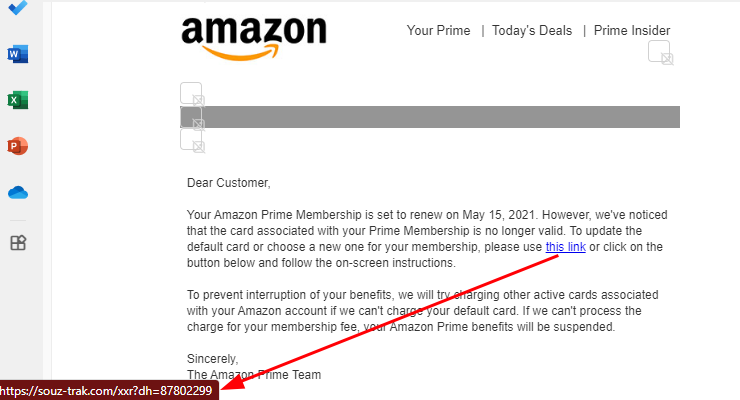
Learn how to spot deceptive links. Do not click on links; instead, hover over the links and buttons to check if the links are genuine:
- +
+ 
If you receive a suspicious email, report it as Phishing via your email program and delete it immediately. You can also block the sender to avoid receiving further emails from this sender, however, this is usually ineffective as scammers constantly change their email addresses.
diff --git a/how-to-choose-web-designer.html b/how-to-choose-web-designer.html index 3606338..f15f1d6 100644 --- a/how-to-choose-web-designer.html +++ b/how-to-choose-web-designer.html @@ -30,7 +30,7 @@ - + @@ -50,7 +50,7 @@ - +