You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Hello,guy,there is a Incorrect access control flaws in your project.
The following is the proof of this flaws.
There are two roles in the project,permission role and super administrator role.The permission role only has the permission to change the permission of the users,and the super administrator role has all of the permissions,which contains permission management,content management,skin management.
when we use super administrator role to login in,we can see:
As the picture shows,the super administrator has three permissions.
When we use permission role to login in ,we can see:
as the picture show,the permission role has only one permission.
How is the flaws happen?
We know if the bakend controller dosen't check the permission of the role,it will cause Incorrect access control flaws.
see the code of the cmscontroller
the path of the cmscontroller is:
tianti-module-admin\src\main\java\com\jeff\tianti\controller\cmscontroller.java
In this place,we can see it use the spring framework,the request of "/column/list" map to function called columnList.It dosen't do permission check,which will cause the Incorect acess contol flaws.
How to proof it?
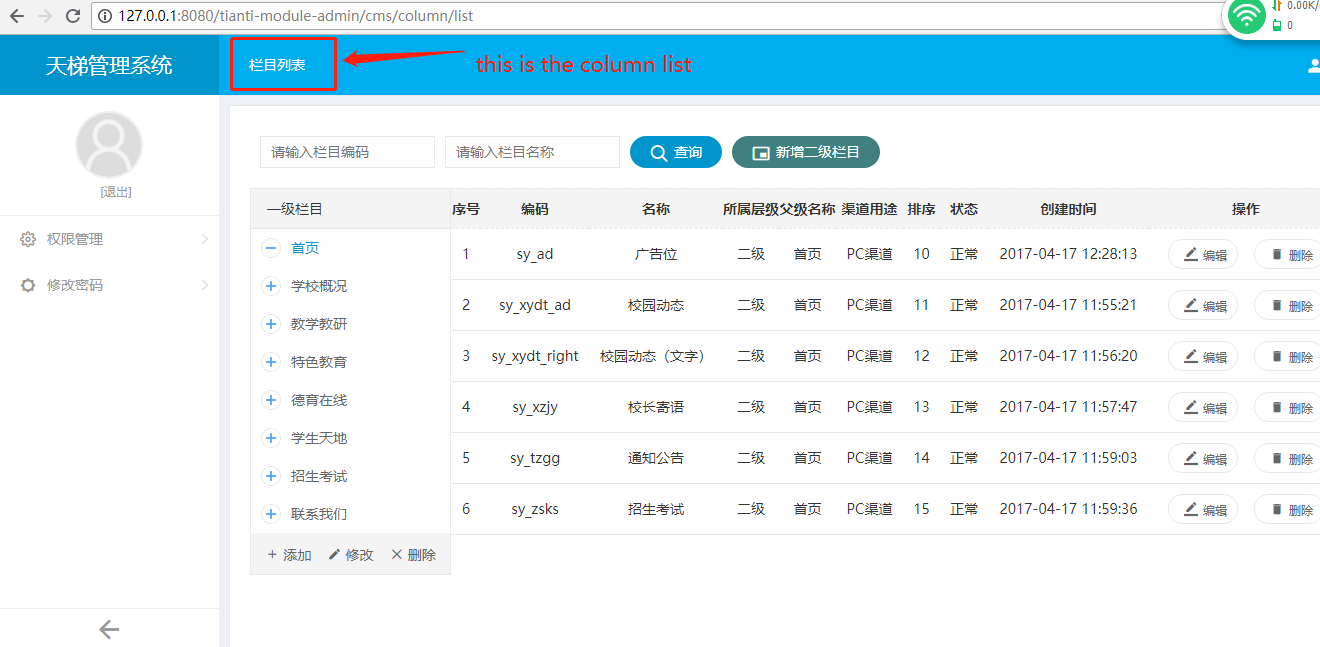
We request the url "http://127.0.0.1:8080/tianti-module-admin/cms/column/list" directly.
We can see,the permission role can access the column list page,and it can edit the column too.
And in the skin management,there exists Incorect access control,too.
We can use permission role to access the url "http://127.0.0.1:8080/tianti-module-admin/user/skin/list"
we can location the flaws code in
tianti-module-admin\src\main\java\com\jeff\tianti\controller\usercontroller.java
it map the request "/skin/list" to the function skinList,and dosen't do permission check.
Advice:
before excuting the main logic code of the function where the controller receiver the request from the frontend,please do permission check.
Hope ,you guy fix this flaws quickly ,if you have some questions,please contact me with the e-mail: 747289639@qq.com
The text was updated successfully, but these errors were encountered:
The following is the proof of this flaws.


There are two roles in the project,permission role and super administrator role.The permission role only has the permission to change the permission of the users,and the super administrator role has all of the permissions,which contains permission management,content management,skin management.
when we use super administrator role to login in,we can see:
As the picture shows,the super administrator has three permissions.
When we use permission role to login in ,we can see:
as the picture show,the permission role has only one permission.
How is the flaws happen?


We know if the bakend controller dosen't check the permission of the role,it will cause Incorrect access control flaws.
see the code of the cmscontroller
the path of the cmscontroller is:
tianti-module-admin\src\main\java\com\jeff\tianti\controller\cmscontroller.java
In this place,we can see it use the spring framework,the request of "/column/list" map to function called columnList.It dosen't do permission check,which will cause the Incorect acess contol flaws.
How to proof it?
We request the url "http://127.0.0.1:8080/tianti-module-admin/cms/column/list" directly.
We can see,the permission role can access the column list page,and it can edit the column too.
we can location the flaws code in
tianti-module-admin\src\main\java\com\jeff\tianti\controller\usercontroller.java
it map the request "/skin/list" to the function skinList,and dosen't do permission check.
Advice:

before excuting the main logic code of the function where the controller receiver the request from the frontend,please do permission check.
Hope ,you guy fix this flaws quickly ,if you have some questions,please contact me with the e-mail:
747289639@qq.com
The text was updated successfully, but these errors were encountered: