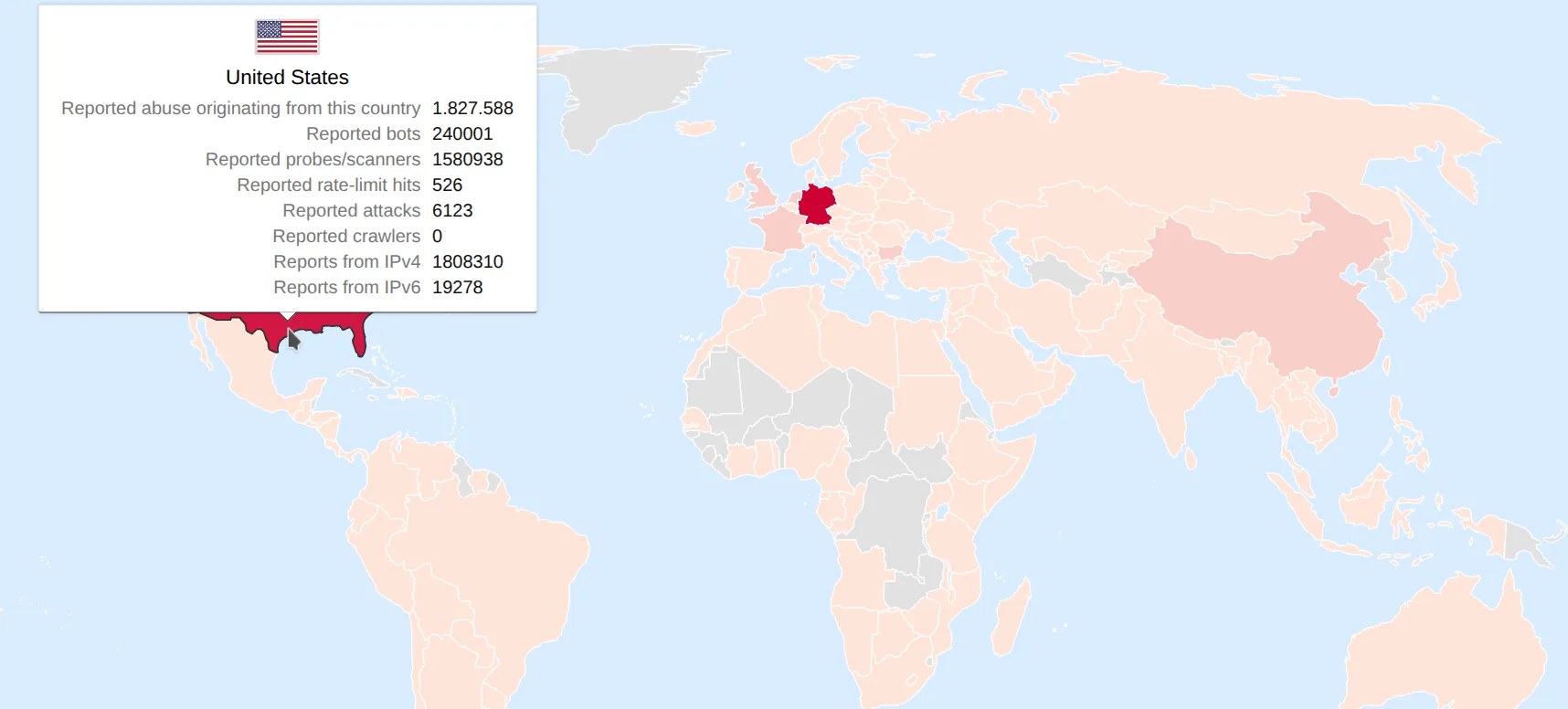
This project wants to help admins/systems flag large quantities of bad traffic.
Most generic attacks and bots originate from cloud-providers, datacenters or other providers with lax security.
By flagging clients originating from these sources you can achieve a nice security improvement.
The databases created from the gathered data will be and stay open-source!
If you (just) want to keep track of abusers internally - you could also host your dedicated instance of this app.
Contributions like reporting issues, engaging in discussions or PRs are welcome!
You SHOULD NOT just drop any requests from these sources.
There might be legit users using a VPN that would match as false-positive.
You might want to flag traffic from those sources and restrict their access like:
- Lower the rate-limits
- Show (more) captcha's on forms
- Lower lifetime of session cookies
- Add that flag to your logs so you can use it to analyze the traffic
- Deny access to administrative locations
This project is still in an early stage.
You may also want to check out these projects: (not open/free data)
Databases marked with the key all include all reports.
The ones marked with med (default) and high only include reports from reporters that have a certain level of reputation.
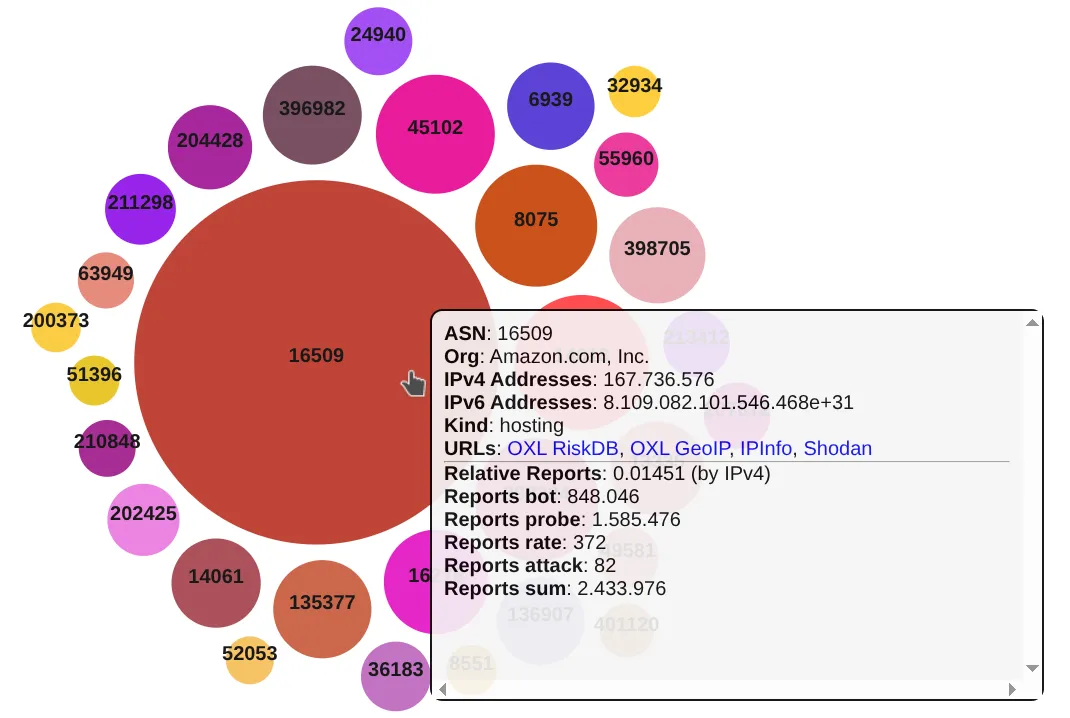
We recommend the use of our GeoIP-ASN Database and IPInfo ASN/Country Databases to get more IP-metadata
-
Reports of filtered ASN in JSON-format (only the ones tagged as hosting-, proxy- or vpn-providers)
Limits:
- Without token: 2 Downloads per IP & day
- With token: 5 Downloads per IP & day
Tip:
You can use jq to easily filter the JSON data:
- Get flat list of ASN's:
cat risk_asn_kind.json | jq 'keys[]' - Only get ASN's that are flagged a certain way:
cat risk_asn_kind.json | jq 'map_values(select(.kind.scanner == true)) | keys[]'
# check IP
curl https://risk.oxl.app/api/ip/<IP>
curl https://risk.oxl.app/api/ip/69.164.207.190
# check network
curl https://risk.oxl.app/api/net/<IP>
curl https://risk.oxl.app/api/net/205.210.31.48
# check ASN/ISP
curl https://risk.oxl.app/api/asn/<ASN>
curl https://risk.oxl.app/api/asn/16509Limits:
- 500 Requests per IP & 10 min
- 5000 Requests per IP & day
You can use our reporting API to report IPs!
# data: "ip": "<IP>", "cat": "<CATEGORY>", "cmt": "<OPTIONAL COMMENT>"
# minimal example
curl -XPOST https://risk.oxl.app/api/report --data '{"ip": "1.1.1.1", "cat": "bot"}' -H 'Content-Type: application/json'
# your reporter-reputation will be better if you add a comment (should not exceed 100 characters)
curl -XPOST https://risk.oxl.app/api/report --data '{"ip": "1.1.1.1", "cat": "attack", "cmt": "Form abuse"}' -H 'Content-Type: application/json'Available categories are: bot, probe, rate, attack, crawler, hosting, vpn, proxy
Limits:
-
Without token:
- 500 Requests per IP & 10 min
- 5000 Requests per IP & day
- Anti-DOS
-
With token:
- 5000 Requests per IP & 10 min
- Anti-DOS
If you want to get a (free) token for your systems - feel free to contact us at: risk-db@oxl.at
A simple script that follows the content of a specific log-file and parses abuser information from it.
See: Report Script
TBD
Free to use.
If you are nice, you can optionally mention that you use this IP data:
<p>IP address data powered by <a href="https://risk.oxl.app">OXL</a></p>