安全であり、機密データのサニタイズに推奨される。NIST 800-88 Revision 1 では、NIST 800-88 Revision 1 で設定された基準を満たすソフトウェア・ツールの使用を推奨しています。 [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)スペック
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md
index 0112e9331ed8c..9c7ca02600ab7 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.nl.md
@@ -28,11 +28,11 @@ Het National Institute of Standards and Technology (NIST) heeft een richtlijn ge
### Schoonmaken
-Clearing is het proces waarbij de gegevens op een apparaat overschreven worden met een reeks binaire waarden. Deze methode is minder veilig dan fysieke vernietiging, maar is nog steeds effectief in het opschonen van de meeste verwijderbare media. NIST 800-88 Revisie 1 raadt aan een softwaretool te gebruiken dat voldoet aan de standaarden van het Ministerie van Defensie (DoD). [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
+Clearing is het proces waarbij de gegevens op een apparaat overschreven worden met een reeks binaire waarden. Deze methode is minder veilig dan fysieke vernietiging, maar is nog steeds effectief in het opschonen van de meeste verwijderbare media. NIST 800-88 Revisie 1 raadt aan een softwaretool te gebruiken dat voldoet aan de standaarden van het Ministerie van Defensie (DoD). [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
### Zuivering
-Zuiveren is het proces waarbij de gegevens op een apparaat meerdere keren worden overschreven met een patroon van binaire waarden. Deze methode is veiliger dan wissen en wordt aanbevolen voor het opschonen van gevoelige gegevens. NIST 800-88 Revisie 1 raadt aan om een softwaretool te gebruiken dat voldoet aan de normen van de [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
+Zuiveren is het proces waarbij de gegevens op een apparaat meerdere keren worden overschreven met een patroon van binaire waarden. Deze methode is veiliger dan wissen en wordt aanbevolen voor het opschonen van gevoelige gegevens. NIST 800-88 Revisie 1 raadt aan om een softwaretool te gebruiken dat voldoet aan de normen van de [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificatie.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md
index dbbd5cfd371d8..a9addf5f7a936 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.pl.md
@@ -28,11 +28,11 @@ National Institute of Standards and Technology (NIST) opublikował wytyczne doty
### Czyszczenie
-Czyszczenie to proces nadpisywania danych na urządzeniu serią wartości binarnych. Metoda ta jest mniej bezpieczna niż fizyczne niszczenie, ale nadal jest skuteczna w oczyszczaniu większości nośników wymiennych. NIST 800-88 Rev. 1 zaleca korzystanie z oprogramowania, które spełnia standardy określone przez Departament Obrony (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
+Czyszczenie to proces nadpisywania danych na urządzeniu serią wartości binarnych. Metoda ta jest mniej bezpieczna niż fizyczne niszczenie, ale nadal jest skuteczna w oczyszczaniu większości nośników wymiennych. NIST 800-88 Rev. 1 zaleca korzystanie z oprogramowania, które spełnia standardy określone przez Departament Obrony (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
### Czyszczenie
-Czyszczenie to proces wielokrotnego nadpisywania danych na urządzeniu wzorcem wartości binarnych. Metoda ta jest bezpieczniejsza niż czyszczenie i jest zalecana do oczyszczania wrażliwych danych. NIST 800-88 Rev. 1 zaleca użycie narzędzia programowego, które spełnia standardy określone przez [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
+Czyszczenie to proces wielokrotnego nadpisywania danych na urządzeniu wzorcem wartości binarnych. Metoda ta jest bezpieczniejsza niż czyszczenie i jest zalecana do oczyszczania wrażliwych danych. NIST 800-88 Rev. 1 zaleca użycie narzędzia programowego, które spełnia standardy określone przez [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specyfikacja.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md
index de97a4d675e9b..6c12f029cecb2 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ro.md
@@ -28,11 +28,11 @@ Institutul Național de Standarde și Tehnologie (NIST) a publicat un ghid de ig
### Clearing
-Curățarea este procesul de suprascriere a datelor de pe un dispozitiv cu o serie de valori binare. Această metodă este mai puțin sigură decât distrugerea fizică, dar este totuși eficientă pentru igienizarea majorității suporturilor detașabile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care respectă standardele stabilite de Departamentul Apărării (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
+Curățarea este procesul de suprascriere a datelor de pe un dispozitiv cu o serie de valori binare. Această metodă este mai puțin sigură decât distrugerea fizică, dar este totuși eficientă pentru igienizarea majorității suporturilor detașabile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care respectă standardele stabilite de Departamentul Apărării (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
### Purgare
-Purjarea este procesul de suprascriere de mai multe ori a datelor de pe un dispozitiv cu un model de valori binare. Această metodă este mai sigură decât ștergerea și este recomandată pentru curățarea datelor sensibile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care să respecte standardele stabilite de către [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
+Purjarea este procesul de suprascriere de mai multe ori a datelor de pe un dispozitiv cu un model de valori binare. Această metodă este mai sigură decât ștergerea și este recomandată pentru curățarea datelor sensibile. NIST 800-88 Revizia 1 recomandă utilizarea unui instrument software care să respecte standardele stabilite de către [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) specificații.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md
index 9b5cd789aa5b9..a9fa0b708f972 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.ru.md
@@ -28,11 +28,11 @@ coverCaption: ""
### Очистка
-Очистка - это процесс перезаписи данных на устройстве серией двоичных значений. Этот метод менее безопасен, чем физическое уничтожение, но все же эффективен для обезвреживания большинства съемных носителей. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным Министерством обороны (DoD) [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
+Очистка - это процесс перезаписи данных на устройстве серией двоичных значений. Этот метод менее безопасен, чем физическое уничтожение, но все же эффективен для обезвреживания большинства съемных носителей. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным Министерством обороны (DoD) [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
### Очистка
-Очистка - это процесс многократной перезаписи данных на устройстве с помощью шаблона двоичных значений. Этот метод более безопасен, чем очистка, и рекомендуется для обезвреживания конфиденциальных данных. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
+Очистка - это процесс многократной перезаписи данных на устройстве с помощью шаблона двоичных значений. Этот метод более безопасен, чем очистка, и рекомендуется для обезвреживания конфиденциальных данных. NIST 800-88 Revision 1 рекомендует использовать программное средство, соответствующее стандартам, установленным [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/) спецификация.
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md
index 93a915c7906ef..8c208cc2077e8 100644
--- a/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md
+++ b/content/cyber-security-career-playbook/moving-up-in-your-cybersecurity-career/regulations-and-acts/nist-800-88-ways-of-sanitizing-removable-media/index.zh.md
@@ -28,11 +28,11 @@ coverCaption: ""
### 清除
-清除是用一系列二进制值覆盖设备上数据的过程。这种方法不如物理销毁方法安全,但仍能有效清除大多数可移动媒体。NIST 800-88 Revision 1 建议使用符合国防部 (DoD) 标准的软件工具。 [5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
+清除是用一系列二进制值覆盖设备上数据的过程。这种方法不如物理销毁方法安全,但仍能有效清除大多数可移动媒体。NIST 800-88 Revision 1 建议使用符合国防部 (DoD) 标准的软件工具。 [5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
### 清除
-清除是用二进制值模式多次覆盖设备上数据的过程。这种方法比清除更安全,建议用于清除敏感数据。NIST 800-88 Revision 1 建议使用符合 NIST 800-88 Revision 1 标准的软件工具。 [DoD 5220.22-M](https://simeononsecurity.ch/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
+清除是用二进制值模式多次覆盖设备上数据的过程。这种方法比清除更安全,建议用于清除敏感数据。NIST 800-88 Revision 1 建议使用符合 NIST 800-88 Revision 1 标准的软件工具。 [DoD 5220.22-M](https://simeononsecurity.com/articles/dod-5220.22-m-data-sanitization-summarized/)规格。
__________________________________________
{{< inarticle-dark >}}
diff --git a/content/github/Automate-Sysmon/index.bn.md b/content/github/Automate-Sysmon/index.bn.md
index 92213e93a57f2..c930afeb44eb1 100644
--- a/content/github/Automate-Sysmon/index.bn.md
+++ b/content/github/Automate-Sysmon/index.bn.md
@@ -27,7 +27,7 @@ Automate-Sysmon ব্যবহার করার দুটি উপায়
স্বয়ংক্রিয় ইনস্টলেশন ব্যবহার করতে, PowerShell-এ কেবল নিম্নলিখিত কমান্ডটি চালান:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ca.md b/content/github/Automate-Sysmon/index.ca.md
index 9731571e7edf2..7e7a370408083 100644
--- a/content/github/Automate-Sysmon/index.ca.md
+++ b/content/github/Automate-Sysmon/index.ca.md
@@ -27,7 +27,7 @@ Hi ha dues maneres d'utilitzar Automate-Sysmon:
Per utilitzar la instal·lació automatitzada, només cal que executeu l'ordre següent a PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.de.md b/content/github/Automate-Sysmon/index.de.md
index c387737f63c82..97f8c62fd5756 100644
--- a/content/github/Automate-Sysmon/index.de.md
+++ b/content/github/Automate-Sysmon/index.de.md
@@ -27,7 +27,7 @@ Es gibt zwei Möglichkeiten, Automate-Sysmon zu verwenden:
Um die automatische Installation zu verwenden, führen Sie einfach den folgenden Befehl in PowerShell aus:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Dadurch wird das Automate-Sysmon-Skript automatisch heruntergeladen und ausgeführt.
diff --git a/content/github/Automate-Sysmon/index.en.md b/content/github/Automate-Sysmon/index.en.md
index cb5b3bdc98157..7a99a1d2f486c 100644
--- a/content/github/Automate-Sysmon/index.en.md
+++ b/content/github/Automate-Sysmon/index.en.md
@@ -27,7 +27,7 @@ There are two ways to use Automate-Sysmon:
To use the automated installation, simply run the following command in PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.es.md b/content/github/Automate-Sysmon/index.es.md
index 239e101328499..b2e7e89d44169 100644
--- a/content/github/Automate-Sysmon/index.es.md
+++ b/content/github/Automate-Sysmon/index.es.md
@@ -27,7 +27,7 @@ Hay dos formas de utilizar Automate-Sysmon:
Para utilizar la instalación automatizada, simplemente ejecute el siguiente comando en PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Esto descargará y ejecutará automáticamente el script Automate-Sysmon.
diff --git a/content/github/Automate-Sysmon/index.fr.md b/content/github/Automate-Sysmon/index.fr.md
index 864c1b0b92bb8..a4e4d317bdc09 100644
--- a/content/github/Automate-Sysmon/index.fr.md
+++ b/content/github/Automate-Sysmon/index.fr.md
@@ -27,7 +27,7 @@ Il y a deux façons d'utiliser Automate-Sysmon :
Pour utiliser l'installation automatisée, il suffit d'exécuter la commande suivante dans PowerShell :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Ceci téléchargera et exécutera automatiquement le script Automate-Sysmon.
diff --git a/content/github/Automate-Sysmon/index.it.md b/content/github/Automate-Sysmon/index.it.md
index f3366d29571ef..73cdbf8ca1fb4 100644
--- a/content/github/Automate-Sysmon/index.it.md
+++ b/content/github/Automate-Sysmon/index.it.md
@@ -27,7 +27,7 @@ Esistono due modi per utilizzare Automate-Sysmon:
Per utilizzare l'installazione automatica, esegui semplicemente il seguente comando in PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ja.md b/content/github/Automate-Sysmon/index.ja.md
index 61842744848b4..4dbb0a14e0a58 100644
--- a/content/github/Automate-Sysmon/index.ja.md
+++ b/content/github/Automate-Sysmon/index.ja.md
@@ -27,7 +27,7 @@ Automate-Sysmon を使用するには 2 つの方法があります。
自動インストールを使用するには、PowerShell で次のコマンドを実行するだけです。
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.nl.md b/content/github/Automate-Sysmon/index.nl.md
index a749560246496..2507cd14fdbd2 100644
--- a/content/github/Automate-Sysmon/index.nl.md
+++ b/content/github/Automate-Sysmon/index.nl.md
@@ -27,7 +27,7 @@ Er zijn twee manieren om Automate-Sysmon te gebruiken:
Om de geautomatiseerde installatie te gebruiken, voert u gewoon de volgende opdracht uit in PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Dit zal automatisch het Automate-Sysmon script downloaden en uitvoeren.
diff --git a/content/github/Automate-Sysmon/index.pa.md b/content/github/Automate-Sysmon/index.pa.md
index 894fcd21cca18..fd26b2b169a4e 100644
--- a/content/github/Automate-Sysmon/index.pa.md
+++ b/content/github/Automate-Sysmon/index.pa.md
@@ -27,7 +27,7 @@ tags: ["ਸਿਸਮੋਨ ਨੂੰ ਆਟੋਮੈਟਿਕ ਕਰੋ", "ਸ
ਆਟੋਮੈਟਿਕ ਇੰਸਟਾਲੇਸ਼ਨ ਦੀ ਵਰਤੋਂ ਕਰਨ ਲਈ, PowerShell ਵਿੱਚ ਸਿਰਫ਼ ਹੇਠ ਦਿੱਤੀ ਕਮਾਂਡ ਚਲਾਓ:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.pl.md b/content/github/Automate-Sysmon/index.pl.md
index 3f50b06a7d201..dc080c99d0e7d 100644
--- a/content/github/Automate-Sysmon/index.pl.md
+++ b/content/github/Automate-Sysmon/index.pl.md
@@ -27,7 +27,7 @@ Istnieją dwa sposoby korzystania z Automate-Sysmon:
Aby użyć automatycznej instalacji, wystarczy uruchomić następujące polecenie w PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
Spowoduje to automatyczne pobranie i uruchomienie skryptu Automate-Sysmon.
diff --git a/content/github/Automate-Sysmon/index.pt.md b/content/github/Automate-Sysmon/index.pt.md
index 480bd76af30d6..426df8096f8eb 100644
--- a/content/github/Automate-Sysmon/index.pt.md
+++ b/content/github/Automate-Sysmon/index.pt.md
@@ -27,7 +27,7 @@ Existem duas maneiras de usar o Automate-Sysmon:
Para usar a instalação automatizada, basta executar o seguinte comando no PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ro.md b/content/github/Automate-Sysmon/index.ro.md
index a1845cbbf29e3..eb5f9bf5a52ff 100644
--- a/content/github/Automate-Sysmon/index.ro.md
+++ b/content/github/Automate-Sysmon/index.ro.md
@@ -27,7 +27,7 @@ Există două moduri de a utiliza Automate-Sysmon:
Pentru a utiliza instalarea automată, pur și simplu rulați următoarea comandă în PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.ru.md b/content/github/Automate-Sysmon/index.ru.md
index 2e97a0a804a09..f8f4ee3466260 100644
--- a/content/github/Automate-Sysmon/index.ru.md
+++ b/content/github/Automate-Sysmon/index.ru.md
@@ -27,7 +27,7 @@ Sysmon — это инструмент мониторинга системы, к
Чтобы использовать автоматическую установку, просто выполните следующую команду в PowerShell:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Automate-Sysmon/index.zh.md b/content/github/Automate-Sysmon/index.zh.md
index 8b98d3882004e..3fc6284097f60 100644
--- a/content/github/Automate-Sysmon/index.zh.md
+++ b/content/github/Automate-Sysmon/index.zh.md
@@ -27,7 +27,7 @@ Automate-Sysmon 有两种使用方式:
要使用自动安装,只需在 PowerShell 中运行以下命令:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosautomatesysmon.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosautomatesysmon.ps1'|iex
```
This will automatically download and run the Automate-Sysmon script.
diff --git a/content/github/Offline-PS-ActiveDirectory-Install/index.en.md b/content/github/Offline-PS-ActiveDirectory-Install/index.en.md
index 25bb6f338c692..d6d5b1a2aba50 100644
--- a/content/github/Offline-PS-ActiveDirectory-Install/index.en.md
+++ b/content/github/Offline-PS-ActiveDirectory-Install/index.en.md
@@ -42,15 +42,15 @@ The script will perform the following actions:
- Copy the necessary files and modules to the appropriate locations on your system.
- Unblock the new PowerShell modules and DLLs.
-- [Import the Active Directory module](https://simeononsecurity.ch/articles/active-directory-module-powershell-installation-usage-guide/) and DLLs using the `Import-Module` command.
+- [Import the Active Directory module](https://simeononsecurity.com/articles/active-directory-module-powershell-installation-usage-guide/) and DLLs using the `Import-Module` command.
- Once the script execution is complete, you will have the Active Directory PowerShell module installed on your Windows 10 machine.
**Verifying the Installation**
-To verify that the [Active Directory PowerShell module](https://simeononsecurity.ch/articles/active-directory-module-powershell-installation-usage-guide/) is installed correctly, follow these steps:
+To verify that the [Active Directory PowerShell module](https://simeononsecurity.com/articles/active-directory-module-powershell-installation-usage-guide/) is installed correctly, follow these steps:
1. Open a PowerShell terminal.
-2. Run the command [`Import-Module ActiveDirectory`](https://simeononsecurity.ch/articles/active-directory-module-powershell-installation-usage-guide/).
+2. Run the command [`Import-Module ActiveDirectory`](https://simeononsecurity.com/articles/active-directory-module-powershell-installation-usage-guide/).
3. If no errors are displayed, the module is successfully installed.
**Conclusion**
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.de.md b/content/github/System-Wide-Windows-Ad-Blocker/index.de.md
index 552ea999fcf74..4d352e01eba6e 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.de.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.de.md
@@ -27,6 +27,6 @@ Dieses Skript ist ein Windows PowerShell-Skript, das die Datei "StevenBlack/host
#### Automatisch installieren:
Führen Sie die neueste Version des Skripts automatisch aus:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.en.md b/content/github/System-Wide-Windows-Ad-Blocker/index.en.md
index a6e57ae2db373..f35dc453e179d 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.en.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.en.md
@@ -27,6 +27,6 @@ This script is a Windows PowerShell script that downloads and applies the "Steve
#### Automated install:
Run the latest version of the script automatically:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.es.md b/content/github/System-Wide-Windows-Ad-Blocker/index.es.md
index 624255540c3e5..8295d150fa959 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.es.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.es.md
@@ -27,6 +27,6 @@ Este script es un script de Windows PowerShell que descarga y aplica el archivo
#### Instalación automática:
Ejecuta automáticamente la última versión del script:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md b/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md
index 02be56decffe9..6fdf41ece8052 100644
--- a/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md
+++ b/content/github/System-Wide-Windows-Ad-Blocker/index.fr.md
@@ -27,6 +27,6 @@ Ce script est un script Windows PowerShell qui télécharge et applique le fichi
#### Installation automatisée :
Exécutez automatiquement la dernière version du script :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/soswindowsadblocker.ps1' | iex
+iwr -useb 'https://simeononsecurity.com/scripts/soswindowsadblocker.ps1' | iex
```
diff --git a/content/github/Windows-Branding-Script/index.de.md b/content/github/Windows-Branding-Script/index.de.md
index cedc3ab80e5c7..fb97f77b2a5c3 100644
--- a/content/github/Windows-Branding-Script/index.de.md
+++ b/content/github/Windows-Branding-Script/index.de.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automatisierte Installation:
Das Skript kann aus dem extrahierten GitHub-Download wie folgt gestartet werden:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.en.md b/content/github/Windows-Branding-Script/index.en.md
index c14ab2cd126c2..f954496cbffb3 100644
--- a/content/github/Windows-Branding-Script/index.en.md
+++ b/content/github/Windows-Branding-Script/index.en.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.es.md b/content/github/Windows-Branding-Script/index.es.md
index 2b7ce802ce37c..b14fbd49d1728 100644
--- a/content/github/Windows-Branding-Script/index.es.md
+++ b/content/github/Windows-Branding-Script/index.es.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.fr.md b/content/github/Windows-Branding-Script/index.fr.md
index bdd545a79fc24..3e512ec658a40 100644
--- a/content/github/Windows-Branding-Script/index.fr.md
+++ b/content/github/Windows-Branding-Script/index.fr.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.it.md b/content/github/Windows-Branding-Script/index.it.md
index efeb90537ced7..619255411d275 100644
--- a/content/github/Windows-Branding-Script/index.it.md
+++ b/content/github/Windows-Branding-Script/index.it.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installazione automatica:
Lo script può essere lanciato dal download estratto da GitHub in questo modo:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.ja.md b/content/github/Windows-Branding-Script/index.ja.md
index 237e3f0c868ac..fb29a8c8cca68 100644
--- a/content/github/Windows-Branding-Script/index.ja.md
+++ b/content/github/Windows-Branding-Script/index.ja.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### 自動インストール:
スクリプトは、GitHubからダウンロードしたものを次のように起動することができます:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.nl.md b/content/github/Windows-Branding-Script/index.nl.md
index 4ccb0ca491a5e..1709e5b100df7 100644
--- a/content/github/Windows-Branding-Script/index.nl.md
+++ b/content/github/Windows-Branding-Script/index.nl.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Geautomatiseerde installatie:
Het script kan vanaf de uitgepakte GitHub-download als volgt worden gestart:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.pl.md b/content/github/Windows-Branding-Script/index.pl.md
index ef09a923330dc..dd77f482d7730 100644
--- a/content/github/Windows-Branding-Script/index.pl.md
+++ b/content/github/Windows-Branding-Script/index.pl.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automatyczna instalacja:
Skrypt można uruchomić z wyodrębnionego pliku do pobrania z GitHub w następujący sposób:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.ro.md b/content/github/Windows-Branding-Script/index.ro.md
index b99e4c22fdc48..30a7197886367 100644
--- a/content/github/Windows-Branding-Script/index.ro.md
+++ b/content/github/Windows-Branding-Script/index.ro.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
Scriptul poate fi lansat din descărcarea extrasă de pe GitHub astfel:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.ru.md b/content/github/Windows-Branding-Script/index.ru.md
index 56bdb8772e171..e53b2b89185aa 100644
--- a/content/github/Windows-Branding-Script/index.ru.md
+++ b/content/github/Windows-Branding-Script/index.ru.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Автоматическая установка:
Скрипт может быть запущен из распакованной загрузки с GitHub следующим образом:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Branding-Script/index.zh.md b/content/github/Windows-Branding-Script/index.zh.md
index 55fa87ecc0e59..3840e47199187 100644
--- a/content/github/Windows-Branding-Script/index.zh.md
+++ b/content/github/Windows-Branding-Script/index.zh.md
@@ -31,6 +31,6 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
#### 自动安装:
可以像这样从 GitHub 下载的提取文件中启动脚本:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/sosbranding.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/sosbranding.ps1'|iex
```
diff --git a/content/github/Windows-Defender-Application-Control-Hardening/index.en.md b/content/github/Windows-Defender-Application-Control-Hardening/index.en.md
index 68e444914de4b..9c99e35c1b738 100644
--- a/content/github/Windows-Defender-Application-Control-Hardening/index.en.md
+++ b/content/github/Windows-Defender-Application-Control-Hardening/index.en.md
@@ -11,7 +11,7 @@ tags: ["Windows Defender Application Control WDAC Hardening", "PowerShell", "Pow
## Notes:
- Windows Server 2016/2019 or anything before version 1903 only support a single legacy policy at a time.
-- Windows Server Core edition supports [WDAC](https://simeononsecurity.ch/til/2022-05-18/) but some components that depend on AppLocker won’t work
+- Windows Server Core edition supports [WDAC](https://simeononsecurity.com/til/2022-05-18/) but some components that depend on AppLocker won’t work
- Please read the [Recommended Reading](https://github.com/simeononsecurity/Windows-Defender-Application-Control-Hardening#recommended-reading) before implementing or even testing.
## A list of scripts and tools this collection utilizes:
diff --git a/content/github/Windows-Hardening-CTF/index.en.md b/content/github/Windows-Hardening-CTF/index.en.md
index 5e1662de9ba34..f6a18cc3d89dc 100644
--- a/content/github/Windows-Hardening-CTF/index.en.md
+++ b/content/github/Windows-Hardening-CTF/index.en.md
@@ -19,7 +19,7 @@ A windows hardening script that makes it difficult and more annoying to compromi
- Disables SMB v2
- Disables TCP Timestamps
- Disables WSMAN and PSRemoting
-- [Enables AppLocker with NSA Recommended Policies](https://simeononsecurity.ch/github/applocker-hardening/)
+- [Enables AppLocker with NSA Recommended Policies](https://simeononsecurity.com/github/applocker-hardening/)
- Enables Best practice Windows Logging and Security Controls
- Enables DEP
- Enables EMET Configurations (Only applies to systems with EMET installed)
diff --git a/content/github/Windows-Optimize-Debloat/index.de.md b/content/github/Windows-Optimize-Debloat/index.de.md
index 05242aa5bac7e..c168134413f1d 100644
--- a/content/github/Windows-Optimize-Debloat/index.de.md
+++ b/content/github/Windows-Optimize-Debloat/index.de.md
@@ -59,7 +59,7 @@ Wenn Sie diese Dienste dennoch nutzen möchten, finden Sie die Lösung in den fo
### Automatisierte Installation:
Das Skript kann wie folgt aus dem extrahierten GitHub-Download gestartet werden:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Manuelle Installation:
Wenn das Skript manuell heruntergeladen wird, muss es von einer administrativen Powershell in dem Verzeichnis gestartet werden, das alle Dateien aus dem [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.en.md b/content/github/Windows-Optimize-Debloat/index.en.md
index 2a55ae6eaa3ef..36e11c45c60e3 100644
--- a/content/github/Windows-Optimize-Debloat/index.en.md
+++ b/content/github/Windows-Optimize-Debloat/index.en.md
@@ -59,7 +59,7 @@ However, if you still wish to use these services see the following issue tickets
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Manual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.es.md b/content/github/Windows-Optimize-Debloat/index.es.md
index de87f05eecb42..0d10421242953 100644
--- a/content/github/Windows-Optimize-Debloat/index.es.md
+++ b/content/github/Windows-Optimize-Debloat/index.es.md
@@ -59,7 +59,7 @@ Sin embargo, si usted todavía desea utilizar estos servicios ver los siguientes
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Instalación manual:
Si se descarga manualmente, el script debe ser lanzado desde un powershell administrativo en el directorio que contiene todos los archivos del [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.fr.md b/content/github/Windows-Optimize-Debloat/index.fr.md
index 5e00b09d02f47..73144d6a13e55 100644
--- a/content/github/Windows-Optimize-Debloat/index.fr.md
+++ b/content/github/Windows-Optimize-Debloat/index.fr.md
@@ -59,7 +59,7 @@ Cependant, si vous souhaitez toujours utiliser ces services, consultez les ticke
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Installation manuelle :
S'il est téléchargé manuellement, le script doit être lancé à partir d'un powerhell d'administration dans le répertoire contenant tous les fichiers du fichier [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.it.md b/content/github/Windows-Optimize-Debloat/index.it.md
index ab32e5fa2bebd..cffc9f82e20ef 100644
--- a/content/github/Windows-Optimize-Debloat/index.it.md
+++ b/content/github/Windows-Optimize-Debloat/index.it.md
@@ -59,7 +59,7 @@ Tuttavia, se si desidera utilizzare questi servizi, consultare i seguenti ticket
### Installazione automatica:
Lo script può essere lanciato dal download estratto da GitHub in questo modo:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Installazione manuale:
Se scaricato manualmente, lo script deve essere lanciato da una powershell amministrativa nella directory contenente tutti i file del file [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.ja.md b/content/github/Windows-Optimize-Debloat/index.ja.md
index d7486df8cdf13..39fb88ff5d9a3 100644
--- a/content/github/Windows-Optimize-Debloat/index.ja.md
+++ b/content/github/Windows-Optimize-Debloat/index.ja.md
@@ -59,7 +59,7 @@ Windows 10 と 11 は、箱から出したままでは侵略的で安全でな
### 自動インストール:
自動インストール:GitHubからダウンロードしたスクリプトを、以下のように起動します:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### 手動でインストールします:
手動でダウンロードした場合、スクリプトは、管理用パワーシェルから、以下のすべてのファイルが含まれるディレクトリで起動する必要があります。 [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.nl.md b/content/github/Windows-Optimize-Debloat/index.nl.md
index 38720aea48e83..6034676de78f8 100644
--- a/content/github/Windows-Optimize-Debloat/index.nl.md
+++ b/content/github/Windows-Optimize-Debloat/index.nl.md
@@ -59,7 +59,7 @@ Als u deze diensten toch wilt gebruiken, zie dan de volgende issue tickets voor
### Geautomatiseerde installatie:
Het script kan vanaf de uitgepakte GitHub-download als volgt worden gestart:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Handmatige installatie:
Indien handmatig gedownload, moet het script worden gestart vanuit een administratieve powershell in de directory die alle bestanden van de [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.pl.md b/content/github/Windows-Optimize-Debloat/index.pl.md
index 394b953160009..86db842a25f57 100644
--- a/content/github/Windows-Optimize-Debloat/index.pl.md
+++ b/content/github/Windows-Optimize-Debloat/index.pl.md
@@ -59,7 +59,7 @@ Jeśli jednak nadal chcesz korzystać z tych usług, zapoznaj się z poniższymi
### Automatyczna instalacja:
Skrypt można uruchomić z wyodrębnionego pliku do pobrania z GitHub w następujący sposób:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Instalacja ręczna:
W przypadku ręcznego pobrania skrypt należy uruchomić z poziomu administracyjnego powershell w katalogu zawierającym wszystkie pliki z pliku [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.ro.md b/content/github/Windows-Optimize-Debloat/index.ro.md
index 5689713444d6b..c4411b16a2f18 100644
--- a/content/github/Windows-Optimize-Debloat/index.ro.md
+++ b/content/github/Windows-Optimize-Debloat/index.ro.md
@@ -59,7 +59,7 @@ Cu toate acestea, dacă doriți totuși să utilizați aceste servicii, consulta
### Automated Install:
Scriptul poate fi lansat din descărcarea extrasă de pe GitHub, astfel:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Instalare manuală:
Dacă este descărcat manual, scriptul trebuie lansat dintr-un powershell administrativ în directorul care conține toate fișierele din fișierul [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.ru.md b/content/github/Windows-Optimize-Debloat/index.ru.md
index df0beed6abc39..3aa8020efa491 100644
--- a/content/github/Windows-Optimize-Debloat/index.ru.md
+++ b/content/github/Windows-Optimize-Debloat/index.ru.md
@@ -59,7 +59,7 @@ Windows 10 и 11 - это инвазивные и небезопасные оп
### Автоматическая установка:
Скрипт может быть запущен из распакованной загрузки с GitHub следующим образом:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
### Установка вручную:
При ручной загрузке скрипт должен быть запущен из административного powershell в директории, содержащей все файлы из файла [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Debloat/index.zh.md b/content/github/Windows-Optimize-Debloat/index.zh.md
index ab0dd0fe0bf8d..5977f4b4a802b 100644
--- a/content/github/Windows-Optimize-Debloat/index.zh.md
+++ b/content/github/Windows-Optimize-Debloat/index.zh.md
@@ -59,7 +59,7 @@ tags: ["视窗-优化-去毛刺", "Windows 优化", "浮动窗口", "加速 Wind
#### 自动安装:
可以像这样从 GitHub 下载的提取文件中启动脚本:
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeanddebloat.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeanddebloat.ps1'|iex
```
#### 手动安装:
如果是手动下载,则必须在包含来自 [GitHub Repository](https://github.com/simeononsecurity/Windows-Optimize-Debloat)
diff --git a/content/github/Windows-Optimize-Harden-Debloat/index.ar.md b/content/github/Windows-Optimize-Harden-Debloat/index.ar.md
index 8f0d9a431a3e2..e63bf912a9ef5 100644
--- a/content/github/Windows-Optimize-Harden-Debloat/index.ar.md
+++ b/content/github/Windows-Optimize-Harden-Debloat/index.ar.md
@@ -175,7 +175,7 @@ tags: ["تحسين Windows", "تصلب النوافذ", "الويندوز الم
### واجهة المستخدم الرسومية - التثبيت الموجه:
قم بتنزيل أحدث إصدار[here](https://github.com/simeononsecurity/Windows-Optimize-Harden-Debloat-GUI/releases/)اختر الخيارات التي تريدها واضغط على تنفيذ. 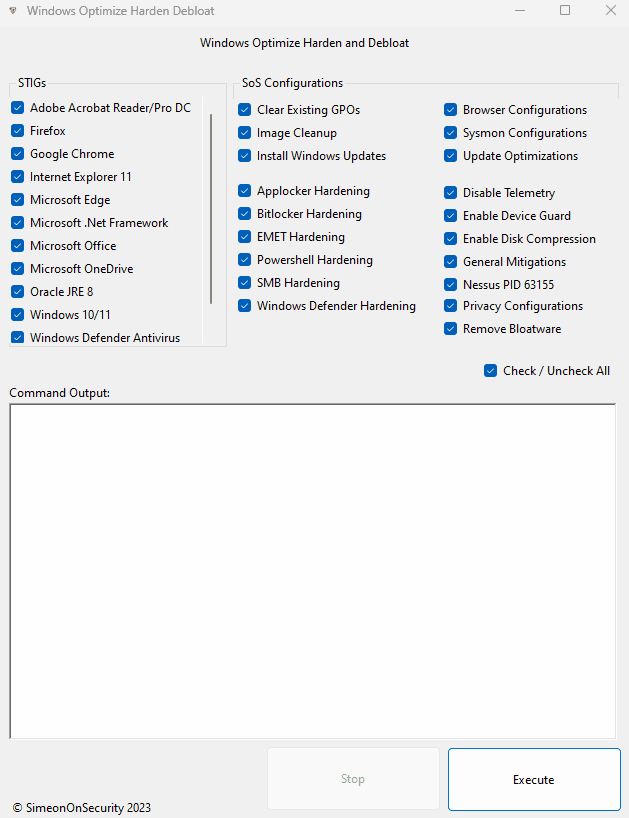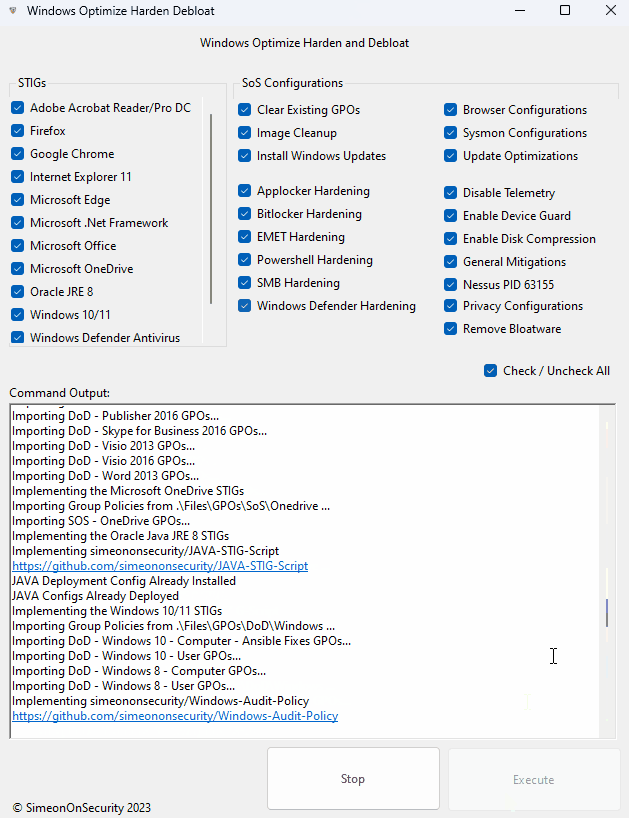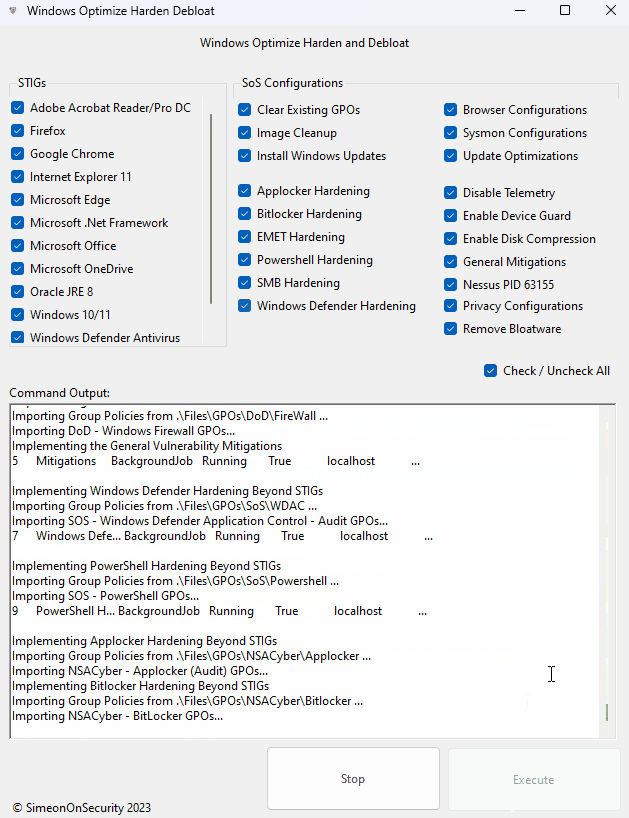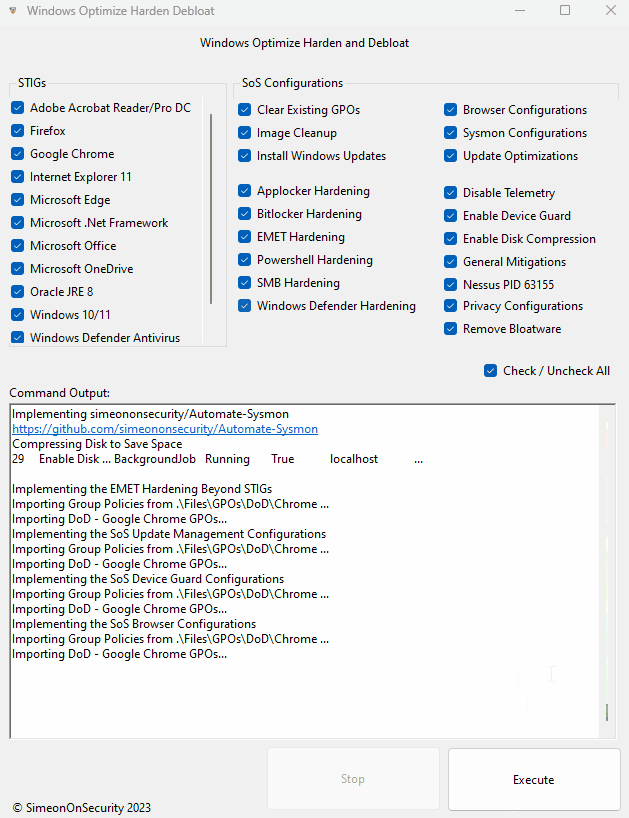 ### التثبيت التلقائي: استخدم هذا المكون من سطر واحد للتنزيل تلقائيًا وفك ضغط جميع الملفات الداعمة وتشغيل أحدث إصدار من البرنامج النصي.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### التثبيت التلقائي: استخدم هذا المكون من سطر واحد للتنزيل تلقائيًا وفك ضغط جميع الملفات الداعمة وتشغيل أحدث إصدار من البرنامج النصي.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
আপনি যে বিকল্পগুলি চান তা চয়ন করুন এবং কার্যকর করুন। <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### স্বয়ংক্রিয় ইনস্টল: স্বয়ংক্রিয়ভাবে ডাউনলোড করতে, সমস্ত সমর্থনকারী ফাইল আনজিপ করতে এবং স্ক্রিপ্টের সর্বশেষ সংস্করণ চালাতে এই ওয়ান-লাইনারটি ব্যবহার করুন।```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### স্বয়ংক্রিয় ইনস্টল: স্বয়ংক্রিয়ভাবে ডাউনলোড করতে, সমস্ত সমর্থনকারী ফাইল আনজিপ করতে এবং স্ক্রিপ্টের সর্বশেষ সংস্করণ চালাতে এই ওয়ান-লাইনারটি ব্যবহার করুন।```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
trieu les opcions que vulgueu i premeu executa. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Instal·lació automàtica: utilitzeu aquesta línia única per descarregar automàticament, descomprimir tots els fitxers compatibles i executar la darrera versió de l'script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Instal·lació automàtica: utilitzeu aquesta línia única per descarregar automàticament, descomprimir tots els fitxers compatibles i executar la darrera versió de l'script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
Wählen Sie die gewünschten Optionen und klicken Sie auf „Ausführen“. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Automatisierte Installation: Verwenden Sie diesen Einzeiler, um alle unterstützenden Dateien automatisch herunterzuladen, zu entpacken und die neueste Version des Skripts auszuführen.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Automatisierte Installation: Verwenden Sie diesen Einzeiler, um alle unterstützenden Dateien automatisch herunterzuladen, zu entpacken und die neueste Version des Skripts auszuführen.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
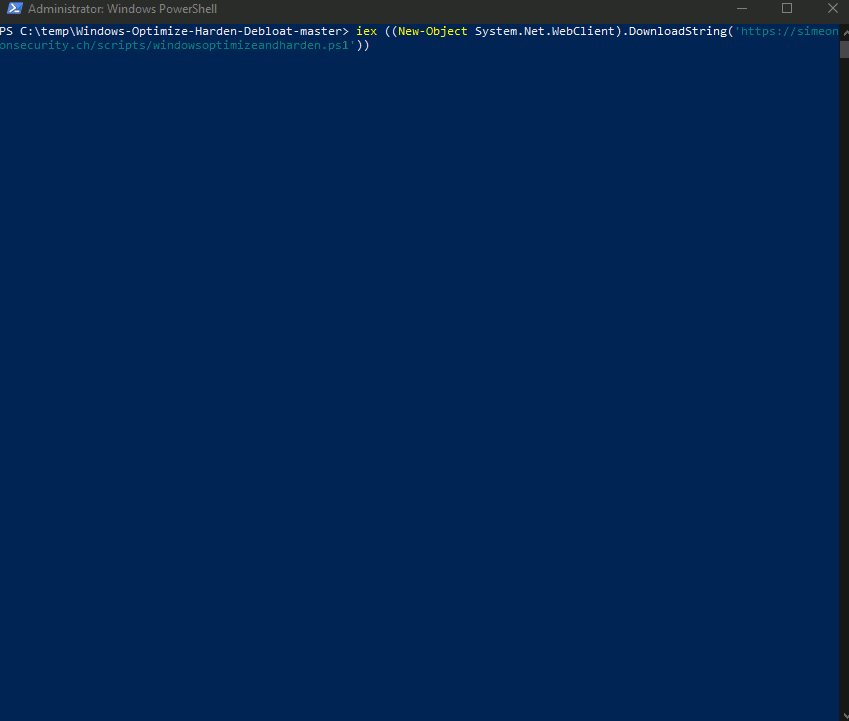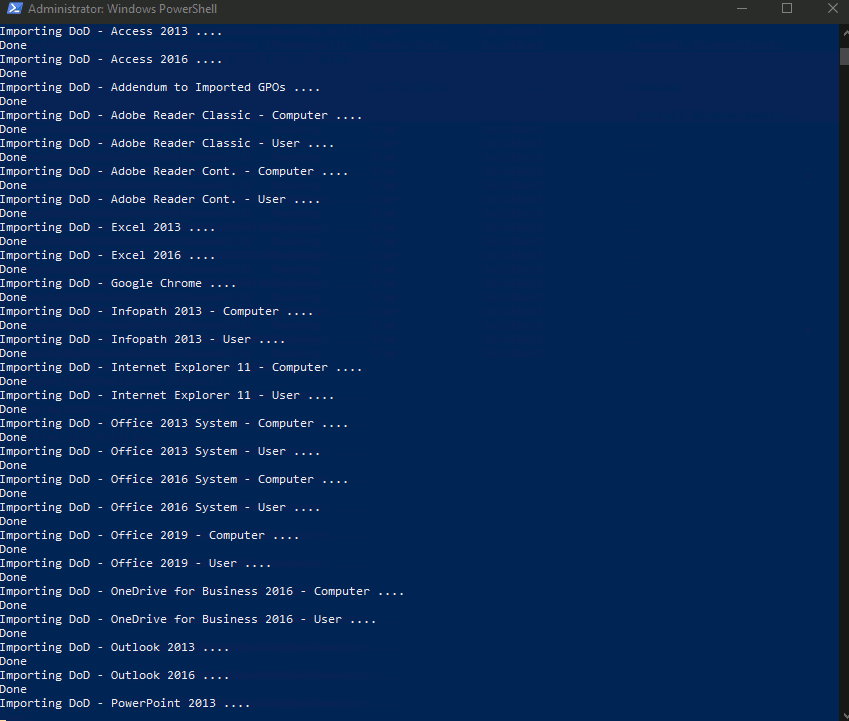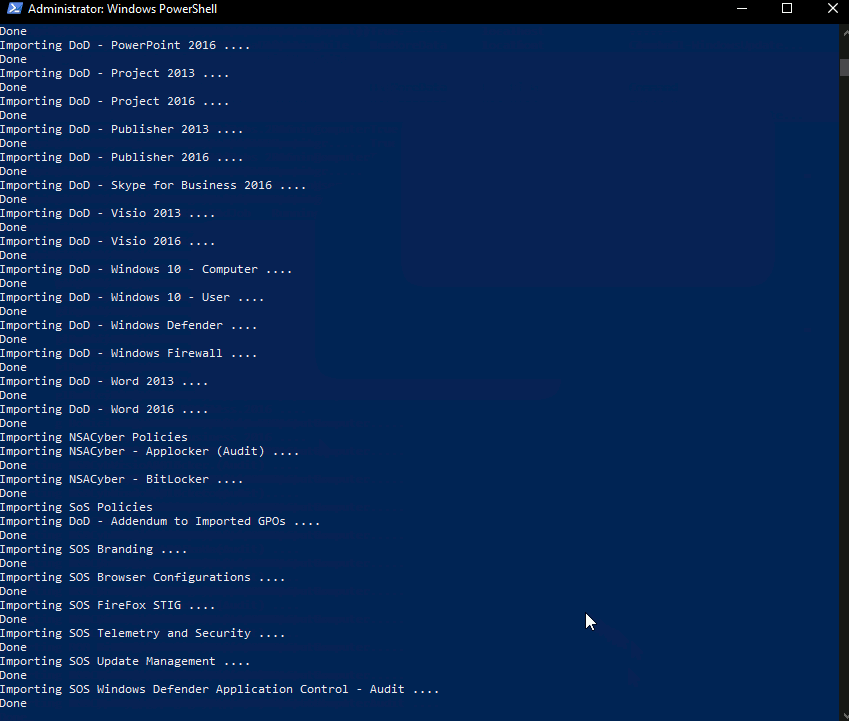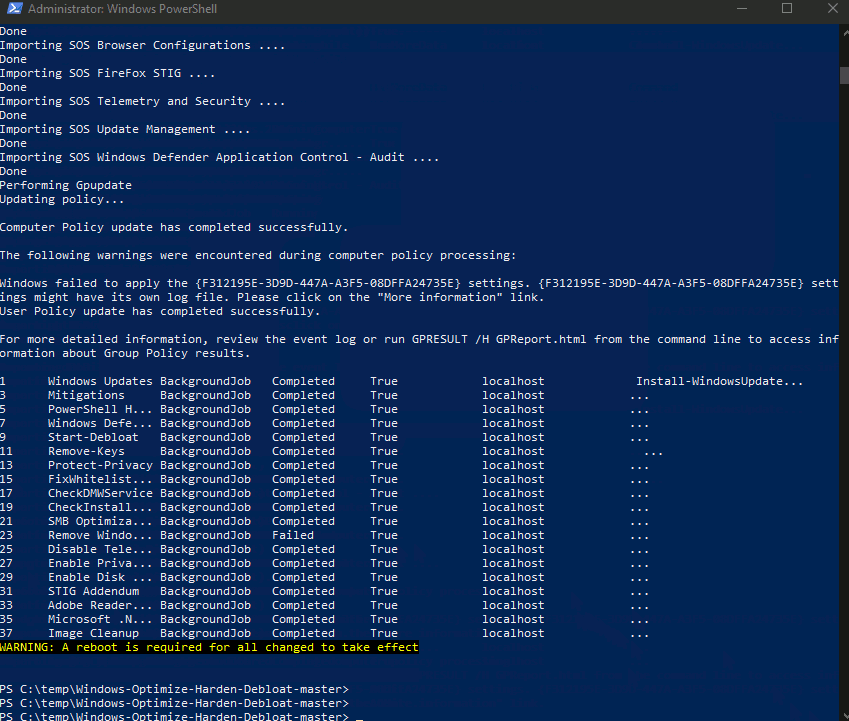 Use this one-liner to automatically download, unzip all supporting files, and run the latest version of the script.
