📣 Prerequisites • 💡 Motivation • 🎒 Exercises • 🚀 Beyond • 📚 Resources
In this workshop, participants learn how to secure Git commits using the new OpenSSH feature. This is an alternative to the traditional method of using GPG and maintaining keys which can be somewhat cumbersome.
Note This workshop was originally presented at Git Merge 2022.
- Setup workstation
- Signing and verifying commits
- Signing and verifying merges
- Signing and verifying tags
- Signing past commits and tags
- 🤔 Author opinion: Enterprise challenges
- 🪙
bitcoin/bitcoinverify-commitsTooling for verification of PGP signed commits
This is an incomplete work in progress, but currently includes a pre-push hook script (
pre-push-hook.sh) for maintainers to ensure that their own commits are PGP signed (nearly always merge commits), as well as a Python 3 script to verify commits against a trusted keys list. - 💻 andyfeller/gh-ssh-allowed-signers
A
ghextension to generate SSH allowed users file from GitHub users' signing keys. - 🎉 Vendor support
- GitHub: GA August 23rd 2022
- GitLab: In progress #343879
- BitBucket: In progress BCLOUD-3166
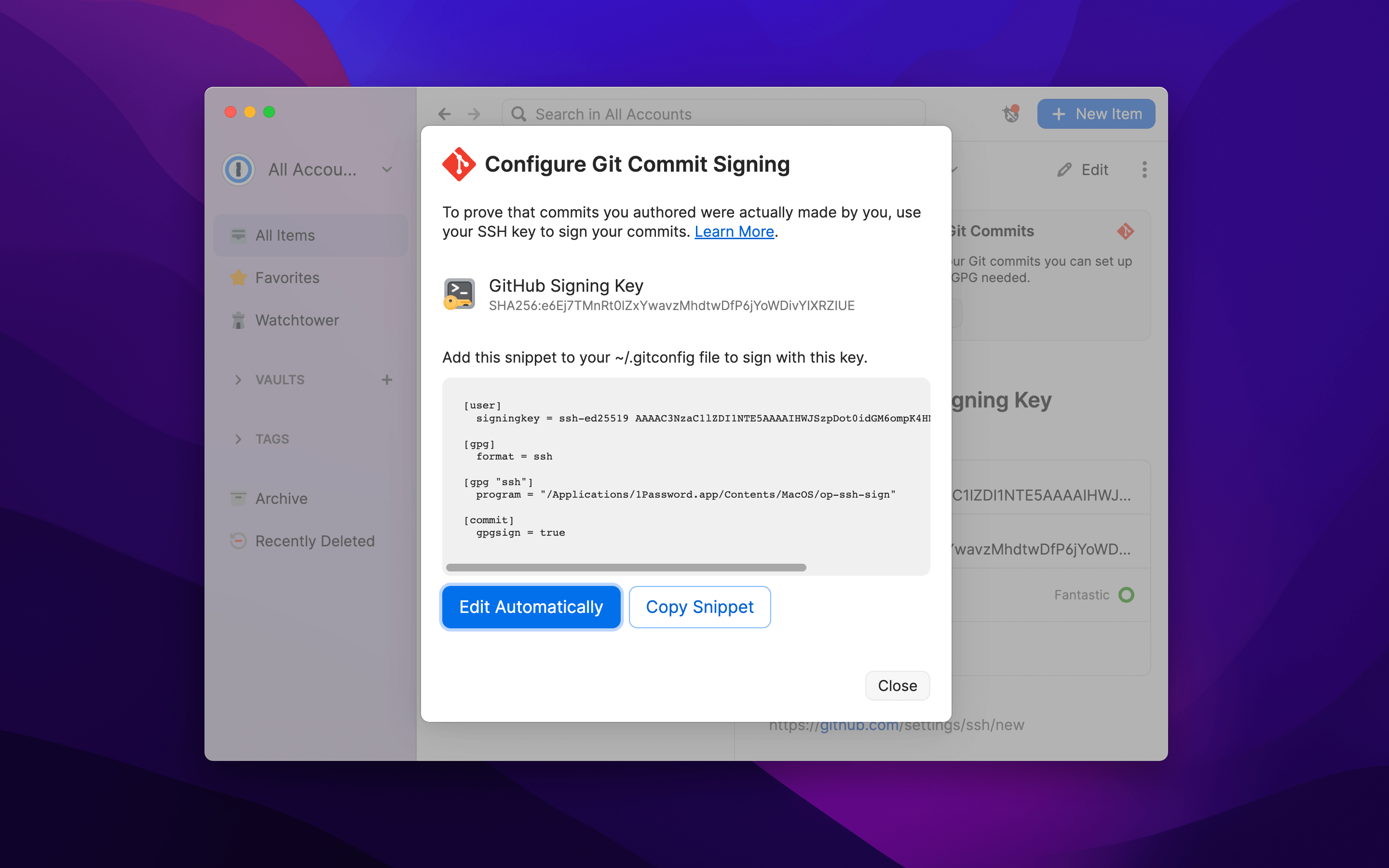
- 🔑 1password "Sign your Git commits with 1Password"
We’re excited to announce that 1Password now allows you to set up and use SSH keys to sign Git commits. And with GitHub supporting SSH key signing as well, you can get that verified badge next to your username in seconds. No GPG keys required.
- Git commands used for signing and verifying
- Git 2.34.0 release notes
This effort couldn't have happened without the support from many people, so thank you to the following who helped throughout the creation of this workshop: