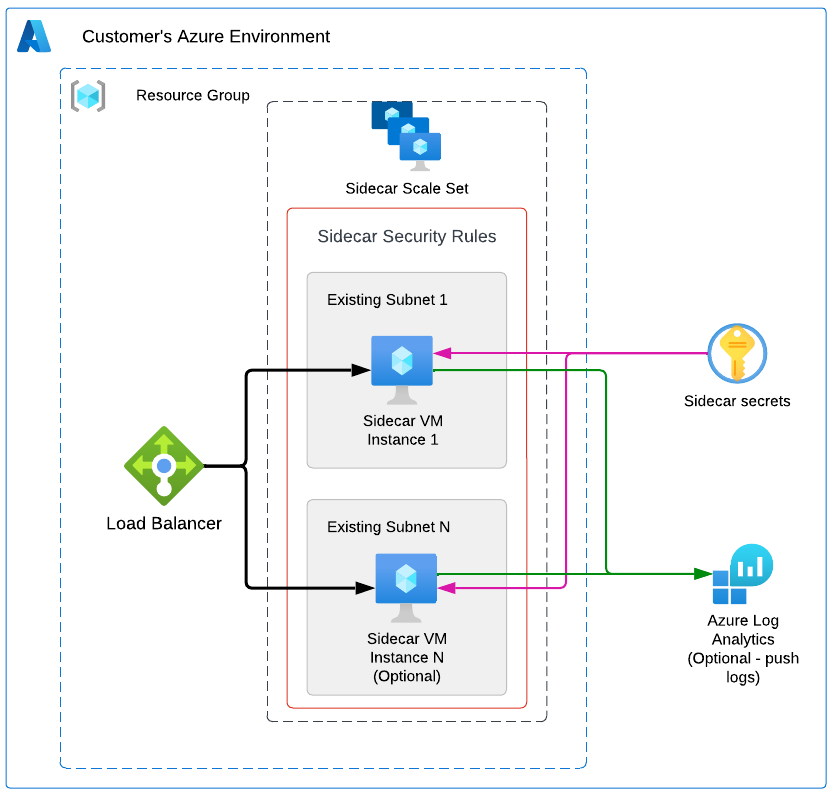
Use this Terraform module to deploy a sidecar on Azure VM instances.
Refer to the quickstart guide for more information on how to use this module or upgrade your sidecar.
The elements shown in the architecture diagram above are deployed by this module. The module requires existing VPC and subnets in order to create the necessary components for the sidecar to run. In a high-level, these are the resources deployed:
- VM
- Scale set (responsible for managing VM instances)
- Network load balancer (optional)
- Security group
- Key Vault
- Sidecar credentials
- Sidecar CA certificate
- Sidecar self-signed certificate
- IAM
- Sidecar role
- Azure Analytics
- Log group (optional)
provider "azurerm" {
# This feature is to immediately destroy secrets when `terraform destroy`
# is executed. We advise you to remove it for production sidecars.
features {
key_vault {
purge_soft_delete_on_destroy = true
}
}
}
module "cyral_sidecar" {
source = "cyralinc/sidecar-vm/azure"
version = "~> 1.0" # terraform module version
sidecar_id = ""
control_plane = ""
client_id = ""
client_secret = ""
# Leave empty if you prefer to perform upgrades directly
# from the control plane.
sidecar_version = ""
# Considering MongoDB ports are from the range 27017 to 27019
sidecar_ports = [443, 3306, 5432, 27017, 27018, 27019]
# Subnets to use to deploy VMs
subnets = [""]
# Source address prefixes for SSH into the VM instances
ssh_source_address_prefixes = ["0.0.0.0/0"]
# Source address prefixes to access ports defined in `sidecar_ports`
db_source_address_prefixes = ["0.0.0.0/0"]
# Source address prefixes to monitor the VM instances (port 9000)
monitoring_source_address_prefixes = ["0.0.0.0/0"]
# Location that will be used to deploy the resource group
# containing the sidecar resources
resource_group_location = ""
# Path to the public key that will be used to SSH into the VMs
admin_ssh_key = file("/Users/me/.ssh/id_rsa.pub")
}Note:
name_prefixis defined automatically. If you wish to define a customname_prefix, please keep in mind that its length must be at most 24 characters.
This module supports 1-click upgrade.
To enable the 1-click upgrade feature, leave the variable sidecar_version empty and upgrade
the sidecar from Cyral control plane.
If you prefer to block upgrades from the Cyral control plane and use a static version, assign
the desired sidecar version to sidecar_version. To upgrade your sidecar, update this parameter
with the target version and run terraform apply.
Learn more in the sidecar upgrade procedures page.
Instructions for advanced deployment configurations are available for the following topics:
- Bring your own secret
- Customer initialization scripts
- Memory limits
- Sidecar certificates
- Sidecar instance metrics
| Name | Version |
|---|---|
| terraform | >= 1.9 |
| azurerm | ~> 4.0 |
| Name | Version |
|---|---|
| azurerm | ~> 4.0 |
| tls | n/a |
No modules.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| admin_ssh_key | The public Key which should be used for authentication, which needs to be at least 2048-bit and in ssh-rsa format | string |
"" |
no |
| auto_scale_default | The number of instances that are available for scaling if metrics are not available for evaluation. The default is only used if the current instance count is lower than the default. Valid values are between 0 and 1000 | number |
1 |
no |
| auto_scale_enabled | Set true to enable the auto scale setting, false to disable. Only for debugging | bool |
true |
no |
| auto_scale_max | The maximum number of instances for this resource. Valid values are between 0 and 1000 | number |
2 |
no |
| auto_scale_min | The minimum number of instances for this resource. Valid values are between 0 and 1000 | number |
1 |
no |
| ca_certificate_secret_id | (Optional) Fully qualified Azure Key Vault Secret resource ID that contains CA certificate to sign sidecar-generated certs. |
string |
"" |
no |
| client_id | (Optional) The client id assigned to the sidecar. If not provided, must provide a secret containing the respective client id using secret_id." |
string |
"" |
no |
| client_secret | (Optional) The client secret assigned to the sidecar. If not provided, must provide a secret containing the respective client secret using secret_id." |
string |
"" |
no |
| container_registry | Address of the container registry where Cyral images are stored | string |
"public.ecr.aws/cyral" |
no |
| control_plane | Address of the control plane - .app.cyral.com | string |
n/a | yes |
| curl_connect_timeout | (Optional) The maximum time in seconds that curl connections are allowed to take. | number |
60 |
no |
| custom_user_data | Ancillary consumer supplied user-data script. Bash scripts must be added to a map as a value of the key pre, pre_sidecar_start, post denoting execution order with respect to sidecar installation. (Approx Input Size = 19KB) |
map(any) |
{ |
no |
| db_source_address_prefixes | Allowed CIDR blocks or IP addresses for database access to the sidecar. | set(string) |
[ |
no |
| iam_actions_role_permissions | (Optional) List of IAM role actions permissions that will be attached to the sidecar IAM role | list(string) |
[] |
no |
| iam_no_actions_role_permissions | (Optional) List of IAM role disallowed actions permissions that will be attached to the sidecar IAM role | list(string) |
[] |
no |
| iam_policies | (Optional) List of IAM policies that will be attached to the sidecar IAM role | list(string) |
[] |
no |
| idp_certificate | (Optional) The certificate used to verify SAML assertions from the IdP being used with Snowflake. Enter this value as a one-line string with literal new line characters (\n) specifying the line breaks. | string |
"" |
no |
| idp_sso_login_url | (Optional) The IdP SSO URL for the IdP being used with Snowflake. | string |
"" |
no |
| instance_os_disk_storage_account_type | The Type of Storage Account which should back this Data Disk | string |
"Standard_LRS" |
no |
| instance_type | Azure virtual machine scale set instance type for the sidecar instances | string |
"standard_ds2_v2" |
no |
| monitoring_source_address_prefixes | Allowed CIDR blocks or IP addresses for health check and metric requests to the sidecar. If restricting the access, consider setting to the Virtual Network CIDR or an equivalent to cover the assigned subnets as the load balancer performs health checks on the VM instances. |
set(string) |
[ |
no |
| name_prefix | Prefix for names of created resources. Maximum length is 24 characters | string |
"" |
no |
| public_load_balancer | Set true to add a public IP to the load balancer | bool |
false |
no |
| recycle_health_check_interval_sec | (Optional) The interval (in seconds) in which the sidecar instance checks whether it has been marked or recycling. | number |
30 |
no |
| repositories_supported | List of all repositories that will be supported by the sidecar (lower case only) | list(string) |
[ |
no |
| resource_group_location | Azure resource group location | string |
n/a | yes |
| resource_group_name | Azure resource group name | string |
"" |
no |
| secret_id | (Optional) Fully qualified Azure Key Vault Secret resource ID whereclientId and clientSecret are stored. If not provided, willautomatically create a secret storing the values in variables client_id and client_secret. |
string |
"" |
no |
| sidecar_id | Sidecar identifier | string |
n/a | yes |
| sidecar_ports | List of ports allowed to connect to the sidecar | list(number) |
n/a | yes |
| sidecar_private_idp_key | (Optional) The private key used to sign SAML Assertions generated by the sidecar. Enter this value as a one-line string with literal new line characters ( ) specifying the line breaks. |
string |
"" |
no |
| sidecar_public_idp_certificate | (Optional) The public certificate used to verify signatures for SAML Assertions generated by the sidecar. Enter this value as a one-line string with literal new line characters ( ) specifying the line breaks. |
string |
"" |
no |
| sidecar_version | Version of the sidecar | string |
"" |
no |
| source_image_offer | Specifies the offer of the image used to create the virtual machines | string |
"ubuntu-24_04-lts" |
no |
| source_image_publisher | Specifies the publisher of the image used to create the virtual machines | string |
"Canonical" |
no |
| source_image_sku | Specifies the SKU of the image used to create the virtual machines | string |
"server" |
no |
| source_image_version | Specifies the version of the image used to create the virtual machines | string |
"latest" |
no |
| ssh_source_address_prefixes | Source address prefixes that will be able to reach the instances using SSH | set(string) |
[ |
no |
| subnets | Subnets to add sidecar to (list of string) | list(string) |
n/a | yes |
| tls_certificate_secret_id | (Optional) Fully qualified Azure Key Vault Secret resource ID that contains a certificate to terminate TLS connections." |
string |
"" |
no |
| tls_skip_verify | (Optional) Skip TLS verification for HTTPS communication with the control plane and during sidecar initialization | bool |
false |
no |
| vm_username | Virtual machine user name | string |
"ubuntu" |
no |
| Name | Description |
|---|---|
| ca_certificate_secret_id | ID of the CA certificate secret used sidecar. |
| load_balancer_dns | Sidecar load balancer DNS endpoint. |
| load_balancer_id | ID of the load balancer. |
| log_analytics_workspace_id | Azure Log Analytics workspace ID. |
| log_analytics_workspace_primary_shared_key | Azure Log Analytics primary shared key. |
| log_analytics_workspace_secondary_shared_key | Azure Log Analytics secondary shared key. |
| resource_group_name | Azure resource group name that the sidecar belongs to. |
| secret_id | ID of the secret with the credentials used by the sidecar |
| tls_certificate_secret_id | ID of the TLS certificate secret used by the sidecar |
| user_assigned_identity_name | Name of the User Assigned Identity used by the sidecar |