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
Use this one-liner to automatically download, unzip all supporting files, and run the latest version of the script.
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
elige las opciones que quieras y presiona ejecutar. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Instalación automatizada: utilice este resumen para descargar automáticamente, descomprimir todos los archivos compatibles y ejecutar la última versión del script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Instalación automatizada: utilice este resumen para descargar automáticamente, descomprimir todos los archivos compatibles y ejecutar la última versión del script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
choisissez les options que vous voulez et appuyez sur exécuter. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Installation automatisée : utilisez cette ligne pour télécharger automatiquement, décompressez tous les fichiers de prise en charge et exécutez la dernière version du script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Installation automatisée : utilisez cette ligne pour télécharger automatiquement, décompressez tous les fichiers de prise en charge et exécutez la dernière version du script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
 ### स्वचालित स्थापना: स्वचालित रूप से डाउनलोड करने, सभी सहायक फ़ाइलों को अनज़िप करने और स्क्रिप्ट के नवीनतम संस्करण को चलाने के लिए इस एक-लाइनर का उपयोग करें।```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### स्वचालित स्थापना: स्वचालित रूप से डाउनलोड करने, सभी सहायक फ़ाइलों को अनज़िप करने और स्क्रिप्ट के नवीनतम संस्करण को चलाने के लिए इस एक-लाइनर का उपयोग करें।```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
scegli le opzioni che desideri e premi esegui. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Installazione automatica: usa questo one-liner per scaricare automaticamente, decomprimere tutti i file di supporto ed eseguire l'ultima versione dello script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Installazione automatica: usa questo one-liner per scaricare automaticamente, decomprimere tutti i file di supporto ed eseguire l'ultima versione dello script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
必要なオプションを選択し、「実行」をクリックします。 <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### 自動インストール: このワンライナーを使用して、すべてのサポート ファイルを自動的にダウンロード、解凍し、最新バージョンのスクリプトを実行します。```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### 自動インストール: このワンライナーを使用して、すべてのサポート ファイルを自動的にダウンロード、解凍し、最新バージョンのスクリプトを実行します。```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
 Gebruik deze one-liner om automatisch alle ondersteunende bestanden te downloaden, uit te pakken en de laatste versie van het script uit te voeren.
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
Gebruik deze one-liner om automatisch alle ondersteunende bestanden te downloaden, uit te pakken en de laatste versie van het script uit te voeren.
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
 ### ਆਟੋਮੇਟਿਡ ਇੰਸਟੌਲ: ਆਟੋਮੈਟਿਕ ਡਾਊਨਲੋਡ ਕਰਨ, ਸਾਰੀਆਂ ਸਹਾਇਕ ਫਾਈਲਾਂ ਨੂੰ ਅਨਜ਼ਿਪ ਕਰਨ ਅਤੇ ਸਕ੍ਰਿਪਟ ਦੇ ਨਵੀਨਤਮ ਸੰਸਕਰਣ ਨੂੰ ਚਲਾਉਣ ਲਈ ਇਸ ਵਨ-ਲਾਈਨਰ ਦੀ ਵਰਤੋਂ ਕਰੋ।```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### ਆਟੋਮੇਟਿਡ ਇੰਸਟੌਲ: ਆਟੋਮੈਟਿਕ ਡਾਊਨਲੋਡ ਕਰਨ, ਸਾਰੀਆਂ ਸਹਾਇਕ ਫਾਈਲਾਂ ਨੂੰ ਅਨਜ਼ਿਪ ਕਰਨ ਅਤੇ ਸਕ੍ਰਿਪਟ ਦੇ ਨਵੀਨਤਮ ਸੰਸਕਰਣ ਨੂੰ ਚਲਾਉਣ ਲਈ ਇਸ ਵਨ-ਲਾਈਨਰ ਦੀ ਵਰਤੋਂ ਕਰੋ।```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
 .
Użyj tego one-linera, aby automatycznie pobrać, rozpakować wszystkie pliki pomocnicze i uruchomić najnowszą wersję skryptu.
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
.
Użyj tego one-linera, aby automatycznie pobrać, rozpakować wszystkie pliki pomocnicze i uruchomić najnowszą wersję skryptu.
```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
escolha as opções desejadas e clique em executar. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Instalação automatizada: use este one-liner para baixar automaticamente, descompactar todos os arquivos de suporte e executar a versão mais recente do script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Instalação automatizada: use este one-liner para baixar automaticamente, descompactar todos os arquivos de suporte e executar a versão mais recente do script.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
alegeți opțiunile dorite și apăsați pe executare. <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Instalare automată: utilizați această linie pentru a descărca automat, a dezarhiva toate fișierele compatibile și a rula cea mai recentă versiune a scriptului.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Instalare automată: utilizați această linie pentru a descărca automat, a dezarhiva toate fișierele compatibile și a rula cea mai recentă versiune a scriptului.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
выберите нужные параметры и нажмите «Выполнить». <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### Автоматическая установка: Используйте эту однострочную строку для автоматической загрузки, распаковки всех вспомогательных файлов и запуска последней версии скрипта.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### Автоматическая установка: Используйте эту однострочную строку для автоматической загрузки, распаковки всех вспомогательных файлов и запуска последней версии скрипта.```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
选择你想要的选项并点击执行。 <img src=](https://raw.githubusercontent.com/simeononsecurity/Windows-Optimize-Harden-Debloat/master/.github/images/w10automatic.gif) ### 自动安装:使用这一行自动下载、解压缩所有支持文件,并运行最新版本的脚本。```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
### 自动安装:使用这一行自动下载、解压缩所有支持文件,并运行最新版本的脚本。```powershell
-iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex
+iwr -useb 'https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'|iex
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.en.md b/content/github/optimizing-and-hardening-windows10-deployments/index.en.md
index 3c410f1cbd8f8..25aca83c1c8ff 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.en.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.en.md
@@ -14,7 +14,7 @@ tags: ["Windows 10 Security", "Automated Configuration Changes", "PrivacyTools.i
## Introduction:
Windows 10 is an invasive and insecure operating system out of the box.
-Organizations like [PrivacyTools.io](https://PrivacyTools.io), [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended configuration changes to lockdown, harden, and secure the operating system. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many digital and physical attacks on a system. This script aims to automate the configurations recommended by those organizations and [debloat windows 10](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/).
+Organizations like [PrivacyTools.io](https://PrivacyTools.io), [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended configuration changes to lockdown, harden, and secure the operating system. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many digital and physical attacks on a system. This script aims to automate the configurations recommended by those organizations and [debloat windows 10](https://simeononsecurity.com/github/windows-optimize-harden-debloat/).
## Notes:
- This script is designed for operation in primarily **Personal Use** environments. With that in mind, certain enterprise configuration settings are not implemented. This script is not designed to bring a system to 100% compliance. Rather it should be used as a stepping stone to complete most, if not all, the configuration changes that can be scripted while skipping past issues like branding and banners where those should not be implemented even in a hardened personal use environment.
@@ -103,7 +103,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.en.md b/content/github/optimizing-and-hardening-windows10-deployments/index.en.md
index 3c410f1cbd8f8..25aca83c1c8ff 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.en.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.en.md
@@ -14,7 +14,7 @@ tags: ["Windows 10 Security", "Automated Configuration Changes", "PrivacyTools.i
## Introduction:
Windows 10 is an invasive and insecure operating system out of the box.
-Organizations like [PrivacyTools.io](https://PrivacyTools.io), [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended configuration changes to lockdown, harden, and secure the operating system. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many digital and physical attacks on a system. This script aims to automate the configurations recommended by those organizations and [debloat windows 10](https://simeononsecurity.ch/github/windows-optimize-harden-debloat/).
+Organizations like [PrivacyTools.io](https://PrivacyTools.io), [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended configuration changes to lockdown, harden, and secure the operating system. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many digital and physical attacks on a system. This script aims to automate the configurations recommended by those organizations and [debloat windows 10](https://simeononsecurity.com/github/windows-optimize-harden-debloat/).
## Notes:
- This script is designed for operation in primarily **Personal Use** environments. With that in mind, certain enterprise configuration settings are not implemented. This script is not designed to bring a system to 100% compliance. Rather it should be used as a stepping stone to complete most, if not all, the configuration changes that can be scripted while skipping past issues like branding and banners where those should not be implemented even in a hardened personal use environment.
@@ -103,7 +103,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.es.md b/content/github/optimizing-and-hardening-windows10-deployments/index.es.md
index 1535963f0ad9c..8ae15e2f84ec3 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.es.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.es.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.es.md b/content/github/optimizing-and-hardening-windows10-deployments/index.es.md
index 1535963f0ad9c..8ae15e2f84ec3 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.es.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.es.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md b/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md
index 39047eb3514aa..3d9a5e0fde4c5 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md b/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md
index 39047eb3514aa..3d9a5e0fde4c5 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.fr.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.it.md b/content/github/optimizing-and-hardening-windows10-deployments/index.it.md
index ea67ee8272809..c6351ce75799e 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.it.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.it.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installazione automatica:
Lo script può essere lanciato dal download estratto da GitHub in questo modo:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.it.md b/content/github/optimizing-and-hardening-windows10-deployments/index.it.md
index ea67ee8272809..c6351ce75799e 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.it.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.it.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Installazione automatica:
Lo script può essere lanciato dal download estratto da GitHub in questo modo:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 .
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md b/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md
index e0961ec28baeb..94e0185655ede 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### 自動インストール:
スクリプトは、GitHubでダウンロードしたものを次のように起動することができます:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
.
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md b/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md
index e0961ec28baeb..94e0185655ede 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.ja.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### 自動インストール:
スクリプトは、GitHubでダウンロードしたものを次のように起動することができます:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 。
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md b/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md
index ef567577e3621..995f60e7dfaad 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Geautomatiseerde installatie:
Het script kan als volgt worden gestart vanaf de uitgepakte GitHub-download:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
。
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md b/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md
index ef567577e3621..995f60e7dfaad 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.nl.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Geautomatiseerde installatie:
Het script kan als volgt worden gestart vanaf de uitgepakte GitHub-download:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md b/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md
index a554cf022c9e5..85492a150f17f 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automatyczna instalacja:
Skrypt można uruchomić z wyodrębnionego pliku do pobrania z GitHub w następujący sposób:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md b/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md
index a554cf022c9e5..85492a150f17f 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.pl.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automatyczna instalacja:
Skrypt można uruchomić z wyodrębnionego pliku do pobrania z GitHub w następujący sposób:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 .
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md b/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md
index 68b9aedaf430e..9aeac7a226afa 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
Scriptul poate fi lansat din descărcarea extrasă de pe GitHub astfel:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
.
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md b/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md
index 68b9aedaf430e..9aeac7a226afa 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.ro.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Automated Install:
Scriptul poate fi lansat din descărcarea extrasă de pe GitHub astfel:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md b/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md
index b5fa8724a40b4..488c5557a2500 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Автоматическая установка:
Скрипт может быть запущен из распакованной загрузки с GitHub следующим образом:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md b/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md
index b5fa8724a40b4..488c5557a2500 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.ru.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
### Автоматическая установка:
Скрипт может быть запущен из распакованной загрузки с GitHub следующим образом:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md b/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md
index eb507210a4e88..3e66348c9db11 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
#### 自动安装:
可以像这样从 GitHub 下载的提取文件中启动脚本:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
diff --git a/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md b/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md
index eb507210a4e88..3e66348c9db11 100644
--- a/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md
+++ b/content/github/optimizing-and-hardening-windows10-deployments/index.zh.md
@@ -99,7 +99,7 @@ Get-ChildItem -Recurse *.ps1 | Unblock-File
#### 自动安装:
可以像这样从 GitHub 下载的提取文件中启动脚本:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/windowsoptimizeandharden.ps1'))
```
 diff --git a/content/github/shodan-api-ansible-automation-guide/index.en.md b/content/github/shodan-api-ansible-automation-guide/index.en.md
index fccf4e17a4f7a..2560d8082781c 100644
--- a/content/github/shodan-api-ansible-automation-guide/index.en.md
+++ b/content/github/shodan-api-ansible-automation-guide/index.en.md
@@ -59,7 +59,7 @@ Contributions to this collection are welcome! If you have improvements or new mo
This project is licensed under the MIT License. See the [`LICENSE`](https://github.com/simeononsecurity/ansible_shodan/blob/main/LICENSE) file for details.
### Author
-This Ansible Shodan Modules collection is authored by [SimeonOnSecurity](https://simeononsecurity.ch/).
+This Ansible Shodan Modules collection is authored by [SimeonOnSecurity](https://simeononsecurity.com/).
### Acknowledgments
Special thanks to the Shodan API for providing the capabilities to interact with their service using Ansible.
\ No newline at end of file
diff --git a/content/github/stiging-standalone-windows-servers/index.bn.md b/content/github/stiging-standalone-windows-servers/index.bn.md
index 0750655ec4765..2ec5f5c5dbec6 100644
--- a/content/github/stiging-standalone-windows-servers/index.bn.md
+++ b/content/github/stiging-standalone-windows-servers/index.bn.md
@@ -84,7 +84,7 @@ Windows 10 বাক্সের বাইরে অনিরাপদ অপা
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ca.md b/content/github/stiging-standalone-windows-servers/index.ca.md
index c4aeb39faeb5b..cb5907ffeedd1 100644
--- a/content/github/stiging-standalone-windows-servers/index.ca.md
+++ b/content/github/stiging-standalone-windows-servers/index.ca.md
@@ -84,7 +84,7 @@ Els sistemes autònoms són alguns dels sistemes més difícils i molestos de pr
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.de.md b/content/github/stiging-standalone-windows-servers/index.de.md
index 9babff3c20e81..3217c3864aef2 100644
--- a/content/github/stiging-standalone-windows-servers/index.de.md
+++ b/content/github/stiging-standalone-windows-servers/index.de.md
@@ -84,7 +84,7 @@ Eigenständige Systeme gehören zu den am schwierigsten und lästigsten zu siche
### Automatisierte Installation:
Das Skript kann wie folgt aus dem extrahierten GitHub-Download gestartet werden:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manuelle Installation:
diff --git a/content/github/stiging-standalone-windows-servers/index.en.md b/content/github/stiging-standalone-windows-servers/index.en.md
index 31fe408cb04ef..c3b9281eb88b5 100644
--- a/content/github/stiging-standalone-windows-servers/index.en.md
+++ b/content/github/stiging-standalone-windows-servers/index.en.md
@@ -22,7 +22,7 @@ We now offer a playbook collection for this script. Please see the following:
Windows 10 is insecure operating system out of the box and requires many changes to insure [FISMA](https://www.cisa.gov/federal-information-security-modernization-act) compliance.
Organizations like [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended and required configuration changes to lockdown, harden, and secure the operating system and ensure government compliance. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many physical attacks on a system.
-Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.ch/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
+Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.com/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
## Notes:
@@ -89,7 +89,7 @@ Standalone systems are some of the most difficult and annoying systems to secure
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.es.md b/content/github/stiging-standalone-windows-servers/index.es.md
index 83003a0215e36..cc3f4f8426ce2 100644
--- a/content/github/stiging-standalone-windows-servers/index.es.md
+++ b/content/github/stiging-standalone-windows-servers/index.es.md
@@ -84,7 +84,7 @@ Los sistemas autónomos son algunos de los más difíciles y molestos de protege
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Instalación manual:
diff --git a/content/github/stiging-standalone-windows-servers/index.fr.md b/content/github/stiging-standalone-windows-servers/index.fr.md
index 13c0104fded1d..993d37a471496 100644
--- a/content/github/stiging-standalone-windows-servers/index.fr.md
+++ b/content/github/stiging-standalone-windows-servers/index.fr.md
@@ -84,7 +84,7 @@ Les systèmes autonomes sont parmi les plus difficiles et les plus ennuyeux à s
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Installation manuelle :
diff --git a/content/github/stiging-standalone-windows-servers/index.it.md b/content/github/stiging-standalone-windows-servers/index.it.md
index 5c2ca36d028c8..d026047751d22 100644
--- a/content/github/stiging-standalone-windows-servers/index.it.md
+++ b/content/github/stiging-standalone-windows-servers/index.it.md
@@ -84,7 +84,7 @@ I sistemi autonomi sono alcuni dei sistemi più difficili e fastidiosi da proteg
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ja.md b/content/github/stiging-standalone-windows-servers/index.ja.md
index 50f60c7029752..75fadacd8fa6c 100644
--- a/content/github/stiging-standalone-windows-servers/index.ja.md
+++ b/content/github/stiging-standalone-windows-servers/index.ja.md
@@ -84,7 +84,7 @@ Windows 10 は、そのままでは安全ではないオペレーティング
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.nl.md b/content/github/stiging-standalone-windows-servers/index.nl.md
index 27776c33eaae3..f6dbaa245528c 100644
--- a/content/github/stiging-standalone-windows-servers/index.nl.md
+++ b/content/github/stiging-standalone-windows-servers/index.nl.md
@@ -84,7 +84,7 @@ Standalone systemen behoren tot de moeilijkste en vervelendste systemen om te be
### Geautomatiseerde installatie:
Het script kan vanaf de uitgepakte GitHub-download als volgt worden gestart:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Handmatige installatie:
diff --git a/content/github/stiging-standalone-windows-servers/index.pa.md b/content/github/stiging-standalone-windows-servers/index.pa.md
index 026e074385c7b..085d0b2b00dfe 100644
--- a/content/github/stiging-standalone-windows-servers/index.pa.md
+++ b/content/github/stiging-standalone-windows-servers/index.pa.md
@@ -84,7 +84,7 @@ Windows 10 ਬਾਕਸ ਤੋਂ ਬਾਹਰ ਅਸੁਰੱਖਿਅਤ ਓ
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.pl.md b/content/github/stiging-standalone-windows-servers/index.pl.md
index d4edc67222118..e3401829110d1 100644
--- a/content/github/stiging-standalone-windows-servers/index.pl.md
+++ b/content/github/stiging-standalone-windows-servers/index.pl.md
@@ -84,7 +84,7 @@ Systemy autonomiczne są jednymi z najtrudniejszych i najbardziej irytujących s
### Automated Install:
Skrypt można uruchomić z rozpakowanego pliku do pobrania z GitHuba w ten sposób:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.pt.md b/content/github/stiging-standalone-windows-servers/index.pt.md
index dafbc6c1fd066..27bc75bcd2593 100644
--- a/content/github/stiging-standalone-windows-servers/index.pt.md
+++ b/content/github/stiging-standalone-windows-servers/index.pt.md
@@ -84,7 +84,7 @@ Os sistemas autônomos são alguns dos sistemas mais difíceis e irritantes de p
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ro.md b/content/github/stiging-standalone-windows-servers/index.ro.md
index bb479b7046b16..4b5364fc3e2da 100644
--- a/content/github/stiging-standalone-windows-servers/index.ro.md
+++ b/content/github/stiging-standalone-windows-servers/index.ro.md
@@ -84,7 +84,7 @@ Sistemele de sine stătătoare sunt unele dintre cele mai dificil și enervant s
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ru.md b/content/github/stiging-standalone-windows-servers/index.ru.md
index f7923bbf4807c..d9813b1b1ca88 100644
--- a/content/github/stiging-standalone-windows-servers/index.ru.md
+++ b/content/github/stiging-standalone-windows-servers/index.ru.md
@@ -84,7 +84,7 @@ Windows 10 — небезопасная операционная система
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.zh.md b/content/github/stiging-standalone-windows-servers/index.zh.md
index 15003c9b12a3c..547a2aa259afd 100644
--- a/content/github/stiging-standalone-windows-servers/index.zh.md
+++ b/content/github/stiging-standalone-windows-servers/index.zh.md
@@ -84,7 +84,7 @@ Windows 10 是开箱即用的不安全操作系统,需要进行许多更改才
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-systems/index.en.md b/content/github/stiging-standalone-windows-systems/index.en.md
index a9776478275a4..d08a55a077f61 100644
--- a/content/github/stiging-standalone-windows-systems/index.en.md
+++ b/content/github/stiging-standalone-windows-systems/index.en.md
@@ -17,7 +17,7 @@ tags: ["Automation", "Windows STIG Compliance", "Powershell Scripting", "Windows
Windows 10 is insecure operating system out of the box and requires many changes to insure [FISMA](https://www.cisa.gov/federal-information-security-modernization-act) compliance.
Organizations like [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended and required configuration changes to lockdown, harden, and secure the operating system and ensure government compliance. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many physical attacks on a system.
-Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.ch/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
+Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.com/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
## Notes:
diff --git a/content/guest-posts/index.de.md b/content/guest-posts/index.de.md
index ec77fb1f5f0a0..475cec6ddbaf6 100644
--- a/content/guest-posts/index.de.md
+++ b/content/guest-posts/index.de.md
@@ -11,11 +11,11 @@ coverCaption: "Teilen Sie Ihr Fachwissen und Ihre Erkenntnisse mit unserer Commu
Vielen Dank für Ihr Interesse, einen Beitrag zu unserer Website zu leisten! Wir freuen uns über Beiträge für Gastblogs, die zu unserem inhaltlichen Schwerpunkt passen. Um einen Artikel einzureichen, folgen Sie bitte diesen Schritten:
-1. Kontaktieren Sie uns über das Webformular unter [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) um Ihr Interesse an Gastbeiträgen zu bekunden.
+1. Kontaktieren Sie uns über das Webformular unter [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) um Ihr Interesse an Gastbeiträgen zu bekunden.
2. Bereiten Sie Ihren Artikel entweder im Markdown- (md) oder HTML-Format vor.
-3. Reichen Sie einen Pull-Request auf unserem GitHub-Repository ein unter [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Reichen Sie einen Pull-Request auf unserem GitHub-Repository ein unter [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Vergewissern Sie sich, dass Ihr Artikel gültige Frontmatter (Metadaten) mit allen erforderlichen Variablen enthält, wie im folgenden Beispiel gezeigt:
@@ -122,7 +122,7 @@ Gast-Blogging ist eine für beide Seiten vorteilhafte Vereinbarung, bei der Auto
- Wir danken Ihnen für Ihr Verständnis und Ihre Mitarbeit bei der Einhaltung dieser Richtlinien, um die Qualität und Relevanz der Inhalte auf SimeonOnSecurity zu erhalten.
-Wir freuen uns auf Ihre wertvollen Beiträge und darauf, Sie dabei zu unterstützen, ein größeres Publikum mit Ihren Erkenntnissen zu erreichen. Sollten Sie weitere Fragen oder Unklarheiten haben, zögern Sie bitte nicht, uns über das Kontaktformular zu kontaktieren. [webform](https://simeononsecurity.ch/contactus/)
+Wir freuen uns auf Ihre wertvollen Beiträge und darauf, Sie dabei zu unterstützen, ein größeres Publikum mit Ihren Erkenntnissen zu erreichen. Sollten Sie weitere Fragen oder Unklarheiten haben, zögern Sie bitte nicht, uns über das Kontaktformular zu kontaktieren. [webform](https://simeononsecurity.com/contactus/)
***Glückliches Schreiben!***
diff --git a/content/guest-posts/index.en.md b/content/guest-posts/index.en.md
index dafcecfa5a4c0..fec7d77fa59f7 100644
--- a/content/guest-posts/index.en.md
+++ b/content/guest-posts/index.en.md
@@ -11,11 +11,11 @@ coverCaption: "Share your expertise and insights with our community through gues
Thank you for your interest in contributing to our website! We welcome guest blog submissions that align with our content focus. To submit an article for consideration, please follow these steps:
-1. Contact us through the webform at [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) to express your interest in guest blogging.
+1. Contact us through the webform at [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) to express your interest in guest blogging.
2. Prepare your article in either Markdown (md) or HTML format.
-3. Submit a pull request on our GitHub repository at [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors).
+3. Submit a pull request on our GitHub repository at [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors).
4. Ensure your article includes valid frontmatter (metadata) with all the required variables, as shown in the example below:
@@ -122,7 +122,7 @@ Guest blogging is a mutually beneficial arrangement where writers have the oppor
- We appreciate your understanding and cooperation in following these guidelines to maintain the quality and relevance of content on SimeonOnSecurity.
-We look forward to receiving your valuable contributions and helping you reach a wider audience with your insights. If you have any further questions or clarifications, please don't hesitate to contact us through the [webform](https://simeononsecurity.ch/contactus/).
+We look forward to receiving your valuable contributions and helping you reach a wider audience with your insights. If you have any further questions or clarifications, please don't hesitate to contact us through the [webform](https://simeononsecurity.com/contactus/).
***Happy writing!***
diff --git a/content/guest-posts/index.es.md b/content/guest-posts/index.es.md
index ba60725d8a701..7e844f782dd67 100644
--- a/content/guest-posts/index.es.md
+++ b/content/guest-posts/index.es.md
@@ -11,11 +11,11 @@ coverCaption: "Comparta su experiencia y conocimientos con nuestra comunidad a t
Gracias por su interés en contribuir a nuestro sitio web. Recibimos con agrado artículos de blogs invitados que se ajusten a nuestro enfoque de contenidos. Para enviar un artículo, siga estos pasos:
-1. Póngase en contacto con nosotros a través del formulario web en [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) para expresar su interés en participar como blogger invitado.
+1. Póngase en contacto con nosotros a través del formulario web en [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) para expresar su interés en participar como blogger invitado.
2. Prepare su artículo en formato Markdown (md) o HTML.
-3. Envíe una solicitud de extracción (pull request) a nuestro repositorio de GitHub en [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Envíe una solicitud de extracción (pull request) a nuestro repositorio de GitHub en [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Asegúrese de que su artículo incluye un frontmatter (metadatos) válido con todas las variables requeridas, como se muestra en el siguiente ejemplo:
@@ -122,7 +122,7 @@ Se trata de un acuerdo mutuamente beneficioso en el que los autores tienen la op
- Agradecemos su comprensión y cooperación en el seguimiento de estas directrices para mantener la calidad y relevancia de los contenidos en SimeonOnSecurity.
-Esperamos recibir sus valiosas contribuciones y ayudarle a llegar a un público más amplio con sus ideas. Si tiene alguna pregunta o aclaración, no dude en ponerse en contacto con nosotros a través de la dirección de correo electrónico [webform](https://simeononsecurity.ch/contactus/)
+Esperamos recibir sus valiosas contribuciones y ayudarle a llegar a un público más amplio con sus ideas. Si tiene alguna pregunta o aclaración, no dude en ponerse en contacto con nosotros a través de la dirección de correo electrónico [webform](https://simeononsecurity.com/contactus/)
***¡Feliz escritura!
diff --git a/content/guest-posts/index.fr.md b/content/guest-posts/index.fr.md
index c709ac5f62963..f7a34bb454580 100644
--- a/content/guest-posts/index.fr.md
+++ b/content/guest-posts/index.fr.md
@@ -11,11 +11,11 @@ coverCaption: "Partagez votre expertise et vos connaissances avec notre communau
Nous vous remercions de l'intérêt que vous portez à notre site web ! Nous accueillons volontiers les propositions de blogs d'invités qui correspondent à notre objectif de contenu. Pour soumettre un article, veuillez suivre les étapes suivantes :
-1. Contactez-nous à l'aide du formulaire Web à l'adresse suivante [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) pour exprimer votre intérêt pour le guest blogging.
+1. Contactez-nous à l'aide du formulaire Web à l'adresse suivante [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) pour exprimer votre intérêt pour le guest blogging.
2. Préparez votre article au format Markdown (md) ou HTML.
-3. Soumettez une demande d'extraction sur notre dépôt GitHub à l'adresse suivante [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Soumettez une demande d'extraction sur notre dépôt GitHub à l'adresse suivante [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Veillez à ce que votre article contienne des métadonnées valides avec toutes les variables requises, comme le montre l'exemple ci-dessous :
@@ -122,7 +122,7 @@ Le guest blogging est un arrangement mutuellement bénéfique dans le cadre duqu
- Nous vous remercions de votre compréhension et de votre coopération en suivant ces directives afin de maintenir la qualité et la pertinence du contenu de SimeonOnSecurity.
-Nous nous réjouissons de recevoir vos précieuses contributions et de vous aider à atteindre un public plus large grâce à vos idées. Si vous avez d'autres questions ou des éclaircissements, n'hésitez pas à nous contacter par l'intermédiaire de l'adresse suivante [webform](https://simeononsecurity.ch/contactus/)
+Nous nous réjouissons de recevoir vos précieuses contributions et de vous aider à atteindre un public plus large grâce à vos idées. Si vous avez d'autres questions ou des éclaircissements, n'hésitez pas à nous contacter par l'intermédiaire de l'adresse suivante [webform](https://simeononsecurity.com/contactus/)
***Heureuse écriture!***
diff --git a/content/guest-posts/index.it.md b/content/guest-posts/index.it.md
index b5601a87aa1ac..00f8aed6eee48 100644
--- a/content/guest-posts/index.it.md
+++ b/content/guest-posts/index.it.md
@@ -11,11 +11,11 @@ coverCaption: "Condividete la vostra esperienza e le vostre intuizioni con la no
Grazie per il vostro interesse a contribuire al nostro sito web! Siamo lieti di ricevere articoli per blog ospiti che siano in linea con i nostri contenuti. Per inviare un articolo da prendere in considerazione, seguite i seguenti passaggi:
-1. Contattateci attraverso il modulo web all'indirizzo [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) per esprimere il vostro interesse per il guest blogging.
+1. Contattateci attraverso il modulo web all'indirizzo [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) per esprimere il vostro interesse per il guest blogging.
2. Preparate il vostro articolo in formato Markdown (md) o HTML.
-3. Inviate una richiesta di pull sul nostro repository GitHub all'indirizzo [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Inviate una richiesta di pull sul nostro repository GitHub all'indirizzo [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Assicuratevi che l'articolo includa un frontmatter (metadati) valido con tutte le variabili richieste, come mostrato nell'esempio seguente:
@@ -122,7 +122,7 @@ Il guest blogging è un accordo reciprocamente vantaggioso in cui gli scrittori
- Apprezziamo la vostra comprensione e collaborazione nel seguire queste linee guida per mantenere la qualità e la rilevanza dei contenuti di SimeonOnSecurity.
-Saremo lieti di ricevere i vostri preziosi contributi e di aiutarvi a raggiungere un pubblico più ampio con le vostre intuizioni. In caso di ulteriori domande o chiarimenti, non esitate a contattarci attraverso il sito [webform](https://simeononsecurity.ch/contactus/)
+Saremo lieti di ricevere i vostri preziosi contributi e di aiutarvi a raggiungere un pubblico più ampio con le vostre intuizioni. In caso di ulteriori domande o chiarimenti, non esitate a contattarci attraverso il sito [webform](https://simeononsecurity.com/contactus/)
***Felice scrittura! ***
diff --git a/content/guest-posts/index.ja.md b/content/guest-posts/index.ja.md
index 0306a01ce55b4..4791c66345904 100644
--- a/content/guest-posts/index.ja.md
+++ b/content/guest-posts/index.ja.md
@@ -11,11 +11,11 @@ coverCaption: "ゲストブログを通じて、あなたの専門知識や見
当サイトへの寄稿にご関心をお寄せいただき、ありがとうございます!私たちは、私たちのコンテンツの焦点に沿ったゲストブログの投稿を歓迎します。記事を投稿するには、以下の手順に従ってください:
-1.以下のウェブフォームからご連絡ください。 [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/)をクリックして、ゲスト・ブログへの興味を表明してください。
+1.以下のウェブフォームからご連絡ください。 [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/)をクリックして、ゲスト・ブログへの興味を表明してください。
2.記事をMarkdown (md)またはHTML形式で準備する。
-3.以下のGitHubリポジトリにプルリクエストを提出する。 [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3.以下のGitHubリポジトリにプルリクエストを提出する。 [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4.以下の例に示すように、あなたの記事がすべての必要な変数を含む有効なフロントマター(メタデータ)を含んでいることを確認してください:
@@ -122,7 +122,7 @@ SimeonOnSecurityでは、ゲストブログは主にネットワーキングと
- SimeonOnSecurityのコンテンツの質と関連性を維持するため、これらのガイドラインに従うことへのご理解とご協力をお願いいたします。
-皆様の貴重なご投稿をお待ちしております。ご質問やご不明な点がございましたら、ご遠慮なく下記までご連絡ください。 [webform](https://simeononsecurity.ch/contactus/)
+皆様の貴重なご投稿をお待ちしております。ご質問やご不明な点がございましたら、ご遠慮なく下記までご連絡ください。 [webform](https://simeononsecurity.com/contactus/)
***ハッピー・ライティング!***
diff --git a/content/guest-posts/index.nl.md b/content/guest-posts/index.nl.md
index fb576c94cc907..caa9fe72d0b27 100644
--- a/content/guest-posts/index.nl.md
+++ b/content/guest-posts/index.nl.md
@@ -11,11 +11,11 @@ coverCaption: "Deel je expertise en inzichten met onze community door te gastblo
Bedankt voor je interesse om bij te dragen aan onze website! We verwelkomen gastblogs die aansluiten bij onze inhoudelijke focus. Volg deze stappen om een artikel in te dienen:
-1. Neem contact met ons op via het webformulier op [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) om je interesse in gastbloggen te tonen.
+1. Neem contact met ons op via het webformulier op [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) om je interesse in gastbloggen te tonen.
2. Bereid je artikel voor in Markdown (md) of HTML-formaat.
-3. Dien een pull request in op onze GitHub repository op [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Dien een pull request in op onze GitHub repository op [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Zorg ervoor dat je artikel geldige frontmatter (metadata) bevat met alle vereiste variabelen, zoals in het onderstaande voorbeeld:
@@ -122,7 +122,7 @@ Gastbloggen is een wederzijds voordelige regeling waarbij schrijvers de kans kri
- Wij waarderen uw begrip en medewerking bij het volgen van deze richtlijnen om de kwaliteit en relevantie van de inhoud op SimeonOnSecurity te behouden.
-We kijken ernaar uit om uw waardevolle bijdragen te ontvangen en u te helpen een breder publiek te bereiken met uw inzichten. Als u nog vragen of verduidelijkingen heeft, aarzel dan niet om contact met ons op te nemen via de [webform](https://simeononsecurity.ch/contactus/)
+We kijken ernaar uit om uw waardevolle bijdragen te ontvangen en u te helpen een breder publiek te bereiken met uw inzichten. Als u nog vragen of verduidelijkingen heeft, aarzel dan niet om contact met ons op te nemen via de [webform](https://simeononsecurity.com/contactus/)
***Veel schrijfplezier!
diff --git a/content/guest-posts/index.pl.md b/content/guest-posts/index.pl.md
index 89eac52d942df..57ed61a9d4747 100644
--- a/content/guest-posts/index.pl.md
+++ b/content/guest-posts/index.pl.md
@@ -11,11 +11,11 @@ coverCaption: "Podziel się swoją wiedzą i spostrzeżeniami z naszą społeczn
Dziękujemy za zainteresowanie współtworzeniem naszej witryny! Czekamy na zgłoszenia gościnnych blogów, które są zgodne z naszą treścią. Aby przesłać artykuł do rozpatrzenia, wykonaj następujące kroki:
-1. Skontaktuj się z nami za pośrednictwem formularza internetowego pod adresem [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) aby wyrazić zainteresowanie gościnnym blogowaniem.
+1. Skontaktuj się z nami za pośrednictwem formularza internetowego pod adresem [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) aby wyrazić zainteresowanie gościnnym blogowaniem.
2. Przygotuj artykuł w formacie Markdown (md) lub HTML.
-3. Prześlij pull request do naszego repozytorium GitHub pod adresem [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Prześlij pull request do naszego repozytorium GitHub pod adresem [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Upewnij się, że artykuł zawiera prawidłowy frontmatter (metadane) ze wszystkimi wymaganymi zmiennymi, jak pokazano w poniższym przykładzie:
@@ -122,7 +122,7 @@ Blogowanie gościnne jest obustronnie korzystnym porozumieniem, w którym autorz
- Dziękujemy za zrozumienie i współpracę w przestrzeganiu tych wytycznych w celu utrzymania jakości i trafności treści na SimeonOnSecurity.
-Z niecierpliwością czekamy na Twój cenny wkład i pomoc w dotarciu z Twoimi spostrzeżeniami do szerszego grona odbiorców. W razie jakichkolwiek dalszych pytań lub wyjaśnień, prosimy o kontakt za pośrednictwem strony internetowej [webform](https://simeononsecurity.ch/contactus/)
+Z niecierpliwością czekamy na Twój cenny wkład i pomoc w dotarciu z Twoimi spostrzeżeniami do szerszego grona odbiorców. W razie jakichkolwiek dalszych pytań lub wyjaśnień, prosimy o kontakt za pośrednictwem strony internetowej [webform](https://simeononsecurity.com/contactus/)
***Happy writing!***
diff --git a/content/guest-posts/index.ro.md b/content/guest-posts/index.ro.md
index 93d1a2b386a9a..5b4545374b684 100644
--- a/content/guest-posts/index.ro.md
+++ b/content/guest-posts/index.ro.md
@@ -11,11 +11,11 @@ coverCaption: "Împărtășiți expertiza și cunoștințele dvs. cu comunitatea
Vă mulțumim pentru interesul dumneavoastră de a contribui la site-ul nostru! Primim cu plăcere propuneri de bloguri invitate care se aliniază cu obiectivul nostru de conținut. Pentru a trimite un articol pentru examinare, vă rugăm să urmați acești pași:
-1. Contactați-ne prin intermediul formularului web de la adresa [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) pentru a vă exprima interesul de a fi guest blogging.
+1. Contactați-ne prin intermediul formularului web de la adresa [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) pentru a vă exprima interesul de a fi guest blogging.
2. Pregătiți articolul în format Markdown (md) sau HTML.
-3. Trimiteți o cerere de tip pull request pe depozitul nostru GitHub la adresa [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Trimiteți o cerere de tip pull request pe depozitul nostru GitHub la adresa [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Asigurați-vă că articolul dvs. include un frontmatter (metadate) valid, cu toate variabilele necesare, așa cum se arată în exemplul de mai jos:
@@ -122,7 +122,7 @@ Blogul invitat este un aranjament reciproc avantajos în care scriitorii au ocaz
- Apreciem înțelegerea și cooperarea dvs. în respectarea acestor linii directoare pentru a menține calitatea și relevanța conținutului pe SimeonOnSecurity.
-Așteptăm cu nerăbdare să primim contribuțiile dvs. valoroase și să vă ajutăm să ajungeți la un public mai larg cu cunoștințele dvs. Dacă aveți întrebări sau clarificări suplimentare, nu ezitați să ne contactați prin intermediul [webform](https://simeononsecurity.ch/contactus/)
+Așteptăm cu nerăbdare să primim contribuțiile dvs. valoroase și să vă ajutăm să ajungeți la un public mai larg cu cunoștințele dvs. Dacă aveți întrebări sau clarificări suplimentare, nu ezitați să ne contactați prin intermediul [webform](https://simeononsecurity.com/contactus/)
***Scriere fericită!
diff --git a/content/guest-posts/index.ru.md b/content/guest-posts/index.ru.md
index 143ef6adb6bbe..84ad0b3c9d6bb 100644
--- a/content/guest-posts/index.ru.md
+++ b/content/guest-posts/index.ru.md
@@ -11,11 +11,11 @@ coverCaption: "Делитесь своим опытом и знаниями с
Благодарим Вас за интерес к участию в работе нашего сайта! Мы приветствуем публикацию статей в гостевых блогах, которые соответствуют нашей тематике. Чтобы отправить статью на рассмотрение, пожалуйста, выполните следующие действия:
-1. Свяжитесь с нами через веб-форму по адресу [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) чтобы выразить свою заинтересованность в ведении гостевого блога.
+1. Свяжитесь с нами через веб-форму по адресу [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) чтобы выразить свою заинтересованность в ведении гостевого блога.
2. Подготовьте статью в формате Markdown (md) или HTML.
-3. Отправьте запрос на притяжение в наш репозиторий GitHub по адресу [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Отправьте запрос на притяжение в наш репозиторий GitHub по адресу [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Убедитесь, что статья содержит корректный frontmatter (метаданные) со всеми необходимыми переменными, как показано в примере ниже:
@@ -122,7 +122,7 @@ coverCaption: "Caption for your cover image."
- Мы благодарим вас за понимание и сотрудничество в соблюдении этих правил для поддержания качества и актуальности контента на сайте SimeonOnSecurity.
-Мы с нетерпением ждем ваших ценных материалов и будем рады помочь вам привлечь внимание широкой аудитории. Если у вас возникнут дополнительные вопросы или уточнения, пожалуйста, обращайтесь к нам по адресу [webform](https://simeononsecurity.ch/contactus/)
+Мы с нетерпением ждем ваших ценных материалов и будем рады помочь вам привлечь внимание широкой аудитории. Если у вас возникнут дополнительные вопросы или уточнения, пожалуйста, обращайтесь к нам по адресу [webform](https://simeononsecurity.com/contactus/)
***Счастливого письма!
diff --git a/content/guest-posts/index.zh.md b/content/guest-posts/index.zh.md
index 71c8f45282740..2e3fee8de209b 100644
--- a/content/guest-posts/index.zh.md
+++ b/content/guest-posts/index.zh.md
@@ -11,11 +11,11 @@ coverCaption: "通过客座博客与我们的社区分享您的专业知识和
感谢您有兴趣为我们的网站投稿!我们欢迎符合我们内容重点的特邀博客投稿。请按照以下步骤提交文章以供考虑:
-1.通过以下网站表格联系我们 [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/)来表达您对客座博客的兴趣。
+1.通过以下网站表格联系我们 [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/)来表达您对客座博客的兴趣。
2.以 Markdown (md) 或 HTML 格式准备文章。
-3.在我们的 GitHub 仓库中提交拉取请求,网址为 [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3.在我们的 GitHub 仓库中提交拉取请求,网址为 [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4.确保您的文章包含有效的 frontmatter(元数据)和所有必需的变量,如下例所示:
@@ -122,7 +122,7 @@ coverCaption: "Caption for your cover image."
- 我们感谢您的理解和合作,请遵守这些准则,以保持 SimeonOnSecurity 上内容的质量和相关性。
-我们期待收到您的宝贵意见,并帮助您将自己的见解传播给更多的受众。如果您有任何进一步的问题或说明,请随时通过以下方式联系我们 [webform](https://simeononsecurity.ch/contactus/)
+我们期待收到您的宝贵意见,并帮助您将自己的见解传播给更多的受众。如果您有任何进一步的问题或说明,请随时通过以下方式联系我们 [webform](https://simeononsecurity.com/contactus/)
***写作愉快!***
diff --git a/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md b/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md
index cfc1533218e5c..0caa7cc4b9622 100644
--- a/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md
+++ b/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md
@@ -19,7 +19,7 @@ Windows 11 introduces new system requirements, including the need for a TPM (Tru
### **Bypassing TPM, Secure Boot, and RAM Checks in Windows 11**
-Virtualized environments like VMware vSphere can utilize a virtual TPM ([vTPM](https://simeononsecurity.ch/guides/enable-virtual-trusted-platform-module-for-existing-virtual-machine/)) to emulate a TPM 2.0 device, satisfying the TPM requirement for Windows 11 installation. However, for scenarios where a vTPM is not available, the following **registry keys** can be used to bypass the checks during the installation process:
+Virtualized environments like VMware vSphere can utilize a virtual TPM ([vTPM](https://simeononsecurity.com/guides/enable-virtual-trusted-platform-module-for-existing-virtual-machine/)) to emulate a TPM 2.0 device, satisfying the TPM requirement for Windows 11 installation. However, for scenarios where a vTPM is not available, the following **registry keys** can be used to bypass the checks during the installation process:
- **BypassTPMCheck**: Skip TPM check.
- **BypassSecureBootCheck**: Skip Secure Boot check.
diff --git a/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md b/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md
index 809208d2fc222..60ff2c6b32840 100644
--- a/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md
+++ b/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md
@@ -23,11 +23,11 @@ The ESP32 is a versatile microcontroller renowned for its WiFi and Bluetooth cap
### Alternate Instructions
**Want to use a linux distro or a raspberry pi?**
-Check out our guide on [**Setting up a NTRIP server on Linux**](https://simeononsecurity.ch/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
+Check out our guide on [**Setting up a NTRIP server on Linux**](https://simeononsecurity.com/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
### Looking for how to use this with Onocoy?
-Check out our guide on [**DIY Onocoy Ntrip Server and Reference Station Setup**](https://simeononsecurity.ch/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
+Check out our guide on [**DIY Onocoy Ntrip Server and Reference Station Setup**](https://simeononsecurity.com/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
### Recommended Hardware Components
Before we begin, let's take a look at the hardware components you'll need:
diff --git a/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md b/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md
index 8591d2ddc7478..4c83136d4b608 100644
--- a/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md
+++ b/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md
@@ -67,7 +67,7 @@ To achieve 10 Gigabit Ethernet capabilities, you'll need to add 10g NICs to your
2. Create a bootable USB drive with the pfSense installer using tools like **Rufus** (Windows) or **dd** (Linux).
-3. Insert the USB drive into the HP t640, and follow the instructions from our guide on [installing pfSense on the HP t640](https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/) .
+3. Insert the USB drive into the HP t640, and follow the instructions from our guide on [installing pfSense on the HP t640](https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/) .
1. It's a bit different than the standard install. Please read the guide.
### **Configuring pfSense**
diff --git a/content/guides/docker-image-optimization-tips/index.en.md b/content/guides/docker-image-optimization-tips/index.en.md
index e551819fd8474..65b6d958727cf 100644
--- a/content/guides/docker-image-optimization-tips/index.en.md
+++ b/content/guides/docker-image-optimization-tips/index.en.md
@@ -15,7 +15,7 @@ ref: ["/articles/how-to-build-docker-containers-from-scratch","/articles/how-to-
**Optimizing Docker Images for Efficiency, Performance, and Security**
-In the realm of containerization, [**Docker**](https://simeononsecurity.ch/articles/how-to-build-docker-containers-from-scratch/) reigns supreme. **Docker images** serve as the foundation of containerized applications, encapsulating every element required for seamless operation, from code to essential libraries and dependencies. However, as applications expand and evolve, [**Docker images**](https://simeononsecurity.ch/articles/how-to-secure-your-docker-and-kubernetes-environment/) can bloat, resulting in inefficient and resource-intensive containers. In this comprehensive guide, we delve into expert techniques to meticulously optimize **Docker images**, enhancing efficiency, boosting performance, and fortifying security.
+In the realm of containerization, [**Docker**](https://simeononsecurity.com/articles/how-to-build-docker-containers-from-scratch/) reigns supreme. **Docker images** serve as the foundation of containerized applications, encapsulating every element required for seamless operation, from code to essential libraries and dependencies. However, as applications expand and evolve, [**Docker images**](https://simeononsecurity.com/articles/how-to-secure-your-docker-and-kubernetes-environment/) can bloat, resulting in inefficient and resource-intensive containers. In this comprehensive guide, we delve into expert techniques to meticulously optimize **Docker images**, enhancing efficiency, boosting performance, and fortifying security.
## **Introduction**
@@ -24,7 +24,7 @@ In the realm of containerization, [**Docker**](https://simeononsecurity.ch/artic
In the world of containerization, **Docker** has become a household name. **Docker images** are the building blocks of containerized applications. They encapsulate everything an application needs to run, from code to libraries and dependencies. However, as your application grows and evolves, so do your **Docker images**, often leading to bloated and inefficient containers. In this article, we'll explore techniques to optimize **Docker images** for efficiency, performance, and security.
______
-Explore more about [Docker optimization](https://simeononsecurity.ch/articles/how-to-build-docker-containers-from-scratch/) and [container security](https://simeononsecurity.ch/articles/how-to-secure-your-docker-and-kubernetes-environment/) in these informative articles:
+Explore more about [Docker optimization](https://simeononsecurity.com/articles/how-to-build-docker-containers-from-scratch/) and [container security](https://simeononsecurity.com/articles/how-to-secure-your-docker-and-kubernetes-environment/) in these informative articles:
- [How to Build Docker Containers from Scratch](/articles/how-to-build-docker-containers-from-scratch/)
- [How to Secure Your Docker and Kubernetes Environment](/articles/how-to-secure-your-docker-and-kubernetes-environment/)
diff --git a/content/guides/enhance-oracle-jre-8-security/index.en.md b/content/guides/enhance-oracle-jre-8-security/index.en.md
index 8612df01f81fd..a91252cb4fb38 100644
--- a/content/guides/enhance-oracle-jre-8-security/index.en.md
+++ b/content/guides/enhance-oracle-jre-8-security/index.en.md
@@ -121,7 +121,7 @@ An **accepted sites list** limits software execution to authorized sources, mini
2. Add each authorized site on a new line.
```ini
https://example.com
- https://simeononsecurity.ch
+ https://simeononsecurity.com
```
See an example of a known [working configuration for `exception.sites`](https://github.com/simeononsecurity/Oracle-JRE-8-STIG-Script/blob/master/Files/exception.sites).
diff --git a/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md b/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md
index c5485f50597f3..68b26e63f6d33 100644
--- a/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md
+++ b/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md
@@ -253,4 +253,4 @@ ______
Creating custom Ethernet cables is a rewarding DIY project, and it allows you to have full control over your network setup. Whether you're a tech enthusiast or need cables for specific applications, this guide will walk you through the process step by step. Don't hesitate to explore the world of custom Ethernet cables and enhance your networking capabilities.
-Lastly, if you've made it this far, you might be interested in reading our guide on [Setting up a Ubiquiti Unifi Home Network](https://simeononsecurity.ch/articles/the-ideal-ubiquiti-unifi-networking-setup-both-simple-and-advanced/).
\ No newline at end of file
+Lastly, if you've made it this far, you might be interested in reading our guide on [Setting up a Ubiquiti Unifi Home Network](https://simeononsecurity.com/articles/the-ideal-ubiquiti-unifi-networking-setup-both-simple-and-advanced/).
\ No newline at end of file
diff --git a/content/guides/secure-sshd-configurations-guide/index.en.md b/content/guides/secure-sshd-configurations-guide/index.en.md
index 9ae701a9e414e..5089209b9fa2a 100644
--- a/content/guides/secure-sshd-configurations-guide/index.en.md
+++ b/content/guides/secure-sshd-configurations-guide/index.en.md
@@ -23,7 +23,7 @@ In an **increasingly digital world**, the security of your server is paramount.
## **Understanding SSHD**
-[**SSH (Secure Shell)**](https://simeononsecurity.ch/articles/what-is-ssh/) is a **cryptographic network protocol** that allows **secure data communication**, **remote command-line login**, and other **secure network services**. **SSHD** is the **server component of SSH**, responsible for **authentication**, **encryption**, and **secure communication**. It's **vital to configure SSHD** properly to prevent **unauthorized access**.
+[**SSH (Secure Shell)**](https://simeononsecurity.com/articles/what-is-ssh/) is a **cryptographic network protocol** that allows **secure data communication**, **remote command-line login**, and other **secure network services**. **SSHD** is the **server component of SSH**, responsible for **authentication**, **encryption**, and **secure communication**. It's **vital to configure SSHD** properly to prevent **unauthorized access**.
### **Key Configuration Steps**
@@ -53,7 +53,7 @@ PermitRootLogin no
In the realm of **Secure SSHD Configurations**, robust authentication is the cornerstone of safeguarding your server. Let's delve into two pivotal methods for achieving this: **strong password policies** and **key-based authentication**.
-1. [**Strong Password Policies**](https://simeononsecurity.ch/articles/ten-essential-password-security-guidelines-to-follow): Start by enforcing stringent password rules. Craft passwords that are lengthy and encompass a mixture of upper and lower-case letters, numbers, and special characters. Steer clear of easily guessable information, such as birthdays or common words.
+1. [**Strong Password Policies**](https://simeononsecurity.com/articles/ten-essential-password-security-guidelines-to-follow): Start by enforcing stringent password rules. Craft passwords that are lengthy and encompass a mixture of upper and lower-case letters, numbers, and special characters. Steer clear of easily guessable information, such as birthdays or common words.
Example: A formidable password might look like "P@$$w0rdS3cureSSH."
@@ -140,13 +140,13 @@ These configurations prioritize stronger encryption and key exchange algorithms,
### **Protecting SSHD from Threats**
#### **Brute Force Attacks**
-SSH is a **common target** for **brute force attacks** where attackers try to guess passwords **repeatedly**. Implementing [**strong password policies**](https://simeononsecurity.ch/articles/ten-essential-password-security-guidelines-to-follow/), using [**key-based authentication**](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/), and **monitoring logs** can help thwart these attacks.
+SSH is a **common target** for **brute force attacks** where attackers try to guess passwords **repeatedly**. Implementing [**strong password policies**](https://simeononsecurity.com/articles/ten-essential-password-security-guidelines-to-follow/), using [**key-based authentication**](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/), and **monitoring logs** can help thwart these attacks.
#### **DDoS Attacks**
**Distributed Denial of Service (DDoS) attacks** can overwhelm your server, making it unresponsive. Use tools like **iptables** or **fail2ban** to mitigate the impact of DDoS attacks on your SSHD service.
#### **Zero-Day Exploits**
-Stay informed about SSHD vulnerabilities and [**patch**](https://simeononsecurity.ch/guides/automate-linux-patching-and-updates-with-ansible/) them as soon as updates become available. Government agencies such as the [**National Institute of Standards and Technology (NIST)**](https://www.nist.gov/) often release guidelines on secure configurations.
+Stay informed about SSHD vulnerabilities and [**patch**](https://simeononsecurity.com/guides/automate-linux-patching-and-updates-with-ansible/) them as soon as updates become available. Government agencies such as the [**National Institute of Standards and Technology (NIST)**](https://www.nist.gov/) often release guidelines on secure configurations.
## **Conclusion**
diff --git a/content/jobs/index.en.html b/content/jobs/index.en.html
index 7f3340ec2c225..e8c0c4fe13de7 100644
--- a/content/jobs/index.en.html
+++ b/content/jobs/index.en.html
@@ -19,7 +19,7 @@
diff --git a/content/github/shodan-api-ansible-automation-guide/index.en.md b/content/github/shodan-api-ansible-automation-guide/index.en.md
index fccf4e17a4f7a..2560d8082781c 100644
--- a/content/github/shodan-api-ansible-automation-guide/index.en.md
+++ b/content/github/shodan-api-ansible-automation-guide/index.en.md
@@ -59,7 +59,7 @@ Contributions to this collection are welcome! If you have improvements or new mo
This project is licensed under the MIT License. See the [`LICENSE`](https://github.com/simeononsecurity/ansible_shodan/blob/main/LICENSE) file for details.
### Author
-This Ansible Shodan Modules collection is authored by [SimeonOnSecurity](https://simeononsecurity.ch/).
+This Ansible Shodan Modules collection is authored by [SimeonOnSecurity](https://simeononsecurity.com/).
### Acknowledgments
Special thanks to the Shodan API for providing the capabilities to interact with their service using Ansible.
\ No newline at end of file
diff --git a/content/github/stiging-standalone-windows-servers/index.bn.md b/content/github/stiging-standalone-windows-servers/index.bn.md
index 0750655ec4765..2ec5f5c5dbec6 100644
--- a/content/github/stiging-standalone-windows-servers/index.bn.md
+++ b/content/github/stiging-standalone-windows-servers/index.bn.md
@@ -84,7 +84,7 @@ Windows 10 বাক্সের বাইরে অনিরাপদ অপা
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ca.md b/content/github/stiging-standalone-windows-servers/index.ca.md
index c4aeb39faeb5b..cb5907ffeedd1 100644
--- a/content/github/stiging-standalone-windows-servers/index.ca.md
+++ b/content/github/stiging-standalone-windows-servers/index.ca.md
@@ -84,7 +84,7 @@ Els sistemes autònoms són alguns dels sistemes més difícils i molestos de pr
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.de.md b/content/github/stiging-standalone-windows-servers/index.de.md
index 9babff3c20e81..3217c3864aef2 100644
--- a/content/github/stiging-standalone-windows-servers/index.de.md
+++ b/content/github/stiging-standalone-windows-servers/index.de.md
@@ -84,7 +84,7 @@ Eigenständige Systeme gehören zu den am schwierigsten und lästigsten zu siche
### Automatisierte Installation:
Das Skript kann wie folgt aus dem extrahierten GitHub-Download gestartet werden:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manuelle Installation:
diff --git a/content/github/stiging-standalone-windows-servers/index.en.md b/content/github/stiging-standalone-windows-servers/index.en.md
index 31fe408cb04ef..c3b9281eb88b5 100644
--- a/content/github/stiging-standalone-windows-servers/index.en.md
+++ b/content/github/stiging-standalone-windows-servers/index.en.md
@@ -22,7 +22,7 @@ We now offer a playbook collection for this script. Please see the following:
Windows 10 is insecure operating system out of the box and requires many changes to insure [FISMA](https://www.cisa.gov/federal-information-security-modernization-act) compliance.
Organizations like [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended and required configuration changes to lockdown, harden, and secure the operating system and ensure government compliance. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many physical attacks on a system.
-Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.ch/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
+Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.com/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
## Notes:
@@ -89,7 +89,7 @@ Standalone systems are some of the most difficult and annoying systems to secure
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.es.md b/content/github/stiging-standalone-windows-servers/index.es.md
index 83003a0215e36..cc3f4f8426ce2 100644
--- a/content/github/stiging-standalone-windows-servers/index.es.md
+++ b/content/github/stiging-standalone-windows-servers/index.es.md
@@ -84,7 +84,7 @@ Los sistemas autónomos son algunos de los más difíciles y molestos de protege
### Instalación automatizada:
El script puede ser lanzado desde la descarga extraída de GitHub así:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Instalación manual:
diff --git a/content/github/stiging-standalone-windows-servers/index.fr.md b/content/github/stiging-standalone-windows-servers/index.fr.md
index 13c0104fded1d..993d37a471496 100644
--- a/content/github/stiging-standalone-windows-servers/index.fr.md
+++ b/content/github/stiging-standalone-windows-servers/index.fr.md
@@ -84,7 +84,7 @@ Les systèmes autonomes sont parmi les plus difficiles et les plus ennuyeux à s
### Installation automatisée :
Le script peut être lancé à partir du téléchargement GitHub extrait comme suit :
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Installation manuelle :
diff --git a/content/github/stiging-standalone-windows-servers/index.it.md b/content/github/stiging-standalone-windows-servers/index.it.md
index 5c2ca36d028c8..d026047751d22 100644
--- a/content/github/stiging-standalone-windows-servers/index.it.md
+++ b/content/github/stiging-standalone-windows-servers/index.it.md
@@ -84,7 +84,7 @@ I sistemi autonomi sono alcuni dei sistemi più difficili e fastidiosi da proteg
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ja.md b/content/github/stiging-standalone-windows-servers/index.ja.md
index 50f60c7029752..75fadacd8fa6c 100644
--- a/content/github/stiging-standalone-windows-servers/index.ja.md
+++ b/content/github/stiging-standalone-windows-servers/index.ja.md
@@ -84,7 +84,7 @@ Windows 10 は、そのままでは安全ではないオペレーティング
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.nl.md b/content/github/stiging-standalone-windows-servers/index.nl.md
index 27776c33eaae3..f6dbaa245528c 100644
--- a/content/github/stiging-standalone-windows-servers/index.nl.md
+++ b/content/github/stiging-standalone-windows-servers/index.nl.md
@@ -84,7 +84,7 @@ Standalone systemen behoren tot de moeilijkste en vervelendste systemen om te be
### Geautomatiseerde installatie:
Het script kan vanaf de uitgepakte GitHub-download als volgt worden gestart:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Handmatige installatie:
diff --git a/content/github/stiging-standalone-windows-servers/index.pa.md b/content/github/stiging-standalone-windows-servers/index.pa.md
index 026e074385c7b..085d0b2b00dfe 100644
--- a/content/github/stiging-standalone-windows-servers/index.pa.md
+++ b/content/github/stiging-standalone-windows-servers/index.pa.md
@@ -84,7 +84,7 @@ Windows 10 ਬਾਕਸ ਤੋਂ ਬਾਹਰ ਅਸੁਰੱਖਿਅਤ ਓ
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.pl.md b/content/github/stiging-standalone-windows-servers/index.pl.md
index d4edc67222118..e3401829110d1 100644
--- a/content/github/stiging-standalone-windows-servers/index.pl.md
+++ b/content/github/stiging-standalone-windows-servers/index.pl.md
@@ -84,7 +84,7 @@ Systemy autonomiczne są jednymi z najtrudniejszych i najbardziej irytujących s
### Automated Install:
Skrypt można uruchomić z rozpakowanego pliku do pobrania z GitHuba w ten sposób:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.pt.md b/content/github/stiging-standalone-windows-servers/index.pt.md
index dafbc6c1fd066..27bc75bcd2593 100644
--- a/content/github/stiging-standalone-windows-servers/index.pt.md
+++ b/content/github/stiging-standalone-windows-servers/index.pt.md
@@ -84,7 +84,7 @@ Os sistemas autônomos são alguns dos sistemas mais difíceis e irritantes de p
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ro.md b/content/github/stiging-standalone-windows-servers/index.ro.md
index bb479b7046b16..4b5364fc3e2da 100644
--- a/content/github/stiging-standalone-windows-servers/index.ro.md
+++ b/content/github/stiging-standalone-windows-servers/index.ro.md
@@ -84,7 +84,7 @@ Sistemele de sine stătătoare sunt unele dintre cele mai dificil și enervant s
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.ru.md b/content/github/stiging-standalone-windows-servers/index.ru.md
index f7923bbf4807c..d9813b1b1ca88 100644
--- a/content/github/stiging-standalone-windows-servers/index.ru.md
+++ b/content/github/stiging-standalone-windows-servers/index.ru.md
@@ -84,7 +84,7 @@ Windows 10 — небезопасная операционная система
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-servers/index.zh.md b/content/github/stiging-standalone-windows-servers/index.zh.md
index 15003c9b12a3c..547a2aa259afd 100644
--- a/content/github/stiging-standalone-windows-servers/index.zh.md
+++ b/content/github/stiging-standalone-windows-servers/index.zh.md
@@ -84,7 +84,7 @@ Windows 10 是开箱即用的不安全操作系统,需要进行许多更改才
### Automated Install:
The script may be launched from the extracted GitHub download like this:
```powershell
-iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/standalonewindows.ps1'))
+iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.com/scripts/standalonewindows.ps1'))
```
### Manual Install:
diff --git a/content/github/stiging-standalone-windows-systems/index.en.md b/content/github/stiging-standalone-windows-systems/index.en.md
index a9776478275a4..d08a55a077f61 100644
--- a/content/github/stiging-standalone-windows-systems/index.en.md
+++ b/content/github/stiging-standalone-windows-systems/index.en.md
@@ -17,7 +17,7 @@ tags: ["Automation", "Windows STIG Compliance", "Powershell Scripting", "Windows
Windows 10 is insecure operating system out of the box and requires many changes to insure [FISMA](https://www.cisa.gov/federal-information-security-modernization-act) compliance.
Organizations like [Microsoft](https://microsoft.com), [Cyber.mil](https://public.cyber.mil), the [Department of Defense](https://dod.gov), and the [National Security Agency](https://www.nsa.gov/) have recommended and required configuration changes to lockdown, harden, and secure the operating system and ensure government compliance. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many physical attacks on a system.
-Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.ch/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
+Standalone systems are some of the most difficult and annoying systems to secure. When not automated, they require manual changes of each [STIG/SRG](https://simeononsecurity.com/github/stiging-standalone-windows-servers/). Totalling over 1000 configuration changes on a typical deployment and an average of 5 minutes per change equaling 3.5 days worth of work. This script aims to speed up that process significantly.
## Notes:
diff --git a/content/guest-posts/index.de.md b/content/guest-posts/index.de.md
index ec77fb1f5f0a0..475cec6ddbaf6 100644
--- a/content/guest-posts/index.de.md
+++ b/content/guest-posts/index.de.md
@@ -11,11 +11,11 @@ coverCaption: "Teilen Sie Ihr Fachwissen und Ihre Erkenntnisse mit unserer Commu
Vielen Dank für Ihr Interesse, einen Beitrag zu unserer Website zu leisten! Wir freuen uns über Beiträge für Gastblogs, die zu unserem inhaltlichen Schwerpunkt passen. Um einen Artikel einzureichen, folgen Sie bitte diesen Schritten:
-1. Kontaktieren Sie uns über das Webformular unter [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) um Ihr Interesse an Gastbeiträgen zu bekunden.
+1. Kontaktieren Sie uns über das Webformular unter [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) um Ihr Interesse an Gastbeiträgen zu bekunden.
2. Bereiten Sie Ihren Artikel entweder im Markdown- (md) oder HTML-Format vor.
-3. Reichen Sie einen Pull-Request auf unserem GitHub-Repository ein unter [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Reichen Sie einen Pull-Request auf unserem GitHub-Repository ein unter [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Vergewissern Sie sich, dass Ihr Artikel gültige Frontmatter (Metadaten) mit allen erforderlichen Variablen enthält, wie im folgenden Beispiel gezeigt:
@@ -122,7 +122,7 @@ Gast-Blogging ist eine für beide Seiten vorteilhafte Vereinbarung, bei der Auto
- Wir danken Ihnen für Ihr Verständnis und Ihre Mitarbeit bei der Einhaltung dieser Richtlinien, um die Qualität und Relevanz der Inhalte auf SimeonOnSecurity zu erhalten.
-Wir freuen uns auf Ihre wertvollen Beiträge und darauf, Sie dabei zu unterstützen, ein größeres Publikum mit Ihren Erkenntnissen zu erreichen. Sollten Sie weitere Fragen oder Unklarheiten haben, zögern Sie bitte nicht, uns über das Kontaktformular zu kontaktieren. [webform](https://simeononsecurity.ch/contactus/)
+Wir freuen uns auf Ihre wertvollen Beiträge und darauf, Sie dabei zu unterstützen, ein größeres Publikum mit Ihren Erkenntnissen zu erreichen. Sollten Sie weitere Fragen oder Unklarheiten haben, zögern Sie bitte nicht, uns über das Kontaktformular zu kontaktieren. [webform](https://simeononsecurity.com/contactus/)
***Glückliches Schreiben!***
diff --git a/content/guest-posts/index.en.md b/content/guest-posts/index.en.md
index dafcecfa5a4c0..fec7d77fa59f7 100644
--- a/content/guest-posts/index.en.md
+++ b/content/guest-posts/index.en.md
@@ -11,11 +11,11 @@ coverCaption: "Share your expertise and insights with our community through gues
Thank you for your interest in contributing to our website! We welcome guest blog submissions that align with our content focus. To submit an article for consideration, please follow these steps:
-1. Contact us through the webform at [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) to express your interest in guest blogging.
+1. Contact us through the webform at [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) to express your interest in guest blogging.
2. Prepare your article in either Markdown (md) or HTML format.
-3. Submit a pull request on our GitHub repository at [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors).
+3. Submit a pull request on our GitHub repository at [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors).
4. Ensure your article includes valid frontmatter (metadata) with all the required variables, as shown in the example below:
@@ -122,7 +122,7 @@ Guest blogging is a mutually beneficial arrangement where writers have the oppor
- We appreciate your understanding and cooperation in following these guidelines to maintain the quality and relevance of content on SimeonOnSecurity.
-We look forward to receiving your valuable contributions and helping you reach a wider audience with your insights. If you have any further questions or clarifications, please don't hesitate to contact us through the [webform](https://simeononsecurity.ch/contactus/).
+We look forward to receiving your valuable contributions and helping you reach a wider audience with your insights. If you have any further questions or clarifications, please don't hesitate to contact us through the [webform](https://simeononsecurity.com/contactus/).
***Happy writing!***
diff --git a/content/guest-posts/index.es.md b/content/guest-posts/index.es.md
index ba60725d8a701..7e844f782dd67 100644
--- a/content/guest-posts/index.es.md
+++ b/content/guest-posts/index.es.md
@@ -11,11 +11,11 @@ coverCaption: "Comparta su experiencia y conocimientos con nuestra comunidad a t
Gracias por su interés en contribuir a nuestro sitio web. Recibimos con agrado artículos de blogs invitados que se ajusten a nuestro enfoque de contenidos. Para enviar un artículo, siga estos pasos:
-1. Póngase en contacto con nosotros a través del formulario web en [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) para expresar su interés en participar como blogger invitado.
+1. Póngase en contacto con nosotros a través del formulario web en [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) para expresar su interés en participar como blogger invitado.
2. Prepare su artículo en formato Markdown (md) o HTML.
-3. Envíe una solicitud de extracción (pull request) a nuestro repositorio de GitHub en [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Envíe una solicitud de extracción (pull request) a nuestro repositorio de GitHub en [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Asegúrese de que su artículo incluye un frontmatter (metadatos) válido con todas las variables requeridas, como se muestra en el siguiente ejemplo:
@@ -122,7 +122,7 @@ Se trata de un acuerdo mutuamente beneficioso en el que los autores tienen la op
- Agradecemos su comprensión y cooperación en el seguimiento de estas directrices para mantener la calidad y relevancia de los contenidos en SimeonOnSecurity.
-Esperamos recibir sus valiosas contribuciones y ayudarle a llegar a un público más amplio con sus ideas. Si tiene alguna pregunta o aclaración, no dude en ponerse en contacto con nosotros a través de la dirección de correo electrónico [webform](https://simeononsecurity.ch/contactus/)
+Esperamos recibir sus valiosas contribuciones y ayudarle a llegar a un público más amplio con sus ideas. Si tiene alguna pregunta o aclaración, no dude en ponerse en contacto con nosotros a través de la dirección de correo electrónico [webform](https://simeononsecurity.com/contactus/)
***¡Feliz escritura!
diff --git a/content/guest-posts/index.fr.md b/content/guest-posts/index.fr.md
index c709ac5f62963..f7a34bb454580 100644
--- a/content/guest-posts/index.fr.md
+++ b/content/guest-posts/index.fr.md
@@ -11,11 +11,11 @@ coverCaption: "Partagez votre expertise et vos connaissances avec notre communau
Nous vous remercions de l'intérêt que vous portez à notre site web ! Nous accueillons volontiers les propositions de blogs d'invités qui correspondent à notre objectif de contenu. Pour soumettre un article, veuillez suivre les étapes suivantes :
-1. Contactez-nous à l'aide du formulaire Web à l'adresse suivante [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) pour exprimer votre intérêt pour le guest blogging.
+1. Contactez-nous à l'aide du formulaire Web à l'adresse suivante [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) pour exprimer votre intérêt pour le guest blogging.
2. Préparez votre article au format Markdown (md) ou HTML.
-3. Soumettez une demande d'extraction sur notre dépôt GitHub à l'adresse suivante [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Soumettez une demande d'extraction sur notre dépôt GitHub à l'adresse suivante [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Veillez à ce que votre article contienne des métadonnées valides avec toutes les variables requises, comme le montre l'exemple ci-dessous :
@@ -122,7 +122,7 @@ Le guest blogging est un arrangement mutuellement bénéfique dans le cadre duqu
- Nous vous remercions de votre compréhension et de votre coopération en suivant ces directives afin de maintenir la qualité et la pertinence du contenu de SimeonOnSecurity.
-Nous nous réjouissons de recevoir vos précieuses contributions et de vous aider à atteindre un public plus large grâce à vos idées. Si vous avez d'autres questions ou des éclaircissements, n'hésitez pas à nous contacter par l'intermédiaire de l'adresse suivante [webform](https://simeononsecurity.ch/contactus/)
+Nous nous réjouissons de recevoir vos précieuses contributions et de vous aider à atteindre un public plus large grâce à vos idées. Si vous avez d'autres questions ou des éclaircissements, n'hésitez pas à nous contacter par l'intermédiaire de l'adresse suivante [webform](https://simeononsecurity.com/contactus/)
***Heureuse écriture!***
diff --git a/content/guest-posts/index.it.md b/content/guest-posts/index.it.md
index b5601a87aa1ac..00f8aed6eee48 100644
--- a/content/guest-posts/index.it.md
+++ b/content/guest-posts/index.it.md
@@ -11,11 +11,11 @@ coverCaption: "Condividete la vostra esperienza e le vostre intuizioni con la no
Grazie per il vostro interesse a contribuire al nostro sito web! Siamo lieti di ricevere articoli per blog ospiti che siano in linea con i nostri contenuti. Per inviare un articolo da prendere in considerazione, seguite i seguenti passaggi:
-1. Contattateci attraverso il modulo web all'indirizzo [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) per esprimere il vostro interesse per il guest blogging.
+1. Contattateci attraverso il modulo web all'indirizzo [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) per esprimere il vostro interesse per il guest blogging.
2. Preparate il vostro articolo in formato Markdown (md) o HTML.
-3. Inviate una richiesta di pull sul nostro repository GitHub all'indirizzo [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Inviate una richiesta di pull sul nostro repository GitHub all'indirizzo [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Assicuratevi che l'articolo includa un frontmatter (metadati) valido con tutte le variabili richieste, come mostrato nell'esempio seguente:
@@ -122,7 +122,7 @@ Il guest blogging è un accordo reciprocamente vantaggioso in cui gli scrittori
- Apprezziamo la vostra comprensione e collaborazione nel seguire queste linee guida per mantenere la qualità e la rilevanza dei contenuti di SimeonOnSecurity.
-Saremo lieti di ricevere i vostri preziosi contributi e di aiutarvi a raggiungere un pubblico più ampio con le vostre intuizioni. In caso di ulteriori domande o chiarimenti, non esitate a contattarci attraverso il sito [webform](https://simeononsecurity.ch/contactus/)
+Saremo lieti di ricevere i vostri preziosi contributi e di aiutarvi a raggiungere un pubblico più ampio con le vostre intuizioni. In caso di ulteriori domande o chiarimenti, non esitate a contattarci attraverso il sito [webform](https://simeononsecurity.com/contactus/)
***Felice scrittura! ***
diff --git a/content/guest-posts/index.ja.md b/content/guest-posts/index.ja.md
index 0306a01ce55b4..4791c66345904 100644
--- a/content/guest-posts/index.ja.md
+++ b/content/guest-posts/index.ja.md
@@ -11,11 +11,11 @@ coverCaption: "ゲストブログを通じて、あなたの専門知識や見
当サイトへの寄稿にご関心をお寄せいただき、ありがとうございます!私たちは、私たちのコンテンツの焦点に沿ったゲストブログの投稿を歓迎します。記事を投稿するには、以下の手順に従ってください:
-1.以下のウェブフォームからご連絡ください。 [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/)をクリックして、ゲスト・ブログへの興味を表明してください。
+1.以下のウェブフォームからご連絡ください。 [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/)をクリックして、ゲスト・ブログへの興味を表明してください。
2.記事をMarkdown (md)またはHTML形式で準備する。
-3.以下のGitHubリポジトリにプルリクエストを提出する。 [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3.以下のGitHubリポジトリにプルリクエストを提出する。 [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4.以下の例に示すように、あなたの記事がすべての必要な変数を含む有効なフロントマター(メタデータ)を含んでいることを確認してください:
@@ -122,7 +122,7 @@ SimeonOnSecurityでは、ゲストブログは主にネットワーキングと
- SimeonOnSecurityのコンテンツの質と関連性を維持するため、これらのガイドラインに従うことへのご理解とご協力をお願いいたします。
-皆様の貴重なご投稿をお待ちしております。ご質問やご不明な点がございましたら、ご遠慮なく下記までご連絡ください。 [webform](https://simeononsecurity.ch/contactus/)
+皆様の貴重なご投稿をお待ちしております。ご質問やご不明な点がございましたら、ご遠慮なく下記までご連絡ください。 [webform](https://simeononsecurity.com/contactus/)
***ハッピー・ライティング!***
diff --git a/content/guest-posts/index.nl.md b/content/guest-posts/index.nl.md
index fb576c94cc907..caa9fe72d0b27 100644
--- a/content/guest-posts/index.nl.md
+++ b/content/guest-posts/index.nl.md
@@ -11,11 +11,11 @@ coverCaption: "Deel je expertise en inzichten met onze community door te gastblo
Bedankt voor je interesse om bij te dragen aan onze website! We verwelkomen gastblogs die aansluiten bij onze inhoudelijke focus. Volg deze stappen om een artikel in te dienen:
-1. Neem contact met ons op via het webformulier op [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) om je interesse in gastbloggen te tonen.
+1. Neem contact met ons op via het webformulier op [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) om je interesse in gastbloggen te tonen.
2. Bereid je artikel voor in Markdown (md) of HTML-formaat.
-3. Dien een pull request in op onze GitHub repository op [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Dien een pull request in op onze GitHub repository op [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Zorg ervoor dat je artikel geldige frontmatter (metadata) bevat met alle vereiste variabelen, zoals in het onderstaande voorbeeld:
@@ -122,7 +122,7 @@ Gastbloggen is een wederzijds voordelige regeling waarbij schrijvers de kans kri
- Wij waarderen uw begrip en medewerking bij het volgen van deze richtlijnen om de kwaliteit en relevantie van de inhoud op SimeonOnSecurity te behouden.
-We kijken ernaar uit om uw waardevolle bijdragen te ontvangen en u te helpen een breder publiek te bereiken met uw inzichten. Als u nog vragen of verduidelijkingen heeft, aarzel dan niet om contact met ons op te nemen via de [webform](https://simeononsecurity.ch/contactus/)
+We kijken ernaar uit om uw waardevolle bijdragen te ontvangen en u te helpen een breder publiek te bereiken met uw inzichten. Als u nog vragen of verduidelijkingen heeft, aarzel dan niet om contact met ons op te nemen via de [webform](https://simeononsecurity.com/contactus/)
***Veel schrijfplezier!
diff --git a/content/guest-posts/index.pl.md b/content/guest-posts/index.pl.md
index 89eac52d942df..57ed61a9d4747 100644
--- a/content/guest-posts/index.pl.md
+++ b/content/guest-posts/index.pl.md
@@ -11,11 +11,11 @@ coverCaption: "Podziel się swoją wiedzą i spostrzeżeniami z naszą społeczn
Dziękujemy za zainteresowanie współtworzeniem naszej witryny! Czekamy na zgłoszenia gościnnych blogów, które są zgodne z naszą treścią. Aby przesłać artykuł do rozpatrzenia, wykonaj następujące kroki:
-1. Skontaktuj się z nami za pośrednictwem formularza internetowego pod adresem [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) aby wyrazić zainteresowanie gościnnym blogowaniem.
+1. Skontaktuj się z nami za pośrednictwem formularza internetowego pod adresem [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) aby wyrazić zainteresowanie gościnnym blogowaniem.
2. Przygotuj artykuł w formacie Markdown (md) lub HTML.
-3. Prześlij pull request do naszego repozytorium GitHub pod adresem [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Prześlij pull request do naszego repozytorium GitHub pod adresem [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Upewnij się, że artykuł zawiera prawidłowy frontmatter (metadane) ze wszystkimi wymaganymi zmiennymi, jak pokazano w poniższym przykładzie:
@@ -122,7 +122,7 @@ Blogowanie gościnne jest obustronnie korzystnym porozumieniem, w którym autorz
- Dziękujemy za zrozumienie i współpracę w przestrzeganiu tych wytycznych w celu utrzymania jakości i trafności treści na SimeonOnSecurity.
-Z niecierpliwością czekamy na Twój cenny wkład i pomoc w dotarciu z Twoimi spostrzeżeniami do szerszego grona odbiorców. W razie jakichkolwiek dalszych pytań lub wyjaśnień, prosimy o kontakt za pośrednictwem strony internetowej [webform](https://simeononsecurity.ch/contactus/)
+Z niecierpliwością czekamy na Twój cenny wkład i pomoc w dotarciu z Twoimi spostrzeżeniami do szerszego grona odbiorców. W razie jakichkolwiek dalszych pytań lub wyjaśnień, prosimy o kontakt za pośrednictwem strony internetowej [webform](https://simeononsecurity.com/contactus/)
***Happy writing!***
diff --git a/content/guest-posts/index.ro.md b/content/guest-posts/index.ro.md
index 93d1a2b386a9a..5b4545374b684 100644
--- a/content/guest-posts/index.ro.md
+++ b/content/guest-posts/index.ro.md
@@ -11,11 +11,11 @@ coverCaption: "Împărtășiți expertiza și cunoștințele dvs. cu comunitatea
Vă mulțumim pentru interesul dumneavoastră de a contribui la site-ul nostru! Primim cu plăcere propuneri de bloguri invitate care se aliniază cu obiectivul nostru de conținut. Pentru a trimite un articol pentru examinare, vă rugăm să urmați acești pași:
-1. Contactați-ne prin intermediul formularului web de la adresa [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) pentru a vă exprima interesul de a fi guest blogging.
+1. Contactați-ne prin intermediul formularului web de la adresa [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) pentru a vă exprima interesul de a fi guest blogging.
2. Pregătiți articolul în format Markdown (md) sau HTML.
-3. Trimiteți o cerere de tip pull request pe depozitul nostru GitHub la adresa [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Trimiteți o cerere de tip pull request pe depozitul nostru GitHub la adresa [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Asigurați-vă că articolul dvs. include un frontmatter (metadate) valid, cu toate variabilele necesare, așa cum se arată în exemplul de mai jos:
@@ -122,7 +122,7 @@ Blogul invitat este un aranjament reciproc avantajos în care scriitorii au ocaz
- Apreciem înțelegerea și cooperarea dvs. în respectarea acestor linii directoare pentru a menține calitatea și relevanța conținutului pe SimeonOnSecurity.
-Așteptăm cu nerăbdare să primim contribuțiile dvs. valoroase și să vă ajutăm să ajungeți la un public mai larg cu cunoștințele dvs. Dacă aveți întrebări sau clarificări suplimentare, nu ezitați să ne contactați prin intermediul [webform](https://simeononsecurity.ch/contactus/)
+Așteptăm cu nerăbdare să primim contribuțiile dvs. valoroase și să vă ajutăm să ajungeți la un public mai larg cu cunoștințele dvs. Dacă aveți întrebări sau clarificări suplimentare, nu ezitați să ne contactați prin intermediul [webform](https://simeononsecurity.com/contactus/)
***Scriere fericită!
diff --git a/content/guest-posts/index.ru.md b/content/guest-posts/index.ru.md
index 143ef6adb6bbe..84ad0b3c9d6bb 100644
--- a/content/guest-posts/index.ru.md
+++ b/content/guest-posts/index.ru.md
@@ -11,11 +11,11 @@ coverCaption: "Делитесь своим опытом и знаниями с
Благодарим Вас за интерес к участию в работе нашего сайта! Мы приветствуем публикацию статей в гостевых блогах, которые соответствуют нашей тематике. Чтобы отправить статью на рассмотрение, пожалуйста, выполните следующие действия:
-1. Свяжитесь с нами через веб-форму по адресу [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/) чтобы выразить свою заинтересованность в ведении гостевого блога.
+1. Свяжитесь с нами через веб-форму по адресу [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/) чтобы выразить свою заинтересованность в ведении гостевого блога.
2. Подготовьте статью в формате Markdown (md) или HTML.
-3. Отправьте запрос на притяжение в наш репозиторий GitHub по адресу [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3. Отправьте запрос на притяжение в наш репозиторий GitHub по адресу [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4. Убедитесь, что статья содержит корректный frontmatter (метаданные) со всеми необходимыми переменными, как показано в примере ниже:
@@ -122,7 +122,7 @@ coverCaption: "Caption for your cover image."
- Мы благодарим вас за понимание и сотрудничество в соблюдении этих правил для поддержания качества и актуальности контента на сайте SimeonOnSecurity.
-Мы с нетерпением ждем ваших ценных материалов и будем рады помочь вам привлечь внимание широкой аудитории. Если у вас возникнут дополнительные вопросы или уточнения, пожалуйста, обращайтесь к нам по адресу [webform](https://simeononsecurity.ch/contactus/)
+Мы с нетерпением ждем ваших ценных материалов и будем рады помочь вам привлечь внимание широкой аудитории. Если у вас возникнут дополнительные вопросы или уточнения, пожалуйста, обращайтесь к нам по адресу [webform](https://simeononsecurity.com/contactus/)
***Счастливого письма!
diff --git a/content/guest-posts/index.zh.md b/content/guest-posts/index.zh.md
index 71c8f45282740..2e3fee8de209b 100644
--- a/content/guest-posts/index.zh.md
+++ b/content/guest-posts/index.zh.md
@@ -11,11 +11,11 @@ coverCaption: "通过客座博客与我们的社区分享您的专业知识和
感谢您有兴趣为我们的网站投稿!我们欢迎符合我们内容重点的特邀博客投稿。请按照以下步骤提交文章以供考虑:
-1.通过以下网站表格联系我们 [https://simeononsecurity.ch/contactus/](https://simeononsecurity.ch/contactus/)来表达您对客座博客的兴趣。
+1.通过以下网站表格联系我们 [https://simeononsecurity.com/contactus/](https://simeononsecurity.com/contactus/)来表达您对客座博客的兴趣。
2.以 Markdown (md) 或 HTML 格式准备文章。
-3.在我们的 GitHub 仓库中提交拉取请求,网址为 [https://github.com/simeononsecurity/simeononsecurity.ch](https://github.com/simeononsecurity/simeononsecurity.ch). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.ch/tree/master/content/authors)
+3.在我们的 GitHub 仓库中提交拉取请求,网址为 [https://github.com/simeononsecurity/simeononsecurity.com](https://github.com/simeononsecurity/simeononsecurity.com). If you don't have an author page already, create one following the example in [our author directory](https://github.com/simeononsecurity/simeononsecurity.com/tree/master/content/authors)
4.确保您的文章包含有效的 frontmatter(元数据)和所有必需的变量,如下例所示:
@@ -122,7 +122,7 @@ coverCaption: "Caption for your cover image."
- 我们感谢您的理解和合作,请遵守这些准则,以保持 SimeonOnSecurity 上内容的质量和相关性。
-我们期待收到您的宝贵意见,并帮助您将自己的见解传播给更多的受众。如果您有任何进一步的问题或说明,请随时通过以下方式联系我们 [webform](https://simeononsecurity.ch/contactus/)
+我们期待收到您的宝贵意见,并帮助您将自己的见解传播给更多的受众。如果您有任何进一步的问题或说明,请随时通过以下方式联系我们 [webform](https://simeononsecurity.com/contactus/)
***写作愉快!***
diff --git a/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md b/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md
index cfc1533218e5c..0caa7cc4b9622 100644
--- a/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md
+++ b/content/guides/automate-windows-11-installation-bypass-tpm-secure-boot-ram/index.en.md
@@ -19,7 +19,7 @@ Windows 11 introduces new system requirements, including the need for a TPM (Tru
### **Bypassing TPM, Secure Boot, and RAM Checks in Windows 11**
-Virtualized environments like VMware vSphere can utilize a virtual TPM ([vTPM](https://simeononsecurity.ch/guides/enable-virtual-trusted-platform-module-for-existing-virtual-machine/)) to emulate a TPM 2.0 device, satisfying the TPM requirement for Windows 11 installation. However, for scenarios where a vTPM is not available, the following **registry keys** can be used to bypass the checks during the installation process:
+Virtualized environments like VMware vSphere can utilize a virtual TPM ([vTPM](https://simeononsecurity.com/guides/enable-virtual-trusted-platform-module-for-existing-virtual-machine/)) to emulate a TPM 2.0 device, satisfying the TPM requirement for Windows 11 installation. However, for scenarios where a vTPM is not available, the following **registry keys** can be used to bypass the checks during the installation process:
- **BypassTPMCheck**: Skip TPM check.
- **BypassSecureBootCheck**: Skip Secure Boot check.
diff --git a/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md b/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md
index 809208d2fc222..60ff2c6b32840 100644
--- a/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md
+++ b/content/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/index.en.md
@@ -23,11 +23,11 @@ The ESP32 is a versatile microcontroller renowned for its WiFi and Bluetooth cap
### Alternate Instructions
**Want to use a linux distro or a raspberry pi?**
-Check out our guide on [**Setting up a NTRIP server on Linux**](https://simeononsecurity.ch/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
+Check out our guide on [**Setting up a NTRIP server on Linux**](https://simeononsecurity.com/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
### Looking for how to use this with Onocoy?
-Check out our guide on [**DIY Onocoy Ntrip Server and Reference Station Setup**](https://simeononsecurity.ch/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
+Check out our guide on [**DIY Onocoy Ntrip Server and Reference Station Setup**](https://simeononsecurity.com/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/)
### Recommended Hardware Components
Before we begin, let's take a look at the hardware components you'll need:
diff --git a/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md b/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md
index 8591d2ddc7478..4c83136d4b608 100644
--- a/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md
+++ b/content/guides/budget-friendly-10g-pfsense-build-hp-t640/index.en.md
@@ -67,7 +67,7 @@ To achieve 10 Gigabit Ethernet capabilities, you'll need to add 10g NICs to your
2. Create a bootable USB drive with the pfSense installer using tools like **Rufus** (Windows) or **dd** (Linux).
-3. Insert the USB drive into the HP t640, and follow the instructions from our guide on [installing pfSense on the HP t640](https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/) .
+3. Insert the USB drive into the HP t640, and follow the instructions from our guide on [installing pfSense on the HP t640](https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/) .
1. It's a bit different than the standard install. Please read the guide.
### **Configuring pfSense**
diff --git a/content/guides/docker-image-optimization-tips/index.en.md b/content/guides/docker-image-optimization-tips/index.en.md
index e551819fd8474..65b6d958727cf 100644
--- a/content/guides/docker-image-optimization-tips/index.en.md
+++ b/content/guides/docker-image-optimization-tips/index.en.md
@@ -15,7 +15,7 @@ ref: ["/articles/how-to-build-docker-containers-from-scratch","/articles/how-to-
**Optimizing Docker Images for Efficiency, Performance, and Security**
-In the realm of containerization, [**Docker**](https://simeononsecurity.ch/articles/how-to-build-docker-containers-from-scratch/) reigns supreme. **Docker images** serve as the foundation of containerized applications, encapsulating every element required for seamless operation, from code to essential libraries and dependencies. However, as applications expand and evolve, [**Docker images**](https://simeononsecurity.ch/articles/how-to-secure-your-docker-and-kubernetes-environment/) can bloat, resulting in inefficient and resource-intensive containers. In this comprehensive guide, we delve into expert techniques to meticulously optimize **Docker images**, enhancing efficiency, boosting performance, and fortifying security.
+In the realm of containerization, [**Docker**](https://simeononsecurity.com/articles/how-to-build-docker-containers-from-scratch/) reigns supreme. **Docker images** serve as the foundation of containerized applications, encapsulating every element required for seamless operation, from code to essential libraries and dependencies. However, as applications expand and evolve, [**Docker images**](https://simeononsecurity.com/articles/how-to-secure-your-docker-and-kubernetes-environment/) can bloat, resulting in inefficient and resource-intensive containers. In this comprehensive guide, we delve into expert techniques to meticulously optimize **Docker images**, enhancing efficiency, boosting performance, and fortifying security.
## **Introduction**
@@ -24,7 +24,7 @@ In the realm of containerization, [**Docker**](https://simeononsecurity.ch/artic
In the world of containerization, **Docker** has become a household name. **Docker images** are the building blocks of containerized applications. They encapsulate everything an application needs to run, from code to libraries and dependencies. However, as your application grows and evolves, so do your **Docker images**, often leading to bloated and inefficient containers. In this article, we'll explore techniques to optimize **Docker images** for efficiency, performance, and security.
______
-Explore more about [Docker optimization](https://simeononsecurity.ch/articles/how-to-build-docker-containers-from-scratch/) and [container security](https://simeononsecurity.ch/articles/how-to-secure-your-docker-and-kubernetes-environment/) in these informative articles:
+Explore more about [Docker optimization](https://simeononsecurity.com/articles/how-to-build-docker-containers-from-scratch/) and [container security](https://simeononsecurity.com/articles/how-to-secure-your-docker-and-kubernetes-environment/) in these informative articles:
- [How to Build Docker Containers from Scratch](/articles/how-to-build-docker-containers-from-scratch/)
- [How to Secure Your Docker and Kubernetes Environment](/articles/how-to-secure-your-docker-and-kubernetes-environment/)
diff --git a/content/guides/enhance-oracle-jre-8-security/index.en.md b/content/guides/enhance-oracle-jre-8-security/index.en.md
index 8612df01f81fd..a91252cb4fb38 100644
--- a/content/guides/enhance-oracle-jre-8-security/index.en.md
+++ b/content/guides/enhance-oracle-jre-8-security/index.en.md
@@ -121,7 +121,7 @@ An **accepted sites list** limits software execution to authorized sources, mini
2. Add each authorized site on a new line.
```ini
https://example.com
- https://simeononsecurity.ch
+ https://simeononsecurity.com
```
See an example of a known [working configuration for `exception.sites`](https://github.com/simeononsecurity/Oracle-JRE-8-STIG-Script/blob/master/Files/exception.sites).
diff --git a/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md b/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md
index c5485f50597f3..68b26e63f6d33 100644
--- a/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md
+++ b/content/guides/how-to-create-custom-ethernet-cables-guide/index.en.md
@@ -253,4 +253,4 @@ ______
Creating custom Ethernet cables is a rewarding DIY project, and it allows you to have full control over your network setup. Whether you're a tech enthusiast or need cables for specific applications, this guide will walk you through the process step by step. Don't hesitate to explore the world of custom Ethernet cables and enhance your networking capabilities.
-Lastly, if you've made it this far, you might be interested in reading our guide on [Setting up a Ubiquiti Unifi Home Network](https://simeononsecurity.ch/articles/the-ideal-ubiquiti-unifi-networking-setup-both-simple-and-advanced/).
\ No newline at end of file
+Lastly, if you've made it this far, you might be interested in reading our guide on [Setting up a Ubiquiti Unifi Home Network](https://simeononsecurity.com/articles/the-ideal-ubiquiti-unifi-networking-setup-both-simple-and-advanced/).
\ No newline at end of file
diff --git a/content/guides/secure-sshd-configurations-guide/index.en.md b/content/guides/secure-sshd-configurations-guide/index.en.md
index 9ae701a9e414e..5089209b9fa2a 100644
--- a/content/guides/secure-sshd-configurations-guide/index.en.md
+++ b/content/guides/secure-sshd-configurations-guide/index.en.md
@@ -23,7 +23,7 @@ In an **increasingly digital world**, the security of your server is paramount.
## **Understanding SSHD**
-[**SSH (Secure Shell)**](https://simeononsecurity.ch/articles/what-is-ssh/) is a **cryptographic network protocol** that allows **secure data communication**, **remote command-line login**, and other **secure network services**. **SSHD** is the **server component of SSH**, responsible for **authentication**, **encryption**, and **secure communication**. It's **vital to configure SSHD** properly to prevent **unauthorized access**.
+[**SSH (Secure Shell)**](https://simeononsecurity.com/articles/what-is-ssh/) is a **cryptographic network protocol** that allows **secure data communication**, **remote command-line login**, and other **secure network services**. **SSHD** is the **server component of SSH**, responsible for **authentication**, **encryption**, and **secure communication**. It's **vital to configure SSHD** properly to prevent **unauthorized access**.
### **Key Configuration Steps**
@@ -53,7 +53,7 @@ PermitRootLogin no
In the realm of **Secure SSHD Configurations**, robust authentication is the cornerstone of safeguarding your server. Let's delve into two pivotal methods for achieving this: **strong password policies** and **key-based authentication**.
-1. [**Strong Password Policies**](https://simeononsecurity.ch/articles/ten-essential-password-security-guidelines-to-follow): Start by enforcing stringent password rules. Craft passwords that are lengthy and encompass a mixture of upper and lower-case letters, numbers, and special characters. Steer clear of easily guessable information, such as birthdays or common words.
+1. [**Strong Password Policies**](https://simeononsecurity.com/articles/ten-essential-password-security-guidelines-to-follow): Start by enforcing stringent password rules. Craft passwords that are lengthy and encompass a mixture of upper and lower-case letters, numbers, and special characters. Steer clear of easily guessable information, such as birthdays or common words.
Example: A formidable password might look like "P@$$w0rdS3cureSSH."
@@ -140,13 +140,13 @@ These configurations prioritize stronger encryption and key exchange algorithms,
### **Protecting SSHD from Threats**
#### **Brute Force Attacks**
-SSH is a **common target** for **brute force attacks** where attackers try to guess passwords **repeatedly**. Implementing [**strong password policies**](https://simeononsecurity.ch/articles/ten-essential-password-security-guidelines-to-follow/), using [**key-based authentication**](https://simeononsecurity.ch/articles/what-are-the-diferent-kinds-of-factors-in-mfa/), and **monitoring logs** can help thwart these attacks.
+SSH is a **common target** for **brute force attacks** where attackers try to guess passwords **repeatedly**. Implementing [**strong password policies**](https://simeononsecurity.com/articles/ten-essential-password-security-guidelines-to-follow/), using [**key-based authentication**](https://simeononsecurity.com/articles/what-are-the-diferent-kinds-of-factors-in-mfa/), and **monitoring logs** can help thwart these attacks.
#### **DDoS Attacks**
**Distributed Denial of Service (DDoS) attacks** can overwhelm your server, making it unresponsive. Use tools like **iptables** or **fail2ban** to mitigate the impact of DDoS attacks on your SSHD service.
#### **Zero-Day Exploits**
-Stay informed about SSHD vulnerabilities and [**patch**](https://simeononsecurity.ch/guides/automate-linux-patching-and-updates-with-ansible/) them as soon as updates become available. Government agencies such as the [**National Institute of Standards and Technology (NIST)**](https://www.nist.gov/) often release guidelines on secure configurations.
+Stay informed about SSHD vulnerabilities and [**patch**](https://simeononsecurity.com/guides/automate-linux-patching-and-updates-with-ansible/) them as soon as updates become available. Government agencies such as the [**National Institute of Standards and Technology (NIST)**](https://www.nist.gov/) often release guidelines on secure configurations.
## **Conclusion**
diff --git a/content/jobs/index.en.html b/content/jobs/index.en.html
index 7f3340ec2c225..e8c0c4fe13de7 100644
--- a/content/jobs/index.en.html
+++ b/content/jobs/index.en.html
@@ -19,7 +19,7 @@ Description:
Requirements:
How to Apply:
-If you are passionate about creating compelling videos and excited about the opportunity to grow with us, please apply through our Contact page. Include brief message explaining why you are interested in this position.
+If you are passionate about creating compelling videos and excited about the opportunity to grow with us, please apply through our Contact page. Include brief message explaining why you are interested in this position.
We look forward to hearing from you and exploring the world of video creation together!
Social Media Manager (Unpaid Intern Position)
Requirements:
How to Apply:
-If you are passionate about social media and excited about the opportunity to gain practical experience, please apply through our Contact page. Include brief message explaining why you are interested in this position.
+If you are passionate about social media and excited about the opportunity to gain practical experience, please apply through our Contact page. Include brief message explaining why you are interested in this position.
We look forward to receiving your application and embarking on a rewarding social media journey together!
\ No newline at end of file diff --git a/content/jobs/pageschema.html b/content/jobs/pageschema.html index fd91ce305eb6f..25cdd47a225e7 100644 --- a/content/jobs/pageschema.html +++ b/content/jobs/pageschema.html @@ -36,12 +36,12 @@ "hiringOrganization": { "@type": "Organization", "name": "SimeonOnSecurity", - "url": "https://simeononsecurity.ch", - "logo": "https://simeononsecurity.ch/img/banner.png" + "url": "https://simeononsecurity.com", + "logo": "https://simeononsecurity.com/img/banner.png" }, "datePosted": "2023-08-01", "validThrough": "2024-09-01", - "url": "https://simeononsecurity.ch/jobs#video-creator-editor", + "url": "https://simeononsecurity.com/jobs#video-creator-editor", "directApply": "true" } }, @@ -77,12 +77,12 @@ "hiringOrganization": { "@type": "Organization", "name": "SimeonOnSecurity", - "url": "https://simeononsecurity.ch", - "logo": "https://simeononsecurity.ch/img/banner.png" + "url": "https://simeononsecurity.com", + "logo": "https://simeononsecurity.com/img/banner.png" }, "datePosted": "2023-08-01", "validThrough": "2024-09-01", - "url": "https://simeononsecurity.ch/jobs#social-media-manager", + "url": "https://simeononsecurity.com/jobs#social-media-manager", "directApply": "true" } } diff --git a/content/network-plus/mastering-network-ports-protocols-guide-secure-communication-networking/index.en.md b/content/network-plus/mastering-network-ports-protocols-guide-secure-communication-networking/index.en.md index 8916ed755def2..ebb838428409b 100644 --- a/content/network-plus/mastering-network-ports-protocols-guide-secure-communication-networking/index.en.md +++ b/content/network-plus/mastering-network-ports-protocols-guide-secure-communication-networking/index.en.md @@ -15,7 +15,7 @@ coverCaption: "Secure communication and efficient networking for enhanced produc ## Introduction -In the world of computer networks, ports, protocols, and network services play a crucial role in enabling communication between devices. Understanding these concepts is essential for network administrators, IT professionals, and anyone interested in the workings of computer networks. This article will explain common ports and protocols, their applications, and introduce encrypted alternatives for secure communication. We will also delve into IP protocol types and explore the difference between connection-oriented and [connectionless protocols](https://simeononsecurity.ch/articles/difference-connection-oriented-connectionless-communication/). +In the world of computer networks, ports, protocols, and network services play a crucial role in enabling communication between devices. Understanding these concepts is essential for network administrators, IT professionals, and anyone interested in the workings of computer networks. This article will explain common ports and protocols, their applications, and introduce encrypted alternatives for secure communication. We will also delve into IP protocol types and explore the difference between connection-oriented and [connectionless protocols](https://simeononsecurity.com/articles/difference-connection-oriented-connectionless-communication/). ## Explaining Common Ports and Protocols diff --git a/content/network-plus/network-plus-course-network-hardening-techniques/index.en.md b/content/network-plus/network-plus-course-network-hardening-techniques/index.en.md index eef25da741a70..c1aebdae41fbf 100644 --- a/content/network-plus/network-plus-course-network-hardening-techniques/index.en.md +++ b/content/network-plus/network-plus-course-network-hardening-techniques/index.en.md @@ -61,7 +61,7 @@ Implementing **access control** measures for SNMP is crucial. Organizations shou ### SNMP Trap Filtering -Filtering [**SNMP traps**](https://simeononsecurity.ch/network-plus/network-plus-course-performance-monitoring-management/) allows organizations to selectively process and respond to specific events. By configuring trap filters, network administrators can reduce the impact of unnecessary SNMP traffic and focus on critical events. +Filtering [**SNMP traps**](https://simeononsecurity.com/network-plus/network-plus-course-performance-monitoring-management/) allows organizations to selectively process and respond to specific events. By configuring trap filters, network administrators can reduce the impact of unnecessary SNMP traffic and focus on critical events. ______ diff --git a/content/network-plus/network-plus-course-troubleshooting-general-networking-issues/index.en.md b/content/network-plus/network-plus-course-troubleshooting-general-networking-issues/index.en.md index 44b001a3165eb..0a5e1db8c35f5 100644 --- a/content/network-plus/network-plus-course-troubleshooting-general-networking-issues/index.en.md +++ b/content/network-plus/network-plus-course-troubleshooting-general-networking-issues/index.en.md @@ -69,7 +69,7 @@ Misconfigured **host-based** or **network-based firewall settings** can block re ### BYOD Challenges and Licensed Feature Issues -[**BYOD challenges**](https://simeononsecurity.ch/articles/the-challenges-and-opportunities-of-implementing-a-byod-policy/) and **licensed feature issues** can arise in networks where Bring Your Own Device (BYOD) policies are implemented or when specific licensed features are utilized. Proper policy enforcement and license management mitigate these challenges. +[**BYOD challenges**](https://simeononsecurity.com/articles/the-challenges-and-opportunities-of-implementing-a-byod-policy/) and **licensed feature issues** can arise in networks where Bring Your Own Device (BYOD) policies are implemented or when specific licensed features are utilized. Proper policy enforcement and license management mitigate these challenges. ### Network Performance Issues diff --git a/content/other/bypassing-the-bgw320-att-fiber-modem-router/index.en.md b/content/other/bypassing-the-bgw320-att-fiber-modem-router/index.en.md index 5a40ab1fb2fd6..783614d3ef51e 100644 --- a/content/other/bypassing-the-bgw320-att-fiber-modem-router/index.en.md +++ b/content/other/bypassing-the-bgw320-att-fiber-modem-router/index.en.md @@ -8,7 +8,7 @@ tags: ["COTS ONT", "BGW-320", "Azores", "fiber", "network", "XGS-PON", "Ethernet cover: "/img/cover/A_cartoon_technician_holding_a_COTS_ONT_with_a_fiber_cable.png" coverAlt: "A cartoon technician holding a COTS ONT with a fiber cable in the background." coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/bypassing-the-bgw320-att-fiber-modem-router/" +canonical: "https://simeononsecurity.com/guides/bypassing-the-bgw320-att-fiber-modem-router/" --- ## How to Bypass the BGW-320 and Using an Azores WAG-D20 diff --git a/content/other/creating-profitable-low-powered-crypto-miners/index.en.md b/content/other/creating-profitable-low-powered-crypto-miners/index.en.md index 137ba0cb008b4..fb1fb9d65566b 100644 --- a/content/other/creating-profitable-low-powered-crypto-miners/index.en.md +++ b/content/other/creating-profitable-low-powered-crypto-miners/index.en.md @@ -90,7 +90,7 @@ docker run -d \ --cleanup ``` -### [Install Bitping](https://simeononsecurity.ch/other/install-bitping-easily-using-docker/): +### [Install Bitping](https://simeononsecurity.com/other/install-bitping-easily-using-docker/): [*Bitping is a website monitoring and performance optimization solution that provides real-time, real user monitoring and instant feedback on downtime or degraded performance, with stress testing and benchmarking capabilities, dynamic rerouting and reprovisioning powered by a distributed network intelligence layer, and integration with existing workflows through webhooks.*](https://bitping.com) Bitping offers you the ability to get paid out in Solana for providing a node for businesses to run lightweight network tests from your network. @@ -115,7 +115,7 @@ docker run --net host --name bitping -td --mount type=bind,source="$HOME/.bitpin ``` -### [Install Earn App](https://simeononsecurity.ch/other/install-earnapp-easily-using-docker/): +### [Install Earn App](https://simeononsecurity.com/other/install-earnapp-easily-using-docker/): [*Take advantage of the time your devices are left idle by getting paid for your device’s unused resources*](https://earnapp.com/i/GCL9QzB5) Earn app lets you share your internet as a VPN service for a surprising amount of rewards. Averages about $5 month per node per residential IP. Offers payouts via paypal and amazon gift cards. @@ -137,7 +137,7 @@ docker run -td --name earnapp --privileged -v /sys/fs/cgroup:/sys/fs/cgroup:ro - #### Video Tutorial: {{< youtube id="tt499o0OjGU" >}} -### [Install Honey Gain](https://simeononsecurity.ch/other/install-honeygain-easily-using-docker/): +### [Install Honey Gain](https://simeononsecurity.com/other/install-honeygain-easily-using-docker/): [*Passive Income – Effortlessly with Honeygain, you can make money by simply sharing your Internet. Start earning now.*](https://r.honeygain.me/DAVID07A75) Honey Gain lets you share your internet as a VPN service for a surprising amount of rewards. Averages about $5 month per node per residential IP. Payouts can be complicated. Read into it further before deciding to use this container @@ -157,7 +157,7 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E #### Video Tutorial: {{< youtube id="Wd11M0nSy1k" >}} -### [Install PawnsApp](https://simeononsecurity.ch/other/install-pawnsapp-easily-using-docker/): +### [Install PawnsApp](https://simeononsecurity.com/other/install-pawnsapp-easily-using-docker/): [*Make passive money online by completing surveys and sharing your internet *](https://pawns.app/?r=2092882) Pawns app, again similar to the others listed here offer to pay you for sharing your internet. Minimum payout is $5. Average payout is $0.50 per month per node per IP. @@ -176,7 +176,7 @@ docker run -td --name pawnsapp --restart=on-failure:5 iproyal/pawns-cli:latest - -### [Install Repocket](https://simeononsecurity.ch/other/install-repocket-easily-using-docker/): +### [Install Repocket](https://simeononsecurity.com/other/install-repocket-easily-using-docker/): [*Get Paid For Your Unused Internet*](https://link.repocket.co/raqc) Similar to other offerings here. Minimum $20 Payout. Payouts can be complicated. Research for yourself to see if you want to use this service. Payouts average about $1 per node per box a month. @@ -191,7 +191,7 @@ docker run -td --name repocket -e RP_EMAIL=your@email.com -e RP_API_KEY=yourapik #### Video Tutorial: {{< youtube id="171gWknfAbY" >}} -### [Install Traff Monetizer](https://simeononsecurity.ch/other/install-traff-monetizer-easily-using-docker/): +### [Install Traff Monetizer](https://simeononsecurity.com/other/install-traff-monetizer-easily-using-docker/): [*Share your internet connection and make money online*](https://traffmonetizer.com/?aff=1389828&utm_source=traffmonetizerdockerguide) Similar to EarnApp and HoneyGain, TraffMonetizer pays you to share your internet. Averages about $2 a month per node per IP. Only offers payouts in BTC. @@ -207,7 +207,7 @@ Copy the following string and append your token that you got from the dashboard docker run -td --name traffmonetizer traffmonetizer/cli start accept --token ``` -### [Install Mysterium](https://simeononsecurity.ch/other/install-mysterium-easily-using-docker/): +### [Install Mysterium](https://simeononsecurity.com/other/install-mysterium-easily-using-docker/): [Mysterium](https://www.mysterium.network/) is a decentralized VPN and webscraping service built on the Etherium and Polygon blockchains. Payments average anywhere from $1-$20 a month depending on multiple factors per node per IP. Costs $1.XX to setup a node for activation. Payouts in MYST token. diff --git a/content/other/install-bitping-easily-using-docker/index.de.md b/content/other/install-bitping-easily-using-docker/index.de.md index 997832ca0fe07..7c31b3139dfbc 100644 --- a/content/other/install-bitping-easily-using-docker/index.de.md +++ b/content/other/install-bitping-easily-using-docker/index.de.md @@ -22,7 +22,7 @@ Um mit Bitping zu beginnen, müssen Sie ein Konto auf der [Bitping website](http ### Docker installieren -Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installieren Sie den Docker-Container @@ -64,7 +64,7 @@ Herzlichen Glückwunsch! Sie haben Bitping erfolgreich auf Ihrem System installi Weitere Informationen und eine ausführliche Dokumentation finden Sie auf der [Bitping website](https://bitping.com) und verweisen auf ihre offiziellen Quellen. -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Referenzen:** diff --git a/content/other/install-bitping-easily-using-docker/index.en.md b/content/other/install-bitping-easily-using-docker/index.en.md index 4be6021654971..dee65f1d7aa95 100644 --- a/content/other/install-bitping-easily-using-docker/index.en.md +++ b/content/other/install-bitping-easily-using-docker/index.en.md @@ -22,7 +22,7 @@ To get started with Bitping, you need to create an account on the [Bitping websi ### Installing Docker -Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). ### Install the Docker container @@ -64,7 +64,7 @@ Congratulations! You have successfully installed and set up Bitping on your syst For more information and detailed documentation, visit the [Bitping website](https://bitping.com) and refer to their official resources. -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **References:** diff --git a/content/other/install-bitping-easily-using-docker/index.es.md b/content/other/install-bitping-easily-using-docker/index.es.md index 11d557195fc2f..58fc3cb753fe7 100644 --- a/content/other/install-bitping-easily-using-docker/index.es.md +++ b/content/other/install-bitping-easily-using-docker/index.es.md @@ -22,7 +22,7 @@ Para empezar a utilizar Bitping, debe crear una cuenta en el sitio web [Bitping ### Instalación de Docker -Aprenda [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Aprenda [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalar el contenedor Docker @@ -64,7 +64,7 @@ Este comando iniciará el contenedor Bitping en segundo plano, asegurándose de Para más información y documentación detallada, visite la página [Bitping website](https://bitping.com) y consulte sus recursos oficiales. -Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Referencias:** diff --git a/content/other/install-bitping-easily-using-docker/index.fr.md b/content/other/install-bitping-easily-using-docker/index.fr.md index 32da05bdeb7b2..9b3efbc3648e6 100644 --- a/content/other/install-bitping-easily-using-docker/index.fr.md +++ b/content/other/install-bitping-easily-using-docker/index.fr.md @@ -22,7 +22,7 @@ Pour commencer à utiliser Bitping, vous devez créer un compte sur le site web ### Installation de Docker -Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installer le conteneur Docker @@ -64,7 +64,7 @@ Félicitations ! Vous avez installé et configuré Bitping avec succès sur votr Pour plus d'informations et une documentation détaillée, visitez le site [Bitping website](https://bitping.com) et se référer à leurs ressources officielles. -Une fois que vous avez terminé, vous devez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous avez terminé, vous devez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Références:** diff --git a/content/other/install-bitping-easily-using-docker/index.it.md b/content/other/install-bitping-easily-using-docker/index.it.md index 1da13b4b41d09..e6a6324a7f1a4 100644 --- a/content/other/install-bitping-easily-using-docker/index.it.md +++ b/content/other/install-bitping-easily-using-docker/index.it.md @@ -22,7 +22,7 @@ Per iniziare a lavorare con Bitping, è necessario creare un account su [Bitping ### Installazione di Docker -Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installare il contenitore Docker @@ -64,7 +64,7 @@ Congratulazioni! Avete installato e configurato con successo Bitping sul vostro Per ulteriori informazioni e documentazione dettagliata, visitare il sito [Bitping website](https://bitping.com) e fare riferimento alle loro risorse ufficiali. -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Riferimenti:** diff --git a/content/other/install-bitping-easily-using-docker/index.ja.md b/content/other/install-bitping-easily-using-docker/index.ja.md index db9c8be411ebc..5abedcb91ff8c 100644 --- a/content/other/install-bitping-easily-using-docker/index.ja.md +++ b/content/other/install-bitping-easily-using-docker/index.ja.md @@ -22,7 +22,7 @@ Bitpingを始めるには、以下のページでアカウントを作成する ### Dockerのインストール -学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Dockerコンテナをインストールする @@ -64,7 +64,7 @@ docker run --net host --name bitping -td --mount type=bind,source="$HOME/.bitpin 詳細な情報および詳細なドキュメントについては、以下のサイトをご覧ください。 [Bitping website](https://bitping.com)と、その公式リソースを参照することができます。 -一度、以下のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +一度、以下のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **参考文献:**1 diff --git a/content/other/install-bitping-easily-using-docker/index.nl.md b/content/other/install-bitping-easily-using-docker/index.nl.md index 664793cf115cd..1d1c31456c473 100644 --- a/content/other/install-bitping-easily-using-docker/index.nl.md +++ b/content/other/install-bitping-easily-using-docker/index.nl.md @@ -22,7 +22,7 @@ Om te beginnen met Bitping moet u een account aanmaken op de [Bitping website](h ### Docker installeren -Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installeer de Docker container @@ -64,7 +64,7 @@ Gefeliciteerd! U hebt Bitping met succes geïnstalleerd en ingesteld op uw syste Voor meer informatie en gedetailleerde documentatie, bezoek de [Bitping website](https://bitping.com) en verwijzen naar hun officiële bronnen. -Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Referenties:** diff --git a/content/other/install-bitping-easily-using-docker/index.pl.md b/content/other/install-bitping-easily-using-docker/index.pl.md index 0863a398365c3..eebd29e6b25d0 100644 --- a/content/other/install-bitping-easily-using-docker/index.pl.md +++ b/content/other/install-bitping-easily-using-docker/index.pl.md @@ -22,7 +22,7 @@ Aby rozpocząć korzystanie z Bitping, należy utworzyć konto na stronie [Bitpi ### Instalacja Dockera -Dowiedz się [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Dowiedz się [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalacja kontenera Docker @@ -64,7 +64,7 @@ Gratulacje! Pomyślnie zainstalowałeś i skonfigurowałeś Bitping w swoim syst Więcej informacji i szczegółową dokumentację można znaleźć na stronie [Bitping website](https://bitping.com) i odnieść się do ich oficjalnych zasobów. -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Referencje:** diff --git a/content/other/install-bitping-easily-using-docker/index.ro.md b/content/other/install-bitping-easily-using-docker/index.ro.md index 9977d75247386..e315902fe1bd3 100644 --- a/content/other/install-bitping-easily-using-docker/index.ro.md +++ b/content/other/install-bitping-easily-using-docker/index.ro.md @@ -22,7 +22,7 @@ Pentru a începe cu Bitping, trebuie să vă creați un cont pe site-ul [Bitping ### Instalarea Docker -Învățați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Învățați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalați containerul Docker @@ -64,7 +64,7 @@ Felicitări! Ați instalat și configurat cu succes Bitping pe sistemul dumneavo Pentru mai multe informații și documentație detaliată, vizitați pagina [Bitping website](https://bitping.com) și să se refere la resursele oficiale ale acestora. -După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Referințe:** diff --git a/content/other/install-bitping-easily-using-docker/index.ru.md b/content/other/install-bitping-easily-using-docker/index.ru.md index b97ca59435d40..e5c10f09438aa 100644 --- a/content/other/install-bitping-easily-using-docker/index.ru.md +++ b/content/other/install-bitping-easily-using-docker/index.ru.md @@ -22,7 +22,7 @@ coverCaption: "" ### Установка Docker -Изучить [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Изучить [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Установите контейнер Docker @@ -64,7 +64,7 @@ docker run --net host --name bitping -td --mount type=bind,source="$HOME/.bitpin Для получения дополнительной информации и подробной документации посетите сайт [Bitping website](https://bitping.com) и обращаться к их официальным ресурсам. -По окончании работы следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +По окончании работы следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **Ссылки:** diff --git a/content/other/install-bitping-easily-using-docker/index.zh.md b/content/other/install-bitping-easily-using-docker/index.zh.md index 4b671bda0f381..b7d7ff980f00c 100644 --- a/content/other/install-bitping-easily-using-docker/index.zh.md +++ b/content/other/install-bitping-easily-using-docker/index.zh.md @@ -22,7 +22,7 @@ coverCaption: "" ### 安装 Docker -学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 安装 Docker 容器 @@ -64,7 +64,7 @@ docker run --net host --name bitping -td --mount type=bind,source="$HOME/.bitpin 欲了解更多信息和详细文档,请访问 [Bitping website](https://bitping.com)并参考其官方资源。 -完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) **参考文献:** diff --git a/content/other/install-earnapp-easily-using-docker/index.de.md b/content/other/install-earnapp-easily-using-docker/index.de.md index 7ae1f2f688260..db2f21c9131c8 100644 --- a/content/other/install-earnapp-easily-using-docker/index.de.md +++ b/content/other/install-earnapp-easily-using-docker/index.de.md @@ -26,7 +26,7 @@ Folgen Sie der [installation instructions](https://help.earnapp.com/hc/en-us/art ### Docker installieren -Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installieren Sie den Docker-Container Um die Earn App mit Docker zu installieren, gehen Sie folgendermaßen vor: @@ -53,7 +53,7 @@ Sehen Sie sich dieses Video-Tutorial an, das Sie durch den Installationsprozess Zusammenfassend lässt sich sagen, dass Earn App eine hervorragende Möglichkeit bietet, Ihre ungenutzten Geräte zu monetarisieren und durch die gemeinsame Nutzung Ihres Internets als VPN-Dienst Geld zu verdienen. Indem Sie die ungenutzten Ressourcen Ihres Geräts nutzen, können Sie mit einer privaten IP ein passives Einkommen von durchschnittlich 5 US-Dollar pro Monat und Knotenpunkt erzielen. Um loszulegen, erstellen Sie ein Konto bei Earn App, folgen Sie den Installationsanweisungen und beginnen Sie noch heute, Prämien zu verdienen. Machen Sie das Beste aus Ihren ungenutzten Geräten und verwandeln Sie sie mühelos in eine wertvolle Einnahmequelle. -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referenzen: diff --git a/content/other/install-earnapp-easily-using-docker/index.en.md b/content/other/install-earnapp-easily-using-docker/index.en.md index 9002d30afd0d4..9296f473f1261 100644 --- a/content/other/install-earnapp-easily-using-docker/index.en.md +++ b/content/other/install-earnapp-easily-using-docker/index.en.md @@ -26,7 +26,7 @@ Follow the [installation instructions](https://help.earnapp.com/hc/en-us/article ### Install Docker -Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). ### Install the Docker Container To install the Earn App using Docker, follow these steps: @@ -53,7 +53,7 @@ Watch this video tutorial to guide you through the Earn App installation process In conclusion, Earn App presents an excellent opportunity to monetize your idle devices and earn rewards by sharing your internet as a VPN service. By leveraging your device's unused resources, you can generate passive income with a residential IP, averaging $5 per month per node. To get started, create an account at Earn App, follow the installation instructions, and begin earning rewards today. Make the most of your idle devices and turn them into a valuable source of income effortlessly. -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## References: diff --git a/content/other/install-earnapp-easily-using-docker/index.es.md b/content/other/install-earnapp-easily-using-docker/index.es.md index 80018175eb95e..9b217cf3d33f9 100644 --- a/content/other/install-earnapp-easily-using-docker/index.es.md +++ b/content/other/install-earnapp-easily-using-docker/index.es.md @@ -26,7 +26,7 @@ Siga las instrucciones de [installation instructions](https://help.earnapp.com/h ### Instalar Docker -Aprenda [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Aprenda [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalación del contenedor Docker Para instalar la aplicación Earn App utilizando Docker, siga estos pasos: @@ -53,7 +53,7 @@ Vea este vídeo tutorial que le guiará a través del proceso de instalación de En conclusión, Earn App presenta una excelente oportunidad para monetizar tus dispositivos inactivos y ganar recompensas compartiendo tu Internet como un servicio VPN. Aprovechando los recursos no utilizados de tu dispositivo, puedes generar ingresos pasivos con una IP residencial, con una media de 5 dólares al mes por nodo. Para empezar, crea una cuenta en Earn App, sigue las instrucciones de instalación y empieza a ganar recompensas hoy mismo. Saca el máximo partido a tus dispositivos inactivos y conviértelos en una valiosa fuente de ingresos sin esfuerzo. -Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencias: diff --git a/content/other/install-earnapp-easily-using-docker/index.fr.md b/content/other/install-earnapp-easily-using-docker/index.fr.md index dcdc5aff80fc0..d0d8d700fe753 100644 --- a/content/other/install-earnapp-easily-using-docker/index.fr.md +++ b/content/other/install-earnapp-easily-using-docker/index.fr.md @@ -26,7 +26,7 @@ Suivez les instructions de l'application [installation instructions](https://hel ### Installer Docker -Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installer le conteneur Docker Pour installer l'application Earn à l'aide de Docker, suivez ces étapes : @@ -53,7 +53,7 @@ Regardez ce tutoriel vidéo qui vous guidera dans le processus d'installation de En conclusion, Earn App présente une excellente opportunité de monétiser vos appareils inutilisés et de gagner des récompenses en partageant votre Internet en tant que service VPN. En exploitant les ressources inutilisées de votre appareil, vous pouvez générer un revenu passif avec une IP résidentielle, en moyenne 5 $ par mois par nœud. Pour commencer, créez un compte sur Earn App, suivez les instructions d'installation et commencez à gagner des récompenses dès aujourd'hui. Tirez le meilleur parti de vos appareils inutilisés et transformez-les en une précieuse source de revenus sans effort. -Une fois que vous aurez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous aurez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Références : diff --git a/content/other/install-earnapp-easily-using-docker/index.it.md b/content/other/install-earnapp-easily-using-docker/index.it.md index 15a75fb26c15a..36241d6dc8193 100644 --- a/content/other/install-earnapp-easily-using-docker/index.it.md +++ b/content/other/install-earnapp-easily-using-docker/index.it.md @@ -26,7 +26,7 @@ Seguire la procedura [installation instructions](https://help.earnapp.com/hc/en- ### Installare Docker -Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installare il contenitore Docker Per installare l'applicazione Earn utilizzando Docker, seguire i seguenti passaggi: @@ -53,7 +53,7 @@ Guardate questo video tutorial che vi guiderà nel processo di installazione di In conclusione, Earn App rappresenta un'eccellente opportunità per monetizzare i vostri dispositivi inattivi e guadagnare ricompense condividendo il vostro internet come servizio VPN. Sfruttando le risorse inutilizzate del vostro dispositivo, potete generare un reddito passivo con un IP residenziale, con una media di 5 dollari al mese per nodo. Per iniziare, create un account su Earn App, seguite le istruzioni di installazione e iniziate a guadagnare ricompense oggi stesso. Sfruttate al massimo i vostri dispositivi inattivi e trasformateli in una preziosa fonte di reddito senza alcuno sforzo. -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Riferimenti: diff --git a/content/other/install-earnapp-easily-using-docker/index.ja.md b/content/other/install-earnapp-easily-using-docker/index.ja.md index 18bff46871810..032280fdaaa5e 100644 --- a/content/other/install-earnapp-easily-using-docker/index.ja.md +++ b/content/other/install-earnapp-easily-using-docker/index.ja.md @@ -26,7 +26,7 @@ Earn Appの仕組みと、今日からできるリワードの獲得方法につ ### Dockerのインストール -学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Dockerコンテナをインストールする Docker を使用して Earn App をインストールするには、以下の手順を実行します: @@ -53,7 +53,7 @@ docker run -td --name earnapp --privileged -v /sys/fs/cgroup:/sys/fs/cgroup:ro - 結論として、Earn Appは、遊休デバイスを収益化し、VPNサービスとしてインターネットを共有することで報酬を得る優れた機会を提供します。デバイスの未使用リソースを活用することで、住宅用IPで受動的な収入を得ることができ、1ノードあたり月平均5ドルの収入を得ることができます。まずは、Earn Appでアカウントを作成し、インストール手順に従って、今日から報酬を獲得してください。遊休デバイスを有効活用して、楽に貴重な収入源に変えてしまいましょう。 -インストールが完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +インストールが完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## リファレンス diff --git a/content/other/install-earnapp-easily-using-docker/index.nl.md b/content/other/install-earnapp-easily-using-docker/index.nl.md index 9626848b1ca21..d04440564014a 100644 --- a/content/other/install-earnapp-easily-using-docker/index.nl.md +++ b/content/other/install-earnapp-easily-using-docker/index.nl.md @@ -26,7 +26,7 @@ Volg de [installation instructions](https://help.earnapp.com/hc/en-us/articles/1 ### Docker installeren -Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installeer de Docker Container Volg deze stappen om de Earn App met behulp van Docker te installeren: @@ -53,7 +53,7 @@ Bekijk deze videohandleiding om u door het Earn App installatieproces te leiden: Kortom, Earn App biedt een uitstekende mogelijkheid om uw ongebruikte apparaten te gelde te maken en beloningen te verdienen door uw internet te delen als een VPN-dienst. Door gebruik te maken van de ongebruikte bronnen van uw apparaat, kunt u passieve inkomsten genereren met een residentieel IP, gemiddeld $5 per maand per node. Maak om te beginnen een account aan bij Earn App, volg de installatie-instructies en begin vandaag nog met het verdienen van beloningen. Haal het meeste uit uw inactieve apparaten en verander ze moeiteloos in een waardevolle bron van inkomsten. -Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referenties: diff --git a/content/other/install-earnapp-easily-using-docker/index.pl.md b/content/other/install-earnapp-easily-using-docker/index.pl.md index e7a6af9333646..0cb03dbaacf9d 100644 --- a/content/other/install-earnapp-easily-using-docker/index.pl.md +++ b/content/other/install-earnapp-easily-using-docker/index.pl.md @@ -26,7 +26,7 @@ Postępuj zgodnie z instrukcjami [installation instructions](https://help.earnap ### Zainstaluj Dockera -Nauka [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Nauka [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalacja kontenera Docker Aby zainstalować aplikację Earn przy użyciu Dockera, wykonaj następujące kroki: @@ -53,7 +53,7 @@ Obejrzyj ten samouczek wideo, który przeprowadzi Cię przez proces instalacji a Podsumowując, aplikacja Earn App stanowi doskonałą okazję do zarabiania na nieużywanych urządzeniach i zarabiania na udostępnianiu Internetu jako usługi VPN. Wykorzystując niewykorzystane zasoby urządzenia, możesz generować pasywny dochód z mieszkaniowego adresu IP, średnio 5 USD miesięcznie na węzeł. Aby rozpocząć, utwórz konto w Earn App, postępuj zgodnie z instrukcjami instalacji i zacznij zdobywać nagrody już dziś. Wykorzystaj w pełni swoje nieużywane urządzenia i zamień je w cenne źródło dochodu bez wysiłku. -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencje: diff --git a/content/other/install-earnapp-easily-using-docker/index.ro.md b/content/other/install-earnapp-easily-using-docker/index.ro.md index edd740cf08f84..7bced13dc6251 100644 --- a/content/other/install-earnapp-easily-using-docker/index.ro.md +++ b/content/other/install-earnapp-easily-using-docker/index.ro.md @@ -26,7 +26,7 @@ Urmați instrucțiunile [installation instructions](https://help.earnapp.com/hc/ ### Instalați Docker -Învățați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Învățați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalați containerul Docker Pentru a instala aplicația Earn App utilizând Docker, urmați acești pași: @@ -53,7 +53,7 @@ Urmăriți acest tutorial video pentru a vă ghida prin procesul de instalare a În concluzie, Earn App prezintă o oportunitate excelentă de a vă monetiza dispozitivele inactive și de a câștiga recompense prin partajarea internetului dvs. ca serviciu VPN. Prin valorificarea resurselor nefolosite ale dispozitivului dvs. puteți genera venituri pasive cu un IP rezidențial, în medie de 5 USD pe lună pe nod. Pentru a începe, creați-vă un cont la Earn App, urmați instrucțiunile de instalare și începeți să câștigați recompense chiar astăzi. Profitați la maximum de dispozitivele dvs. inactive și transformați-le într-o sursă valoroasă de venit fără efort. -După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referințe: diff --git a/content/other/install-earnapp-easily-using-docker/index.ru.md b/content/other/install-earnapp-easily-using-docker/index.ru.md index 28d2c9ef9a5c8..b2e0abe541025 100644 --- a/content/other/install-earnapp-easily-using-docker/index.ru.md +++ b/content/other/install-earnapp-easily-using-docker/index.ru.md @@ -26,7 +26,7 @@ coverCaption: "Монетизация неработающих устройст ### Установите Docker -Изучить [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Изучить [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Установка контейнера Docker Чтобы установить приложение Earn App с помощью Docker, выполните следующие действия: @@ -53,7 +53,7 @@ docker run -td --name earnapp --privileged -v /sys/fs/cgroup:/sys/fs/cgroup:ro - В заключение можно сказать, что приложение Earn App представляет собой отличную возможность монетизировать неиспользуемые устройства и получать вознаграждение, предоставляя свой Интернет в качестве VPN-сервиса. Используя неиспользуемые ресурсы своего устройства, вы можете получать пассивный доход с домашнего IP-адреса, составляющий в среднем 5 долл. в месяц на узел. Чтобы начать работу, создайте учетную запись на сайте Earn App, следуйте инструкциям по установке и начните получать вознаграждения уже сегодня. Используйте неработающие устройства по максимуму и превратите их в ценный источник дохода без особых усилий. -После завершения работы вы должны [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +После завершения работы вы должны [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Ссылки: diff --git a/content/other/install-earnapp-easily-using-docker/index.zh.md b/content/other/install-earnapp-easily-using-docker/index.zh.md index ceb58f766fb29..1f4860ff8356a 100644 --- a/content/other/install-earnapp-easily-using-docker/index.zh.md +++ b/content/other/install-earnapp-easily-using-docker/index.zh.md @@ -26,7 +26,7 @@ coverCaption: "利用盈利应用程序为闲置设备赚钱" ### 安装 Docker -学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### 安装 Docker 容器 要使用 Docker 安装小赚应用程序,请按照以下步骤操作: @@ -53,7 +53,7 @@ docker run -td --name earnapp --privileged -v /sys/fs/cgroup:/sys/fs/cgroup:ro - 总之,"赚App "为您提供了一个绝佳的机会,让您可以将闲置设备货币化,并通过共享互联网作为 VPN 服务赚取奖励。通过利用您设备的闲置资源,您可以通过住宅 IP 获得被动收入,平均每个节点每月 5 美元。要开始使用,请在 Earn App 创建一个账户,按照安装说明操作,今天就开始赚取奖励。充分利用您的闲置设备,毫不费力地将它们转化为宝贵的收入来源。 -完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## 参考文献: diff --git a/content/other/install-honeygain-easily-using-docker/index.de.md b/content/other/install-honeygain-easily-using-docker/index.de.md index 8fc6533294e76..6cc083aadad9b 100644 --- a/content/other/install-honeygain-easily-using-docker/index.de.md +++ b/content/other/install-honeygain-easily-using-docker/index.de.md @@ -23,7 +23,7 @@ Erstellen Sie ein Konto unter [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Docker installieren -Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installieren Sie den Docker-Container: Ändern Sie den String mit der offensichtlichen E-Mail, dem Passwort und dem Gerätenamen, bevor Sie ihn in das Terminal einfügen @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E Zusammenfassend lässt sich sagen, dass Honey Gain eine attraktive Möglichkeit bietet, durch die gemeinsame Nutzung Ihrer Internetverbindung ein passives Einkommen zu erzielen. Indem Sie Teil des Netzwerks werden, können Sie Ihre ungenutzte Bandbreite zu Geld machen und sie in eine beständige Einnahmequelle verwandeln. Es ist jedoch wichtig, die Komplexität des Auszahlungsprozesses zu verstehen und die Details sorgfältig zu prüfen, bevor Sie sich für diesen Dienst entscheiden. Um mit Honey Gain zu beginnen, folgen Sie den Installations- und Einrichtungsanweisungen und beginnen Sie Ihre Reise zu einem mühelosen passiven Einkommen. -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.en.md b/content/other/install-honeygain-easily-using-docker/index.en.md index 50ddfef6d7b1c..d3744db727a88 100644 --- a/content/other/install-honeygain-easily-using-docker/index.en.md +++ b/content/other/install-honeygain-easily-using-docker/index.en.md @@ -23,7 +23,7 @@ Create an account at [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Install Docker -Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). ### Install the Docker Container: Modify the string with the obvious email, password, and device name before pasting into the terminal @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E In conclusion, Honey Gain offers an appealing opportunity to earn passive income by sharing your internet connection. By becoming a part of their network, you can monetize your unused bandwidth and turn it into a consistent source of revenue. However, it's important to understand the complexities of the payout process and carefully evaluate the details before deciding to use this service. To get started with Honey Gain, follow the provided installation and setup instructions and begin your journey towards earning passive income effortlessly. -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.es.md b/content/other/install-honeygain-easily-using-docker/index.es.md index f82a4eda3c660..9a0c310e02970 100644 --- a/content/other/install-honeygain-easily-using-docker/index.es.md +++ b/content/other/install-honeygain-easily-using-docker/index.es.md @@ -23,7 +23,7 @@ Cree una cuenta en [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Install Docker -Aprender [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Aprender [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instala el contenedor Docker: Modifica la cadena con el email obvio, la contraseña y el nombre del dispositivo antes de pegarlo en el terminal @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E En conclusión, Honey Gain ofrece una atractiva oportunidad de obtener ingresos pasivos compartiendo tu conexión a Internet. Al formar parte de su red, puedes monetizar tu ancho de banda no utilizado y convertirlo en una fuente constante de ingresos. Sin embargo, es importante entender las complejidades del proceso de pago y evaluar cuidadosamente los detalles antes de decidirse a utilizar este servicio. Para empezar con Honey Gain, siga las instrucciones de instalación y configuración proporcionadas y comience su viaje hacia la obtención de ingresos pasivos sin esfuerzo. -Una vez que haya terminado, deberá [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que haya terminado, deberá [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.fr.md b/content/other/install-honeygain-easily-using-docker/index.fr.md index ab315fb377cf2..2de885b937c46 100644 --- a/content/other/install-honeygain-easily-using-docker/index.fr.md +++ b/content/other/install-honeygain-easily-using-docker/index.fr.md @@ -23,7 +23,7 @@ Créer un compte sur [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Installer Docker -Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installer le conteneur Docker : Modifier la chaîne avec l'email, le mot de passe et le nom de l'appareil avant de la coller dans le terminal. @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E En conclusion, Honey Gain offre une opportunité intéressante de gagner un revenu passif en partageant votre connexion Internet. En devenant membre de leur réseau, vous pouvez monétiser votre bande passante inutilisée et la transformer en une source de revenus régulière. Cependant, il est important de comprendre les complexités du processus de paiement et d'évaluer soigneusement les détails avant de décider d'utiliser ce service. Pour commencer avec Honey Gain, suivez les instructions d'installation et de configuration fournies et commencez votre voyage pour gagner des revenus passifs sans effort. -Une fois que vous aurez terminé, vous devrez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous aurez terminé, vous devrez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.it.md b/content/other/install-honeygain-easily-using-docker/index.it.md index 665cf7c752264..b30fe540facdc 100644 --- a/content/other/install-honeygain-easily-using-docker/index.it.md +++ b/content/other/install-honeygain-easily-using-docker/index.it.md @@ -23,7 +23,7 @@ Creare un account all'indirizzo [honeygain.com](https://r.honeygain.me/HONEY9149 ### Installare Docker -Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installare il contenitore Docker: Modificare la stringa con l'email, la password e il nome del dispositivo prima di incollarla nel terminale. @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E In conclusione, Honey Gain offre un'interessante opportunità di guadagno passivo condividendo la propria connessione a Internet. Entrando a far parte della loro rete, è possibile monetizzare la propria larghezza di banda inutilizzata e trasformarla in una fonte di reddito costante. Tuttavia, è importante comprendere le complessità del processo di pagamento e valutare attentamente i dettagli prima di decidere di utilizzare questo servizio. Per iniziare a utilizzare Honey Gain, seguite le istruzioni di installazione e configurazione fornite e iniziate il vostro viaggio verso il guadagno passivo senza sforzo. -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.ja.md b/content/other/install-honeygain-easily-using-docker/index.ja.md index e1d4573f85d91..6aabc5465786c 100644 --- a/content/other/install-honeygain-easily-using-docker/index.ja.md +++ b/content/other/install-honeygain-easily-using-docker/index.ja.md @@ -23,7 +23,7 @@ coverCaption: "" ### Dockerのインストール -学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Docker Containerをインストールします: 端末に貼り付ける前に、メール、パスワード、端末名で文字列を修正する。 @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E 結論として、Honey Gainはインターネット接続を共有することで受動的な収入を得ることができる魅力的な機会を提供しています。ハニーゲインのネットワークの一員となることで、未使用の帯域幅を収益化し、安定した収入源にすることができます。しかし、このサービスの利用を決定する前に、支払いプロセスの複雑さを理解し、詳細を慎重に評価することが重要です。ハニーゲインを始めるには、提供されたインストールとセットアップの指示に従って、楽に受動的な収入を得るための旅を始めてください。 -完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.nl.md b/content/other/install-honeygain-easily-using-docker/index.nl.md index 7d8b8c2e3d119..3719575380800 100644 --- a/content/other/install-honeygain-easily-using-docker/index.nl.md +++ b/content/other/install-honeygain-easily-using-docker/index.nl.md @@ -23,7 +23,7 @@ Maak een account aan op [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Docker installeren -Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Installeer de Docker Container: Wijzig de string met de voor de hand liggende e-mail, wachtwoord en apparaatnaam voordat u deze in de terminal plakt. @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E Kortom, Honey Gain biedt een aantrekkelijke mogelijkheid om passief inkomen te verdienen door uw internetverbinding te delen. Door deel uit te maken van hun netwerk kunt u uw ongebruikte bandbreedte te gelde maken en omzetten in een consistente bron van inkomsten. Het is echter belangrijk om de complexiteit van het uitbetalingsproces te begrijpen en de details zorgvuldig te evalueren voordat u besluit om deze dienst te gebruiken. Om te beginnen met Honey Gain, volgt u de meegeleverde installatie- en instellingsinstructies en begint u uw reis naar het moeiteloos verdienen van passief inkomen. -Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.pl.md b/content/other/install-honeygain-easily-using-docker/index.pl.md index c13d7e71c3420..cf41bbc283d0a 100644 --- a/content/other/install-honeygain-easily-using-docker/index.pl.md +++ b/content/other/install-honeygain-easily-using-docker/index.pl.md @@ -23,7 +23,7 @@ Utwórz konto pod adresem [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Zainstaluj Dockera -Nauka [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Nauka [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Zainstaluj kontener Docker: Zmodyfikuj ciąg znaków za pomocą oczywistego adresu e-mail, hasła i nazwy urządzenia przed wklejeniem do terminala @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E Podsumowując, Honey Gain oferuje atrakcyjną możliwość zarabiania pasywnego dochodu poprzez udostępnianie połączenia internetowego. Stając się częścią ich sieci, możesz zarabiać na niewykorzystanej przepustowości i przekształcić ją w stałe źródło przychodów. Ważne jest jednak, aby zrozumieć złożoność procesu wypłaty i dokładnie ocenić szczegóły przed podjęciem decyzji o skorzystaniu z tej usługi. Aby rozpocząć korzystanie z Honey Gain, postępuj zgodnie z dostarczonymi instrukcjami instalacji i konfiguracji i rozpocznij swoją podróż w kierunku zarabiania pasywnego dochodu bez wysiłku. -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.ro.md b/content/other/install-honeygain-easily-using-docker/index.ro.md index 6fa4443d00fbe..97002059cb327 100644 --- a/content/other/install-honeygain-easily-using-docker/index.ro.md +++ b/content/other/install-honeygain-easily-using-docker/index.ro.md @@ -23,7 +23,7 @@ Creați un cont la [honeygain.com](https://r.honeygain.me/HONEY9149D) ### Instalați Docker -Învățați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Învățați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Instalați containerul Docker: Modificați șirul cu e-mailul, parola și numele dispozitivului evident înainte de a-l lipi în terminal @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E În concluzie, Honey Gain oferă o oportunitate atractivă de a câștiga un venit pasiv prin partajarea conexiunii tale la internet. Devenind parte a rețelei lor, puteți monetiza lățimea de bandă nefolosită și o puteți transforma într-o sursă consistentă de venituri. Cu toate acestea, este important să înțelegeți complexitatea procesului de plată și să evaluați cu atenție detaliile înainte de a decide să utilizați acest serviciu. Pentru a începe cu Honey Gain, urmați instrucțiunile de instalare și configurare furnizate și începeți călătoria către obținerea unui venit pasiv fără efort. -Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.ru.md b/content/other/install-honeygain-easily-using-docker/index.ru.md index dc1f24571ffb2..30bacb67cda66 100644 --- a/content/other/install-honeygain-easily-using-docker/index.ru.md +++ b/content/other/install-honeygain-easily-using-docker/index.ru.md @@ -23,7 +23,7 @@ coverCaption: "" ### Установите Docker -Изучить [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Изучить [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) ### Установите контейнер Docker: Перед вставкой в терминал измените строку, указав очевидные email, пароль и имя устройства @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E В заключение можно сказать, что Honey Gain предлагает привлекательную возможность получения пассивного дохода за счет совместного использования своего Интернет-соединения. Став частью их сети, вы сможете монетизировать свою неиспользуемую пропускную способность и превратить ее в постоянный источник дохода. Однако важно понимать сложность процесса выплат и внимательно изучить все детали, прежде чем принимать решение об использовании этой услуги. Чтобы начать работу с Honey Gain, следуйте прилагаемым инструкциям по установке и настройке и начните свой путь к получению пассивного дохода без особых усилий. -По окончании работы вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +По окончании работы вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-honeygain-easily-using-docker/index.zh.md b/content/other/install-honeygain-easily-using-docker/index.zh.md index 1d6eff8277134..051eb3f8e2360 100644 --- a/content/other/install-honeygain-easily-using-docker/index.zh.md +++ b/content/other/install-honeygain-easily-using-docker/index.zh.md @@ -23,7 +23,7 @@ coverCaption: "" #### 安装 Docker -学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 安装 Docker 容器: 用明显的电子邮件、密码和设备名称修改字符串,然后粘贴到终端中 @@ -42,5 +42,5 @@ docker run --name honeygain -td honeygain/honeygain -tou-accept -email ACCOUNT_E 总之,Honey Gain 提供了一个通过共享网络连接赚取被动收入的诱人机会。加入他们的网络,您就可以将闲置带宽变为货币,并将其转化为稳定的收入来源。不过,在决定使用这项服务之前,一定要了解支付流程的复杂性,并仔细评估细节。要开始使用 Honey Gain,请按照提供的安装和设置说明进行操作,然后开始轻松赚取被动收入的旅程。 -完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) diff --git a/content/other/install-mysterium-easily-using-docker/index.de.md b/content/other/install-mysterium-easily-using-docker/index.de.md index 8c304605aea82..8147c675eaf4d 100644 --- a/content/other/install-mysterium-easily-using-docker/index.de.md +++ b/content/other/install-mysterium-easily-using-docker/index.de.md @@ -21,7 +21,7 @@ Um Mysterium mit Hilfe des Docker-Containers zu installieren, gehen Sie wie folg #### Docker installieren -Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Installieren Sie den Mysterium-Docker-Container @@ -50,7 +50,7 @@ Eine Anleitung zur Portweiterleitung finden Sie in den folgenden Ressourcen: Mysterium ist ein dezentraler VPN- und Web-Scraping-Dienst, der es Ihnen ermöglicht, Geld zu verdienen und gleichzeitig Ihre Privatsphäre und Sicherheit zu wahren. Mit potenziellen monatlichen Einnahmen zwischen $1 und $20 pro Knoten pro IP bietet es eine Einkommensmöglichkeit für Benutzer. Beginnen Sie noch heute mit der Nutzung von Mysterium und nutzen Sie die Vorteile seiner Funktionen! -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referenz diff --git a/content/other/install-mysterium-easily-using-docker/index.en.md b/content/other/install-mysterium-easily-using-docker/index.en.md index f22cc52b30ea9..367130b84f5c4 100644 --- a/content/other/install-mysterium-easily-using-docker/index.en.md +++ b/content/other/install-mysterium-easily-using-docker/index.en.md @@ -21,7 +21,7 @@ To install Mysterium using the Docker container, follow these steps: #### Install Docker -Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). #### Install the Mysterium Docker Container @@ -50,7 +50,7 @@ For instructions on port forwarding, you can refer to the following resources: Mysterium provides a decentralized VPN and web scraping service that allows you to earn money while maintaining privacy and security. With potential monthly earnings ranging from $1 to $20 per node per IP, it offers an income opportunity for users. Start using Mysterium and take advantage of its features today! -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference diff --git a/content/other/install-mysterium-easily-using-docker/index.es.md b/content/other/install-mysterium-easily-using-docker/index.es.md index 3f0f9af553011..9cc761eced79f 100644 --- a/content/other/install-mysterium-easily-using-docker/index.es.md +++ b/content/other/install-mysterium-easily-using-docker/index.es.md @@ -21,7 +21,7 @@ Para instalar Mysterium utilizando el contenedor Docker, siga estos pasos: #### Instalar Docker -Aprenda [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Aprenda [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Instalar el contenedor Docker Mysterium @@ -50,7 +50,7 @@ Para obtener instrucciones sobre el reenvío de puertos, puede consultar los sig Mysterium proporciona una VPN descentralizada y un servicio de web scraping que permite ganar dinero manteniendo la privacidad y la seguridad. Con un potencial de ganancias mensuales que van desde $ 1 a $ 20 por nodo por IP, ofrece una oportunidad de ingresos para los usuarios. ¡Empieza a usar Mysterium y aprovéchate de sus características hoy mismo! -Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencia diff --git a/content/other/install-mysterium-easily-using-docker/index.fr.md b/content/other/install-mysterium-easily-using-docker/index.fr.md index 5b791a52427f0..a92207dc382ea 100644 --- a/content/other/install-mysterium-easily-using-docker/index.fr.md +++ b/content/other/install-mysterium-easily-using-docker/index.fr.md @@ -21,7 +21,7 @@ Pour installer Mysterium à l'aide du conteneur Docker, suivez les étapes suiva #### Installer Docker -Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Installer le conteneur Docker Mysterium @@ -50,7 +50,7 @@ Pour obtenir des instructions sur le transfert de port, vous pouvez consulter le Mysterium fournit un VPN décentralisé et un service de web scraping qui vous permet de gagner de l'argent tout en préservant votre vie privée et votre sécurité. Avec des revenus mensuels potentiels allant de 1 à 20 $ par nœud et par IP, il offre une opportunité de revenus pour les utilisateurs. Commencez à utiliser Mysterium et profitez de ses fonctionnalités dès aujourd'hui ! -Une fois que vous aurez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous aurez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Référence diff --git a/content/other/install-mysterium-easily-using-docker/index.it.md b/content/other/install-mysterium-easily-using-docker/index.it.md index b22d6cbae4b8f..8b93f7168eba8 100644 --- a/content/other/install-mysterium-easily-using-docker/index.it.md +++ b/content/other/install-mysterium-easily-using-docker/index.it.md @@ -21,7 +21,7 @@ Per installare Mysterium usando il contenitore Docker, seguite i seguenti passi: #### Installare Docker -Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Installare il contenitore Docker Mysterium @@ -50,7 +50,7 @@ Per istruzioni sul port forwarding, potete consultare le seguenti risorse: Mysterium fornisce un servizio di VPN e web scraping decentralizzato che consente di guadagnare denaro mantenendo privacy e sicurezza. Con potenziali guadagni mensili che vanno da 1 a 20 dollari per nodo e per IP, Mysterium offre un'opportunità di guadagno agli utenti. Iniziate a usare Mysterium e sfruttate le sue caratteristiche oggi stesso! -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Riferimento diff --git a/content/other/install-mysterium-easily-using-docker/index.ja.md b/content/other/install-mysterium-easily-using-docker/index.ja.md index b3140800fa6d5..cdb94df2d360d 100644 --- a/content/other/install-mysterium-easily-using-docker/index.ja.md +++ b/content/other/install-mysterium-easily-using-docker/index.ja.md @@ -21,7 +21,7 @@ Dockerコンテナを使用してMysteriumをインストールする場合は #### Dockerをインストールする -学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Mysterium Docker Containerのインストール @@ -50,7 +50,7 @@ ufw allow 59850:60000/tcp Mysteriumは、プライバシーとセキュリティを維持しながら収入を得ることができる、分散型VPNとウェブスクレイピングサービスを提供します。IPごとのノードあたり1ドルから20ドルの潜在的な月間収益があり、ユーザーに収入の機会を提供します。Mysteriumの使用を開始し、その機能を今すぐ利用しましょう! -ご利用が完了しましたら [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +ご利用が完了しましたら [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## リファレンス diff --git a/content/other/install-mysterium-easily-using-docker/index.nl.md b/content/other/install-mysterium-easily-using-docker/index.nl.md index a34f79c244f59..f374503966bba 100644 --- a/content/other/install-mysterium-easily-using-docker/index.nl.md +++ b/content/other/install-mysterium-easily-using-docker/index.nl.md @@ -21,7 +21,7 @@ Volg deze stappen om Mysterium te installeren met behulp van de Docker-container #### Installeer Docker -Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Installeer de Mysterium Docker Container @@ -50,7 +50,7 @@ Voor instructies over port forwarding kunt u de volgende bronnen raadplegen: Mysterium biedt een gedecentraliseerde VPN en web scraping dienst waarmee je geld kunt verdienen met behoud van privacy en veiligheid. Met potentiële maandelijkse verdiensten van $1 tot $20 per node per IP, biedt het een inkomenskans voor gebruikers. Begin Mysterium te gebruiken en profiteer vandaag nog van de functies! -Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference diff --git a/content/other/install-mysterium-easily-using-docker/index.pl.md b/content/other/install-mysterium-easily-using-docker/index.pl.md index 2e9a236e7f81f..8ddb1bac82e36 100644 --- a/content/other/install-mysterium-easily-using-docker/index.pl.md +++ b/content/other/install-mysterium-easily-using-docker/index.pl.md @@ -21,7 +21,7 @@ Aby zainstalować Mysterium przy użyciu kontenera Docker, wykonaj następujące #### Zainstaluj Docker -Dowiedz się [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Dowiedz się [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Instalacja kontenera Docker Mysterium @@ -50,7 +50,7 @@ Instrukcje dotyczące przekierowywania portów można znaleźć w następującyc Mysterium zapewnia zdecentralizowaną sieć VPN i usługę skrobania stron internetowych, która pozwala zarabiać pieniądze przy jednoczesnym zachowaniu prywatności i bezpieczeństwa. Dzięki potencjalnym miesięcznym zarobkom w wysokości od 1 do 20 USD za węzeł na IP, oferuje on użytkownikom możliwość uzyskania dochodu. Zacznij korzystać z Mysterium i skorzystaj z jego funkcji już dziś! -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencje diff --git a/content/other/install-mysterium-easily-using-docker/index.ro.md b/content/other/install-mysterium-easily-using-docker/index.ro.md index 2ce18790e6d06..066e16833bb60 100644 --- a/content/other/install-mysterium-easily-using-docker/index.ro.md +++ b/content/other/install-mysterium-easily-using-docker/index.ro.md @@ -21,7 +21,7 @@ Pentru a instala Mysterium utilizând containerul Docker, urmați acești pași: #### Instalați Docker -Învățați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Învățați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Instalați containerul Docker Mysterium @@ -50,7 +50,7 @@ Pentru instrucțiuni privind redirecționarea porturilor, puteți consulta urmă Mysterium oferă un VPN descentralizat și un serviciu de web scraping care vă permite să câștigați bani, menținând în același timp confidențialitatea și securitatea. Cu câștiguri lunare potențiale cuprinse între 1 și 20 de dolari pe nod și pe IP, oferă o oportunitate de venit pentru utilizatori. Începeți să folosiți Mysterium și profitați de caracteristicile sale astăzi! -Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referință diff --git a/content/other/install-mysterium-easily-using-docker/index.ru.md b/content/other/install-mysterium-easily-using-docker/index.ru.md index d0b8d7e77976e..b2b7a1bf998e8 100644 --- a/content/other/install-mysterium-easily-using-docker/index.ru.md +++ b/content/other/install-mysterium-easily-using-docker/index.ru.md @@ -21,7 +21,7 @@ coverCaption: "" #### Установить Docker -Изучить [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Изучить [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### Установка Docker-контейнера Mysterium @@ -50,7 +50,7 @@ ufw allow 59850:60000/tcp Mysterium - это децентрализованный VPN-сервис и служба веб-скреппинга, позволяющая зарабатывать деньги, сохраняя конфиденциальность и безопасность. Потенциальный ежемесячный доход составляет от 1 до 20 долл. за узел на IP, что открывает перед пользователями возможность заработка. Начните использовать Mysterium и воспользуйтесь его возможностями уже сегодня! -По окончании работы вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +По окончании работы вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference diff --git a/content/other/install-mysterium-easily-using-docker/index.zh.md b/content/other/install-mysterium-easily-using-docker/index.zh.md index 0954ef3ad1f4e..5315eb0b3def8 100644 --- a/content/other/install-mysterium-easily-using-docker/index.zh.md +++ b/content/other/install-mysterium-easily-using-docker/index.zh.md @@ -21,7 +21,7 @@ coverCaption: "" #### 安装 Docker -学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 安装 Mysterium Docker 容器 @@ -50,7 +50,7 @@ ufw allow 59850:60000/tcp Mysterium 提供去中心化的 VPN 和网络搜刮服务,让你在维护隐私和安全的同时赚取收入。每个 IP 节点的潜在月收入从 1 美元到 20 美元不等,它为用户提供了创收机会。现在就开始使用 Mysterium 并利用其功能吧! -完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## 参考资料 diff --git a/content/other/install-pawnsapp-easily-using-docker/index.de.md b/content/other/install-pawnsapp-easily-using-docker/index.de.md index 82b0e58044849..6f256efc5498b 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.de.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.de.md @@ -27,7 +27,7 @@ Erstellen Sie ein PawnsApp Konto indem Sie besuchen [https://pawns.app](https:// #### 2. Docker installieren -Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. Sobald Sie ein Konto erstellt haben, folgen Sie den Anweisungen unten, um den Docker-Container für PawnsApp zu installieren: @@ -55,7 +55,7 @@ PawnsApp bietet eine hervorragende Möglichkeit, ein passives Einkommen zu erzie Beginnen Sie Ihre Reise mit PawnsApp noch heute und erschließen Sie sich das Potenzial, mühelos Geld zu verdienen! -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Referenz - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.en.md b/content/other/install-pawnsapp-easily-using-docker/index.en.md index d6d00ca4f7507..cb6dd8249764d 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.en.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.en.md @@ -27,7 +27,7 @@ Create a PawnsApp account by visiting [https://pawns.app](https://pawns.app/?r=2 #### 2. Install Docker -Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). #### 3. Once you have created an account, follow the instructions below to install the Docker container for PawnsApp: @@ -55,7 +55,7 @@ PawnsApp provides an excellent opportunity to earn passive income by sharing you Start your journey with PawnsApp today and unlock the potential of earning money effortlessly! -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Reference - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.es.md b/content/other/install-pawnsapp-easily-using-docker/index.es.md index 028197f55fcb6..a73564b154113 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.es.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.es.md @@ -27,7 +27,7 @@ Cree una cuenta de PawnsApp visitando [https://pawns.app](https://pawns.app/?r=2 #### 2. Instalar Docker -Aprende [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Aprende [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. Una vez que haya creado una cuenta, siga las siguientes instrucciones para instalar el contenedor Docker para PawnsApp: @@ -55,7 +55,7 @@ PawnsApp ofrece una excelente oportunidad para obtener ingresos pasivos comparti ¡Comienza tu viaje con PawnsApp hoy mismo y desbloquea el potencial de ganar dinero sin esfuerzo! -Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Referencia - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.fr.md b/content/other/install-pawnsapp-easily-using-docker/index.fr.md index 5ab1850937553..3ee7aab731ed2 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.fr.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.fr.md @@ -27,7 +27,7 @@ Créez un compte PawnsApp en visitant [https://pawns.app](https://pawns.app/?r=2 #### 2. Installer Docker -Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. Une fois que vous avez créé un compte, suivez les instructions ci-dessous pour installer le conteneur Docker pour PawnsApp : @@ -55,7 +55,7 @@ PawnsApp offre une excellente opportunité de gagner un revenu passif en partage Commencez votre voyage avec PawnsApp aujourd'hui et libérez le potentiel de gagner de l'argent sans effort ! -Une fois que vous avez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous avez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Référence - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.it.md b/content/other/install-pawnsapp-easily-using-docker/index.it.md index 42b3226f82a12..fb6224fcb5e84 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.it.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.it.md @@ -27,7 +27,7 @@ Creare un account PawnsApp visitando [https://pawns.app](https://pawns.app/?r=20 #### 2. Installare Docker -Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. Una volta creato un account, seguite le istruzioni seguenti per installare il contenitore Docker di PawnsApp: @@ -55,7 +55,7 @@ PawnsApp offre un'eccellente opportunità di guadagno passivo condividendo la pr Iniziate oggi stesso il vostro viaggio con PawnsApp e sbloccate il potenziale di guadagno senza sforzo! -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Riferimento - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.ja.md b/content/other/install-pawnsapp-easily-using-docker/index.ja.md index 1a9ab27e0b580..55e9a7ba22bf0 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.ja.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.ja.md @@ -27,7 +27,7 @@ PawnsAppのアカウントを作成するには、以下のサイトにアクセ #### 2.Dockerのインストール -学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3.アカウントの作成が完了したら、以下の手順でPawnsAppのDockerコンテナをインストールします: @@ -55,7 +55,7 @@ PawnsApp は、インターネット接続を共有し、アンケートに回 今日からPawnsAppで旅を始め、楽にお金を稼ぐ可能性を解き放ちましょう! -インストールが完了したら [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +インストールが完了したら [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### リファレンス - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.nl.md b/content/other/install-pawnsapp-easily-using-docker/index.nl.md index bcfc837c06746..5c248fe69e14b 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.nl.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.nl.md @@ -27,7 +27,7 @@ Maak een PawnsApp account aan door naar [https://pawns.app](https://pawns.app/?r #### 2. Docker installeren -Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. Zodra u een account hebt aangemaakt, volgt u de onderstaande instructies om de Docker-container voor PawnsApp te installeren: @@ -55,7 +55,7 @@ PawnsApp biedt een uitstekende mogelijkheid om passief inkomen te verdienen door Begin uw reis met PawnsApp vandaag nog en ontgrendel het potentieel van moeiteloos geld verdienen! -Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Referentie - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.pl.md b/content/other/install-pawnsapp-easily-using-docker/index.pl.md index 1e95ae959a097..32e0ec655a569 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.pl.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.pl.md @@ -27,7 +27,7 @@ Utwórz konto PawnsApp, odwiedzając stronę [https://pawns.app](https://pawns.a #### 2. Zainstaluj Docker -Dowiedz się [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Dowiedz się [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. Po utworzeniu konta postępuj zgodnie z poniższymi instrukcjami, aby zainstalować kontener Docker dla aplikacji PawnsApp: @@ -55,7 +55,7 @@ PawnsApp zapewnia doskonałą okazję do zarabiania pasywnego dochodu poprzez ud Rozpocznij swoją przygodę z PawnsApp już dziś i uwolnij potencjał zarabiania pieniędzy bez wysiłku! -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Referencje - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.ro.md b/content/other/install-pawnsapp-easily-using-docker/index.ro.md index fb1887fad5ca6..8f4836fbee37a 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.ro.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.ro.md @@ -27,7 +27,7 @@ Creați un cont PawnsApp vizitând [https://pawns.app](https://pawns.app/?r=2092 #### 2. Instalați Docker -Învățați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Învățați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. După ce ați creat un cont, urmați instrucțiunile de mai jos pentru a instala containerul Docker pentru PawnsApp: @@ -55,7 +55,7 @@ PawnsApp oferă o oportunitate excelentă de a câștiga venituri pasive prin pa Începeți astăzi călătoria cu PawnsApp și deblocați potențialul de a câștiga bani fără efort! -După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Referință - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.ru.md b/content/other/install-pawnsapp-easily-using-docker/index.ru.md index 99b6d936fe8b8..927f561b79dd1 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.ru.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.ru.md @@ -27,7 +27,7 @@ PawnsApp похож на другие платформы, которые пла #### 2. Установите Docker -Изучить [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +Изучить [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3. После создания учетной записи следуйте приведенным ниже инструкциям для установки Docker-контейнера для PawnsApp: @@ -55,7 +55,7 @@ PawnsApp предоставляет отличную возможность по Начните свой путь с PawnsApp уже сегодня и откройте для себя возможность зарабатывать деньги без особых усилий! -По окончании работы вы должны [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +По окончании работы вы должны [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### Ссылка - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-pawnsapp-easily-using-docker/index.zh.md b/content/other/install-pawnsapp-easily-using-docker/index.zh.md index fa1736ae29fec..11d3ca55a06a0 100644 --- a/content/other/install-pawnsapp-easily-using-docker/index.zh.md +++ b/content/other/install-pawnsapp-easily-using-docker/index.zh.md @@ -27,7 +27,7 @@ PawnsApp 与其他通过共享网络连接向您支付报酬的平台类似。 #### 2.安装 Docker -学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) #### 3.创建账户后,请按照以下说明安装 PawnsApp 的 Docker 容器: @@ -55,7 +55,7 @@ PawnsApp 提供了一个绝佳的机会,让您通过共享互联网连接和 今天就开始您的 PawnsApp 之旅,发掘轻松赚钱的潜力! -安装完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +安装完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) #### 参考资料 - [PawnsApp](https://pawns.app/?r=2092882) diff --git a/content/other/install-peer2profit-easily-using-docker/index.de.md b/content/other/install-peer2profit-easily-using-docker/index.de.md index c61e9abfec2ab..42857ad2a9799 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.de.md +++ b/content/other/install-peer2profit-easily-using-docker/index.de.md @@ -22,7 +22,7 @@ Um loszulegen, erstellen Sie ein Konto bei [peer2profit.com](https://peer2profit ### Installieren Sie den Docker-Container: Folgen Sie diesen Schritten, um den Peer 2 Profit Docker-Container zu installieren: -0. Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Öffnen Sie Ihr Terminal und geben Sie den folgenden Befehl ein, wobei Sie "your_email_without_quotes" durch Ihre tatsächliche E-Mail-Adresse ersetzen: ```bash @@ -41,7 +41,7 @@ Für eine visuelle Anleitung können Sie sich das folgende Video-Tutorial ansehe ## Fazit Durch die Installation von Peer 2 Profit und die gemeinsame Nutzung Ihres Internets haben Sie die Möglichkeit, mühelos ein passives Einkommen zu erzielen. Mit seiner benutzerfreundlichen Oberfläche und mehreren Auszahlungsoptionen bietet Peer 2 Profit eine bequeme Möglichkeit, Ihre Internetverbindung zu monetarisieren. Legen Sie noch heute los und beginnen Sie zu verdienen! -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referenz - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.en.md b/content/other/install-peer2profit-easily-using-docker/index.en.md index 141e9ac3ebcfe..c9a71f85686f3 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.en.md +++ b/content/other/install-peer2profit-easily-using-docker/index.en.md @@ -12,7 +12,7 @@ coverCaption: "" ## Install Peer 2 Profit: Earn Passive Income by Sharing Your Internet -Are you searching for a reliable way to generate passive income from your internet connection? Look no further than Peer 2 Profit. This platform offers you the opportunity to share your internet for VPN and scraping purposes, just like [EarnApp](https://simeononsecurity.ch/other/install-earnapp-easily-using-docker/) and [HoneyGain](https://simeononsecurity.ch/other/install-honeygain-easily-using-docker/). By participating in Peer 2 Profit, you can earn an average of $1 per month per node per IP. What's more, the platform provides multiple payout options, including money orders, BTC, LTC, and MATIC, giving you the flexibility to receive your earnings in your preferred method. Discover how Peer 2 Profit can help you make the most of your internet connection and start earning today. +Are you searching for a reliable way to generate passive income from your internet connection? Look no further than Peer 2 Profit. This platform offers you the opportunity to share your internet for VPN and scraping purposes, just like [EarnApp](https://simeononsecurity.com/other/install-earnapp-easily-using-docker/) and [HoneyGain](https://simeononsecurity.com/other/install-honeygain-easily-using-docker/). By participating in Peer 2 Profit, you can earn an average of $1 per month per node per IP. What's more, the platform provides multiple payout options, including money orders, BTC, LTC, and MATIC, giving you the flexibility to receive your earnings in your preferred method. Discover how Peer 2 Profit can help you make the most of your internet connection and start earning today. {{< youtube id="Ir6Etplqj3c" >}} @@ -22,7 +22,7 @@ To get started, create an account at [peer2profit.com](https://peer2profit.com/) ### Install the Docker Container: Follow these steps to install the Peer 2 Profit Docker container: -0. Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +0. Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). 1. Open your terminal and enter the following command, replacing "your_email_without_quotes" with your actual email address: ```bash @@ -41,7 +41,7 @@ For a visual guide, you can watch the following video tutorial: ## Conclusion By installing Peer 2 Profit and sharing your internet, you have the opportunity to earn passive income effortlessly. With its user-friendly interface and multiple payout options, Peer 2 Profit offers a convenient way to monetize your internet connection. Get started today and start earning! -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.es.md b/content/other/install-peer2profit-easily-using-docker/index.es.md index 92f371df7e9e2..63b2e396b1df3 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.es.md +++ b/content/other/install-peer2profit-easily-using-docker/index.es.md @@ -22,7 +22,7 @@ Para empezar, cree una cuenta en [peer2profit.com](https://peer2profit.com/) ### Instalar el contenedor Docker: Siga estos pasos para instalar el contenedor Docker de Peer 2 Profit: -0. Aprenda [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Aprenda [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Abra su terminal e introduzca el siguiente comando, sustituyendo "su_email_sin_comillas" por su dirección de correo electrónico real: ```bash @@ -41,7 +41,7 @@ Para una guía visual, puedes ver el siguiente video tutorial: ## Conclusión Al instalar Peer 2 Profit y compartir tu conexión a Internet, tienes la oportunidad de obtener ingresos pasivos sin esfuerzo. Con su interfaz fácil de usar y múltiples opciones de pago, Peer 2 Profit ofrece una manera conveniente de monetizar su conexión a Internet. ¡Empieza hoy mismo y empieza a ganar! -Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencia - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.fr.md b/content/other/install-peer2profit-easily-using-docker/index.fr.md index 1585e16ab5b32..07dd0a414b9c6 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.fr.md +++ b/content/other/install-peer2profit-easily-using-docker/index.fr.md @@ -22,7 +22,7 @@ Pour commencer, créez un compte sur [peer2profit.com](https://peer2profit.com/) ### Installer le conteneur Docker : Suivez ces étapes pour installer le conteneur Docker Peer 2 Profit : -0. Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Ouvrez votre terminal et entrez la commande suivante, en remplaçant "your_email_without_quotes" par votre adresse e-mail réelle : ```bash @@ -41,7 +41,7 @@ Pour un guide visuel, vous pouvez regarder le tutoriel vidéo suivant : ## Conclusion En installant Peer 2 Profit et en partageant votre internet, vous avez la possibilité de gagner des revenus passifs sans effort. Avec son interface conviviale et ses multiples options de paiement, Peer 2 Profit offre un moyen pratique de monétiser votre connexion Internet. Démarrez dès aujourd'hui et commencez à gagner de l'argent ! -Une fois que vous aurez terminé, vous devrez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous aurez terminé, vous devrez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Référence - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.it.md b/content/other/install-peer2profit-easily-using-docker/index.it.md index 99c5f77264ae5..936760c67f60e 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.it.md +++ b/content/other/install-peer2profit-easily-using-docker/index.it.md @@ -22,7 +22,7 @@ Per iniziare, creare un account su [peer2profit.com](https://peer2profit.com/) ### Installare il contenitore Docker: Seguire questi passaggi per installare il contenitore Docker Peer 2 Profit: -0. Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Aprite il terminale e inserite il seguente comando, sostituendo "your_email_without_quotes" con il vostro indirizzo e-mail reale: ```bash @@ -41,7 +41,7 @@ Per una guida visiva, potete guardare il seguente video tutorial: ## Conclusione Installando Peer 2 Profit e condividendo il vostro internet, avrete l'opportunità di guadagnare reddito passivo senza sforzo. Con la sua interfaccia facile da usare e le sue molteplici opzioni di pagamento, Peer 2 Profit offre un modo conveniente per monetizzare la vostra connessione a internet. Iniziate oggi stesso a guadagnare! -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Riferimento - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.ja.md b/content/other/install-peer2profit-easily-using-docker/index.ja.md index 98f1cf670a9c1..926d1d3a1c7ee 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.ja.md +++ b/content/other/install-peer2profit-easily-using-docker/index.ja.md @@ -22,7 +22,7 @@ coverCaption: "" ### Dockerコンテナをインストールする: 以下の手順で、Peer 2 Profit Docker コンテナをインストールします: -0.学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0.学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1.ターミナルを開き、以下のコマンドを入力します。"your_email_without_quotes "を実際の電子メールアドレスに置き換えてください: ```bash @@ -41,7 +41,7 @@ docker rm -f peer2profit || true && docker run -td --restart always \ ## 結論 Peer 2 Profitをインストールし、インターネットを共有することで、受動的な収入を楽に得る機会があります。ユーザーフレンドリーなインターフェースと複数の支払いオプションにより、Peer 2 Profitはあなたのインターネット接続を収益化する便利な方法を提供します。今すぐ始めて、収入を得るようにしましょう! -完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## リファレンス - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.nl.md b/content/other/install-peer2profit-easily-using-docker/index.nl.md index fb4ad03b19540..d6e8f8be5ecad 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.nl.md +++ b/content/other/install-peer2profit-easily-using-docker/index.nl.md @@ -22,7 +22,7 @@ Om te beginnen, maak een account aan bij [peer2profit.com](https://peer2profit.c ### Installeer de Docker Container: Volg deze stappen om de Peer 2 Profit Docker-container te installeren: -0. Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Open uw terminal en voer het volgende commando in, waarbij u "your_email_without_quotes" vervangt door uw werkelijke e-mailadres: ```bash @@ -41,7 +41,7 @@ Voor een visuele gids kunt u de volgende videohandleiding bekijken: ## Conclusie Door Peer 2 Profit te installeren en je internet te delen, heb je de mogelijkheid om moeiteloos passief inkomen te verdienen. Met zijn gebruiksvriendelijke interface en meerdere uitbetalingsopties, biedt Peer 2 Profit een handige manier om je internetverbinding te gelde te maken. Begin vandaag nog en begin met verdienen! -Zodra je klaar bent, moet je [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra je klaar bent, moet je [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.pl.md b/content/other/install-peer2profit-easily-using-docker/index.pl.md index ced71b1e4dc6a..b0ca6171b31d8 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.pl.md +++ b/content/other/install-peer2profit-easily-using-docker/index.pl.md @@ -22,7 +22,7 @@ Aby rozpocząć, utwórz konto na stronie [peer2profit.com](https://peer2profit. ### Instalacja kontenera Docker: Wykonaj poniższe kroki, aby zainstalować kontener Docker Peer 2 Profit: -0. Ucz się [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Ucz się [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Otwórz terminal i wprowadź następujące polecenie, zastępując "your_email_without_quotes" swoim rzeczywistym adresem e-mail: ```bash @@ -41,7 +41,7 @@ Aby uzyskać przewodnik wizualny, możesz obejrzeć poniższy samouczek wideo: ## Podsumowanie Instalując Peer 2 Profit i udostępniając swój Internet, masz możliwość zarabiania pasywnego dochodu bez wysiłku. Dzięki przyjaznemu dla użytkownika interfejsowi i wielu opcjom wypłat, Peer 2 Profit oferuje wygodny sposób zarabiania na połączeniu internetowym. Zacznij już dziś i zacznij zarabiać! -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencje - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.ro.md b/content/other/install-peer2profit-easily-using-docker/index.ro.md index 604aae5cfef68..e8308abafae3c 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.ro.md +++ b/content/other/install-peer2profit-easily-using-docker/index.ro.md @@ -22,7 +22,7 @@ Pentru a începe, creați un cont la [peer2profit.com](https://peer2profit.com/) ### Instalați containerul Docker: Urmați acești pași pentru a instala containerul Docker Peer 2 Profit: -0. Aflați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Aflați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Deschideți terminalul și introduceți următoarea comandă, înlocuind "your_email_without_quotes" cu adresa dvs. de e-mail reală: ```bash @@ -41,7 +41,7 @@ Pentru un ghid vizual, puteți viziona următorul tutorial video: ## Concluzie Prin instalarea Peer 2 Profit și partajarea internetului, aveți posibilitatea de a câștiga venituri pasive fără efort. Cu interfața sa prietenoasă și multiplele opțiuni de plată, Peer 2 Profit oferă o modalitate convenabilă de a vă monetiza conexiunea la internet. Începeți astăzi și începeți să câștigați! -După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +După ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referință - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.ru.md b/content/other/install-peer2profit-easily-using-docker/index.ru.md index d02df2d232291..54c82d17c678c 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.ru.md +++ b/content/other/install-peer2profit-easily-using-docker/index.ru.md @@ -22,7 +22,7 @@ coverCaption: "" ### Установка контейнера Docker: Выполните следующие шаги для установки Docker-контейнера Peer 2 Profit: -0. Узнать [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Узнать [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Откройте терминал и введите следующую команду, заменив "your_email_without_quotes" на ваш реальный адрес электронной почты: ```bash @@ -41,7 +41,7 @@ docker rm -f peer2profit || true && docker run -td --restart always \ ## Заключение Установив Peer 2 Profit и поделившись своим интернетом, вы получаете возможность получать пассивный доход без особых усилий. Благодаря удобному интерфейсу и множеству вариантов выплат Peer 2 Profit предлагает удобный способ монетизации вашего Интернет-соединения. Приступайте к работе сегодня и начните зарабатывать! -По окончании работы вы должны [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +По окончании работы вы должны [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-peer2profit-easily-using-docker/index.zh.md b/content/other/install-peer2profit-easily-using-docker/index.zh.md index f1e3ca72a56e5..cff79e1aaef61 100644 --- a/content/other/install-peer2profit-easily-using-docker/index.zh.md +++ b/content/other/install-peer2profit-easily-using-docker/index.zh.md @@ -22,7 +22,7 @@ coverCaption: "" #### 安装 Docker 容器: 按照以下步骤安装 Peer 2 Profit Docker 容器: -0.学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0.学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1.打开终端,输入以下命令,用实际电子邮件地址替换 "your_email_without_quotes": ```bash @@ -41,7 +41,7 @@ docker rm -f peer2profit || true && docker run -td --restart always \ ## 结论 通过安装 Peer 2 Profit 并共享您的互联网,您就有机会毫不费力地赚取被动收入。Peer 2 Profit 拥有友好的用户界面和多种支付方式,为您的互联网连接盈利提供了便捷途径。今天就开始使用,赚取收入吧! -完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## 参考资料 - [Peer 2 Profit](https://peer2profit.com/) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.de.md b/content/other/install-repocket-easily-using-docker/index.de.md index fa28a57e9277c..e0809ff932345 100644 --- a/content/other/install-repocket-easily-using-docker/index.de.md +++ b/content/other/install-repocket-easily-using-docker/index.de.md @@ -20,7 +20,7 @@ Um loszulegen, erstellen Sie ein Konto bei [repocket.co](https://link.repocket.c ### Installieren Sie den Docker-Container Folgen Sie diesen Schritten, um den Repocket-Docker-Container zu installieren: -0. Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Öffnen Sie Ihr Terminal und geben Sie den folgenden Befehl ein, wobei Sie "your@email.com" und "yourapikey" durch Ihre tatsächliche E-Mail und Ihren API-Schlüssel ersetzen: ```bash @@ -36,7 +36,7 @@ Ausführlichere Anweisungen finden Sie in der [Repocket documentation](https://l ## Fazit Repocket bietet die Möglichkeit, Geld zu verdienen, indem Sie Ihre ungenutzte Internetverbindung teilen. Mit einer Mindestauszahlung von 20 $ und der Möglichkeit, etwa 1 $ pro Knotenpunkt und Box pro Monat zu verdienen, kann Repocket eine wertvolle Quelle für passives Einkommen sein. Es ist jedoch wichtig, das Auszahlungssystem gründlich zu verstehen und eigene Nachforschungen anzustellen, bevor man sich entscheidet, den Dienst zu nutzen. -Sobald Sie das getan haben, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie das getan haben, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referenz - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.en.md b/content/other/install-repocket-easily-using-docker/index.en.md index 0acba21e139a5..b909093e5dd4a 100644 --- a/content/other/install-repocket-easily-using-docker/index.en.md +++ b/content/other/install-repocket-easily-using-docker/index.en.md @@ -20,7 +20,7 @@ To get started, create an account at [repocket.co](https://link.repocket.co/raqc ### Install the Docker Container Follow these steps to install the Repocket Docker container: -0. Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +0. Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). 1. Open your terminal and enter the following command, replacing "your@email.com" and "yourapikey" with your actual email and API key: ```bash @@ -36,7 +36,7 @@ For more detailed instructions, refer to the [Repocket documentation](https://li ## Conclusion Repocket offers an opportunity to earn money by sharing your unused internet connection. With a minimum payout of $20 and the potential to earn about $1 per node per box per month, Repocket can be a valuable source of passive income. However, it's crucial to thoroughly understand the payout system and conduct your own research before deciding to use the service. -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.es.md b/content/other/install-repocket-easily-using-docker/index.es.md index a1a9a02dac810..f006930a1fc44 100644 --- a/content/other/install-repocket-easily-using-docker/index.es.md +++ b/content/other/install-repocket-easily-using-docker/index.es.md @@ -20,7 +20,7 @@ Para empezar, cree una cuenta en [repocket.co](https://link.repocket.co/raqc) y ### Instalar el contenedor Docker Siga estos pasos para instalar el contenedor Docker Repocket: -0. Aprenda [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Aprenda [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Abra su terminal e introduzca el siguiente comando, sustituyendo "your@email.com" y "yourapikey" por su correo electrónico y clave API reales: ```bash @@ -36,7 +36,7 @@ Para obtener instrucciones más detalladas, consulte el [Repocket documentation] ## Conclusión Repocket ofrece la oportunidad de ganar dinero compartiendo tu conexión a Internet no utilizada. Con un pago mínimo de 20$ y el potencial de ganar alrededor de 1$ por nodo por caja al mes, Repocket puede ser una valiosa fuente de ingresos pasivos. Sin embargo, es crucial entender a fondo el sistema de pago y llevar a cabo su propia investigación antes de decidirse a utilizar el servicio. -Una vez que lo hayas hecho, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que lo hayas hecho, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencia - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.fr.md b/content/other/install-repocket-easily-using-docker/index.fr.md index 4cae0969caf90..af8535234fcfd 100644 --- a/content/other/install-repocket-easily-using-docker/index.fr.md +++ b/content/other/install-repocket-easily-using-docker/index.fr.md @@ -20,7 +20,7 @@ Pour commencer, créez un compte sur [repocket.co](https://link.repocket.co/raqc ### Installer le conteneur Docker Suivez ces étapes pour installer le conteneur Docker Repocket : -0. Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Ouvrez votre terminal et entrez la commande suivante, en remplaçant "your@email.com" et "yourapikey" par votre adresse e-mail et votre clé API : ```bash @@ -36,7 +36,7 @@ Pour des instructions plus détaillées, consultez le [Repocket documentation](h ## Conclusion Repocket offre la possibilité de gagner de l'argent en partageant votre connexion Internet inutilisée. Avec un paiement minimum de 20 $ et la possibilité de gagner environ 1 $ par nœud, par boîte et par mois, Repocket peut être une source précieuse de revenus passifs. Cependant, il est essentiel de bien comprendre le système de paiement et d'effectuer vos propres recherches avant de décider d'utiliser le service. -Une fois que vous avez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous avez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Référence - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.it.md b/content/other/install-repocket-easily-using-docker/index.it.md index 5d5464c5cb1e1..cc80cecbbd87f 100644 --- a/content/other/install-repocket-easily-using-docker/index.it.md +++ b/content/other/install-repocket-easily-using-docker/index.it.md @@ -20,7 +20,7 @@ Per iniziare, create un account su [repocket.co](https://link.repocket.co/raqc) ### Installare il contenitore Docker Seguite questi passaggi per installare il contenitore Docker di Repocket: -0. Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Aprite il vostro terminale e inserite il seguente comando, sostituendo "your@email.com" e "yourapikey" con il vostro indirizzo e-mail e la vostra chiave API: ```bash @@ -36,7 +36,7 @@ Per istruzioni più dettagliate, consultare la sezione [Repocket documentation]( ## Conclusione Repocket offre l'opportunità di guadagnare condividendo la propria connessione internet inutilizzata. Con un pagamento minimo di 20 dollari e la possibilità di guadagnare circa 1 dollaro per nodo per casella al mese, Repocket può essere una preziosa fonte di reddito passivo. Tuttavia, è fondamentale comprendere a fondo il sistema di pagamento e condurre le proprie ricerche prima di decidere di utilizzare il servizio. -Una volta fatto, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta fatto, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Riferimento - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.ja.md b/content/other/install-repocket-easily-using-docker/index.ja.md index 714412ccec21a..95d6988c3ef3b 100644 --- a/content/other/install-repocket-easily-using-docker/index.ja.md +++ b/content/other/install-repocket-easily-using-docker/index.ja.md @@ -20,7 +20,7 @@ coverCaption: "" ### Dockerコンテナをインストールする 以下の手順で、RepocketのDockerコンテナをインストールします: -0.学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0.学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1.ターミナルを開き、以下のコマンドを入力します。「your@email.com」と「yourapikey」は、実際のメールとAPIキーに置き換えてください: ```bash @@ -36,7 +36,7 @@ docker run -td --name repocket -e RP_EMAIL=your@email.com -e RP_API_KEY=yourapik ## 結論 Repocketは、あなたの未使用のインターネット接続を共有することによってお金を稼ぐ機会を提供しています。最低支払額20ドル、1ノード1ボックスあたり月1ドル程度の収入を得る可能性があるため、Repocketは受動的収入の貴重なソースとなり得ます。しかし、サービスの利用を決定する前に、ペイアウトシステムを徹底的に理解し、独自の調査を行うことが極めて重要です。 -一度、以下のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +一度、以下のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## リファレンス - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.nl.md b/content/other/install-repocket-easily-using-docker/index.nl.md index f0b1e802b411d..4e41b1a4eecbf 100644 --- a/content/other/install-repocket-easily-using-docker/index.nl.md +++ b/content/other/install-repocket-easily-using-docker/index.nl.md @@ -20,7 +20,7 @@ Om te beginnen, maakt u een account aan bij [repocket.co](https://link.repocket. ### Installeer de Docker Container Volg deze stappen om de Repocket Docker-container te installeren: -0. Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Open uw terminal en voer het volgende commando in, waarbij u "your@email.com" en "yourapikey" vervangt door uw werkelijke e-mail en API-sleutel: ```bash @@ -36,7 +36,7 @@ Zie voor meer gedetailleerde instructies de [Repocket documentation](https://lin ## Conclusie Repocket biedt een kans om geld te verdienen door je ongebruikte internetverbinding te delen. Met een minimale uitbetaling van $20 en het potentieel om ongeveer $1 per node per box per maand te verdienen, kan Repocket een waardevolle bron van passief inkomen zijn. Het is echter cruciaal om het uitbetalingssysteem grondig te begrijpen en uw eigen onderzoek uit te voeren voordat u besluit de dienst te gebruiken. -Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra u klaar bent, moet u [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.pl.md b/content/other/install-repocket-easily-using-docker/index.pl.md index c329f15441659..6bb660d4acf74 100644 --- a/content/other/install-repocket-easily-using-docker/index.pl.md +++ b/content/other/install-repocket-easily-using-docker/index.pl.md @@ -20,7 +20,7 @@ Aby rozpocząć, utwórz konto na stronie [repocket.co](https://link.repocket.co ### Instalacja kontenera Docker Wykonaj poniższe kroki, aby zainstalować kontener Repocket Docker: -0. Ucz się [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Ucz się [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Otwórz terminal i wprowadź następujące polecenie, zastępując "your@email.com" i "yourapikey" rzeczywistym adresem e-mail i kluczem API: ```bash @@ -36,7 +36,7 @@ Więcej szczegółowych instrukcji można znaleźć w sekcji [Repocket documenta ## Podsumowanie Repocket oferuje możliwość zarabiania pieniędzy poprzez udostępnianie nieużywanego połączenia internetowego. Przy minimalnej wypłacie w wysokości 20 USD i możliwości zarobienia około 1 USD za węzeł na skrzynkę miesięcznie, Repocket może być cennym źródłem pasywnego dochodu. Ważne jest jednak, aby dokładnie zrozumieć system wypłat i przeprowadzić własne badania przed podjęciem decyzji o skorzystaniu z usługi. -Gdy już to zrobisz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy już to zrobisz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencje - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.ro.md b/content/other/install-repocket-easily-using-docker/index.ro.md index a04de262f1a5e..eb6958c2ffbda 100644 --- a/content/other/install-repocket-easily-using-docker/index.ro.md +++ b/content/other/install-repocket-easily-using-docker/index.ro.md @@ -20,7 +20,7 @@ Pentru a începe, creați un cont la [repocket.co](https://link.repocket.co/raqc ### Instalați containerul Docker Urmați acești pași pentru a instala containerul Docker Repocket: -0. Învățați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Învățați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Deschideți terminalul și introduceți următoarea comandă, înlocuind "your@email.com" și "yourapikey" cu adresa de e-mail și cheia API reale: ```bash @@ -36,7 +36,7 @@ Pentru instrucțiuni mai detaliate, consultați [Repocket documentation](https:/ ## Concluzie Repocket oferă o oportunitate de a câștiga bani prin partajarea conexiunii dvs. de internet neutilizate. Cu o plată minimă de 20 de dolari și potențialul de a câștiga aproximativ 1 dolar pe nod pe cutie pe lună, Repocket poate fi o sursă valoroasă de venit pasiv. Cu toate acestea, este esențial să înțelegeți bine sistemul de plată și să efectuați propriile cercetări înainte de a decide să utilizați serviciul. -Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referință - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.ru.md b/content/other/install-repocket-easily-using-docker/index.ru.md index 1d7c2b8b77454..47936a3312780 100644 --- a/content/other/install-repocket-easily-using-docker/index.ru.md +++ b/content/other/install-repocket-easily-using-docker/index.ru.md @@ -20,7 +20,7 @@ coverCaption: "" ### Установка контейнера Docker Выполните следующие шаги для установки Docker-контейнера Repocket: -0. Узнать [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Узнать [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Откройте терминал и введите следующую команду, заменив "your@email.com" и "yourapikey" на ваш реальный email и API-ключ: ```bash @@ -36,7 +36,7 @@ docker run -td --name repocket -e RP_EMAIL=your@email.com -e RP_API_KEY=yourapik ## Заключение Repocket предлагает возможность зарабатывать деньги, предоставляя в пользование неиспользуемое подключение к Интернету. При минимальной выплате в 20 долл. и потенциальном заработке около 1 долл. за узел на ящик в месяц Repocket может стать ценным источником пассивного дохода. Однако перед тем как принять решение об использовании сервиса, необходимо тщательно разобраться в системе выплат и провести собственное исследование. -После этого вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +После этого вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-repocket-easily-using-docker/index.zh.md b/content/other/install-repocket-easily-using-docker/index.zh.md index 6112b86194b35..6038d53649215 100644 --- a/content/other/install-repocket-easily-using-docker/index.zh.md +++ b/content/other/install-repocket-easily-using-docker/index.zh.md @@ -20,7 +20,7 @@ coverCaption: "" ### 安装 Docker 容器 按照以下步骤安装 Repocket Docker 容器: -0.学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0.学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1.打开终端,输入以下命令,用实际电子邮件和 API 密钥替换 "your@email.com "和 "yourapikey": ```bash @@ -36,7 +36,7 @@ docker run -td --name repocket -e RP_EMAIL=your@email.com -e RP_API_KEY=yourapik ## 结论 Repocket 提供了一个通过共享闲置互联网连接赚钱的机会。Repocket 的最低付费额为 20 美元,每个节点每个月可获得约 1 美元的收入,是一种宝贵的被动收入来源。不过,在决定使用该服务之前,务必要彻底了解支付系统并进行自己的研究。 -完成研究后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成研究后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## 参考资料 - [Repocket](https://link.repocket.co/raqc) \ No newline at end of file diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.de.md b/content/other/install-traff-monetizer-easily-using-docker/index.de.md index 9c24a346f38c0..7cc541849079d 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.de.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.de.md @@ -22,7 +22,7 @@ Um loszulegen, erstellen Sie ein Konto bei [traffmonetizer.com](https://traffmon ### Installieren Sie den Docker-Container Folgen Sie diesen Schritten, um den Traff Monetizer Docker-Container zu installieren: -0. Lernen Sie [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Lernen Sie [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Kopieren Sie die folgende Zeichenfolge und fügen Sie das vom Dashboard erhaltene Token hinzu: ```bash @@ -36,7 +36,7 @@ Ausführlichere Anweisungen finden Sie in der [Traff Monetizer documentation](ht Durch die Installation von Traff Monetizer und die Freigabe Ihres Internets haben Sie die Möglichkeit, online Geld zu verdienen. Mit einem durchschnittlichen monatlichen Verdienst von ca. $2 pro Node pro IP stellt es eine potentielle Einkommensquelle dar. Bitte beachten Sie, dass Auszahlungen nur in BTC möglich sind. Beginnen Sie noch heute, Ihre Internetverbindung zu monetarisieren! -Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Sobald Sie fertig sind, sollten Sie [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referenz diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.en.md b/content/other/install-traff-monetizer-easily-using-docker/index.en.md index 80677bae29317..25f4f0fb1e328 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.en.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.en.md @@ -11,7 +11,7 @@ coverCaption: "" --- ## Install Traff Monetizer: Share Your Internet Connection and Make Money Online -Looking for a way to monetize your internet connection? Look no further than Traff Monetizer. Similar to [EarnApp](https://simeononsecurity.ch/other/install-earnapp-easily-using-docker/) and [HoneyGain](https://simeononsecurity.ch/other/install-honeygain-easily-using-docker/), Traff Monetizer offers you the opportunity to earn money by sharing your internet. With an average monthly earning of about $2 per node per IP, Traff Monetizer provides a potential income stream. However, it's important to note that payouts are only offered in BTC. +Looking for a way to monetize your internet connection? Look no further than Traff Monetizer. Similar to [EarnApp](https://simeononsecurity.com/other/install-earnapp-easily-using-docker/) and [HoneyGain](https://simeononsecurity.com/other/install-honeygain-easily-using-docker/), Traff Monetizer offers you the opportunity to earn money by sharing your internet. With an average monthly earning of about $2 per node per IP, Traff Monetizer provides a potential income stream. However, it's important to note that payouts are only offered in BTC. {{< youtube id="8hJgITEz3bA" >}} @@ -21,7 +21,7 @@ To get started, create an account at [traffmonetizer.com](https://traffmonetizer ### Install the Docker Container Follow these steps to install the Traff Monetizer Docker container: -0. Learn [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker). +0. Learn [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker). 1. Copy the following string and append your token obtained from the dashboard: ```bash @@ -35,7 +35,7 @@ For more detailed instructions, refer to the [Traff Monetizer documentation](htt By installing Traff Monetizer and sharing your internet, you have the opportunity to earn money online. With an average monthly earning of about $2 per node per IP, it presents a potential source of income. Keep in mind that payouts are only available in BTC. Start monetizing your internet connection today! -Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Once you're done, you should [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.es.md b/content/other/install-traff-monetizer-easily-using-docker/index.es.md index c4a83f8d83aca..deb7f8b1ce5e9 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.es.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.es.md @@ -22,7 +22,7 @@ Para empezar, cree una cuenta en [traffmonetizer.com](https://traffmonetizer.com ### Instalar el Contenedor Docker Siga estos pasos para instalar el contenedor Docker de Traff Monetizer: -0. Aprenda [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Aprenda [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Copie la siguiente cadena y añádale el token obtenido del panel de control: ```bash @@ -36,7 +36,7 @@ Para obtener instrucciones más detalladas, consulte el [Traff Monetizer documen Instalando Traff Monetizer y compartiendo tu Internet, tienes la oportunidad de ganar dinero online. Con un promedio de ganancias mensuales de alrededor de $2 por nodo por IP, presenta una fuente potencial de ingresos. Ten en cuenta que los pagos sólo están disponibles en BTC. ¡Empieza a monetizar tu conexión a Internet hoy mismo! -Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una vez que hayas terminado, deberías [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencia diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.fr.md b/content/other/install-traff-monetizer-easily-using-docker/index.fr.md index 17fe758fae1d8..176a9f6068418 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.fr.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.fr.md @@ -22,7 +22,7 @@ Pour commencer, créez un compte sur [traffmonetizer.com](https://traffmonetizer ### Installer le conteneur Docker Suivez ces étapes pour installer le conteneur Docker Traff Monetizer : -0. Apprendre [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Apprendre [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Copiez la chaîne suivante et ajoutez-y votre jeton obtenu à partir du tableau de bord : ```bash @@ -36,7 +36,7 @@ Pour des instructions plus détaillées, consultez le [Traff Monetizer documenta En installant Traff Monetizer et en partageant votre internet, vous avez la possibilité de gagner de l'argent en ligne. Avec un gain mensuel moyen d'environ 2 $ par nœud et par IP, il s'agit d'une source potentielle de revenus. Gardez à l'esprit que les paiements ne sont disponibles qu'en BTC. Commencez à monétiser votre connexion Internet dès aujourd'hui ! -Une fois que vous avez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Une fois que vous avez terminé, vous devriez [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Référence diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.it.md b/content/other/install-traff-monetizer-easily-using-docker/index.it.md index 096631b24070c..b6e641a1c06ea 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.it.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.it.md @@ -22,7 +22,7 @@ Per iniziare, create un account su [traffmonetizer.com](https://traffmonetizer.c ### Installare il contenitore Docker Seguite questi passaggi per installare il contenitore Docker di Traff Monetizer: -0. Imparare [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Imparare [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Copiare la seguente stringa e aggiungere il token ottenuto dal dashboard: ```bash @@ -36,7 +36,7 @@ Per istruzioni più dettagliate, consultare la sezione [Traff Monetizer document Installando Traff Monetizer e condividendo il proprio Internet, si ha l'opportunità di guadagnare online. Con un guadagno medio mensile di circa 2 dollari per nodo per IP, rappresenta una potenziale fonte di reddito. Tenete presente che i pagamenti sono disponibili solo in BTC. Iniziate a monetizzare la vostra connessione internet oggi stesso! -Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Una volta terminato, dovreste [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Riferimento diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.ja.md b/content/other/install-traff-monetizer-easily-using-docker/index.ja.md index 13f84f1505bcb..8716c15fba4fe 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.ja.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.ja.md @@ -22,7 +22,7 @@ coverCaption: "" ### Dockerコンテナのインストール 以下の手順で、Traff Monetizer Dockerコンテナをインストールします: -0.学ぶ [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0.学ぶ [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1.以下の文字列をコピーして、ダッシュボードから取得したトークンを追加します: ```bash @@ -36,7 +36,7 @@ docker run -td --name traffmonetizer traffmonetizer/cli start accept --token YOU Traff Monetizerをインストールし、インターネットを共有することで、オンラインでお金を稼ぐ機会があります。IPごとにノードあたり約2ドルの平均月収で、それは収入の潜在的な源を提示します。ペイアウトはBTCでのみ利用可能であることに留意してください。今日からあなたのインターネット接続をマネタイズしましょう! -完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完了したら、次のことを行ってください。 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## リファレンス diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.nl.md b/content/other/install-traff-monetizer-easily-using-docker/index.nl.md index ea77fe1ca67f5..1fe92b7f52e84 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.nl.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.nl.md @@ -22,7 +22,7 @@ Om te beginnen, maak een account aan bij [traffmonetizer.com](https://traffmonet ### Installeer de Docker Container Volg deze stappen om de Traff Monetizer Docker-container te installeren: -0. Leer [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Leer [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Kopieer de volgende string en voeg uw van het dashboard verkregen token toe: ```bash @@ -36,7 +36,7 @@ Zie voor meer gedetailleerde instructies de [Traff Monetizer documentation](http Door Traff Monetizer te installeren en je internet te delen, heb je de mogelijkheid om online geld te verdienen. Met een gemiddelde maandelijkse verdienste van ongeveer $2 per node per IP is het een potentiële bron van inkomsten. Houd er rekening mee dat uitbetalingen alleen beschikbaar zijn in BTC. Begin vandaag nog met het te gelde maken van uw internetverbinding! -Zodra je klaar bent, zou je [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Zodra je klaar bent, zou je [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.pl.md b/content/other/install-traff-monetizer-easily-using-docker/index.pl.md index 7ae719df82c36..7a171708a139f 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.pl.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.pl.md @@ -22,7 +22,7 @@ Aby rozpocząć, utwórz konto na stronie [traffmonetizer.com](https://traffmone ### Instalacja kontenera Docker Wykonaj poniższe kroki, aby zainstalować kontener Docker Traff Monetizer: -0. Ucz się [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Ucz się [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Skopiuj poniższy ciąg znaków i dołącz token uzyskany z pulpitu nawigacyjnego: ```bash @@ -36,7 +36,7 @@ Więcej szczegółowych instrukcji można znaleźć w sekcji [Traff Monetizer do Instalując Traff Monetizer i udostępniając swój Internet, masz możliwość zarabiania pieniędzy online. Przy średnim miesięcznym zarobku wynoszącym około 2 USD na węzeł na IP, stanowi to potencjalne źródło dochodu. Należy pamiętać, że wypłaty są dostępne tylko w BTC. Zacznij zarabiać na swoim połączeniu internetowym już dziś! -Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Gdy skończysz, powinieneś [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referencje diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.ro.md b/content/other/install-traff-monetizer-easily-using-docker/index.ro.md index fe3be7b923076..abdc3eb728c8d 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.ro.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.ro.md @@ -22,7 +22,7 @@ Pentru a începe, creați-vă un cont la [traffmonetizer.com](https://traffmonet ### Instalați containerul Docker Urmați acești pași pentru a instala containerul Docker Traff Monetizer: -0. Aflați [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Aflați [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Copiați următorul șir de caractere și adăugați token-ul obținut din tabloul de bord: ```bash @@ -36,7 +36,7 @@ Pentru instrucțiuni mai detaliate, consultați [Traff Monetizer documentation]( Prin instalarea Traff Monetizer și partajarea internetului, aveți posibilitatea de a câștiga bani online. Cu un câștig mediu lunar de aproximativ 2 dolari pe nodul per IP, acesta prezintă o sursă potențială de venit. Rețineți că plățile sunt disponibile doar în BTC. Începeți să vă monetizați conexiunea la internet chiar astăzi! -Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +Odată ce ați terminat, ar trebui să [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Referință diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.ru.md b/content/other/install-traff-monetizer-easily-using-docker/index.ru.md index 5de535dc02898..da1d92fafd05c 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.ru.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.ru.md @@ -22,7 +22,7 @@ coverCaption: "" ### Установка контейнера Docker Выполните следующие шаги для установки Docker-контейнера Traff Monetizer: -0. Узнать [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0. Узнать [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1. Скопируйте следующую строку и добавьте к ней свой токен, полученный из панели управления: ```bash @@ -36,7 +36,7 @@ docker run -td --name traffmonetizer traffmonetizer/cli start accept --token YOU Установив Traff Monetizer и поделившись своим интернетом, вы получаете возможность зарабатывать деньги в Интернете. При среднемесячном заработке около 2 долл. за узел на IP он представляет собой потенциальный источник дохода. Следует помнить, что выплаты производятся только в BTC. Начните монетизировать свое интернет-соединение уже сегодня! -По окончании работы вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +По окончании работы вам следует [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## Reference diff --git a/content/other/install-traff-monetizer-easily-using-docker/index.zh.md b/content/other/install-traff-monetizer-easily-using-docker/index.zh.md index 6617d1b158721..c72aae18926d1 100644 --- a/content/other/install-traff-monetizer-easily-using-docker/index.zh.md +++ b/content/other/install-traff-monetizer-easily-using-docker/index.zh.md @@ -22,7 +22,7 @@ coverCaption: "" ### 安装 Docker 容器 按照以下步骤安装 Traff Monetizer Docker 容器: -0.学习 [how to install docker](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#installing-docker) +0.学习 [how to install docker](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#installing-docker) 1.复制以下字符串并添加从仪表板获取的令牌: ```bash @@ -36,7 +36,7 @@ docker run -td --name traffmonetizer traffmonetizer/cli start accept --token YOU 安装 Traff Monetizer 并分享您的互联网,您就有机会在网上赚钱。每个 IP 节点的平均月收入约为 2 美元,这是一个潜在的收入来源。请记住,只能以 BTC 支付。今天就开始为您的网络连接赚钱吧! -完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.ch/other/how-to-secure-internet-sharing-applications/) +完成后,您应该 [Learn How to Secure Internet Sharing Applications](https://simeononsecurity.com/other/how-to-secure-internet-sharing-applications/) ## 参考资料 diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ar.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ar.md index 399915209c496..705132effee74 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ar.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ar.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "تصلب", "طابعة HP t740", "عميل رفي cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "رسم كاريكاتوري لمعالج يلقي تعويذة لإصلاح جهاز كمبيوتر مجمّد ، مع فقاعة كلام تقول تم حل المشكلة" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense أو OPNsense أو HardenedBSD على جهاز HP t740 Thin Client ** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.bn.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.bn.md index e60058f44b18b..5dbe971e5c3cf 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.bn.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.bn.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "শক্ত বিএসডি", "HP t740", "প cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "একটি জাদুকরের একটি কার্টুন একটি হিমায়িত কম্পিউটার ঠিক করার জন্য একটি বানান কাস্ট করছে, একটি বক্তৃতা বুদবুদ সহ বলছে সমস্যা সমাধান" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- HP t740 থিন ক্লায়েন্টে pfSense, OPNsense, বা HardenedBSD** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ca.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ca.md index 6c42eba96de4a..0b0b76ffdce27 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ca.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ca.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "client prim", "servidor cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Un dibuix animat d'un mag fent un encanteri per arreglar un ordinador congelat, amb una bafarada que diu Problema resolt" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense o HardenedBSD al client prim HP t740** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.de.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.de.md index 30e8b6043de55..62089e6ad4f80 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.de.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.de.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "Dünner Kunde", "Heimse cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Eine Karikatur eines Zauberers, der einen Zauber wirkt, um einen eingefrorenen Computer zu reparieren, mit einer Sprechblase mit der Aufschrift „Problem gelöst“" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense oder HardenedBSD auf dem HP t740 Thin Client** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.en.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.en.md index dad1dd6c9d2a7..c1e1398f348a2 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.en.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.en.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "thin client", "home ser cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "A cartoon of a wizard casting a spell to fix a frozen computer, with a speech bubble saying Problem Solved" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- **Running pfSense, OPNsense, or HardenedBSD on the HP t740 Thin Client** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.es.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.es.md index 293b44f142187..15c9e15f5e445 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.es.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.es.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "BSD endurecido", "hp t740", "cliente ligero", "se cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Una caricatura de un mago lanzando un hechizo para reparar una computadora congelada, con una burbuja de diálogo que dice Problema resuelto" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense o HardenedBSD en el Thin Client HP t740** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.fr.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.fr.md index 6e8daf9be801d..ef302f2a57f07 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.fr.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.fr.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "BSD renforcé", "HP t740", "client léger", "serv cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Un dessin animé d'un assistant jetant un sort pour réparer un ordinateur gelé, avec une bulle disant Problème résolu" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense ou HardenedBSD sur le client léger HP t740** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.hi.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.hi.md index f926b15147fe0..f2e52522f52a6 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.hi.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.hi.md @@ -8,7 +8,7 @@ tags: ["pfSense", "ओपीएनसेंस", "कठोरबीएसडी cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "जमे हुए कंप्यूटर को ठीक करने के लिए जादू करने वाले जादूगर का कार्टून, जिसमें स्पीच बबल कह रहा है प्रॉब्लम सॉल्व्ड" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- HP t740 थिन क्लाइंट** पर pfSense, OPNsense, या HardenedBSD** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.it.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.it.md index ddd677ceee340..e87e93c974426 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.it.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.it.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "cliente sottile", "serv cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Un cartone animato di un mago che lancia un incantesimo per riparare un computer bloccato, con un fumetto che dice Problema risolto" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense o HardenedBSD sul thin client HP t740** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ja.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ja.md index 44964e3beccb8..feadb1e562f8d 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ja.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ja.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNセンス", "強化されたBSD", "HP t740", "シン・ク cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "フリーズしたコンピューターを修復するための呪文を唱えるウィザードの漫画。「問題が解決しました」という吹き出しが表示されます。" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- HP t740 Thin Client 上の pfSense、OPNsense、または HardenedBSD** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.nl.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.nl.md index a2423d7b071e1..ac928a4266582 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.nl.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.nl.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "dunne cliënt", "homese cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Een cartoon van een tovenaar die een spreuk uitspreekt om een bevroren computer te repareren, met een tekstballon die zegt Probleem opgelost" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense of HardenedBSD op de HP t740 Thin Client**. diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.pa.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.pa.md index eaa54dd127b84..7356e7957a061 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.pa.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.pa.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "ਸਖ਼ਤ ਬੀ.ਐੱਸ.ਡੀ", "HP t740", cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "ਇੱਕ ਵਿਜ਼ਾਰਡ ਦਾ ਇੱਕ ਕਾਰਟੂਨ ਜੋ ਇੱਕ ਜੰਮੇ ਹੋਏ ਕੰਪਿਊਟਰ ਨੂੰ ਠੀਕ ਕਰਨ ਲਈ ਇੱਕ ਸਪੈੱਲ ਕੱਢਦਾ ਹੈ, ਇੱਕ ਸਪੀਚ ਬੁਲਬੁਲੇ ਦੇ ਨਾਲ ਸਮੱਸਿਆ ਹੱਲ ਹੋ ਗਈ ਹੈ" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- HP t740 ਥਿਨ ਕਲਾਇੰਟ** 'ਤੇ pfSense, OPNsense, ਜਾਂ HardenedBSD diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.pl.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.pl.md index cf46fa331850c..17b831511156f 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.pl.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.pl.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "cienki klient", "serwer cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Kreskówka z czarodziejem rzucającym zaklęcie, aby naprawić zamrożony komputer, z dymkiem mówiącym o rozwiązaniu problemu" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense lub HardenedBSD na HP t740 Thin Client**. diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.pt.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.pt.md index d5dc26234ee8a..e9dab4e25b103 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.pt.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.pt.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "cliente magro", "servid cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Uma caricatura de um mago lançando um feitiço para consertar um computador congelado, com um balão dizendo Problema resolvido" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense ou HardenedBSD no HP t740 Thin Client** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ro.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ro.md index f5c0cbba4bc5f..11888d71b852d 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ro.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ro.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "HardenedBSD", "HP t740", "client slab", "serverul cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Un desen animat cu un vrăjitor care aruncă o vrajă pentru a repara un computer înghețat, cu un balon care spune Problema rezolvată" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense sau HardenedBSD pe clientul subțire HP t740** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ru.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ru.md index 28d613052887a..f3c6b0618acdd 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.ru.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.ru.md @@ -8,7 +8,7 @@ tags: ["pfSense", "OPNsense", "ЗакаленнаяBSD", "HP т740", "Тонки cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "Карикатура, на которой волшебник произносит заклинание, чтобы починить зависший компьютер, с речевым пузырем, говорящим, что проблема решена" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- pfSense, OPNsense или HardenedBSD на тонком клиенте HP t740** diff --git a/content/other/installing-pfsense-on-hp-t740-thin-client/index.zh.md b/content/other/installing-pfsense-on-hp-t740-thin-client/index.zh.md index cf081179e8001..e3c25b6500057 100644 --- a/content/other/installing-pfsense-on-hp-t740-thin-client/index.zh.md +++ b/content/other/installing-pfsense-on-hp-t740-thin-client/index.zh.md @@ -8,7 +8,7 @@ tags: ["感知", "OPNsense", "强化BSD", "惠普t740", "瘦客户端", "家庭 cover: "/img/cover/A_cartoon_of_a_wizard_casting_a_spell_to_fix_a_frozen_computer.png" coverAlt: "一幅卡通画,画的是巫师施咒修复冻结的计算机,并带有一个对话泡泡,上面写着“问题已解决”" coverCaption: "" -canonical: "https://simeononsecurity.ch/guides/installing-pfsense-on-hp-t740-thin-client/" +canonical: "https://simeononsecurity.com/guides/installing-pfsense-on-hp-t740-thin-client/" --- HP t740 瘦客户机上的 pfSense、OPNsense 或 HardenedBSD** diff --git a/content/other/mastering-decentralization-setting-up-presearch-node/index.en.md b/content/other/mastering-decentralization-setting-up-presearch-node/index.en.md index 4f79a36e5eeda..f8d2ca010ede1 100644 --- a/content/other/mastering-decentralization-setting-up-presearch-node/index.en.md +++ b/content/other/mastering-decentralization-setting-up-presearch-node/index.en.md @@ -17,7 +17,7 @@ In the world of decentralized search engines, operating a Presearch Node can be ## Introduction -[Presearch](https://simeononsecurity.ch/other/exploring-presearch-as-a-alternative-to-google/) is a decentralized search engine that offers an alternative to the dominance of Big Tech companies in the online search landscape. By operating a Presearch Node, you contribute to a more open and decentralized internet while earning Presearch PRE tokens. +[Presearch](https://simeononsecurity.com/other/exploring-presearch-as-a-alternative-to-google/) is a decentralized search engine that offers an alternative to the dominance of Big Tech companies in the online search landscape. By operating a Presearch Node, you contribute to a more open and decentralized internet while earning Presearch PRE tokens. ______ {{< inarticle-dark >}} diff --git a/content/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/index.en.md b/content/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/index.en.md index df56c5a507e8d..0c014f72f84c1 100644 --- a/content/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/index.en.md +++ b/content/other/onocoy-gps-gnss-reciever-basestation-on-a-budget/index.en.md @@ -81,10 +81,10 @@ For super low power Raspberry Pi equivalent but on x64 platform. - [TRIGKEY Mini Computer](https://amzn.to/3XkbXkS) ### Ultra Low Power / Low Budget -If you're interested in a lower power and/or low budget setup, read our guide on [How to Set Up a GPS/GNSS Bases Station on an ESP32](https://simeononsecurity.ch/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/). +If you're interested in a lower power and/or low budget setup, read our guide on [How to Set Up a GPS/GNSS Bases Station on an ESP32](https://simeononsecurity.com/guides/budget-diy-gps-gnss-base-station-setup-esp32-um980/). ### Compute Notable Mentions -Older Raspberry Pi models (1, 2, 3) should be sufficient. But newer models should be significantly more efficient and allow you do run multiple [low powered mining setups](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/) on a single device. This is why we recommend newer compute hardware. +Older Raspberry Pi models (1, 2, 3) should be sufficient. But newer models should be significantly more efficient and allow you do run multiple [low powered mining setups](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/) on a single device. This is why we recommend newer compute hardware. ## Recommended GPS Receivers for DIY Onocoy Deployments There are many recievers on the market but at a bare minimum it must support [**RTCM (Radio Technical Commission for Maritime Services)**](https://en.wikipedia.org/wiki/RTCM_SC-104) and ideally have the ability to be hooked up to an antenna outside of the install location with 360 degree unobstructed view of the sky. @@ -505,7 +505,7 @@ So, **go ahead and set up your Onocoy Reference Station**, refine your skills, a Stay inspired, stay innovative, and keep pushing the **boundaries of what's possible with technology**. -Lastly, check out our article on more [low powered mining setups](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/). +Lastly, check out our article on more [low powered mining setups](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/). ## References diff --git a/content/other/spacemesh-mining-eco-friendly-decentralized-rewards/index.en.md b/content/other/spacemesh-mining-eco-friendly-decentralized-rewards/index.en.md index 3d1ba02319d5b..e2b4ee8e4ca86 100644 --- a/content/other/spacemesh-mining-eco-friendly-decentralized-rewards/index.en.md +++ b/content/other/spacemesh-mining-eco-friendly-decentralized-rewards/index.en.md @@ -15,7 +15,7 @@ coverCaption: "Mining to the Stars! Spacemesh's Eco-Friendly Rewards Await." ## Introduction -[Spacemesh](https://www.spacemesh.io/) is a novel and innovative cryptocurrency that employs a unique mining approach known as [**Spacemesh mining**](https://simeononsecurity.ch/other/efficient-spacemesh-mining-multiple-gpus-guide/). Unlike traditional proof-of-work (PoW) or proof-of-stake (PoS) mechanisms, [Spacemesh](https://simeononsecurity.ch/other/efficient-spacemesh-mining-multiple-gpus-guide/) utilizes a **proof-of-space-time (PoST)** consensus algorithm. This groundbreaking concept aims to be more environmentally friendly and decentralized while ensuring network security and efficiency. +[Spacemesh](https://www.spacemesh.io/) is a novel and innovative cryptocurrency that employs a unique mining approach known as [**Spacemesh mining**](https://simeononsecurity.com/other/efficient-spacemesh-mining-multiple-gpus-guide/). Unlike traditional proof-of-work (PoW) or proof-of-stake (PoS) mechanisms, [Spacemesh](https://simeononsecurity.com/other/efficient-spacemesh-mining-multiple-gpus-guide/) utilizes a **proof-of-space-time (PoST)** consensus algorithm. This groundbreaking concept aims to be more environmentally friendly and decentralized while ensuring network security and efficiency. In this article, we will explore the ins and outs of Spacemesh mining, understand how it works, and discuss its advantages and potential challenges. Whether you are a seasoned crypto enthusiast or a newcomer to the world of cryptocurrencies, this guide will provide you with valuable insights into the fascinating world of Spacemesh mining. diff --git a/content/other/t-mobile-home-internet-benefits-connectivity-features/index.en.md b/content/other/t-mobile-home-internet-benefits-connectivity-features/index.en.md index d7cb84b00f9b8..bc29081ca4b0d 100644 --- a/content/other/t-mobile-home-internet-benefits-connectivity-features/index.en.md +++ b/content/other/t-mobile-home-internet-benefits-connectivity-features/index.en.md @@ -75,7 +75,7 @@ When choosing a home internet service, it's crucial to assess the security measu T-Mobile's home internet service utilizes encryption protocols to secure data transmission between your devices and their network. They employ industry-standard encryption methods, such as WPA2 or WPA3, to protect your connection from unauthorized access and ensure the privacy of your online activities. ### Password and Network Security -To maintain the security of your T-Mobile home internet connection, it's important to follow best practices for password management. T-Mobile provides guidelines for creating [strong passwords](https://simeononsecurity.ch/articles/how-to-create-strong-passwords/) and recommends changing them periodically. Additionally, they advise against sharing your network password with unauthorized individuals to prevent unauthorized access to your network. +To maintain the security of your T-Mobile home internet connection, it's important to follow best practices for password management. T-Mobile provides guidelines for creating [strong passwords](https://simeononsecurity.com/articles/how-to-create-strong-passwords/) and recommends changing them periodically. Additionally, they advise against sharing your network password with unauthorized individuals to prevent unauthorized access to your network. ### Device and Endpoint Security While T-Mobile safeguards the security of your home internet connection, it's crucial to ensure that your devices and endpoints are also protected. Implementing robust security measures on your devices, such as using up-to-date antivirus software, enabling firewalls, and practicing safe browsing habits, adds an extra layer of security to your online experience. diff --git a/content/other/ultimate-guide-money-earning-apps-mobile-devices/index.en.md b/content/other/ultimate-guide-money-earning-apps-mobile-devices/index.en.md index d705b8788f753..3f4467cff11dc 100644 --- a/content/other/ultimate-guide-money-earning-apps-mobile-devices/index.en.md +++ b/content/other/ultimate-guide-money-earning-apps-mobile-devices/index.en.md @@ -71,7 +71,7 @@ ______ ## **Advanced Approach**: Exploring Passive Crypto Mining -For those seeking an alternative path to passive earnings without utilizing their mobile devices extensively, consider delving into a more advanced strategy. Check out [this guide](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/) that walks you through the process of setting up profitable, low-powered crypto miners. This approach opens up opportunities for generating income through crypto mining while bypassing the need to rely heavily on your mobile phone. +For those seeking an alternative path to passive earnings without utilizing their mobile devices extensively, consider delving into a more advanced strategy. Check out [this guide](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/) that walks you through the process of setting up profitable, low-powered crypto miners. This approach opens up opportunities for generating income through crypto mining while bypassing the need to rely heavily on your mobile phone. ______ @@ -81,7 +81,7 @@ While money earning apps offer enticing opportunities for generating extra incom One primary concern is the potential exposure to **malicious activities**, including malware and trackers. Sharing your internet connection could expose your device to harmful software or unauthorized data collection. To address these concerns, it's advisable to implement security measures that safeguard your online experience. -To learn more about mitigating security risks and enhancing your protection while using these apps, refer to resources like [SimeonOnSecurity's guide](https://simeononsecurity.ch/other/creating-profitable-low-powered-crypto-miners/#increase-security-by-blocking-malware-and-trackers). This guide provides insights into increasing security by blocking malware and trackers, helping you maintain a safe and secure environment while leveraging these money earning apps. +To learn more about mitigating security risks and enhancing your protection while using these apps, refer to resources like [SimeonOnSecurity's guide](https://simeononsecurity.com/other/creating-profitable-low-powered-crypto-miners/#increase-security-by-blocking-malware-and-trackers). This guide provides insights into increasing security by blocking malware and trackers, helping you maintain a safe and secure environment while leveraging these money earning apps. By staying informed about security best practices and taking proactive steps to protect your device and personal information, you can confidently navigate the world of money earning apps without compromising your online security. diff --git a/content/privacypolicy/index.de.md b/content/privacypolicy/index.de.md index 9e50b697d904e..8f33cf3f9ebc8 100644 --- a/content/privacypolicy/index.de.md +++ b/content/privacypolicy/index.de.md @@ -3,7 +3,7 @@ title: "Datenschutzrichtlinien: Sammlung von Informationen, Nutzung und Zustimmu date: 2020-08-08 --- -Bei SimeonOnSecurity, erreichbar unter https://simeononsecurity.ch, ist eine unserer Hauptprioritäten der Schutz der Privatsphäre unserer Besucher. Diese Datenschutzrichtlinie enthält die Arten von Informationen, die von SimeonOnSecurity gesammelt und aufgezeichnet werden, und wie wir sie verwenden. +Bei SimeonOnSecurity, erreichbar unter https://simeononsecurity.com, ist eine unserer Hauptprioritäten der Schutz der Privatsphäre unserer Besucher. Diese Datenschutzrichtlinie enthält die Arten von Informationen, die von SimeonOnSecurity gesammelt und aufgezeichnet werden, und wie wir sie verwenden. Wenn Sie weitere Fragen haben oder mehr Informationen über unsere Datenschutzpolitik benötigen, zögern Sie nicht, uns zu kontaktieren. diff --git a/content/privacypolicy/index.en.md b/content/privacypolicy/index.en.md index 0a81320b1ca7b..e0a9eb0e891fb 100644 --- a/content/privacypolicy/index.en.md +++ b/content/privacypolicy/index.en.md @@ -6,7 +6,7 @@ tags: ["privacy policy", "information collection", "data usage", "visitor consen description: "Learn how SimeonOnSecurity collects, uses, and protects visitor information through its comprehensive Privacy Policy, ensuring consent and online privacy." --- -At SimeonOnSecurity, accessible from https://simeononsecurity.ch, one of our main priorities is the privacy of our visitors. This Privacy Policy document contains types of information that is collected and recorded by SimeonOnSecurity and how we use it. +At SimeonOnSecurity, accessible from https://simeononsecurity.com, one of our main priorities is the privacy of our visitors. This Privacy Policy document contains types of information that is collected and recorded by SimeonOnSecurity and how we use it. If you have additional questions or require more information about our Privacy Policy, do not hesitate to contact us. diff --git a/content/privacypolicy/index.es.md b/content/privacypolicy/index.es.md index 9fa23a76d53f2..830324c607aaa 100644 --- a/content/privacypolicy/index.es.md +++ b/content/privacypolicy/index.es.md @@ -3,7 +3,7 @@ title: "Política de privacidad: Recogida de información, uso y consentimiento date: 2020-08-08 --- -En SimeonOnSecurity, accesible desde https://simeononsecurity.ch, una de nuestras principales prioridades es la privacidad de nuestros visitantes. Este documento de política de privacidad contiene los tipos de información que recoge y registra SimeonOnSecurity y cómo la utilizamos. +En SimeonOnSecurity, accesible desde https://simeononsecurity.com, una de nuestras principales prioridades es la privacidad de nuestros visitantes. Este documento de política de privacidad contiene los tipos de información que recoge y registra SimeonOnSecurity y cómo la utilizamos. Si tiene preguntas adicionales o necesita más información sobre nuestra Política de Privacidad, no dude en ponerse en contacto con nosotros. diff --git a/content/privacypolicy/index.fr.md b/content/privacypolicy/index.fr.md index f0c7cb7ccdc10..ba57359b9888e 100644 --- a/content/privacypolicy/index.fr.md +++ b/content/privacypolicy/index.fr.md @@ -3,7 +3,7 @@ title: "Politique de confidentialité : Collecte, utilisation et consentement de date: 2020-08-08 --- -Chez SimeonOnSecurity, accessible à partir de https://simeononsecurity.ch, l'une de nos principales priorités est la protection de la vie privée de nos visiteurs. La présente politique de confidentialité décrit les types d'informations collectées et enregistrées par SimeonOnSecurity, ainsi que la manière dont elles sont utilisées. +Chez SimeonOnSecurity, accessible à partir de https://simeononsecurity.com, l'une de nos principales priorités est la protection de la vie privée de nos visiteurs. La présente politique de confidentialité décrit les types d'informations collectées et enregistrées par SimeonOnSecurity, ainsi que la manière dont elles sont utilisées. Si vous avez des questions supplémentaires ou si vous souhaitez obtenir plus d'informations sur notre politique de confidentialité, n'hésitez pas à nous contacter. diff --git a/content/privacypolicy/index.it.md b/content/privacypolicy/index.it.md index 348995a7c1e72..569bbcb81c926 100644 --- a/content/privacypolicy/index.it.md +++ b/content/privacypolicy/index.it.md @@ -3,7 +3,7 @@ title: "Informativa sulla privacy: Raccolta, uso e consenso delle informazioni | date: 2020-08-08 --- -In SimeonOnSecurity, accessibile da https://simeononsecurity.ch, una delle nostre principali priorità è la privacy dei nostri visitatori. Questo documento sulla privacy contiene i tipi di informazioni che vengono raccolte e registrate da SimeonOnSecurity e il modo in cui vengono utilizzate. +In SimeonOnSecurity, accessibile da https://simeononsecurity.com, una delle nostre principali priorità è la privacy dei nostri visitatori. Questo documento sulla privacy contiene i tipi di informazioni che vengono raccolte e registrate da SimeonOnSecurity e il modo in cui vengono utilizzate. Se avete ulteriori domande o desiderate maggiori informazioni sulla nostra Politica sulla privacy, non esitate a contattarci. diff --git a/content/privacypolicy/index.ja.md b/content/privacypolicy/index.ja.md index b49bced5f6316..d5080cf3a4614 100644 --- a/content/privacypolicy/index.ja.md +++ b/content/privacypolicy/index.ja.md @@ -3,7 +3,7 @@ title: "プライバシーポリシー情報の収集、利用、同意|Simeon date: 2020-08-08 --- -https://simeononsecurity.ch からアクセスできるSimeonOnSecurityでは、私たちの主な優先事項の一つは、訪問者のプライバシーです。このプライバシーポリシーの文書には、SimeonOnSecurityによって収集され記録される情報の種類とその使用方法が記載されています。 +https://simeononsecurity.com からアクセスできるSimeonOnSecurityでは、私たちの主な優先事項の一つは、訪問者のプライバシーです。このプライバシーポリシーの文書には、SimeonOnSecurityによって収集され記録される情報の種類とその使用方法が記載されています。 私たちの個人情報保護方針について、ご質問がある場合、またはより詳細な情報が必要な場合は、ご遠慮なくご連絡ください。 diff --git a/content/privacypolicy/index.nl.md b/content/privacypolicy/index.nl.md index 4d0a138b16ad1..06faeb95e9d6f 100644 --- a/content/privacypolicy/index.nl.md +++ b/content/privacypolicy/index.nl.md @@ -3,7 +3,7 @@ title: "Privacybeleid: Informatieverzameling, gebruik en toestemming | SimeonOnS date: 2020-08-08 --- -Bij SimeonOnSecurity, bereikbaar via https://simeononsecurity.ch, is één van onze belangrijkste prioriteiten de privacy van onze bezoekers. Dit Privacybeleid document bevat soorten informatie die wordt verzameld en opgeslagen door SimeonOnSecurity en hoe we het gebruiken. +Bij SimeonOnSecurity, bereikbaar via https://simeononsecurity.com, is één van onze belangrijkste prioriteiten de privacy van onze bezoekers. Dit Privacybeleid document bevat soorten informatie die wordt verzameld en opgeslagen door SimeonOnSecurity en hoe we het gebruiken. Als u nog vragen heeft of meer informatie wenst over onze Privacy Policy, aarzel dan niet om contact met ons op te nemen. diff --git a/content/privacypolicy/index.pl.md b/content/privacypolicy/index.pl.md index ee89c6e9ff81b..8592b1d370534 100644 --- a/content/privacypolicy/index.pl.md +++ b/content/privacypolicy/index.pl.md @@ -3,7 +3,7 @@ title: "Polityka prywatności: Gromadzenie informacji, wykorzystanie i zgoda | S date: 2020-08-08 --- -W SimeonOnSecurity, dostępnym pod adresem https://simeononsecurity.ch, jednym z naszych głównych priorytetów jest prywatność odwiedzających. Niniejsza Polityka prywatności zawiera rodzaje informacji, które są gromadzone i rejestrowane przez SimeonOnSecurity oraz sposób, w jaki je wykorzystujemy. +W SimeonOnSecurity, dostępnym pod adresem https://simeononsecurity.com, jednym z naszych głównych priorytetów jest prywatność odwiedzających. Niniejsza Polityka prywatności zawiera rodzaje informacji, które są gromadzone i rejestrowane przez SimeonOnSecurity oraz sposób, w jaki je wykorzystujemy. Jeśli masz dodatkowe pytania lub potrzebujesz więcej informacji na temat naszej Polityki prywatności, nie wahaj się z nami skontaktować. diff --git a/content/privacypolicy/index.ro.md b/content/privacypolicy/index.ro.md index 11e061b099789..bbd5dc89624d5 100644 --- a/content/privacypolicy/index.ro.md +++ b/content/privacypolicy/index.ro.md @@ -3,7 +3,7 @@ title: "Politica de confidențialitate: Colectarea informațiilor, utilizarea ș date: 2020-08-08 --- -La SimeonOnSecurity, accesibil de la https://simeononsecurity.ch, una dintre prioritățile noastre principale este confidențialitatea vizitatorilor noștri. Acest document privind politica de confidențialitate conține tipurile de informații care sunt colectate și înregistrate de către SimeonOnSecurity și modul în care le folosim. +La SimeonOnSecurity, accesibil de la https://simeononsecurity.com, una dintre prioritățile noastre principale este confidențialitatea vizitatorilor noștri. Acest document privind politica de confidențialitate conține tipurile de informații care sunt colectate și înregistrate de către SimeonOnSecurity și modul în care le folosim. Dacă aveți întrebări suplimentare sau aveți nevoie de mai multe informații despre Politica noastră de confidențialitate, nu ezitați să ne contactați. diff --git a/content/privacypolicy/index.ru.md b/content/privacypolicy/index.ru.md index e11c5509e12e4..5f330ff86c213 100644 --- a/content/privacypolicy/index.ru.md +++ b/content/privacypolicy/index.ru.md @@ -3,7 +3,7 @@ title: "Политика конфиденциальности: Сбор инфо date: 2020-08-08 --- -Для компании SimeonOnSecurity, доступной по адресу https://simeononsecurity.ch, одним из главных приоритетов является конфиденциальность наших посетителей. В данном документе, посвященном политике конфиденциальности, указаны типы информации, которую собирает и записывает компания SimeonOnSecurity, а также порядок ее использования. +Для компании SimeonOnSecurity, доступной по адресу https://simeononsecurity.com, одним из главных приоритетов является конфиденциальность наших посетителей. В данном документе, посвященном политике конфиденциальности, указаны типы информации, которую собирает и записывает компания SimeonOnSecurity, а также порядок ее использования. Если у Вас возникнут дополнительные вопросы или потребуется дополнительная информация о нашей Политике конфиденциальности, не стесняйтесь обращаться к нам. diff --git a/content/privacypolicy/index.zh.md b/content/privacypolicy/index.zh.md index 335a6d88872b9..5cf7e2c759bf2 100644 --- a/content/privacypolicy/index.zh.md +++ b/content/privacypolicy/index.zh.md @@ -3,7 +3,7 @@ title: "隐私政策:信息收集、使用和同意 | SimeonOnSecurity" date: 2020-08-08 --- -在 SimeonOnSecurity(可从 https://simeononsecurity.ch 访问),我们的首要任务之一是保护访问者的隐私。本隐私政策文件包含 SimeonOnSecurity 收集和记录的信息类型以及我们如何使用这些信息。 +在 SimeonOnSecurity(可从 https://simeononsecurity.com 访问),我们的首要任务之一是保护访问者的隐私。本隐私政策文件包含 SimeonOnSecurity 收集和记录的信息类型以及我们如何使用这些信息。 如果您对我们的隐私政策有其他疑问或需要更多信息,请随时联系我们。 diff --git a/content/recommendations/certifications/index.de.md b/content/recommendations/certifications/index.de.md index f00fa51a444f4..e676c903adfc9 100644 --- a/content/recommendations/certifications/index.de.md +++ b/content/recommendations/certifications/index.de.md @@ -68,8 +68,8 @@ Zusätzlich zu den oben aufgeführten Zertifizierungen gibt es noch einige ander Um sich auf diese Zertifizierungen vorzubereiten, ist es wichtig, Zugang zu hochwertigen Lernressourcen zu haben. SimeonOnSecurity empfiehlt die folgenden: -- [Books](https://simeononsecurity.ch/recommendations/books/) Diese Seite enthält eine Liste empfohlener Bücher, um sich über verschiedene Themen im Bereich Cyber und IT zu informieren. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Auf dieser Seite finden Sie eine Liste empfohlener Schulungskurse und Bootcamps, die Sie bei der Vorbereitung auf Zertifizierungen unterstützen können. +- [Books](https://simeononsecurity.com/recommendations/books/) Diese Seite enthält eine Liste empfohlener Bücher, um sich über verschiedene Themen im Bereich Cyber und IT zu informieren. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Auf dieser Seite finden Sie eine Liste empfohlener Schulungskurse und Bootcamps, die Sie bei der Vorbereitung auf Zertifizierungen unterstützen können. ## Visualisieren diff --git a/content/recommendations/certifications/index.en.md b/content/recommendations/certifications/index.en.md index 31bec5b38a3f3..81efed230637a 100644 --- a/content/recommendations/certifications/index.en.md +++ b/content/recommendations/certifications/index.en.md @@ -68,8 +68,8 @@ In addition to the certifications listed above, there are several other certific To prepare for these certifications, it's important to have access to quality learning resources. SimeonOnSecurity recommends the following: -- [Books](https://simeononsecurity.ch/recommendations/books/): This page includes a list of recommended books for learning about various topics in Cyber and IT fields. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/): This page includes a list of recommended training courses and bootcamps that can help you prepare for certifications. +- [Books](https://simeononsecurity.com/recommendations/books/): This page includes a list of recommended books for learning about various topics in Cyber and IT fields. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/): This page includes a list of recommended training courses and bootcamps that can help you prepare for certifications. ## Visualize diff --git a/content/recommendations/certifications/index.es.md b/content/recommendations/certifications/index.es.md index 7ce7774adb920..5f168151eeb51 100644 --- a/content/recommendations/certifications/index.es.md +++ b/content/recommendations/certifications/index.es.md @@ -68,8 +68,8 @@ Además de las certificaciones enumeradas anteriormente, hay varias otras certif Para preparar estas certificaciones, es importante tener acceso a recursos de aprendizaje de calidad. SimeonOnSecurity recomienda los siguientes: -- [Books](https://simeononsecurity.ch/recommendations/books/) Esta página incluye una lista de libros recomendados para aprender sobre diversos temas de los ámbitos cibernético e informático. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Esta página incluye una lista de cursos de formación y bootcamps recomendados que pueden ayudarle a prepararse para las certificaciones. +- [Books](https://simeononsecurity.com/recommendations/books/) Esta página incluye una lista de libros recomendados para aprender sobre diversos temas de los ámbitos cibernético e informático. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Esta página incluye una lista de cursos de formación y bootcamps recomendados que pueden ayudarle a prepararse para las certificaciones. ## Visualizar diff --git a/content/recommendations/certifications/index.fr.md b/content/recommendations/certifications/index.fr.md index 9177873d48426..5b6da788c894b 100644 --- a/content/recommendations/certifications/index.fr.md +++ b/content/recommendations/certifications/index.fr.md @@ -68,8 +68,8 @@ Outre les certifications énumérées ci-dessus, plusieurs autres certifications Pour se préparer à ces certifications, il est important d'avoir accès à des ressources d'apprentissage de qualité. SimeonOnSecurity recommande les ressources suivantes : -- [Books](https://simeononsecurity.ch/recommendations/books/) Cette page comprend une liste de livres recommandés pour apprendre divers sujets dans les domaines de la cybernétique et des technologies de l'information. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Cette page comprend une liste de cours de formation et de bootcamps recommandés qui peuvent vous aider à vous préparer aux certifications. +- [Books](https://simeononsecurity.com/recommendations/books/) Cette page comprend une liste de livres recommandés pour apprendre divers sujets dans les domaines de la cybernétique et des technologies de l'information. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Cette page comprend une liste de cours de formation et de bootcamps recommandés qui peuvent vous aider à vous préparer aux certifications. ## Visualiser diff --git a/content/recommendations/certifications/index.it.md b/content/recommendations/certifications/index.it.md index 769338c36655f..397b94ec39ca5 100644 --- a/content/recommendations/certifications/index.it.md +++ b/content/recommendations/certifications/index.it.md @@ -68,8 +68,8 @@ Oltre alle certificazioni sopra elencate, ci sono diverse altre certificazioni c Per prepararsi a queste certificazioni, è importante avere accesso a risorse di apprendimento di qualità. SimeonOnSecurity consiglia le seguenti: -- [Books](https://simeononsecurity.ch/recommendations/books/) Questa pagina contiene un elenco di libri consigliati per l'apprendimento di vari argomenti nei settori Cyber e IT. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Questa pagina contiene un elenco di corsi di formazione e bootcamp consigliati che possono aiutare a prepararsi alle certificazioni. +- [Books](https://simeononsecurity.com/recommendations/books/) Questa pagina contiene un elenco di libri consigliati per l'apprendimento di vari argomenti nei settori Cyber e IT. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Questa pagina contiene un elenco di corsi di formazione e bootcamp consigliati che possono aiutare a prepararsi alle certificazioni. ## Visualizza diff --git a/content/recommendations/certifications/index.ja.md b/content/recommendations/certifications/index.ja.md index 6ee332a536559..1bb2215a9f071 100644 --- a/content/recommendations/certifications/index.ja.md +++ b/content/recommendations/certifications/index.ja.md @@ -68,8 +68,8 @@ SimeonOnSecurityでは、その分野の専門家になるために、以下の これらの資格に備えるには、質の高い学習リソースにアクセスすることが重要です。SimeonOnSecurityでは、以下を推奨しています: -- [Books](https://simeononsecurity.ch/recommendations/books/)このページでは、サイバー・IT分野の様々なトピックを学ぶためのおすすめ書籍の一覧を掲載しています。 -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/)このページでは、資格取得の準備に役立つ、おすすめのトレーニングコースやブートキャンプを紹介しています。 +- [Books](https://simeononsecurity.com/recommendations/books/)このページでは、サイバー・IT分野の様々なトピックを学ぶためのおすすめ書籍の一覧を掲載しています。 +- [Training](https://simeononsecurity.com/recommendations/learning_resources/)このページでは、資格取得の準備に役立つ、おすすめのトレーニングコースやブートキャンプを紹介しています。 ## ビジュアライズ diff --git a/content/recommendations/certifications/index.nl.md b/content/recommendations/certifications/index.nl.md index 06dd3d47a56f6..52642cfcde251 100644 --- a/content/recommendations/certifications/index.nl.md +++ b/content/recommendations/certifications/index.nl.md @@ -68,8 +68,8 @@ Naast de bovenstaande certificeringen zijn er nog een aantal andere certificerin Om je voor te bereiden op deze certificeringen is het belangrijk om toegang te hebben tot kwalitatief goede leermiddelen. SimeonOnSecurity raadt het volgende aan: -- [Books](https://simeononsecurity.ch/recommendations/books/) Deze pagina bevat een lijst met aanbevolen boeken voor het leren over verschillende onderwerpen op het gebied van Cyber en IT. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Deze pagina bevat een lijst met aanbevolen trainingen en bootcamps die je kunnen helpen je voor te bereiden op certificeringen. +- [Books](https://simeononsecurity.com/recommendations/books/) Deze pagina bevat een lijst met aanbevolen boeken voor het leren over verschillende onderwerpen op het gebied van Cyber en IT. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Deze pagina bevat een lijst met aanbevolen trainingen en bootcamps die je kunnen helpen je voor te bereiden op certificeringen. ## Visualiseren diff --git a/content/recommendations/certifications/index.pl.md b/content/recommendations/certifications/index.pl.md index 599093b5e16d5..10222f890717b 100644 --- a/content/recommendations/certifications/index.pl.md +++ b/content/recommendations/certifications/index.pl.md @@ -68,8 +68,8 @@ Oprócz certyfikatów wymienionych powyżej, istnieje kilka innych certyfikatów Aby przygotować się do tych certyfikatów, ważne jest, aby mieć dostęp do wysokiej jakości zasobów edukacyjnych. SimeonOnSecurity zaleca następujące: -- [Books](https://simeononsecurity.ch/recommendations/books/) Ta strona zawiera listę polecanych książek do nauki na różne tematy w dziedzinie cyberbezpieczeństwa i IT. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Ta strona zawiera listę zalecanych kursów szkoleniowych i bootcampów, które mogą pomóc w przygotowaniu się do certyfikacji. +- [Books](https://simeononsecurity.com/recommendations/books/) Ta strona zawiera listę polecanych książek do nauki na różne tematy w dziedzinie cyberbezpieczeństwa i IT. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Ta strona zawiera listę zalecanych kursów szkoleniowych i bootcampów, które mogą pomóc w przygotowaniu się do certyfikacji. ## Visualize diff --git a/content/recommendations/certifications/index.ro.md b/content/recommendations/certifications/index.ro.md index 6abadf25e439f..2756021624346 100644 --- a/content/recommendations/certifications/index.ro.md +++ b/content/recommendations/certifications/index.ro.md @@ -68,8 +68,8 @@ Pe lângă certificările enumerate mai sus, există alte câteva certificări c Pentru a vă pregăti pentru aceste certificări, este important să aveți acces la resurse de învățare de calitate. SimeonOnSecurity recomandă următoarele: -- [Books](https://simeononsecurity.ch/recommendations/books/) Această pagină include o listă de cărți recomandate pentru a învăța despre diverse subiecte din domeniile Cyber și IT. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) Această pagină include o listă de cursuri de formare și bootcamps recomandate care vă pot ajuta să vă pregătiți pentru certificări. +- [Books](https://simeononsecurity.com/recommendations/books/) Această pagină include o listă de cărți recomandate pentru a învăța despre diverse subiecte din domeniile Cyber și IT. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) Această pagină include o listă de cursuri de formare și bootcamps recomandate care vă pot ajuta să vă pregătiți pentru certificări. ## Vizualizare diff --git a/content/recommendations/certifications/index.ru.md b/content/recommendations/certifications/index.ru.md index becbca627474a..d6bdc28473bdd 100644 --- a/content/recommendations/certifications/index.ru.md +++ b/content/recommendations/certifications/index.ru.md @@ -68,8 +68,8 @@ tags: ["Сертификация в области кибернетики и и Для подготовки к этим сертификациям важно иметь доступ к качественным учебным ресурсам. SimeonOnSecurity рекомендует следующее: -- [Books](https://simeononsecurity.ch/recommendations/books/) На этой странице представлен список рекомендуемой литературы для изучения различных тем в области кибернетики и информационных технологий. -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/) На этой странице представлен список рекомендуемых учебных курсов и загрузочных центров, которые помогут вам подготовиться к сертификации. +- [Books](https://simeononsecurity.com/recommendations/books/) На этой странице представлен список рекомендуемой литературы для изучения различных тем в области кибернетики и информационных технологий. +- [Training](https://simeononsecurity.com/recommendations/learning_resources/) На этой странице представлен список рекомендуемых учебных курсов и загрузочных центров, которые помогут вам подготовиться к сертификации. ## Visualize diff --git a/content/recommendations/certifications/index.zh.md b/content/recommendations/certifications/index.zh.md index d8d6f237e42dd..ce0e7a68f69da 100644 --- a/content/recommendations/certifications/index.zh.md +++ b/content/recommendations/certifications/index.zh.md @@ -68,8 +68,8 @@ tags: ["网络和 IT 认证", "CompTIA", "思科", "安全理事会", "ISC2", " 要准备这些认证,获得优质的学习资源非常重要。SimeonOnSecurity 推荐以下资源: -- [Books](https://simeononsecurity.ch/recommendations/books/)本页包含学习网络和 IT 领域各种主题的推荐书目。 -- [Training](https://simeononsecurity.ch/recommendations/learning_resources/)本页包含可帮助您准备认证的推荐培训课程和训练营列表。 +- [Books](https://simeononsecurity.com/recommendations/books/)本页包含学习网络和 IT 领域各种主题的推荐书目。 +- [Training](https://simeononsecurity.com/recommendations/learning_resources/)本页包含可帮助您准备认证的推荐培训课程和训练营列表。 ## 视觉 diff --git a/content/recommendations/learning_resources/index.de.md b/content/recommendations/learning_resources/index.de.md index 16a18c5c750b6..15ab04f2c0b6a 100644 --- a/content/recommendations/learning_resources/index.de.md +++ b/content/recommendations/learning_resources/index.de.md @@ -27,7 +27,7 @@ Für diejenigen, die sich für Cybersicherheit interessieren, gibt es mehrere Re - [**INE**](https://ine.com/) INE bietet sowohl kostenlose als auch kostenpflichtige hochqualitative Cybersicherheitslabore und Schulungen an. - [**Immersive Labs**](https://www.immersivelabs.com/) Diese Plattform bietet kostenlose Cybersicherheitslabore an, wobei auch kostenpflichtige Angebote verfügbar sind. Kostenlos für aktive Studenten. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Diese Plattform bietet kostenlose Cyber Security Labs, aber auch kostenpflichtige Angebote. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) Auch kostenpflichtige Angebote sind verfügbar. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) Auch kostenpflichtige Angebote sind verfügbar. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Diese Plattform bietet geführte CTF-Herausforderungen mit der Option einer kostenpflichtigen Mitgliedschaft. ## Networking: diff --git a/content/recommendations/learning_resources/index.en.md b/content/recommendations/learning_resources/index.en.md index 6dca5360eb845..5fda75e94d413 100644 --- a/content/recommendations/learning_resources/index.en.md +++ b/content/recommendations/learning_resources/index.en.md @@ -27,7 +27,7 @@ For those interested in Cybersecurity, there are several resources available to - [**INE**](https://ine.com/) INE offers both free and paid High-Quality Cyber Security labs and training. - [**Immersive Labs**](https://www.immersivelabs.com/) This platform offers free Cyber Security Labs, with paid offerings also available. Free for active students. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) This platform offers free Cyber Security Labs, with paid offerings also available. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/), with paid offerings also available. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/), with paid offerings also available. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) This platform offers guided CTF challenges, with a paid membership option. ## Networking: diff --git a/content/recommendations/learning_resources/index.es.md b/content/recommendations/learning_resources/index.es.md index 479841b810f8a..ff69ae0dcab84 100644 --- a/content/recommendations/learning_resources/index.es.md +++ b/content/recommendations/learning_resources/index.es.md @@ -27,7 +27,7 @@ Para aquellos interesados en la Ciberseguridad, hay varios recursos disponibles - [**INE**](https://ine.com/) El INE ofrece laboratorios y formación en ciberseguridad de alta calidad, tanto gratuitos como de pago. - [**Immersive Labs**](https://www.immersivelabs.com/) Esta plataforma ofrece laboratorios de ciberseguridad gratuitos, con ofertas de pago también disponibles. Gratuito para estudiantes activos. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Esta plataforma ofrece laboratorios de ciberseguridad gratuitos, con ofertas de pago también disponibles. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) con ofertas de pago también disponibles. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) con ofertas de pago también disponibles. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Esta plataforma ofrece retos CTF guiados, con opción de suscripción de pago. ## Redes: diff --git a/content/recommendations/learning_resources/index.fr.md b/content/recommendations/learning_resources/index.fr.md index c9be9aa1e091c..d2802b9a028d6 100644 --- a/content/recommendations/learning_resources/index.fr.md +++ b/content/recommendations/learning_resources/index.fr.md @@ -27,7 +27,7 @@ Pour ceux qui s'intéressent à la cybersécurité, plusieurs ressources sont di - [**INE**](https://ine.com/) INE propose des laboratoires et des formations de haute qualité en cybersécurité, gratuits ou payants. - [**Immersive Labs**](https://www.immersivelabs.com/) Cette plateforme propose des laboratoires de cybersécurité gratuits, ainsi que des offres payantes. Gratuit pour les étudiants actifs. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Cette plateforme propose des laboratoires de cybersécurité gratuits, ainsi que des offres payantes. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) avec des offres payantes également disponibles. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) avec des offres payantes également disponibles. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Cette plateforme propose des défis CTF guidés, avec une option d'adhésion payante. ## Mise en réseau : diff --git a/content/recommendations/learning_resources/index.it.md b/content/recommendations/learning_resources/index.it.md index b9e2e057101b5..e0ffa8350c18e 100644 --- a/content/recommendations/learning_resources/index.it.md +++ b/content/recommendations/learning_resources/index.it.md @@ -27,7 +27,7 @@ Per chi è interessato alla Cybersecurity, ci sono diverse risorse disponibili p - [**INE**](https://ine.com/) INE offre laboratori e formazione di alta qualità sulla sicurezza informatica, sia gratuiti che a pagamento. - [**Immersive Labs**](https://www.immersivelabs.com/) Questa piattaforma offre laboratori gratuiti di sicurezza informatica, con offerte a pagamento. Gratuiti per gli studenti attivi. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Questa piattaforma offre laboratori di sicurezza informatica gratuiti, con offerte a pagamento. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) Sono disponibili anche offerte a pagamento. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) Sono disponibili anche offerte a pagamento. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Questa piattaforma offre sfide CTF guidate, con un'opzione di iscrizione a pagamento. ## Networking: diff --git a/content/recommendations/learning_resources/index.ja.md b/content/recommendations/learning_resources/index.ja.md index 0f6fc50cfafea..045535e026d8a 100644 --- a/content/recommendations/learning_resources/index.ja.md +++ b/content/recommendations/learning_resources/index.ja.md @@ -27,7 +27,7 @@ IT、サイバーセキュリティ、ネットワーキング、オペレーテ - [**INE**](https://ine.com/)INEは、無料と有料の両方の高品質なサイバーセキュリティラボとトレーニングを提供しています。 - [**Immersive Labs**](https://www.immersivelabs.com/)サイバーセキュリティラボを無料で提供するプラットフォームで、有料のものも用意されています。現役の学生は無料で利用できます。 - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/)本プラットフォームでは、無料でサイバーセキュリティラボを提供しており、有料での提供も可能です。 -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/)を、有償で提供することも可能です。 +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/)を、有償で提供することも可能です。 - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56)ガイド付きのCTFチャレンジを提供するプラットフォームで、有料会員オプションがあります。 ## ネットワーキング diff --git a/content/recommendations/learning_resources/index.nl.md b/content/recommendations/learning_resources/index.nl.md index fd342aaea4100..175d00de296ed 100644 --- a/content/recommendations/learning_resources/index.nl.md +++ b/content/recommendations/learning_resources/index.nl.md @@ -27,7 +27,7 @@ Voor degenen die geïnteresseerd zijn in cyberbeveiliging zijn er verschillende - [**INE**](https://ine.com/) INE biedt zowel gratis als betaalde hoogwaardige cyberbeveiligingslabs en -trainingen. - [**Immersive Labs**](https://www.immersivelabs.com/) Dit platform biedt gratis Cyber Security Labs, maar er zijn ook betaalde aanbiedingen beschikbaar. Gratis voor actieve studenten. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Dit platform biedt gratis Cyber Security Labs, maar er zijn ook betaalde aanbiedingen. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) met ook betaalde aanbiedingen. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) met ook betaalde aanbiedingen. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Dit platform biedt begeleide CTF-uitdagingen, met een optie voor betaald lidmaatschap. ## Netwerken: diff --git a/content/recommendations/learning_resources/index.pl.md b/content/recommendations/learning_resources/index.pl.md index 144f1bef57e64..56a91768f4377 100644 --- a/content/recommendations/learning_resources/index.pl.md +++ b/content/recommendations/learning_resources/index.pl.md @@ -27,7 +27,7 @@ Dla osób zainteresowanych cyberbezpieczeństwem dostępnych jest kilka zasobów - [**INE**](https://ine.com/) INE oferuje zarówno bezpłatne, jak i płatne wysokiej jakości laboratoria i szkolenia z zakresu cyberbezpieczeństwa. - [**Immersive Labs**](https://www.immersivelabs.com/) Ta platforma oferuje bezpłatne laboratoria cyberbezpieczeństwa, a także płatne oferty. Bezpłatne dla aktywnych studentów. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Platforma ta oferuje bezpłatne laboratoria cyberbezpieczeństwa, a także płatne oferty. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) dostępne są również płatne oferty. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) dostępne są również płatne oferty. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Platforma ta oferuje wyzwania CTF z przewodnikiem, z opcją płatnego członkostwa. ## Networking: diff --git a/content/recommendations/learning_resources/index.ro.md b/content/recommendations/learning_resources/index.ro.md index 8a62582934684..315277951b808 100644 --- a/content/recommendations/learning_resources/index.ro.md +++ b/content/recommendations/learning_resources/index.ro.md @@ -27,7 +27,7 @@ Pentru cei interesați de securitatea cibernetică, există mai multe resurse di - [**INE**](https://ine.com/) INE oferă atât laboratoare de securitate cibernetică de înaltă calitate, cât și traininguri gratuite și plătite. - [**Immersive Labs**](https://www.immersivelabs.com/) Această platformă oferă gratuit laboratoare de securitate cibernetică, fiind disponibile și oferte cu plată. Gratuit pentru studenții activi. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Această platformă oferă gratuit laboratoare de securitate cibernetică, fiind disponibile și oferte cu plată. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) fiind disponibile și oferte cu plată. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) fiind disponibile și oferte cu plată. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Această platformă oferă provocări CTF ghidate, cu opțiunea de abonament plătit. ## Networking: diff --git a/content/recommendations/learning_resources/index.ru.md b/content/recommendations/learning_resources/index.ru.md index 21825d6f202d2..c75eea9ccbcc1 100644 --- a/content/recommendations/learning_resources/index.ru.md +++ b/content/recommendations/learning_resources/index.ru.md @@ -27,7 +27,7 @@ tags: ["Рекомендуемые учебные ресурсы", "Рекоме - [**INE**](https://ine.com/) INE предлагает как бесплатные, так и платные высококачественные лабораторные работы и тренинги по кибербезопасности. - [**Immersive Labs**](https://www.immersivelabs.com/) Эта платформа предлагает бесплатные лаборатории кибербезопасности, а также платные предложения. Бесплатно для активных студентов. - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/) Эта платформа предлагает бесплатные лаборатории кибербезопасности, а также платные предложения. -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/) также доступны платные предложения. +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/) также доступны платные предложения. - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56) Эта платформа предлагает управляемые CTF-задачи с возможностью платного участия. ## Networking: diff --git a/content/recommendations/learning_resources/index.zh.md b/content/recommendations/learning_resources/index.zh.md index 6eb7e817411a2..c82212e6fc715 100644 --- a/content/recommendations/learning_resources/index.zh.md +++ b/content/recommendations/learning_resources/index.zh.md @@ -27,7 +27,7 @@ tags: ["推荐学习资源", "SimeonOnSecurity 的建议", "信息技术学习", - [**INE**](https://ine.com/)INE 提供免费和付费的高质量网络安全实验室和培训。 - [**Immersive Labs**](https://www.immersivelabs.com/)该平台提供免费的网络安全实验室,也提供付费服务。对在校学生免费。 - [**Mosse Cyber Security Institute**](https://platform.mosse-institute.com/#/)该平台提供免费的网络安全实验室,也提供付费服务。 -- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.ch/tags/pentesterlab/)还提供付费服务。 +- [**PenTesterLab**](https://pentesterlab.com/) This platform offers hands-on [Pentesting Labs](https://simeononsecurity.com/tags/pentesterlab/)还提供付费服务。 - [**TryHackMe**](https://tryhackme.com/signup?referrer=5f651e437af6815dfbc2ab56)该平台提供有指导的 CTF 挑战,并提供付费会员选项。 ## 网络: diff --git a/content/recommendations/privacy/index.de.md b/content/recommendations/privacy/index.de.md index f1f82f1b0698a..bc3f8c608891f 100644 --- a/content/recommendations/privacy/index.de.md +++ b/content/recommendations/privacy/index.de.md @@ -33,9 +33,9 @@ Gute digitale Sicherheits- und Hygienepraktiken sind entscheidend für den Schut Wenn Sie den Verdacht haben, dass Ihre Privatsphäre verletzt wurde, ist es wichtig, den Vorfall zu melden. Sie können ein vermisstes, missbrauchtes oder sexuell ausgebeutetes Kind melden unter [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) für Cyberkriminalität, Hacks, digitalen Diebstahl und mehr. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Wenn Sie zusätzliche Hilfe zum Schutz Ihrer Privatsphäre benötigen, sollten Sie Folgendes in Betracht ziehen [privacy services](https://simeononsecurity.ch/recommendations/services/) um Ihre Einträge bei großen Datenmaklern zu löschen. Einige empfohlene Dienste sind: +Wenn Sie zusätzliche Hilfe zum Schutz Ihrer Privatsphäre benötigen, sollten Sie Folgendes in Betracht ziehen [privacy services](https://simeononsecurity.com/recommendations/services/) um Ihre Einträge bei großen Datenmaklern zu löschen. Einige empfohlene Dienste sind: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Dieser bevorzugte Dienst kann Ihnen dabei helfen, Ihre Einträge bei den großen Datenmaklern zu löschen. - [OneRep](https://onerep.com) Dieser alternative Dienst kann Ihnen dabei helfen, Ihre Einträge bei den großen Datenmaklern zu löschen. diff --git a/content/recommendations/privacy/index.en.md b/content/recommendations/privacy/index.en.md index 43603c4e58700..00ea1a6561181 100644 --- a/content/recommendations/privacy/index.en.md +++ b/content/recommendations/privacy/index.en.md @@ -33,12 +33,12 @@ Good digital security and hygiene practices are critical for protecting your pri If you suspect that your privacy has been violated, it is crucial to report the incident. You can report a missing, abused, or sexually exploited child at [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) for cyber crimes, hacks, digital theft, and more. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -If you need additional help protecting your privacy, consider using [privacy services](https://simeononsecurity.ch/recommendations/services/) to delete your records from major data brokers. Some recommended services include: +If you need additional help protecting your privacy, consider using [privacy services](https://simeononsecurity.com/recommendations/services/) to delete your records from major data brokers. Some recommended services include: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4): This preferred service can help you delete your records from major data brokers. -- [OneRep](https://onerep.com): [Onerep](https://simeononsecurity.ch/articles/onerep-data-removal-privacy-service/) is an alternate service can help you delete your records from major data brokers. +- [OneRep](https://onerep.com): [Onerep](https://simeononsecurity.com/articles/onerep-data-removal-privacy-service/) is an alternate service can help you delete your records from major data brokers. - [Privacy Duck](https://www.privacyduck.com/): This alternate service can also help you delete your records from major data brokers. You can also mask your information with services like [Abine Blur](https://dnt.abine.com/#/ref_register/pC8ZbvQtt) and [Privacy.com](https://privacy.com/join/SU86Y). Abine Blur provides a password manager, identity masking, and one-time-use debit cards. Privacy.com, on the other hand, generates one-time-use debit cards, which can help prevent fraud. diff --git a/content/recommendations/privacy/index.es.md b/content/recommendations/privacy/index.es.md index 4a778b2712ce8..c88438c909880 100644 --- a/content/recommendations/privacy/index.es.md +++ b/content/recommendations/privacy/index.es.md @@ -33,9 +33,9 @@ Unas buenas prácticas de seguridad e higiene digital son fundamentales para pro Si sospecha que se ha violado su intimidad, es crucial que denuncie el incidente. Puede denunciar la desaparición, maltrato o explotación sexual de un menor en [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) por ciberdelitos, hackeos, robos digitales, etc. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Si necesita más ayuda para proteger su privacidad, considere la posibilidad de utilizar [privacy services](https://simeononsecurity.ch/recommendations/services/) para eliminar sus registros de los principales corredores de datos. Algunos servicios recomendados son: +Si necesita más ayuda para proteger su privacidad, considere la posibilidad de utilizar [privacy services](https://simeononsecurity.com/recommendations/services/) para eliminar sus registros de los principales corredores de datos. Algunos servicios recomendados son: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Este servicio preferente puede ayudarle a eliminar sus registros de los principales corredores de datos. - [OneRep](https://onerep.com) Este servicio alternativo puede ayudarte a eliminar tus registros de los principales corredores de datos. diff --git a/content/recommendations/privacy/index.fr.md b/content/recommendations/privacy/index.fr.md index 55a1fc1eb5f1e..b1dfed1cf6e11 100644 --- a/content/recommendations/privacy/index.fr.md +++ b/content/recommendations/privacy/index.fr.md @@ -33,9 +33,9 @@ De bonnes pratiques en matière de sécurité et d'hygiène numériques sont ess Si vous pensez que votre vie privée a été violée, il est essentiel de signaler l'incident. Vous pouvez signaler la disparition, la maltraitance ou l'exploitation sexuelle d'un enfant à l'adresse suivante [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) pour les cybercrimes, les piratages, les vols numériques, etc. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Si vous avez besoin d'aide supplémentaire pour protéger votre vie privée, envisagez d'utiliser [privacy services](https://simeononsecurity.ch/recommendations/services/) pour supprimer vos données des principaux courtiers en données. Voici quelques services recommandés : +Si vous avez besoin d'aide supplémentaire pour protéger votre vie privée, envisagez d'utiliser [privacy services](https://simeononsecurity.com/recommendations/services/) pour supprimer vos données des principaux courtiers en données. Voici quelques services recommandés : - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Ce service privilégié peut vous aider à supprimer vos enregistrements auprès des principaux courtiers en données. - [OneRep](https://onerep.com) Ce service alternatif peut vous aider à supprimer vos dossiers auprès des principaux courtiers en données. diff --git a/content/recommendations/privacy/index.it.md b/content/recommendations/privacy/index.it.md index b1d09d30afbb3..8b11ab234663f 100644 --- a/content/recommendations/privacy/index.it.md +++ b/content/recommendations/privacy/index.it.md @@ -33,9 +33,9 @@ Le buone pratiche di sicurezza e igiene digitale sono fondamentali per protegger Se si sospetta che la propria privacy sia stata violata, è fondamentale segnalare l'accaduto. È possibile denunciare la scomparsa, l'abuso o lo sfruttamento sessuale di un bambino all'indirizzo [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) per crimini informatici, hacking, furti digitali e altro ancora. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Se avete bisogno di ulteriore aiuto per proteggere la vostra privacy, considerate l'utilizzo di [privacy services](https://simeononsecurity.ch/recommendations/services/) per cancellare i vostri dati dai principali broker di dati. Alcuni servizi consigliati sono: +Se avete bisogno di ulteriore aiuto per proteggere la vostra privacy, considerate l'utilizzo di [privacy services](https://simeononsecurity.com/recommendations/services/) per cancellare i vostri dati dai principali broker di dati. Alcuni servizi consigliati sono: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Questo servizio preferenziale può aiutarvi a cancellare i vostri dati dai principali broker di dati. - [OneRep](https://onerep.com) Questo servizio alternativo può aiutarvi a cancellare i vostri dati dai principali broker di dati. diff --git a/content/recommendations/privacy/index.ja.md b/content/recommendations/privacy/index.ja.md index 12da7d3e0eea5..b5da91e625e01 100644 --- a/content/recommendations/privacy/index.ja.md +++ b/content/recommendations/privacy/index.ja.md @@ -33,9 +33,9 @@ tags: ["推奨プライバシーリソース", "プライバシー権", "イン プライバシーが侵害されていると思われる場合は、通報することが肝心です。行方不明、虐待、性的搾取を受けた子どもの通報は、次のサイトで行えます。 [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?)サイバー犯罪、ハッキング、デジタル窃盗などのために -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -プライバシーを守るために、さらにサポートが必要な場合は、以下の利用を検討してください。 [privacy services](https://simeononsecurity.ch/recommendations/services/)を利用して、大手データブローカーから自分の記録を削除することができます。おすすめのサービスとしては、以下のようなものがあります: +プライバシーを守るために、さらにサポートが必要な場合は、以下の利用を検討してください。 [privacy services](https://simeononsecurity.com/recommendations/services/)を利用して、大手データブローカーから自分の記録を削除することができます。おすすめのサービスとしては、以下のようなものがあります: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4)この優先サービスは、主要なデータブローカーからあなたの記録を削除するのに役立ちます。 - [OneRep](https://onerep.com)この代替サービスでは、主要なデータブローカーから記録を削除することができます。 diff --git a/content/recommendations/privacy/index.nl.md b/content/recommendations/privacy/index.nl.md index 993bfcbe645f7..72364cfb79802 100644 --- a/content/recommendations/privacy/index.nl.md +++ b/content/recommendations/privacy/index.nl.md @@ -33,9 +33,9 @@ Goede digitale beveiliging en hygiëne zijn essentieel voor het beschermen van u Als u vermoedt dat uw privacy is geschonden, is het van cruciaal belang om het incident te melden. U kunt een vermist, misbruikt of seksueel uitgebuit kind melden bij [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) voor cybermisdaden, hacks, digitale diefstal en meer. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Als je extra hulp nodig hebt bij het beschermen van je privacy, overweeg dan het gebruik van [privacy services](https://simeononsecurity.ch/recommendations/services/) om je gegevens van grote gegevensmakelaars te verwijderen. Enkele aanbevolen diensten zijn: +Als je extra hulp nodig hebt bij het beschermen van je privacy, overweeg dan het gebruik van [privacy services](https://simeononsecurity.com/recommendations/services/) om je gegevens van grote gegevensmakelaars te verwijderen. Enkele aanbevolen diensten zijn: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Deze voorkeurservice kan je helpen om je gegevens te verwijderen van grote gegevensmakelaars. - [OneRep](https://onerep.com) Deze alternatieve service kan je helpen om je gegevens te verwijderen van grote gegevensmakelaars. diff --git a/content/recommendations/privacy/index.pl.md b/content/recommendations/privacy/index.pl.md index dea4e0b5e655d..40c82abf3bc77 100644 --- a/content/recommendations/privacy/index.pl.md +++ b/content/recommendations/privacy/index.pl.md @@ -33,9 +33,9 @@ Dobre praktyki w zakresie bezpieczeństwa cyfrowego i higieny mają kluczowe zna Jeśli podejrzewasz, że Twoja prywatność została naruszona, koniecznie zgłoś ten incydent. Zaginięcie, nadużycie lub wykorzystywanie seksualne dziecka można zgłosić pod adresem [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) za cyberprzestępstwa, włamania, kradzieże cyfrowe i nie tylko. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Jeśli potrzebujesz dodatkowej pomocy w ochronie swojej prywatności, rozważ skorzystanie z usługi [privacy services](https://simeononsecurity.ch/recommendations/services/) aby usunąć swoje rekordy z głównych brokerów danych. Niektóre zalecane usługi obejmują: +Jeśli potrzebujesz dodatkowej pomocy w ochronie swojej prywatności, rozważ skorzystanie z usługi [privacy services](https://simeononsecurity.com/recommendations/services/) aby usunąć swoje rekordy z głównych brokerów danych. Niektóre zalecane usługi obejmują: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Ta preferowana usługa może pomóc w usunięciu rekordów z głównych brokerów danych. - [OneRep](https://onerep.com) Ta alternatywna usługa może pomóc w usunięciu rekordów z głównych brokerów danych. diff --git a/content/recommendations/privacy/index.ro.md b/content/recommendations/privacy/index.ro.md index 734fc227a05c2..04414c76c9d51 100644 --- a/content/recommendations/privacy/index.ro.md +++ b/content/recommendations/privacy/index.ro.md @@ -33,9 +33,9 @@ Bunele practici de securitate digitală și de igienă sunt esențiale pentru a Dacă bănuiți că viața dumneavoastră privată a fost încălcată, este esențial să raportați incidentul. Puteți raporta un copil dispărut, abuzat sau exploatat sexual la adresa [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) pentru infracțiuni cibernetice, piraterie informatică, furturi digitale și multe altele. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Dacă aveți nevoie de ajutor suplimentar pentru a vă proteja confidențialitatea, luați în considerare utilizarea [privacy services](https://simeononsecurity.ch/recommendations/services/) pentru a vă șterge înregistrările de la marii brokeri de date. Printre serviciile recomandate se numără: +Dacă aveți nevoie de ajutor suplimentar pentru a vă proteja confidențialitatea, luați în considerare utilizarea [privacy services](https://simeononsecurity.com/recommendations/services/) pentru a vă șterge înregistrările de la marii brokeri de date. Printre serviciile recomandate se numără: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Acest serviciu preferat vă poate ajuta să vă ștergeți înregistrările de la principalii brokeri de date. - [OneRep](https://onerep.com) Acest serviciu alternativ vă poate ajuta să vă ștergeți înregistrările de la principalii brokeri de date. diff --git a/content/recommendations/privacy/index.ru.md b/content/recommendations/privacy/index.ru.md index 866ad0f2c8530..15e9258a59122 100644 --- a/content/recommendations/privacy/index.ru.md +++ b/content/recommendations/privacy/index.ru.md @@ -33,9 +33,9 @@ tags: ["рекомендуемые ресурсы по защите персон Если вы подозреваете, что ваша частная жизнь была нарушена, необходимо сообщить о случившемся. Сообщить о пропаже, жестоком обращении или сексуальной эксплуатации ребенка можно по адресу [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?) для борьбы с киберпреступлениями, взломами, кражами цифровых данных и т.д. -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -Если вам нужна дополнительная помощь в защите конфиденциальности, воспользуйтесь [privacy services](https://simeononsecurity.ch/recommendations/services/) для удаления ваших записей у крупных брокеров данных. Среди рекомендуемых сервисов можно назвать следующие: +Если вам нужна дополнительная помощь в защите конфиденциальности, воспользуйтесь [privacy services](https://simeononsecurity.com/recommendations/services/) для удаления ваших записей у крупных брокеров данных. Среди рекомендуемых сервисов можно назвать следующие: - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4) Эта предпочтительная услуга поможет вам удалить свои записи у крупнейших брокеров данных. - [OneRep](https://onerep.com) Этот альтернативный сервис поможет вам удалить свои записи у крупных брокеров данных. diff --git a/content/recommendations/privacy/index.zh.md b/content/recommendations/privacy/index.zh.md index 382b8f5f3d52f..818926f8575e9 100644 --- a/content/recommendations/privacy/index.zh.md +++ b/content/recommendations/privacy/index.zh.md @@ -33,9 +33,9 @@ tags: ["推荐的隐私资源", "隐私权", "身份盗窃保护", "数字安全 如果您怀疑自己的隐私受到了侵犯,报告该事件至关重要。您可以通过以下网址报告儿童失踪、受虐待或性剥削事件 [Report a Missing, Abused or Sexually Exploited Child](http://www.missingkids.com/Report). For cyber-related complaints such as identity theft, spam, online scams, and more, file a complaint with the Federal Trade Commission (FTC) at [File a cyber-related complaint with the Federal Trade Commission (FTC)](https://www.ftccomplaintassistant.gov/#&panel1-1). You can also file a complaint with the Internet Crime Complaint Center (IC3) at [File a complaint with the Internet Crime Complaint Center (IC3)](https://complaint.ic3.gov/default.aspx?)网络犯罪、黑客攻击、数字盗窃等。 -### [Services](https://simeononsecurity.ch/recommendations/services/) +### [Services](https://simeononsecurity.com/recommendations/services/) -如果您需要额外的隐私保护帮助,请考虑使用 [privacy services](https://simeononsecurity.ch/recommendations/services/)从主要数据经纪商那里删除您的记录。推荐的一些服务包括 +如果您需要额外的隐私保护帮助,请考虑使用 [privacy services](https://simeononsecurity.com/recommendations/services/)从主要数据经纪商那里删除您的记录。推荐的一些服务包括 - [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4)这项首选服务可帮助您删除主要数据经纪商的记录。 - [OneRep](https://onerep.com)这项备用服务可帮助您删除主要数据经纪商的记录。 diff --git a/content/recommendations/services/index.en.md b/content/recommendations/services/index.en.md index ca47aa78ba569..815f4270e7fe5 100644 --- a/content/recommendations/services/index.en.md +++ b/content/recommendations/services/index.en.md @@ -14,7 +14,7 @@ The first category of privacy services we'll cover is services that help you rem The **preferred** service in this category is [Abine DeleteMe](https://joindeleteme.com/refer?coupon=RFR-40867-7DWHR4). This service has been in business since 2010 and is trusted by over 20,000 customers. DeleteMe offers several subscription options, starting at $129 per year, and will remove your personal information from up to 25 data brokers. -Another **alternate** service to consider in this category is [OneRep](https://onerep.com). [OneRep](https://simeononsecurity.ch/articles/onerep-data-removal-privacy-service/) offers a similar service to DeleteMe, removing your personal information from data brokers. OneRep's pricing is more affordable than DeleteMe, starting at $4.95 per month, but they do not remove information from as many data brokers as DeleteMe. +Another **alternate** service to consider in this category is [OneRep](https://onerep.com). [OneRep](https://simeononsecurity.com/articles/onerep-data-removal-privacy-service/) offers a similar service to DeleteMe, removing your personal information from data brokers. OneRep's pricing is more affordable than DeleteMe, starting at $4.95 per month, but they do not remove information from as many data brokers as DeleteMe. A new addition to this category is [Optery](https://app.optery.com/). Optery is a comprehensive privacy service that helps you manage and protect your personal information online. With Optery, you can easily remove your information from data brokers, control your online presence, and safeguard your privacy. Although specific pricing details may vary, Optery offers competitive subscription options tailored to meet your privacy needs. We really like the screenshots and direct links to each data exposure. This information can make tracking your exposures significantly easier. diff --git a/content/recommendhome/pageshema.html b/content/recommendhome/pageshema.html index d3e8dbb40de84..6b68978b2a45d 100644 --- a/content/recommendhome/pageshema.html +++ b/content/recommendhome/pageshema.html @@ -6,99 +6,99 @@ "description": "Explore SimeonOnSecurity's expert recommendations for trusted and highly rated security and privacy-related products and resources.", "genre": ["Cybersecurity", "Privacy Protection", "Product Recommendations", "Resource Recommendations", "Security Tools", "Privacy Tools", "Data Protection", "Internet Privacy"], "keywords": ["security recommendations", "privacy products", "cybersecurity tools", "data protection", "internet privacy", "anti-virus", "books", "browser plugins", "certifications", "email providers", "every day carry", "hackers toolkit", "headphones", "microphones", "speakers", "learning resources", "messenger clients", "organizations to support", "privacy resources", "SIP DID VOIP providers", "security creators", "service providers", "VPN providers", "webcams"], - "image": "https://simeononsecurity.ch/img/cover/A_cartoon-style_image_of_a_shield_with_a_lock_on_it.png", + "image": "https://simeononsecurity.com/img/cover/A_cartoon-style_image_of_a_shield_with_a_lock_on_it.png", "mainEntity": { "@type": "ItemList", "itemListElement": [ { "@type": "ListItem", "position": 1, - "url": "https://simeononsecurity.ch/recommendations/anti-virus" + "url": "https://simeononsecurity.com/recommendations/anti-virus" }, { "@type": "ListItem", "position": 2, - "url": "https://simeononsecurity.ch/recommendations/books" + "url": "https://simeononsecurity.com/recommendations/books" }, { "@type": "ListItem", "position": 3, - "url": "https://simeononsecurity.ch/recommendations/browser_plugins" + "url": "https://simeononsecurity.com/recommendations/browser_plugins" }, { "@type": "ListItem", "position": 4, - "url": "https://simeononsecurity.ch/recommendations/cell-phone-service-providers" + "url": "https://simeononsecurity.com/recommendations/cell-phone-service-providers" }, { "@type": "ListItem", "position": 5, - "url": "https://simeononsecurity.ch/recommendations/certifications" + "url": "https://simeononsecurity.com/recommendations/certifications" }, { "@type": "ListItem", "position": 6, - "url": "https://simeononsecurity.ch/recommendations/email" + "url": "https://simeononsecurity.com/recommendations/email" }, { "@type": "ListItem", "position": 7, - "url": "https://simeononsecurity.ch/recommendations/edc" + "url": "https://simeononsecurity.com/recommendations/edc" }, { "@type": "ListItem", "position": 8, - "url": "https://simeononsecurity.ch/recommendations/hacker_hardware" + "url": "https://simeononsecurity.com/recommendations/hacker_hardware" }, { "@type": "ListItem", "position": 9, - "url": "https://simeononsecurity.ch/recommendations/audio" + "url": "https://simeononsecurity.com/recommendations/audio" }, { "@type": "ListItem", "position": 10, - "url": "https://simeononsecurity.ch/recommendations/learning_resources" + "url": "https://simeononsecurity.com/recommendations/learning_resources" }, { "@type": "ListItem", "position": 11, - "url": "https://simeononsecurity.ch/recommendations/messengers" + "url": "https://simeononsecurity.com/recommendations/messengers" }, { "@type": "ListItem", "position": 12, - "url": "https://simeononsecurity.ch/recommendations/organizations" + "url": "https://simeononsecurity.com/recommendations/organizations" }, { "@type": "ListItem", "position": 13, - "url": "https://simeononsecurity.ch/recommendations/privacy" + "url": "https://simeononsecurity.com/recommendations/privacy" }, { "@type": "ListItem", "position": 14, - "url": "https://simeononsecurity.ch/recommendations/voip" + "url": "https://simeononsecurity.com/recommendations/voip" }, { "@type": "ListItem", "position": 15, - "url": "https://simeononsecurity.ch/recommendations/creators" + "url": "https://simeononsecurity.com/recommendations/creators" }, { "@type": "ListItem", "position": 16, - "url": "https://simeononsecurity.ch/recommendations/services" + "url": "https://simeononsecurity.com/recommendations/services" }, { "@type": "ListItem", "position": 17, - "url": "https://simeononsecurity.ch/recommendations/vpns" + "url": "https://simeononsecurity.com/recommendations/vpns" }, { "@type": "ListItem", "position": 18, - "url": "https://simeononsecurity.ch/recommendations/webcams" + "url": "https://simeononsecurity.com/recommendations/webcams" } ] } diff --git a/content/search/_index.de.md b/content/search/_index.de.md index 4672a26c71569..f1bd30b59bcaa 100644 --- a/content/search/_index.de.md +++ b/content/search/_index.de.md @@ -1,5 +1,5 @@ --- -title: "Suche auf simeononsecurity.ch" +title: "Suche auf simeononsecurity.com" description: "Durchsuche die SimeonOnSecurity-Website nach Experteneinblicken in Cybersicherheit, Automatisierung und modernster Technologie. Bleibe informiert und sicher." tags: ["Einblicke in Cybersicherheit", "Automatisierungsexpertise", "Technologietrends", "Digitale Sicherheit", "Cyberabwehr", "Netzwerkschutz", "Informationssicherheit", "Technologieeinblicke", "Cyberbedrohungen", "Technologieressourcen", "Sicherheitstipps", "Branchennews", "Technologieaktualisierungen", "Cybersicherheitsartikel", "Automatisierungstechniken", "Digitale Privatsphäre", "Technische Expertise", "IT-Wissen", "Netzwerksicherheit", "Cybersicherheitsressourcen"] sitemap: diff --git a/content/search/_index.en.md b/content/search/_index.en.md index 92a6ad23587cb..91ccf2745eab2 100644 --- a/content/search/_index.en.md +++ b/content/search/_index.en.md @@ -1,5 +1,5 @@ --- -title: "Search simeononsecurity.ch" +title: "Search simeononsecurity.com" description : "Search the SimeonOnSecurity website for expert insights on cybersecurity, automation, and cutting-edge technology. Stay informed and secure." tags: ["cybersecurity insights", "automation expertise", "technology trends", "digital security", "cyber defense", "network protection", "information security", "technology insights", "cyber threats", "technology resources", "security tips", "industry news", "technology updates", "cybersecurity articles", "automation techniques", "digital privacy", "technical expertise", "IT knowledge", "network security", "cybersecurity resources"] sitemap: diff --git a/content/search/_index.es.md b/content/search/_index.es.md index 30970cd1c2022..d20609803372d 100644 --- a/content/search/_index.es.md +++ b/content/search/_index.es.md @@ -1,5 +1,5 @@ --- -title: "Buscar en simeononsecurity.ch" +title: "Buscar en simeononsecurity.com" description: "Busca en el sitio web de SimeonOnSecurity información experta sobre ciberseguridad, automatización y tecnología de vanguardia. Mantente informado y seguro." tags: ["ideas sobre ciberseguridad", "experiencia en automatización", "tendencias tecnológicas", "seguridad digital", "defensa cibernética", "protección de redes", "seguridad de la información", "conocimiento tecnológico", "amenazas cibernéticas", "recursos tecnológicos", "consejos de seguridad", "noticias de la industria", "actualizaciones tecnológicas", "artículos de ciberseguridad", "técnicas de automatización", "privacidad digital", "experiencia técnica", "conocimiento de IT", "seguridad de redes", "recursos de ciberseguridad"] sitemap: diff --git a/content/search/_index.fr.md b/content/search/_index.fr.md index fe2343e3eb578..fcd2212790503 100644 --- a/content/search/_index.fr.md +++ b/content/search/_index.fr.md @@ -1,5 +1,5 @@ --- -title: "Recherche sur simeononsecurity.ch" +title: "Recherche sur simeononsecurity.com" description: "Recherchez sur le site SimeonOnSecurity des informations d'experts sur la cybersécurité, l'automatisation et les technologies de pointe. Restez informé et sécurisé." tags: ["informations sur la cybersécurité", "expertise en automatisation", "tendances technologiques", "sécurité numérique", "défense contre les cyberattaques", "protection des réseaux", "sécurité de l'information", "connaissances technologiques", "menaces cybernétiques", "ressources technologiques", "conseils de sécurité", "actualités sectorielles", "mises à jour technologiques", "articles sur la cybersécurité", "techniques d'automatisation", "vie privée numérique", "expertise technique", "connaissances en IT", "sécurité des réseaux", "ressources en cybersécurité"] sitemap: diff --git a/content/search/_index.it.md b/content/search/_index.it.md index 12f2c94f1b170..66aa4e74f9424 100644 --- a/content/search/_index.it.md +++ b/content/search/_index.it.md @@ -1,5 +1,5 @@ --- -title: "Cerca su simeononsecurity.ch" +title: "Cerca su simeononsecurity.com" description: "Cerca nel sito web di SimeonOnSecurity per ottenere approfondimenti di esperti sulla sicurezza informatica, l'automazione e le tecnologie all'avanguardia. Rimani informato e protetto." tags: ["approfondimenti sulla sicurezza informatica", "competenze in automazione", "tendenze tecnologiche", "sicurezza digitale", "difesa cibernetica", "protezione delle reti", "sicurezza delle informazioni", "approfondimenti tecnologici", "minacce cibernetiche", "risorse tecnologiche", "consigli sulla sicurezza", "notizie del settore", "aggiornamenti tecnologici", "articoli sulla sicurezza informatica", "tecniche di automazione", "privacy digitale", "competenze tecniche", "conoscenze IT", "sicurezza delle reti", "risorse sulla sicurezza informatica"] sitemap: diff --git a/content/search/_index.ja.md b/content/search/_index.ja.md index 8bbec9974c788..6f6cc9703a279 100644 --- a/content/search/_index.ja.md +++ b/content/search/_index.ja.md @@ -1,5 +1,5 @@ --- -title: "simeononsecurity.chで検索" +title: "simeononsecurity.comで検索" description: "SimeonOnSecurityのウェブサイトで、サイバーセキュリティ、自動化、最先端技術に関する専門家の洞察を検索してください。情報を入手し、安全を確保しましょう。" tags: ["サイバーセキュリティの洞察", "自動化の専門知識", "技術トレンド", "デジタルセキュリティ", "サイバーディフェンス", "ネットワーク保護", "情報セキュリティ", "技術の洞察", "サイバー脅威", "技術リソース", "セキュリティのヒント", "業界ニュース", "技術のアップデート", "サイバーセキュリティの記事", "自動化の技術", "デジタルプライバシー", "技術的な専門知識", "ITの知識", "ネットワークセキュリティ", "サイバーセキュリティのリソース"] sitemap: diff --git a/content/search/_index.nl.md b/content/search/_index.nl.md index 99d39e5820884..29f731e2af5bc 100644 --- a/content/search/_index.nl.md +++ b/content/search/_index.nl.md @@ -1,5 +1,5 @@ --- -title: "Zoeken op simeononsecurity.ch" +title: "Zoeken op simeononsecurity.com" description: "Doorzoek de SimeonOnSecurity-website naar deskundige inzichten op het gebied van cybersecurity, automatisering en geavanceerde technologie. Blijf geïnformeerd en beveiligd." tags: ["inzichten in cybersecurity", "automatiseringsdeskundigheid", "technologietrends", "digitale beveiliging", "cyberverdediging", "netwerkbescherming", "informatiebeveiliging", "technologie-inzichten", "cyberdreigingen", "technologische hulpbronnen", "beveiligingstips", "branchenieuws", "technologie-updates", "cybersecurity-artikelen", "automatiseringstechnieken", "digitale privacy", "technische expertise", "IT-kennis", "netwerkbeveiliging", "cybersecurity-hulpmiddelen"] sitemap: diff --git a/content/search/_index.pl.md b/content/search/_index.pl.md index dada68345b0c6..6ca16eb106f78 100644 --- a/content/search/_index.pl.md +++ b/content/search/_index.pl.md @@ -1,5 +1,5 @@ --- -title: "Szukaj na stronie simeononsecurity.ch" +title: "Szukaj na stronie simeononsecurity.com" description: "Przeszukaj stronę SimeonOnSecurity w poszukiwaniu ekspertów w dziedzinie cyberbezpieczeństwa, automatyzacji i nowoczesnej technologii. Bądź na bieżąco i bezpieczny." tags: ["wgląd w cyberbezpieczeństwo", "ekspertyza w dziedzinie automatyzacji", "trendy technologiczne", "bezpieczeństwo cyfrowe", "obrona przed cyberatakami", "ochrona sieci", "bezpieczeństwo informacji", "wgląd w technologię", "zagrożenia cybernetyczne", "zasoby technologiczne", "porady dotyczące bezpieczeństwa", "wiadomości branżowe", "aktualizacje technologiczne", "artykuły o cyberbezpieczeństwie", "techniki automatyzacji", "prywatność cyfrowa", "ekspertyza techniczna", "wiedza IT", "bezpieczeństwo sieci", "zasoby w dziedzinie cyberbezpieczeństwa"] sitemap: diff --git a/content/termsandconditions/index.de.md b/content/termsandconditions/index.de.md index 62a4c10494785..c857ccb8799e6 100644 --- a/content/termsandconditions/index.de.md +++ b/content/termsandconditions/index.de.md @@ -5,7 +5,7 @@ date: 2020-08-08 Willkommen bei SimeonOnSecurity! -Diese Bedingungen umreißen die Regeln und Vorschriften für die Nutzung der Website von SimeonOnSecurity, die sich unter https://simeononsecurity.ch befindet. +Diese Bedingungen umreißen die Regeln und Vorschriften für die Nutzung der Website von SimeonOnSecurity, die sich unter https://simeononsecurity.com befindet. Wenn Sie auf diese Website zugreifen, gehen wir davon aus, dass Sie diese Bestimmungen und Bedingungen akzeptieren. Setzen Sie die Nutzung von SimeonOnSecurity nicht fort, wenn Sie nicht mit allen auf dieser Seite genannten Bedingungen einverstanden sind. diff --git a/content/termsandconditions/index.en.md b/content/termsandconditions/index.en.md index 413941bd01d94..6ffb73c015db9 100644 --- a/content/termsandconditions/index.en.md +++ b/content/termsandconditions/index.en.md @@ -9,7 +9,7 @@ tags: ["Terms and Conditions", "website rules", "security information", "securit Welcome to SimeonOnSecurity! -These terms and conditions outline the rules and regulations for the use of SimeonOnSecurity's Website, located at https://simeononsecurity.ch. +These terms and conditions outline the rules and regulations for the use of SimeonOnSecurity's Website, located at https://simeononsecurity.com. By accessing this website we assume you accept these terms and conditions. Do not continue to use SimeonOnSecurity if you do not agree to take all of the terms and conditions stated on this page. diff --git a/content/termsandconditions/index.es.md b/content/termsandconditions/index.es.md index 75277ebfda732..adf2b63a194d6 100644 --- a/content/termsandconditions/index.es.md +++ b/content/termsandconditions/index.es.md @@ -5,7 +5,7 @@ date: 2020-08-08 ¡Bienvenido a SimeonOnSecurity! -Estos términos y condiciones describen las normas y reglamentos de uso del sitio web de SimeonOnSecurity, ubicado en https://simeononsecurity.ch. +Estos términos y condiciones describen las normas y reglamentos de uso del sitio web de SimeonOnSecurity, ubicado en https://simeononsecurity.com. Al acceder a este sitio web asumimos que acepta estos términos y condiciones. No continúe utilizando SimeonOnSecurity si no está de acuerdo en aceptar todos los términos y condiciones establecidos en esta página. diff --git a/content/termsandconditions/index.fr.md b/content/termsandconditions/index.fr.md index 2405b12745b0a..51671634509cf 100644 --- a/content/termsandconditions/index.fr.md +++ b/content/termsandconditions/index.fr.md @@ -5,7 +5,7 @@ date: 2020-08-08 Bienvenue à SimeonOnSecurity ! -Ces termes et conditions définissent les règles et règlements pour l'utilisation du site Internet de SimeonOnSecurity, situé à l'adresse https://simeononsecurity.ch. +Ces termes et conditions définissent les règles et règlements pour l'utilisation du site Internet de SimeonOnSecurity, situé à l'adresse https://simeononsecurity.com. En accédant à ce site web, nous supposons que vous acceptez ces conditions générales. Ne continuez pas à utiliser SimeonOnSecurity si vous n'acceptez pas toutes les conditions générales énoncées sur cette page. diff --git a/content/termsandconditions/index.it.md b/content/termsandconditions/index.it.md index 3dba3ccb4dd30..54df5bc095396 100644 --- a/content/termsandconditions/index.it.md +++ b/content/termsandconditions/index.it.md @@ -5,7 +5,7 @@ date: 2020-08-08 Benvenuti a SimeonOnSecurity! -Questi termini e condizioni definiscono le norme e i regolamenti per l'utilizzo del sito web di SimeonOnSecurity, situato all'indirizzo https://simeononsecurity.ch. +Questi termini e condizioni definiscono le norme e i regolamenti per l'utilizzo del sito web di SimeonOnSecurity, situato all'indirizzo https://simeononsecurity.com. Accedendo a questo sito web si presume che l'utente accetti questi termini e condizioni. Non continuare a utilizzare SimeonOnSecurity se non si accettano tutti i termini e le condizioni riportate in questa pagina. diff --git a/content/termsandconditions/index.ja.md b/content/termsandconditions/index.ja.md index ecb83645b26a5..e6b70390edad2 100644 --- a/content/termsandconditions/index.ja.md +++ b/content/termsandconditions/index.ja.md @@ -5,7 +5,7 @@ date: 2020-08-08 SimeonOnSecurityへようこそ! -本規約は、SimeonOnSecurityのウェブサイト(https://simeononsecurity.ch)を利用する際のルールと規則をまとめたものです。 +本規約は、SimeonOnSecurityのウェブサイト(https://simeononsecurity.com)を利用する際のルールと規則をまとめたものです。 このウェブサイトにアクセスすることで、私たちはあなたがこれらの条件に同意したものとみなします。このページに記載されているすべての条件を取ることに同意しない場合は、SimeonOnSecurityを使用し続けないでください。 diff --git a/content/termsandconditions/index.nl.md b/content/termsandconditions/index.nl.md index 23fef7d7d7ba0..1bfabc44bd8c1 100644 --- a/content/termsandconditions/index.nl.md +++ b/content/termsandconditions/index.nl.md @@ -5,7 +5,7 @@ date: 2020-08-08 Welkom bij SimeonOnSecurity! -Deze algemene voorwaarden bevatten de regels en voorschriften voor het gebruik van de website van SimeonOnSecurity, te vinden op https://simeononsecurity.ch. +Deze algemene voorwaarden bevatten de regels en voorschriften voor het gebruik van de website van SimeonOnSecurity, te vinden op https://simeononsecurity.com. Door deze website te bezoeken gaan wij ervan uit dat u deze voorwaarden accepteert. Ga niet verder met het gebruik van SimeonOnSecurity als u niet akkoord gaat met alle voorwaarden en condities die op deze pagina vermeld staan. diff --git a/content/termsandconditions/index.pl.md b/content/termsandconditions/index.pl.md index cef3b5d52688b..8540618408e55 100644 --- a/content/termsandconditions/index.pl.md +++ b/content/termsandconditions/index.pl.md @@ -5,7 +5,7 @@ date: 2020-08-08 Witamy w SimeonOnSecurity! -Niniejsze warunki określają zasady i przepisy dotyczące korzystania z witryny internetowej SimeonOnSecurity, znajdującej się pod adresem https://simeononsecurity.ch. +Niniejsze warunki określają zasady i przepisy dotyczące korzystania z witryny internetowej SimeonOnSecurity, znajdującej się pod adresem https://simeononsecurity.com. Uzyskując dostęp do tej witryny, zakładamy, że akceptujesz te warunki. Nie kontynuuj korzystania z SimeonOnSecurity, jeśli nie zgadzasz się na wszystkie warunki określone na tej stronie. diff --git a/content/til/2020-12-27/index.ar.md b/content/til/2020-12-27/index.ar.md index 056939d429b8b..c315c49bd3fd2 100644 --- a/content/til/2020-12-27/index.ar.md +++ b/content/til/2020-12-27/index.ar.md @@ -57,4 +57,4 @@ SimeonOnSecurity هو شخص لديه اهتمام كبير بالأمن وال ## nikitavoloboev / احترام الخصوصية: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- قائمة كبيرة من الخدمات والبرامج التي تحترم الخصوصية. انا بالفعل[recommend](https://simeononsecurity.ch/recommendations) بعض العناصر المرتبطة. أخطط لمواصلة القراءة في العناصر الموجودة في القائمة. +- قائمة كبيرة من الخدمات والبرامج التي تحترم الخصوصية. انا بالفعل[recommend](https://simeononsecurity.com/recommendations) بعض العناصر المرتبطة. أخطط لمواصلة القراءة في العناصر الموجودة في القائمة. diff --git a/content/til/2020-12-27/index.bn.md b/content/til/2020-12-27/index.bn.md index 0e92ec68efca0..71d7f772c71e4 100644 --- a/content/til/2020-12-27/index.bn.md +++ b/content/til/2020-12-27/index.bn.md @@ -57,4 +57,4 @@ GitHub-এ "আশ্চর্যজনক সেল্ফহোস্টেড" ## নিকিতাভোলোবোয়েভ/গোপনীয়তা-সম্মানমূলক: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- পরিষেবা এবং সফ্টওয়্যার সম্পর্কিত গোপনীয়তার একটি দুর্দান্ত তালিকা৷ আমি ইতিমধ্যে[recommend](https://simeononsecurity.ch/recommendations) লিঙ্ক করা আইটেম কিছু. আমি তালিকার আইটেমগুলিতে পড়া চালিয়ে যাওয়ার পরিকল্পনা করছি। +- পরিষেবা এবং সফ্টওয়্যার সম্পর্কিত গোপনীয়তার একটি দুর্দান্ত তালিকা৷ আমি ইতিমধ্যে[recommend](https://simeononsecurity.com/recommendations) লিঙ্ক করা আইটেম কিছু. আমি তালিকার আইটেমগুলিতে পড়া চালিয়ে যাওয়ার পরিকল্পনা করছি। diff --git a/content/til/2020-12-27/index.ca.md b/content/til/2020-12-27/index.ca.md index dd77cbe4d6bdf..2ac48b61df614 100644 --- a/content/til/2020-12-27/index.ca.md +++ b/content/til/2020-12-27/index.ca.md @@ -57,4 +57,4 @@ En conclusió, SimeonOnSecurity s'ha trobat avui amb diversos recursos interessa ## nikitavoloboev/privacy-respecting: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Una gran llista de serveis i programari respecte a la privadesa. Ja[recommend](https://simeononsecurity.ch/recommendations) alguns dels elements enllaçats. Tinc la intenció de continuar llegint els elements de la llista. +- Una gran llista de serveis i programari respecte a la privadesa. Ja[recommend](https://simeononsecurity.com/recommendations) alguns dels elements enllaçats. Tinc la intenció de continuar llegint els elements de la llista. diff --git a/content/til/2020-12-27/index.de.md b/content/til/2020-12-27/index.de.md index 54ab063b81e8d..8dc2be987b2ac 100644 --- a/content/til/2020-12-27/index.de.md +++ b/content/til/2020-12-27/index.de.md @@ -57,4 +57,4 @@ Zusammenfassend kann man sagen, dass SimeonOnSecurity heute auf mehrere interess ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Eine tolle Liste von Diensten und Software, die die Privatsphäre schützen. Ich habe bereits [recommend](https://simeononsecurity.ch/recommendations) einige der verlinkten Punkte. Ich habe vor, mich weiter in die Punkte der Liste einzulesen. +- Eine tolle Liste von Diensten und Software, die die Privatsphäre schützen. Ich habe bereits [recommend](https://simeononsecurity.com/recommendations) einige der verlinkten Punkte. Ich habe vor, mich weiter in die Punkte der Liste einzulesen. diff --git a/content/til/2020-12-27/index.en.md b/content/til/2020-12-27/index.en.md index 9fb814c5b828c..44a8a3eadae97 100644 --- a/content/til/2020-12-27/index.en.md +++ b/content/til/2020-12-27/index.en.md @@ -57,4 +57,4 @@ In conclusion, SimeonOnSecurity has come across several interesting resources to ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- A great list of privacy respecting services and software. I already [recommend](https://simeononsecurity.ch/recommendations) some of the linked items. I plan to continue reading into the items in the list. +- A great list of privacy respecting services and software. I already [recommend](https://simeononsecurity.com/recommendations) some of the linked items. I plan to continue reading into the items in the list. diff --git a/content/til/2020-12-27/index.es.md b/content/til/2020-12-27/index.es.md index 89cc85478f7aa..cc0a7b97b0f36 100644 --- a/content/til/2020-12-27/index.es.md +++ b/content/til/2020-12-27/index.es.md @@ -57,4 +57,4 @@ En conclusión, SimeonOnSecurity ha encontrado hoy varios recursos interesantes ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Una gran lista de servicios y programas que respetan la privacidad. Yo ya [recommend](https://simeononsecurity.ch/recommendations) algunos de los artículos enlazados. Pienso seguir leyendo los artículos de la lista. +- Una gran lista de servicios y programas que respetan la privacidad. Yo ya [recommend](https://simeononsecurity.com/recommendations) algunos de los artículos enlazados. Pienso seguir leyendo los artículos de la lista. diff --git a/content/til/2020-12-27/index.fr.md b/content/til/2020-12-27/index.fr.md index 8425e880186f7..6ff914509440b 100644 --- a/content/til/2020-12-27/index.fr.md +++ b/content/til/2020-12-27/index.fr.md @@ -57,4 +57,4 @@ En conclusion, SimeonOnSecurity a découvert aujourd'hui plusieurs ressources in ## nikitavoloboev/privacy-respecting : - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Une excellente liste de services et de logiciels respectueux de la vie privée. J'ai déjà [recommend](https://simeononsecurity.ch/recommendations) certains des éléments liés. J'ai l'intention de continuer à lire les éléments de la liste. +- Une excellente liste de services et de logiciels respectueux de la vie privée. J'ai déjà [recommend](https://simeononsecurity.com/recommendations) certains des éléments liés. J'ai l'intention de continuer à lire les éléments de la liste. diff --git a/content/til/2020-12-27/index.hi.md b/content/til/2020-12-27/index.hi.md index 1de46adcfde7c..6abc7333bbbf5 100644 --- a/content/til/2020-12-27/index.hi.md +++ b/content/til/2020-12-27/index.hi.md @@ -57,4 +57,4 @@ tags: [] ## निकितावोलोबोएव/गोपनीयता का सम्मान: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- सेवाओं और सॉफ्टवेयर का सम्मान करने वाली गोपनीयता की एक बड़ी सूची। मैं पहले से ही[recommend](https://simeononsecurity.ch/recommendations) कुछ जुड़े आइटम। मैं सूची में आइटमों को पढ़ना जारी रखने की योजना बना रहा हूं। +- सेवाओं और सॉफ्टवेयर का सम्मान करने वाली गोपनीयता की एक बड़ी सूची। मैं पहले से ही[recommend](https://simeononsecurity.com/recommendations) कुछ जुड़े आइटम। मैं सूची में आइटमों को पढ़ना जारी रखने की योजना बना रहा हूं। diff --git a/content/til/2020-12-27/index.it.md b/content/til/2020-12-27/index.it.md index b97e7af93a9ab..8eb6810e9406d 100644 --- a/content/til/2020-12-27/index.it.md +++ b/content/til/2020-12-27/index.it.md @@ -57,4 +57,4 @@ In conclusione, SimeonOnSecurity si è imbattuto oggi in diverse risorse interes ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Un ottimo elenco di servizi e software che rispettano la privacy. Ho già [recommend](https://simeononsecurity.ch/recommendations) alcuni degli articoli collegati. Ho intenzione di continuare a leggere gli articoli dell'elenco. +- Un ottimo elenco di servizi e software che rispettano la privacy. Ho già [recommend](https://simeononsecurity.com/recommendations) alcuni degli articoli collegati. Ho intenzione di continuare a leggere gli articoli dell'elenco. diff --git a/content/til/2020-12-27/index.ja.md b/content/til/2020-12-27/index.ja.md index 47d4ae0b744a1..3928edf8065de 100644 --- a/content/til/2020-12-27/index.ja.md +++ b/content/til/2020-12-27/index.ja.md @@ -57,4 +57,4 @@ GitHubの「Awesome Selfhosted」リストも、SimeonOnSecurityが注目した ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- プライバシーを尊重するサービスやソフトウェアの素晴らしいリストです。私はすでに [recommend](https://simeononsecurity.ch/recommendations)リンク先の項目の一部です。今後もリストの項目を読み込んでいく予定です。 +- プライバシーを尊重するサービスやソフトウェアの素晴らしいリストです。私はすでに [recommend](https://simeononsecurity.com/recommendations)リンク先の項目の一部です。今後もリストの項目を読み込んでいく予定です。 diff --git a/content/til/2020-12-27/index.nl.md b/content/til/2020-12-27/index.nl.md index c29f2be64761e..750d2b7139d30 100644 --- a/content/til/2020-12-27/index.nl.md +++ b/content/til/2020-12-27/index.nl.md @@ -57,4 +57,4 @@ Tot slot is SimeonOnSecurity vandaag verschillende interessante bronnen tegengek ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Een geweldige lijst met privacy respecterende diensten en software. Ik heb al [recommend](https://simeononsecurity.ch/recommendations) sommige van de gelinkte items. Ik ben van plan om verder te lezen in de items van de lijst. +- Een geweldige lijst met privacy respecterende diensten en software. Ik heb al [recommend](https://simeononsecurity.com/recommendations) sommige van de gelinkte items. Ik ben van plan om verder te lezen in de items van de lijst. diff --git a/content/til/2020-12-27/index.pa.md b/content/til/2020-12-27/index.pa.md index 5172979a630d8..168ab13ea7aa5 100644 --- a/content/til/2020-12-27/index.pa.md +++ b/content/til/2020-12-27/index.pa.md @@ -57,4 +57,4 @@ GitHub 'ਤੇ "Awesome Selfhosted" ਸੂਚੀ ਇੱਕ ਹੋਰ ਸਰੋ ## nikitavoloboev/privacy-respecting: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- ਸੇਵਾਵਾਂ ਅਤੇ ਸੌਫਟਵੇਅਰ ਦਾ ਸਨਮਾਨ ਕਰਨ ਵਾਲੀ ਗੋਪਨੀਯਤਾ ਦੀ ਇੱਕ ਮਹਾਨ ਸੂਚੀ। ਮੈਂ ਪਹਿਲਾਂ ਹੀ[recommend](https://simeononsecurity.ch/recommendations) ਕੁਝ ਲਿੰਕ ਕੀਤੀਆਂ ਆਈਟਮਾਂ। ਮੈਂ ਸੂਚੀ ਵਿੱਚ ਆਈਟਮਾਂ ਨੂੰ ਪੜ੍ਹਨਾ ਜਾਰੀ ਰੱਖਣ ਦੀ ਯੋਜਨਾ ਬਣਾ ਰਿਹਾ ਹਾਂ। +- ਸੇਵਾਵਾਂ ਅਤੇ ਸੌਫਟਵੇਅਰ ਦਾ ਸਨਮਾਨ ਕਰਨ ਵਾਲੀ ਗੋਪਨੀਯਤਾ ਦੀ ਇੱਕ ਮਹਾਨ ਸੂਚੀ। ਮੈਂ ਪਹਿਲਾਂ ਹੀ[recommend](https://simeononsecurity.com/recommendations) ਕੁਝ ਲਿੰਕ ਕੀਤੀਆਂ ਆਈਟਮਾਂ। ਮੈਂ ਸੂਚੀ ਵਿੱਚ ਆਈਟਮਾਂ ਨੂੰ ਪੜ੍ਹਨਾ ਜਾਰੀ ਰੱਖਣ ਦੀ ਯੋਜਨਾ ਬਣਾ ਰਿਹਾ ਹਾਂ। diff --git a/content/til/2020-12-27/index.pl.md b/content/til/2020-12-27/index.pl.md index e811f417bd17c..dc3c56d16f25b 100644 --- a/content/til/2020-12-27/index.pl.md +++ b/content/til/2020-12-27/index.pl.md @@ -57,4 +57,4 @@ Podsumowując, SimeonOnSecurity natknął się dziś na kilka interesujących za ## nikitavoloboev/privacy-respecting: - [https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Świetna lista usług i oprogramowania szanujących prywatność. Już [recommend](https://simeononsecurity.ch/recommendations) niektóre z połączonych elementów. Planuję kontynuować czytanie pozycji z listy. +- Świetna lista usług i oprogramowania szanujących prywatność. Już [recommend](https://simeononsecurity.com/recommendations) niektóre z połączonych elementów. Planuję kontynuować czytanie pozycji z listy. diff --git a/content/til/2020-12-27/index.pt.md b/content/til/2020-12-27/index.pt.md index c306d2191f38c..a5daf87b744b3 100644 --- a/content/til/2020-12-27/index.pt.md +++ b/content/til/2020-12-27/index.pt.md @@ -57,4 +57,4 @@ Em conclusão, SimeonOnSecurity encontrou vários recursos interessantes hoje qu ## nikitavoloboev/respeitador da privacidade: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Uma grande lista de serviços e softwares que respeitam a privacidade. Eu já[recommend](https://simeononsecurity.ch/recommendations) alguns dos itens vinculados. Pretendo continuar lendo os itens da lista. +- Uma grande lista de serviços e softwares que respeitam a privacidade. Eu já[recommend](https://simeononsecurity.com/recommendations) alguns dos itens vinculados. Pretendo continuar lendo os itens da lista. diff --git a/content/til/2020-12-27/index.ro.md b/content/til/2020-12-27/index.ro.md index 9dc7e9c461698..336b975199935 100644 --- a/content/til/2020-12-27/index.ro.md +++ b/content/til/2020-12-27/index.ro.md @@ -57,4 +57,4 @@ Pentru cei care sunt interesați să înființeze un laborator acasă, SimeonOnS ## nikitavoloboev/privacy-respecting: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- O listă excelentă de servicii și software care respectă confidențialitatea. eu deja[recommend](https://simeononsecurity.ch/recommendations) unele dintre elementele legate. Plănuiesc să continui să citesc articolele din listă. +- O listă excelentă de servicii și software care respectă confidențialitatea. eu deja[recommend](https://simeononsecurity.com/recommendations) unele dintre elementele legate. Plănuiesc să continui să citesc articolele din listă. diff --git a/content/til/2020-12-27/index.ru.md b/content/til/2020-12-27/index.ru.md index d5fae9f85d268..0156b17bcd12f 100644 --- a/content/til/2020-12-27/index.ru.md +++ b/content/til/2020-12-27/index.ru.md @@ -57,4 +57,4 @@ SimeonOnSecurity также наткнулся на «контрольный с ## nikitavoloboev/соблюдение конфиденциальности: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- Большой список услуг и программного обеспечения, обеспечивающих конфиденциальность. я уже[recommend](https://simeononsecurity.ch/recommendations) некоторые из связанных элементов. Я планирую продолжить чтение пунктов в списке. +- Большой список услуг и программного обеспечения, обеспечивающих конфиденциальность. я уже[recommend](https://simeononsecurity.com/recommendations) некоторые из связанных элементов. Я планирую продолжить чтение пунктов в списке. diff --git a/content/til/2020-12-27/index.zh.md b/content/til/2020-12-27/index.zh.md index d6785e0efa6f5..16f9709cb5d6d 100644 --- a/content/til/2020-12-27/index.zh.md +++ b/content/til/2020-12-27/index.zh.md @@ -57,4 +57,4 @@ GitHub 上的“Awesome Selfhosted”列表是另一个引起 SimeonOnSecurity ## nikitavoloboev/尊重隐私: -[https://github.com/nikitavoloboev/privacy-respecting](https://github.com/nikitavoloboev/privacy-respecting) -- 大量尊重隐私的服务和软件。我已经[recommend](https://simeononsecurity.ch/recommendations) 一些链接的项目。我打算继续阅读列表中的项目。 +- 大量尊重隐私的服务和软件。我已经[recommend](https://simeononsecurity.com/recommendations) 一些链接的项目。我打算继续阅读列表中的项目。 diff --git a/content/til/2021-01-04/index.en.md b/content/til/2021-01-04/index.en.md index 4368bef612047..94a19122eaf31 100644 --- a/content/til/2021-01-04/index.en.md +++ b/content/til/2021-01-04/index.en.md @@ -10,9 +10,9 @@ tags: ["Windows Defender Application Control", "WDAC Policies", "Windows Securit **What SimeonOnSecurity learned about and found interesting today** -Today, SimeonOnSecurity delved into the topic of auditing and enforcing Windows Defender Application Control [WDAC](https://simeononsecurity.ch/github/windows-defender-application-control-hardening/) policies. [WDAC](https://simeononsecurity.ch/github/windows-defender-application-control-hardening/) is a feature in Windows that helps to prevent unauthorized or untrusted software from running on a device. It provides a means of controlling which applications can run on a device, thereby helping to improve the overall security of the device. +Today, SimeonOnSecurity delved into the topic of auditing and enforcing Windows Defender Application Control [WDAC](https://simeononsecurity.com/github/windows-defender-application-control-hardening/) policies. [WDAC](https://simeononsecurity.com/github/windows-defender-application-control-hardening/) is a feature in Windows that helps to prevent unauthorized or untrusted software from running on a device. It provides a means of controlling which applications can run on a device, thereby helping to improve the overall security of the device. -## Auditing and Enforcing Windows Defender Application Control [WDAC](https://simeononsecurity.ch/github/windows-defender-application-control-hardening/) Policies: +## Auditing and Enforcing Windows Defender Application Control [WDAC](https://simeononsecurity.com/github/windows-defender-application-control-hardening/) Policies: - [Microsoft - Audit Windows Defender Application Control Policies](https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/audit-windows-defender-application-control-policies) - [Microsoft - Deploy Windows Defender Application Control policies by using Group Policy](https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/deploy-windows-defender-application-control-policies-using-group-policy) - [Microsoft - Deploy Windows Defender Application Control policies by using Microsoft Intune](https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/deploy-windows-defender-application-control-policies-using-intune) diff --git a/content/til/2021-01-08/index.en.md b/content/til/2021-01-08/index.en.md index 4642a93297faf..b769af6d39f09 100644 --- a/content/til/2021-01-08/index.en.md +++ b/content/til/2021-01-08/index.en.md @@ -14,7 +14,7 @@ Today, SimeonOnSecurity learned about and found interesting topics related to NT In the world of file systems, NTFS is a commonly used file system for Windows. To enhance its performance and reliability, SimeonOnSecurity found a great resource on PonderWorthy discussing NTFS tweaks using fsutil. The article offers insight into how to optimize the NTFS file system for better performance and stability. -SimeonOnSecurity also updated multiple repositories, including setup-scripts, [Windows-Optimize-Harden-Debloat](https://simeononsecurity.ch/github/windows-optimize-debloat/), and [Windows-Optimize-Debloat](https://simeononsecurity.ch/github/Windows-Optimize-Harden-Debloat/). These repositories contain scripts and tools to optimize, harden, and [debloat Windows](https://simeononsecurity.ch/github/windows-optimize-debloat/) systems. +SimeonOnSecurity also updated multiple repositories, including setup-scripts, [Windows-Optimize-Harden-Debloat](https://simeononsecurity.com/github/windows-optimize-debloat/), and [Windows-Optimize-Debloat](https://simeononsecurity.com/github/Windows-Optimize-Harden-Debloat/). These repositories contain scripts and tools to optimize, harden, and [debloat Windows](https://simeononsecurity.com/github/windows-optimize-debloat/) systems. In addition, SimeonOnSecurity watched a number of videos related to information security and found them interesting. These videos include BHIS - Talkin' Bout News 2021-01-06, Crosstalk Solutions - Cloud Key Firmware v2.0.24 - Major Update!, Hak5 - Burn-in Test Payloads, Hak5 - The 3 (or 4) P's of Post Exploitation, Null Byte - One Way Hackers Can Perform Keystroke Injection Over Wi-Fi from a Smartphone, and The Linux Experiment - elementary OS is MORE than a Linux distribution.... These videos provide information on various topics in the field of information security and showcase new tools, techniques, and ideas in the industry. diff --git a/content/til/2021-02-17/index.de.md b/content/til/2021-02-17/index.de.md index 9b6afad196e8a..6ddea7f3a9a81 100644 --- a/content/til/2021-02-17/index.de.md +++ b/content/til/2021-02-17/index.de.md @@ -16,7 +16,7 @@ Zusätzlich zu der aktualisierten Seite hat SimeonOnSecurity auch einige nützli Zwei weitere Ressourcen beziehen sich auf die Konvertierung von JSON-Daten in PowerShell. Die Microsoft-Dokumentation enthält Informationen zu den Cmdlets ConvertFrom-Json und ConvertTo-Json. Diese Cmdlets ermöglichen die Konvertierung von JSON-Daten in und aus PowerShell-Objekten, was eine einfachere Bearbeitung und Analyse der Daten ermöglicht. ## Aktualisierte Seiten: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Lernressourcen: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.en.md b/content/til/2021-02-17/index.en.md index db6a599ba482b..e7d89d21f7eec 100644 --- a/content/til/2021-02-17/index.en.md +++ b/content/til/2021-02-17/index.en.md @@ -16,7 +16,7 @@ In addition to the updated page, SimeonOnSecurity also discovered some useful le Another two resources are related to the conversion of JSON data in PowerShell. The Microsoft documentation provides information on the ConvertFrom-Json and ConvertTo-Json cmdlets. These cmdlets make it possible to convert JSON data into and from PowerShell objects, allowing for easier manipulation and analysis of the data. ## Updated Pages: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Learning Resources: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.es.md b/content/til/2021-02-17/index.es.md index 2175460b54c25..eeaba32d096e6 100644 --- a/content/til/2021-02-17/index.es.md +++ b/content/til/2021-02-17/index.es.md @@ -16,7 +16,7 @@ Además de la página actualizada, SimeonOnSecurity también descubrió algunos Otros dos recursos están relacionados con la conversión de datos JSON en PowerShell. La documentación de Microsoft proporciona información sobre los cmdlets ConvertFrom-Json y ConvertTo-Json. Estos cmdlets permiten convertir datos JSON en y desde objetos PowerShell, lo que facilita la manipulación y el análisis de los datos. ## Páginas actualizadas: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Recursos de Aprendizaje: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.fr.md b/content/til/2021-02-17/index.fr.md index 60c4c058d693b..6848338e97dfc 100644 --- a/content/til/2021-02-17/index.fr.md +++ b/content/til/2021-02-17/index.fr.md @@ -16,7 +16,7 @@ Outre la page mise à jour, SimeonOnSecurity a également découvert quelques re Deux autres ressources sont liées à la conversion de données JSON dans PowerShell. La documentation Microsoft fournit des informations sur les cmdlets ConvertFrom-Json et ConvertTo-Json. Ces cmdlets permettent de convertir des données JSON en objets PowerShell ou à partir de ceux-ci, ce qui facilite la manipulation et l'analyse des données. ## Pages mises à jour : -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Ressources pédagogiques : - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.it.md b/content/til/2021-02-17/index.it.md index d2ed8955105ad..c1a736a823eb3 100644 --- a/content/til/2021-02-17/index.it.md +++ b/content/til/2021-02-17/index.it.md @@ -16,7 +16,7 @@ Oltre alla pagina aggiornata, SimeonOnSecurity ha scoperto anche alcune utili ri Altre due risorse riguardano la conversione di dati JSON in PowerShell. La documentazione Microsoft fornisce informazioni sulle cmdlet ConvertFrom-Json e ConvertTo-Json. Queste cmdlet consentono di convertire i dati JSON in e da oggetti PowerShell, facilitando la manipolazione e l'analisi dei dati. ## Pagine aggiornate: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Risorse didattiche: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.ja.md b/content/til/2021-02-17/index.ja.md index 39ca5ad6efcc8..5141be9cedd7a 100644 --- a/content/til/2021-02-17/index.ja.md +++ b/content/til/2021-02-17/index.ja.md @@ -16,7 +16,7 @@ SimeonOnSecurityは、更新されたページに加えて、いくつかの有 もう2つのリソースは、PowerShellでのJSONデータの変換に関連するものです。Microsoftのドキュメントには、ConvertFrom-JsonおよびConvertTo-Jsonコマンドレットに関する情報が記載されています。これらのコマンドレットを使用すると、JSONデータをPowerShellオブジェクトに変換したり、PowerShellオブジェクトから変換したりすることができ、データの操作や分析が容易になります。 ## Updated Pages: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## ラーニング・リソース - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.nl.md b/content/til/2021-02-17/index.nl.md index 3e24359cfbbbe..8f87217ba1281 100644 --- a/content/til/2021-02-17/index.nl.md +++ b/content/til/2021-02-17/index.nl.md @@ -16,7 +16,7 @@ Naast de bijgewerkte pagina heeft SimeonOnSecurity ook een aantal nuttige leermi Twee andere bronnen hebben betrekking op het omzetten van JSON-gegevens in PowerShell. De Microsoft documentatie biedt informatie over de ConvertFrom-Json en ConvertTo-Json cmdlets. Deze cmdlets maken het mogelijk om JSON-gegevens te converteren naar en van PowerShell-objecten, waardoor de gegevens gemakkelijker kunnen worden gemanipuleerd en geanalyseerd. ## Bijgewerkte pagina's: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Leerbronnen: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.pl.md b/content/til/2021-02-17/index.pl.md index 22628cb4976e3..877380e5c563f 100644 --- a/content/til/2021-02-17/index.pl.md +++ b/content/til/2021-02-17/index.pl.md @@ -16,7 +16,7 @@ Oprócz zaktualizowanej strony, SimeonOnSecurity odkrył również kilka przydat Kolejne dwa zasoby dotyczą konwersji danych JSON w PowerShell. Dokumentacja Microsoft zawiera informacje na temat poleceń cmdlet ConvertFrom-Json i ConvertTo-Json. Te polecenia cmdlet umożliwiają konwersję danych JSON do i z obiektów PowerShell, umożliwiając łatwiejszą manipulację i analizę danych. ## Zaktualizowane strony: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Zasoby edukacyjne: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.ro.md b/content/til/2021-02-17/index.ro.md index 22e9396d2175c..d4a1fa5072ef8 100644 --- a/content/til/2021-02-17/index.ro.md +++ b/content/til/2021-02-17/index.ro.md @@ -16,7 +16,7 @@ Pe lângă pagina actualizată, SimeonOnSecurity a mai descoperit și câteva re Alte două resurse sunt legate de conversia datelor JSON în PowerShell. Documentația Microsoft oferă informații despre cmdleturile ConvertFrom-Json și ConvertTo-Json. Aceste cmdlet-uri fac posibilă conversia datelor JSON în și din obiecte PowerShell, permițând o manipulare și o analiză mai ușoară a datelor. ## Pagini actualizate: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Resurse de învățare: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.ru.md b/content/til/2021-02-17/index.ru.md index eb9ee30b25778..4ffc6b564d6d3 100644 --- a/content/til/2021-02-17/index.ru.md +++ b/content/til/2021-02-17/index.ru.md @@ -16,7 +16,7 @@ SimeonOnSecurity обновил страницу на своем сайте и Еще два ресурса связаны с преобразованием JSON-данных в PowerShell. В документации Microsoft содержится информация о командах ConvertFrom-Json и ConvertTo-Json. Эти команды позволяют преобразовывать JSON-данные в объекты PowerShell и из них, что упрощает манипулирование и анализ данных. ## Обновленные страницы: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## Учебные ресурсы: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2021-02-17/index.zh.md b/content/til/2021-02-17/index.zh.md index c6b4b8e5acea0..905d45f18c9b4 100644 --- a/content/til/2021-02-17/index.zh.md +++ b/content/til/2021-02-17/index.zh.md @@ -16,7 +16,7 @@ SimeonOnSecurity 更新了他网站上的一个页面,并了解了一些他认 另外两个资源与在 PowerShell 中转换 JSON 数据有关。Microsoft 文档提供了有关 ConvertFrom-Json 和 ConvertTo-Json cmdlets 的信息。通过这些 cmdlet,可以将 JSON 数据转换为 PowerShell 对象或从 PowerShell 对象转换为 JSON 数据,从而可以更轻松地操作和分析数据。 ## 已更新页面: -- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.ch/writeups/hackthebox-invite-challenge/) +- [HackTheBox - Invite Challenge (Windows/Linux)](https://simeononsecurity.com/writeups/hackthebox-invite-challenge/) ## 学习资源: - [Cameron Nokes - Working with JSON in bash using jq](https://cameronnokes.com/blog/working-with-json-in-bash-using-jq/) diff --git a/content/til/2022-05-03/index.en.md b/content/til/2022-05-03/index.en.md index 0ac9e11485928..9d2691d70552a 100644 --- a/content/til/2022-05-03/index.en.md +++ b/content/til/2022-05-03/index.en.md @@ -9,7 +9,7 @@ tags: ["Automation", "Compliance", "Ansible", "Ansible Playbooks", "Ansible Coll --- **What SimeonOnSecurity learned about and found interesting today** -SimeonOnSecurity learned about [Windows STIG](https://simeononsecurity.ch/github/stiging-standalone-windows-servers/) Ansible and updated related repos. Also, studied various Microsoft and Ansible resources related to powershell, remoting, and executing shell/powershell commands on Windows using modules like invoke-command, start-process, win_powershell, win_shell, psexec, and win_psexec. +SimeonOnSecurity learned about [Windows STIG](https://simeononsecurity.com/github/stiging-standalone-windows-servers/) Ansible and updated related repos. Also, studied various Microsoft and Ansible resources related to powershell, remoting, and executing shell/powershell commands on Windows using modules like invoke-command, start-process, win_powershell, win_shell, psexec, and win_psexec. ## New/Updated Repos: diff --git a/content/til/2022-05-18/index.en.md b/content/til/2022-05-18/index.en.md index a4706c2dd8fad..cdbdf391959e8 100644 --- a/content/til/2022-05-18/index.en.md +++ b/content/til/2022-05-18/index.en.md @@ -10,7 +10,7 @@ tags: ["automation", "WDAC", "application control", "Windows Defender Applicatio **What SimeonOnSecurity learned about and found interesting today** -Today, SimeonOnSecurity updated his repository Windows-Defender-Application-Control-Hardening and learned about [Windows Defender Application Control](https://simeononsecurity.ch/github/windows-defender-application-control-hardening/) [WDAC](https://simeononsecurity.ch/github/windows-defender-application-control-hardening/), a feature of Windows 10 Enterprise and Windows Server 2019 that provides security by controlling what is executed on a device. +Today, SimeonOnSecurity updated his repository Windows-Defender-Application-Control-Hardening and learned about [Windows Defender Application Control](https://simeononsecurity.com/github/windows-defender-application-control-hardening/) [WDAC](https://simeononsecurity.com/github/windows-defender-application-control-hardening/), a feature of Windows 10 Enterprise and Windows Server 2019 that provides security by controlling what is executed on a device. SimeonOnSecurity delved into the Microsoft documentation on WDAC and discovered several key resources for creating and deploying policies. He learned about how to create a WDAC policy for fixed-workload devices using a reference computer, how to deploy WDAC policies using script, and how to use multiple policies for different scenarios. diff --git a/content/til/2022-05-23/index.en.md b/content/til/2022-05-23/index.en.md index 45fa3b99eafa4..8c053cf06aca6 100644 --- a/content/til/2022-05-23/index.en.md +++ b/content/til/2022-05-23/index.en.md @@ -10,13 +10,13 @@ tags: ["automation", "Powershell", "Chocolatey Package Manager", "Chocolatey", " **What SimeonOnSecurity learned about and found interesting today** -Today, SimeonOnSecurity learned about the process of creating packages for the [Chocolatey Package Manager](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/). [Chocolatey](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/) is a package manager for Windows that makes it easy to install, upgrade, and manage applications and tools. By creating packages, SimeonOnSecurity can automate the installation of software and share packages with others in the community. +Today, SimeonOnSecurity learned about the process of creating packages for the [Chocolatey Package Manager](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/). [Chocolatey](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/) is a package manager for Windows that makes it easy to install, upgrade, and manage applications and tools. By creating packages, SimeonOnSecurity can automate the installation of software and share packages with others in the community. SimeonOnSecurity created and updated two repositories on GitHub related to creating Chocolatey packages. The first repository, simeononsecurity/Chocolatey-Nethor, is a package for Nethor. The second repository, simeononsecurity/chocolateypackages, is a collection of packages created by SimeonOnSecurity for various applications and tools. To create a package, SimeonOnSecurity used the Nuspec file format, which provides metadata about the package and its contents. The package creation process also involved using functions such as Install-ChocolateyInstallPackage and Install-ChocolateyPackage to specify the software to be installed and any necessary dependencies. -SimeonOnSecurity also reviewed several learning resources, including the official Chocolatey documentation and a tutorial by Top Bug Net, to gain a deeper understanding of the process of creating and publishing [Chocolatey packages](https://simeononsecurity.ch/articles/why-you-should-be-using-chocolatey-for-windows-package-management/). +SimeonOnSecurity also reviewed several learning resources, including the official Chocolatey documentation and a tutorial by Top Bug Net, to gain a deeper understanding of the process of creating and publishing [Chocolatey packages](https://simeononsecurity.com/articles/why-you-should-be-using-chocolatey-for-windows-package-management/). Overall, SimeonOnSecurity's learning experience today provided a comprehensive understanding of the process of creating packages for the Chocolatey Package Manager, making it easier to automate software installations and share packages with others in the community. diff --git a/content/tools/index.en.md b/content/tools/index.en.md index 3453fdd3e467c..c88f99d0328fc 100644 --- a/content/tools/index.en.md +++ b/content/tools/index.en.md @@ -21,7 +21,7 @@ sitemap: | Network Tools | A client-side tool that allows you to ping a domain or IP address and view the latency results. | [HTTP Ping Tool](/ping) | | Network Tools | Check your public IP address with our What's My IP tool. Easily find your IP address for networking and security purposes. | [What's My IP](/whatsmyip) | | File Permissions Tools | A menu-based tool that generates chmod commands based on user input for modifying file permissions. | [Chmod Command Generator](/chmod) | -| [Security Headers Check](https://simeononsecurity.ch/securityheaders/) | Check the security headers of a website and ensure it follows best security practices. This tool is capable of handling CORS policies. | [Security Headers Check](/securityheaders) | +| [Security Headers Check](https://simeononsecurity.com/securityheaders/) | Check the security headers of a website and ensure it follows best security practices. This tool is capable of handling CORS policies. | [Security Headers Check](/securityheaders) | ## Password Tools This section provides tools related to password management and security. diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.de.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.de.md index 2e4c4431b0d32..995f1e01f776a 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.de.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.de.md @@ -10,7 +10,7 @@ coverAlt: "eine Cartoon-Tresortür, die mit einem Schlüssel aufgeschlossen wird coverCaption: "" --- -Eine umfassende Anleitung zum Lösen der "Bank Heist" Krypto-Herausforderung auf HackTheBox. Die Herausforderung beinhaltet die Entschlüsselung einer [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) Text mit Decode.fr und einen atbash-Chiffretext mit CyberChef, um die Flagge zu enthüllen. Eine Pflichtlektüre für angehende Cybersicherheitsexperten und alle, die ihre Kryptografiekenntnisse verbessern möchten. +Eine umfassende Anleitung zum Lösen der "Bank Heist" Krypto-Herausforderung auf HackTheBox. Die Herausforderung beinhaltet die Entschlüsselung einer [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) Text mit Decode.fr und einen atbash-Chiffretext mit CyberChef, um die Flagge zu enthüllen. Eine Pflichtlektüre für angehende Cybersicherheitsexperten und alle, die ihre Kryptografiekenntnisse verbessern möchten. ## Bereitgestellte Dateien: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.en.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.en.md index b4f681a3280f4..4f9f58f37edd2 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.en.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.en.md @@ -10,7 +10,7 @@ coverAlt: "a cartoon vault door being unlocked with a key revealing a treasure c coverCaption: "" --- -A comprehensive guide to solving the "Bank Heist" Crypto challenge on HackTheBox. The challenge involves decoding a [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) text using Decode.fr and an atbash cipher text using CyberChef to reveal the flag. A must-read for aspiring cyber security professionals and anyone looking to enhance their skills in cryptography. +A comprehensive guide to solving the "Bank Heist" Crypto challenge on HackTheBox. The challenge involves decoding a [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) text using Decode.fr and an atbash cipher text using CyberChef to reveal the flag. A must-read for aspiring cyber security professionals and anyone looking to enhance their skills in cryptography. ## Provided Files: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.es.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.es.md index 36155edcf4742..e62bee3f64d18 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.es.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.es.md @@ -10,7 +10,7 @@ coverAlt: "una puerta de cámara acorazada de dibujos animados que se abre con u coverCaption: "" --- -Una guía completa para resolver el desafío criptográfico "Atraco a un banco" en HackTheBox. El desafío consiste en descifrar un [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) utilizando Decode.fr y un texto cifrado atbash utilizando CyberChef para revelar la bandera. Una lectura obligada para los aspirantes a profesionales de la ciberseguridad y para cualquiera que quiera mejorar sus conocimientos de criptografía. +Una guía completa para resolver el desafío criptográfico "Atraco a un banco" en HackTheBox. El desafío consiste en descifrar un [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) utilizando Decode.fr y un texto cifrado atbash utilizando CyberChef para revelar la bandera. Una lectura obligada para los aspirantes a profesionales de la ciberseguridad y para cualquiera que quiera mejorar sus conocimientos de criptografía. ## Archivos proporcionados: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.fr.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.fr.md index 0df0f7e25a5e3..ee72ad384eb08 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.fr.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.fr.md @@ -10,7 +10,7 @@ coverAlt: "une porte de coffre-fort en bande dessinée qui s'ouvre avec une clé coverCaption: "" --- -Un guide complet pour résoudre le défi Crypto "Bank Heist" sur HackTheBox. Le défi consiste à décoder un [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) Le texte chiffré de l'attaque de l'armée française a été révélé à l'aide de Decode.fr et le texte chiffré de l'attaque à l'aide de CyberChef pour dévoiler le drapeau. Une lecture incontournable pour les professionnels de la cybersécurité en herbe et pour tous ceux qui cherchent à améliorer leurs compétences en cryptographie. +Un guide complet pour résoudre le défi Crypto "Bank Heist" sur HackTheBox. Le défi consiste à décoder un [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) Le texte chiffré de l'attaque de l'armée française a été révélé à l'aide de Decode.fr et le texte chiffré de l'attaque à l'aide de CyberChef pour dévoiler le drapeau. Une lecture incontournable pour les professionnels de la cybersécurité en herbe et pour tous ceux qui cherchent à améliorer leurs compétences en cryptographie. ## Fichiers fournis : diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.it.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.it.md index 4b8981e25c770..03856b90c767b 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.it.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.it.md @@ -10,7 +10,7 @@ coverAlt: "una porta di un caveau a fumetti che viene aperta con una chiave e ri coverCaption: "" --- -Una guida completa per risolvere la sfida Crypto "Bank Heist" su HackTheBox. La sfida prevede la decodifica di un [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) e un testo cifrato atbash usando CyberChef per rivelare la bandiera. Una lettura imperdibile per gli aspiranti professionisti della sicurezza informatica e per chiunque voglia migliorare le proprie competenze in materia di crittografia. +Una guida completa per risolvere la sfida Crypto "Bank Heist" su HackTheBox. La sfida prevede la decodifica di un [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) e un testo cifrato atbash usando CyberChef per rivelare la bandiera. Una lettura imperdibile per gli aspiranti professionisti della sicurezza informatica e per chiunque voglia migliorare le proprie competenze in materia di crittografia. ## File forniti: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ja.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ja.md index 5c5972b08f7a1..f9704e82ff596 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ja.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ja.md @@ -10,7 +10,7 @@ coverAlt: "夕暮れ時のパリの街並みを背景に、金庫の扉を鍵で coverCaption: "" --- -HackTheBoxのCryptoチャレンジ「Bank Heist」を解くための包括的なガイドです。このチャレンジでは、暗号を解読するために [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/)Decode.frを使ったテキストとCyberChefを使ったatbashの暗号テキストからフラグを明らかにする。サイバーセキュリティのプロを目指す人、暗号技術のスキルアップを目指す人は必読の書です。 +HackTheBoxのCryptoチャレンジ「Bank Heist」を解くための包括的なガイドです。このチャレンジでは、暗号を解読するために [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/)Decode.frを使ったテキストとCyberChefを使ったatbashの暗号テキストからフラグを明らかにする。サイバーセキュリティのプロを目指す人、暗号技術のスキルアップを目指す人は必読の書です。 ## Provided Files: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.nl.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.nl.md index 702abb67842ee..8b5791003462b 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.nl.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.nl.md @@ -10,7 +10,7 @@ coverAlt: "een cartoonachtige kluisdeur die wordt ontgrendeld met een sleutel di coverCaption: "" --- -Een uitgebreide handleiding voor het oplossen van de Crypto-uitdaging "Bank Heist" op HackTheBox. De uitdaging bestaat uit het decoderen van een [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) tekst met Decode.fr en een atbash-cryptekst met CyberChef om de vlag te onthullen. Een must voor aspirant cyberbeveiligingsprofessionals en iedereen die zijn vaardigheden in cryptografie wil verbeteren. +Een uitgebreide handleiding voor het oplossen van de Crypto-uitdaging "Bank Heist" op HackTheBox. De uitdaging bestaat uit het decoderen van een [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) tekst met Decode.fr en een atbash-cryptekst met CyberChef om de vlag te onthullen. Een must voor aspirant cyberbeveiligingsprofessionals en iedereen die zijn vaardigheden in cryptografie wil verbeteren. ## Meegeleverde bestanden: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.pl.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.pl.md index 7d5f30ff73488..59c24ada9b5b7 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.pl.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.pl.md @@ -10,7 +10,7 @@ coverAlt: "kreskówkowe drzwi skarbca otwierane kluczem, odsłaniające skrzyni coverCaption: "" --- -Kompleksowy przewodnik po rozwiązaniu wyzwania kryptograficznego "Napad na bank" w HackTheBox. Wyzwanie polega na zdekodowaniu [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) przy użyciu Decode.fr i szyfrogramu atbash przy użyciu CyberChef w celu ujawnienia flagi. Lektura obowiązkowa dla aspirujących specjalistów ds. cyberbezpieczeństwa i każdego, kto chce podnieść swoje umiejętności w zakresie kryptografii. +Kompleksowy przewodnik po rozwiązaniu wyzwania kryptograficznego "Napad na bank" w HackTheBox. Wyzwanie polega na zdekodowaniu [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) przy użyciu Decode.fr i szyfrogramu atbash przy użyciu CyberChef w celu ujawnienia flagi. Lektura obowiązkowa dla aspirujących specjalistów ds. cyberbezpieczeństwa i każdego, kto chce podnieść swoje umiejętności w zakresie kryptografii. ## Dostarczone pliki: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ro.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ro.md index e9823fdf57b59..62fec7f88cf11 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ro.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ro.md @@ -10,7 +10,7 @@ coverAlt: "o ușă de seif din desene animate care se deschide cu o cheie și de coverCaption: "" --- -Un ghid complet pentru a rezolva provocarea Crypto "Bank Heist" pe HackTheBox. Provocarea presupune decodarea unui [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) text folosind Decode.fr și un text cifrat atbash folosind CyberChef pentru a descoperi steagul. O lectură obligatorie pentru profesioniștii aspiranți la securitate cibernetică și pentru oricine dorește să își îmbunătățească abilitățile în domeniul criptografiei. +Un ghid complet pentru a rezolva provocarea Crypto "Bank Heist" pe HackTheBox. Provocarea presupune decodarea unui [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) text folosind Decode.fr și un text cifrat atbash folosind CyberChef pentru a descoperi steagul. O lectură obligatorie pentru profesioniștii aspiranți la securitate cibernetică și pentru oricine dorește să își îmbunătățească abilitățile în domeniul criptografiei. ## Fișiere furnizate: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ru.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ru.md index 506f731b7d461..d82ee864bfb4b 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ru.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.ru.md @@ -10,7 +10,7 @@ coverAlt: "мультяшная дверь хранилища, отпираем coverCaption: "" --- -Исчерпывающее руководство по решению криптозадачи "Ограбление банка" на HackTheBox. Задача заключается в расшифровке [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) текст с помощью Decode.fr и шифр-текст atbash с помощью CyberChef для раскрытия флага. Обязательно к прочтению для начинающих специалистов по кибербезопасности и всех, кто хочет повысить свою квалификацию в области криптографии. +Исчерпывающее руководство по решению криптозадачи "Ограбление банка" на HackTheBox. Задача заключается в расшифровке [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) текст с помощью Decode.fr и шифр-текст atbash с помощью CyberChef для раскрытия флага. Обязательно к прочтению для начинающих специалистов по кибербезопасности и всех, кто хочет повысить свою квалификацию в области криптографии. ## Предоставляемые файлы: diff --git a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.zh.md b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.zh.md index 6e9c6aeb90af5..5160512c7e08b 100644 --- a/content/writeups/hackthebox-challenges-crypto-bank_heist/index.zh.md +++ b/content/writeups/hackthebox-challenges-crypto-bank_heist/index.zh.md @@ -10,7 +10,7 @@ coverAlt: "卡通金库门被一把钥匙打开,露出一个宝箱,背景是 coverCaption: "" --- -破解 HackTheBox 上 "银行劫案 "加密挑战的综合指南。该挑战涉及解码一个 [T9](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.ch/articles/introduction-to-t9-cipher/)使用 Decode.fr 阅读文本,并使用 CyberChef 阅读 atbash 密码文本,从而揭示旗帜。对于有抱负的网络安全专业人士和任何希望提高密码学技能的人来说,这是一本必读书。 +破解 HackTheBox 上 "银行劫案 "加密挑战的综合指南。该挑战涉及解码一个 [T9](https://simeononsecurity.com/articles/introduction-to-t9-cipher/) or [Multitap cipher](https://simeononsecurity.com/articles/introduction-to-t9-cipher/)使用 Decode.fr 阅读文本,并使用 CyberChef 阅读 atbash 密码文本,从而揭示旗帜。对于有抱负的网络安全专业人士和任何希望提高密码学技能的人来说,这是一本必读书。 ## 提供的文件: