-
Notifications
You must be signed in to change notification settings - Fork 4
docs: cost-visibility doc #149
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Draft
Hii-Arpit
wants to merge
39
commits into
devtron-labs:main
Choose a base branch
from
Hii-Arpit:cost-visibility
base: main
Could not load branches
Branch not found: {{ refName }}
Loading
Could not load tags
Nothing to show
Loading
Are you sure you want to change the base?
Some commits from the old base branch may be removed from the timeline,
and old review comments may become outdated.
Draft
Changes from all commits
Commits
Show all changes
39 commits
Select commit
Hold shift + click to select a range
467fd43
added a file
Hii-Arpit 8b5a275
docs: intr added
Hii-Arpit 50432b7
Merge branch 'main' of https://github.com/Hii-Arpit/devtron-documenta…
Hii-Arpit 5d330d8
Merge branch 'main' of https://github.com/Hii-Arpit/devtron-documenta…
Hii-Arpit 69635a9
Merge branch 'main' of https://github.com/Hii-Arpit/devtron-documenta…
Hii-Arpit dbf0514
test
Hii-Arpit d4b130a
docs: test-reversed
Hii-Arpit c732a94
docs: mid commit
Hii-Arpit 66d7a63
Merge branch 'main' of https://github.com/Hii-Arpit/devtron-documenta…
Hii-Arpit ec2c919
docs: overview page fixes
Hii-Arpit c7e980d
docs: added cost breakdown
Hii-Arpit 2d39247
Merge branch 'main' of https://github.com/Hii-Arpit/devtron-documenta…
Hii-Arpit a627374
docs: fixes
Hii-Arpit ff333d3
docs: structure changed
Hii-Arpit 9d447d7
docs: added configurations
Hii-Arpit f3798b2
docs: added custom views
Hii-Arpit 7164b86
docs: added supademos
Hii-Arpit b118b24
docs: added Readme.md
Hii-Arpit bc7bd81
docs: fixes
Hii-Arpit c3babe8
docs: added images and some fixes
Hii-Arpit ae18ca0
docs: added use cases and examples
Hii-Arpit ec05c63
docs: added application overview
Hii-Arpit b682ea3
docs: added more sections and application overview
Hii-Arpit 998f11b
docs: added infrastructure overview
Hii-Arpit fe0639d
docs: implement changes
Hii-Arpit 82eb3f3
docs: added supademos
Hii-Arpit 6dc4ceb
docs: supademo position changes
Hii-Arpit 2490e8f
docs: implemented changes
Hii-Arpit 93b5bf9
docs: replaced supademos
Hii-Arpit 46d0509
docs: implemented changes
Hii-Arpit 618bc43
docs: minor fix
Hii-Arpit c03fc0e
docs: minor fixes
Hii-Arpit b07676a
docs: changes implemented over the call
Hii-Arpit 0eb415b
docs: changes implemented over the call part 2
Hii-Arpit 3fc4709
docs: changes implemented over the call part 3
Hii-Arpit dc6b9d7
docs: fixed Faqs
Hii-Arpit 62263c2
docs: fixed links
Hii-Arpit 10e0a06
docs: added some hintblocks and fixes
Hii-Arpit a685c02
docs: added enterprise tagging
Hii-Arpit File filter
Filter by extension
Conversations
Failed to load comments.
Loading
Jump to
Jump to file
Failed to load files.
Loading
Diff view
Diff view
There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,12 @@ | ||
| # Cost Visibility | ||
| ## Introduction [](https://devtron.ai/pricing) | ||
|
|
||
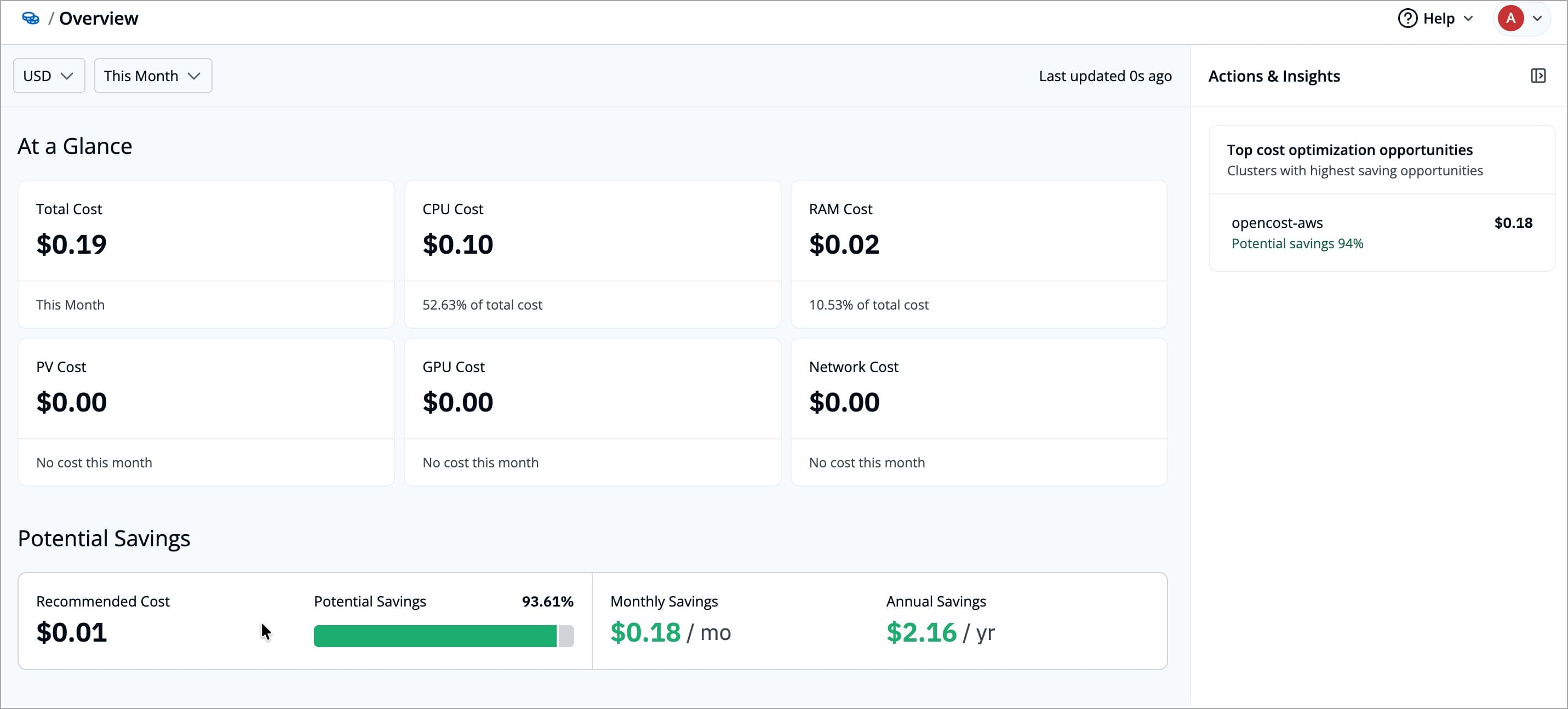
| Cost Visibility in Devtron provides a unified view of your Kubernetes infrastructure costs within the Devtron dashboard. It eliminates the need to switch between cloud provider billing consoles by integrating cost insights directly into your DevOps workflow. | ||
|
|
||
|  | ||
|
|
||
| You can view and analyze costs across multiple scopes such as Clusters, Projects, Environments, Applications, and Infrastructure Resources. Devtron automatically tracks the spend on CPU, Memory, Storage, GPU, and Network, giving you a clear picture of how resources are utilized and what contributes most to your total cost. | ||
|
|
||
| The dashboard highlights recommended costs and potential savings, helping you identify underutilized resources and opportunities for optimization. | ||
|
|
||
| You can choose your preferred currency to view all cost data consistently across different time periods, such as daily, monthly, quarterly, or custom ranges. This helps you move seamlessly from a high-level overview to a granular analysis of costs within a specific category. |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,311 @@ | ||
| # Configurations | ||
|
|
||
| The **Configurations** page lets you manage configurations for Cost Visibility in Devtron. You can: | ||
|
|
||
| * Set the default currency for all cost-related data. | ||
| * Enable or disable cost tracking for your connected clusters. | ||
|
|
||
| --- | ||
|
|
||
| ## Currency (Default) | ||
|
|
||
| You can select your preferred currency as default. | ||
|
|
||
| --- | ||
|
|
||
| ## Enable Cost Tracking | ||
|
|
||
| To enable cost visibility for a cluster, follow the below steps: | ||
|
|
||
| 1. Choose your preferred cluster, and click on **Off/Enabled**. An **Edit Cluster** modal window will open. | ||
|
|
||
| 2. Enable the toggle next to **Enable cost tracking**. | ||
|
|
||
| 3. Select the cloud provider in which you have created your cluster. | ||
|
|
||
| 4. Based on the cloud provider you need to do the following configurations: | ||
|
|
||
| {% tabs %} | ||
|
|
||
| {% tab title="GCP" %} | ||
|
|
||
| ### Enable Cost Visibility for GCP | ||
|
|
||
| To enable cost visibility for Google Cloud in Devtron, you need to generate an API key and use it to connect Devtron with your GCP account. | ||
|
|
||
| 1. Generate the API key using standard [Google Cloud API key documentation](https://cloud.google.com/docs/authentication/api-keys#gcloud). | ||
|
|
||
| 2. Now go back to the **Edit cluster** modal window, and enter the API key in the **Cloud Provider API Key** field. | ||
|
|
||
| {% hint style="info" %} | ||
| If you face any issues while enabling or configuring the **Cost Visibility** module, reach out to [Devtron Support Team](mailto:enterprise@devtron.ai) for assistance. | ||
| {% endhint %} | ||
|
|
||
| {% endtab %} | ||
|
|
||
| {% tab title="Azure" %} | ||
|
|
||
| ### Enable Cost Visibility for Azure | ||
|
|
||
| To enable cost visibility for your Azure clusters in Devtron, you need to allow Devtron to access your billing data securely. This requires two steps: | ||
| 1. Create a custom role in Azure with billing access. | ||
| 2. Create a service principal (an identity) that Devtron can use to fetch cost details. | ||
|
|
||
| ### Step 1: Creating Custom Role | ||
|
|
||
| 1. Open a text editor and copy the following JSON: | ||
|
|
||
| ```json | ||
| { | ||
| "Name": "OpenCostRole", | ||
| "IsCustom": true, | ||
| "Description": "Rate Card query role", | ||
| "Actions": [ | ||
| "Microsoft.Compute/virtualMachines/vmSizes/read", | ||
| "Microsoft.Resources/subscriptions/locations/read", | ||
| "Microsoft.Resources/providers/read", | ||
| "Microsoft.ContainerService/containerServices/read", | ||
| "Microsoft.Commerce/RateCard/read" | ||
| ], | ||
| "AssignableScopes": [ | ||
| "/subscriptions/YOUR_SUBSCRIPTION_ID" | ||
| ] | ||
| } | ||
| ``` | ||
|
|
||
| 2. Replace `YOUR_SUBSCRIPTION_ID` with your actual subscription ID. | ||
|
|
||
| 3. Save the file as `myrole.json`. | ||
|
|
||
| 4. Run the following command in your terminal: | ||
|
|
||
| ```bash | ||
| az role definition create --verbose --role-definition @myrole.json | ||
| ``` | ||
|
|
||
| This creates a role called `OpenCostRole` with just enough access to read pricing information. | ||
|
|
||
| ### Step 2: Create a Service Principal | ||
|
|
||
| 1. Run the command below, again replacing `YOUR_SUBSCRIPTION_ID` with your subscription ID: | ||
|
|
||
| ```bash | ||
| az ad sp create-for-rbac \ | ||
| --name "OpenCostAccess" \ | ||
| --role "OpenCostRole" \ | ||
| --scope "/subscriptions/YOUR_SUBSCRIPTION_ID" \ | ||
| --output json | ||
| ``` | ||
|
|
||
| 2. You’ll get an output like this: | ||
|
|
||
| ```json | ||
| { | ||
| "appId": "1d9b1532-abe4-4e08-b172-adfa5384da1", | ||
| "displayName": "OpenCostAccess", | ||
| "password": "3DZ8Q~KOE.WgdmmRkBHg3dF1rfrpFhSPk.Hnb4-", | ||
| "tenant": "aee9b2ed-7ecc-4cb2-bfed-60d71c0e957" | ||
| } | ||
| ``` | ||
|
|
||
| 3. Note this information as you need to enter this in Devtron. | ||
|
|
||
| ### Step 3: Enter Details in Devtron | ||
|
|
||
| Now go back to the **Edit cluster** modal window, and fill the following fields: | ||
|
|
||
| | **Field** | **Value to Provide** | | ||
| |---------------------|---------------------------------| | ||
| | Subscription ID | Your Azure subscription ID | | ||
| | App ID | Value of `appId` from the output | | ||
| | Display Name | Value of `displayName` from the output| | ||
| | Password | Value of `password` from the output | | ||
| | Tenant | Value of `tenant` from the output | | ||
| | Billing Account | Optional (fill if available) | | ||
| | Offer ID | Optional (fill if available) | | ||
|
|
||
| {% hint style="info" %} | ||
| If you face any issues while enabling or configuring the **Cost Visibility** module, reach out to [Devtron Support Team](mailto:enterprise@devtron.ai) for assistance. | ||
| {% endhint %} | ||
|
|
||
| {% endtab %} | ||
|
|
||
| {% tab title="AWS" %} | ||
|
|
||
| ### Enable Cost Visibility for AWS | ||
|
|
||
| If you have spot node instances in your AWS cluster, then only you need to do the below additional configurations for your AWS cluster, else you can skip the below configurations | ||
|
|
||
| ### Step 1: Set up a Spot Instance Data Feed | ||
|
|
||
| 1. Create an S3 bucket | ||
|
|
||
| 2. Assign full access permissions to the AWS Spot Data Feed service | ||
|
|
||
| ```json | ||
| { | ||
| "Version": "2012-10-17", | ||
| "Statement": [ | ||
| { | ||
| "Effect": "Allow", | ||
| "Principal": { | ||
| "Service": "spot.amazonaws.com" | ||
| }, | ||
| "Action": "*", | ||
| "Resource": "arn:aws:s3:::devtron-spot-feed/*" | ||
| }, | ||
| { | ||
| "Effect": "Allow", | ||
| "Principal": { | ||
| "Service": "spot.amazonaws.com" | ||
| }, | ||
| "Action": "*", | ||
| "Resource": "arn:aws:s3:::devtron-spot-feed" | ||
| } | ||
| ] | ||
| } | ||
| ``` | ||
|
|
||
| 3. Run the following command to subscribe to the data feed using the AWS CLI | ||
|
|
||
| ```bash | ||
| aws ec2 create-spot-datafeed-subscription \ | ||
| --bucket devtron-spot-feed --prefix cost | ||
| ``` | ||
| {% hint style="warning" %} | ||
| ### Note | ||
| You can subscribe to the Spot Data Feed for only one S3 bucket at a time. Running the command again updates the feed to the latest bucket.{% endhint %} | ||
|
|
||
|
|
||
| ### Step 2: Create an IAM Role or Use Access Keys | ||
|
|
||
| You can connect Devtron to AWS cost data using either of the following methods: | ||
|
|
||
| #### IAM Role (Recommended) | ||
|
|
||
| Create a Web Identity IAM role for your EKS/EC2 cluster with permissions to access the Spot Data Feed bucket. Attach the following policy (replace CHANGE-ME with your bucket name) | ||
|
|
||
| ```json | ||
| { | ||
| "Version": "2012-10-17", | ||
| "Statement": [ | ||
| { | ||
| "Action": [ | ||
| "s3:ListAllMyBuckets", | ||
| "s3:ListBucket", | ||
| "s3:Get*" | ||
| ], | ||
| "Resource": [ | ||
| "arn:aws:s3:::CHANGE-ME", | ||
| "arn:aws:s3:::CHANGE-ME/*" | ||
| ], | ||
| "Effect": "Allow" | ||
| } | ||
| ] | ||
| } | ||
|
|
||
| ``` | ||
|
|
||
| #### Access Keys (Alternative) | ||
|
|
||
| Provide an Access Key and Secret Key with permissions `s3:ListBucket` and `s3:GetObject` for the Spot Data Feed bucket. | ||
|
|
||
| ### Step 3: Configure in Devtron | ||
|
|
||
| Now go back to the **Edit cluster** modal window, and fill the following fields: | ||
|
|
||
| | **Field** | **Description** | | ||
| |-----------------------|---------------------------------------------------------------------------------| | ||
| | Spot Data Bucket | Name of the S3 bucket storing Spot Instance Data Feed | | ||
| | Spot Data Region | AWS region of the Spot Data Feed | | ||
| | Spot Data Prefix | Prefix (if any) used for the Spot Data Feed | | ||
| | Project ID | Your AWS Account ID | | ||
| | Access Key | (Optional) AWS Access Key with S3 read permissions | | ||
| | Secret Access Key | (Optional) AWS Secret Access Key with S3 read permissions | | ||
| | IAM Role | (Recommended) IAM role ARN assigned to the EKS/EC2 cluster for bucket access | | ||
|
|
||
| {% endtab %} | ||
|
|
||
| {% endtabs %} | ||
|
|
||
| 5. Enter Prometheus endpoint of your cluster. Refer [Fetching Prometheus Endpoint](#fetching-prometheus-endpoint) to learn more. | ||
|
|
||
| {% hint style="warning" %} | ||
| Prometheus endpoint should be publicly exposed for the cost visibility to work. | ||
| {% endhint %} | ||
|
|
||
| 6. Click **Save**, cost visibility will be enabled for the cluster. | ||
|
|
||
| {% hint style="warning"%} | ||
| ### Note | ||
| After enabling cost visibility, you will see your cluster information after 1 hour in cost visibility module. | ||
| {% endhint %} | ||
|
|
||
| ### Fetching Prometheus Endpoint | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Note | ||
| Ensure [GitOps](../global-configurations/gitops.md) is configured before deploying Prometheus. If not, Prometheus will default to being deployed via Helm. | ||
| {% endhint %} | ||
|
|
||
| #### Installing Prometheus | ||
|
|
||
| 1. Go to the **Chart Store** and search for `prometheus`. Use the Prometheus community's `kube-prometheus-stack` chart to deploy Prometheus. | ||
|
|
||
|  | ||
|
|
||
| 2. After selecting the chart, configure these values as needed before deployment. | ||
|
|
||
| ```yaml | ||
| kube-state-metrics: | ||
| metricLabelsAllowlist: | ||
| - pods=[*] | ||
| ``` | ||
|
|
||
| <br /> | ||
|
|
||
| ```yaml | ||
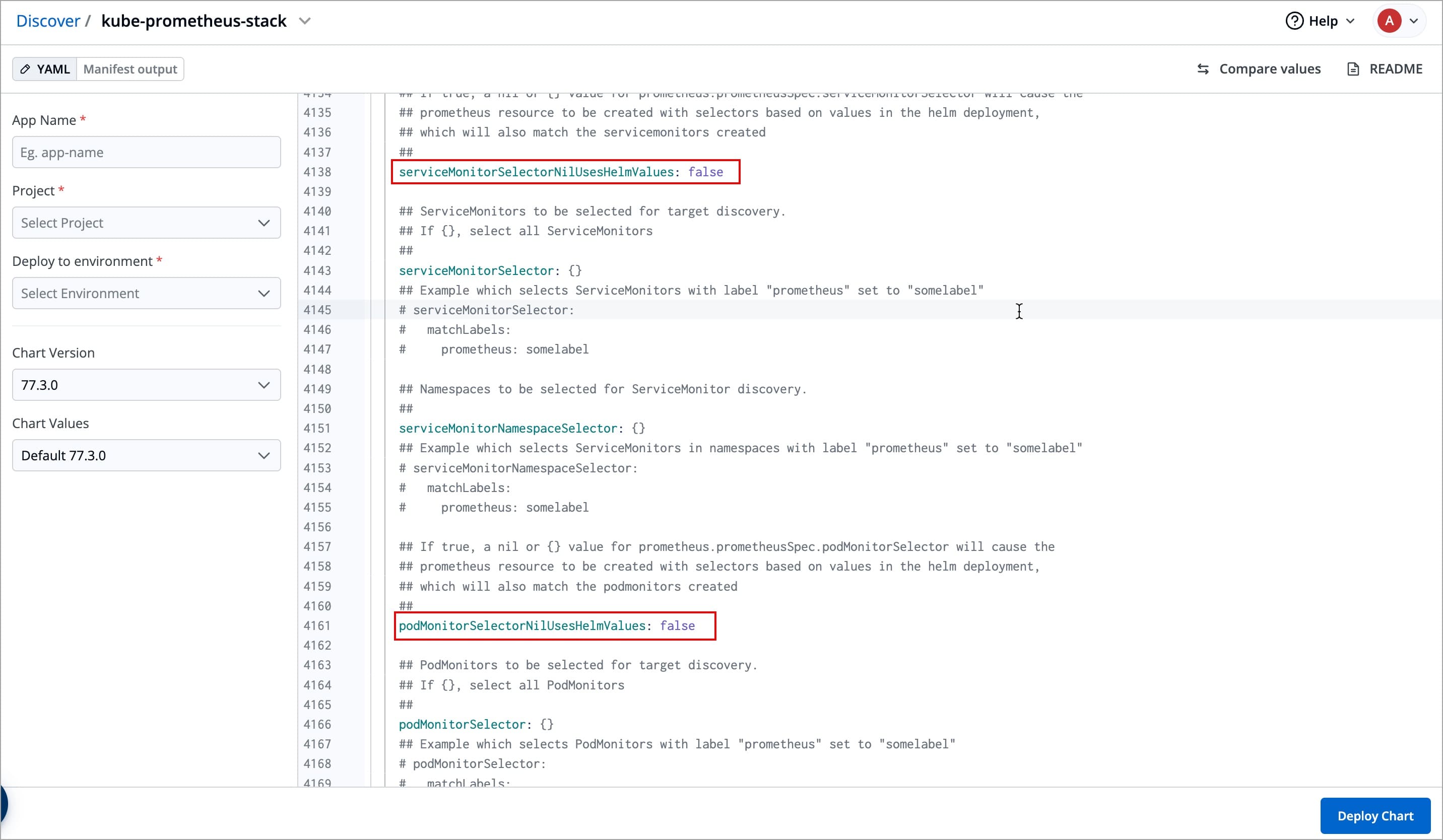
| serviceMonitorSelectorNilUsesHelmValues: false | ||
| podMonitorSelectorNilUsesHelmValues: false | ||
| ``` | ||
|
|
||
| <br /> | ||
|
|
||
| Search for the above parameters, and update them as shown (or customize as needed). | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| 3. Enable `upgradeJob` parameter to install CRDs: | ||
|
|
||
| Since Helm does not automatically apply CRDs, you need to enable the `upgradeJob` parameter in the Helm chart to ensure CRDs are applied before deploying Prometheus. | ||
|
|
||
| In the Prometheus Helm chart settings, locate the `upgradeJob` parameter and set it to `true` if it is `false`. | ||
|
|
||
|  | ||
|
|
||
| 4. After enabling the parameter, click **Deploy Chart**. | ||
|
|
||
| {% hint style="warning" %} | ||
| ### Common Pitfall: Prometheus Deployment Timeout due to Failed CRDs | ||
|
|
||
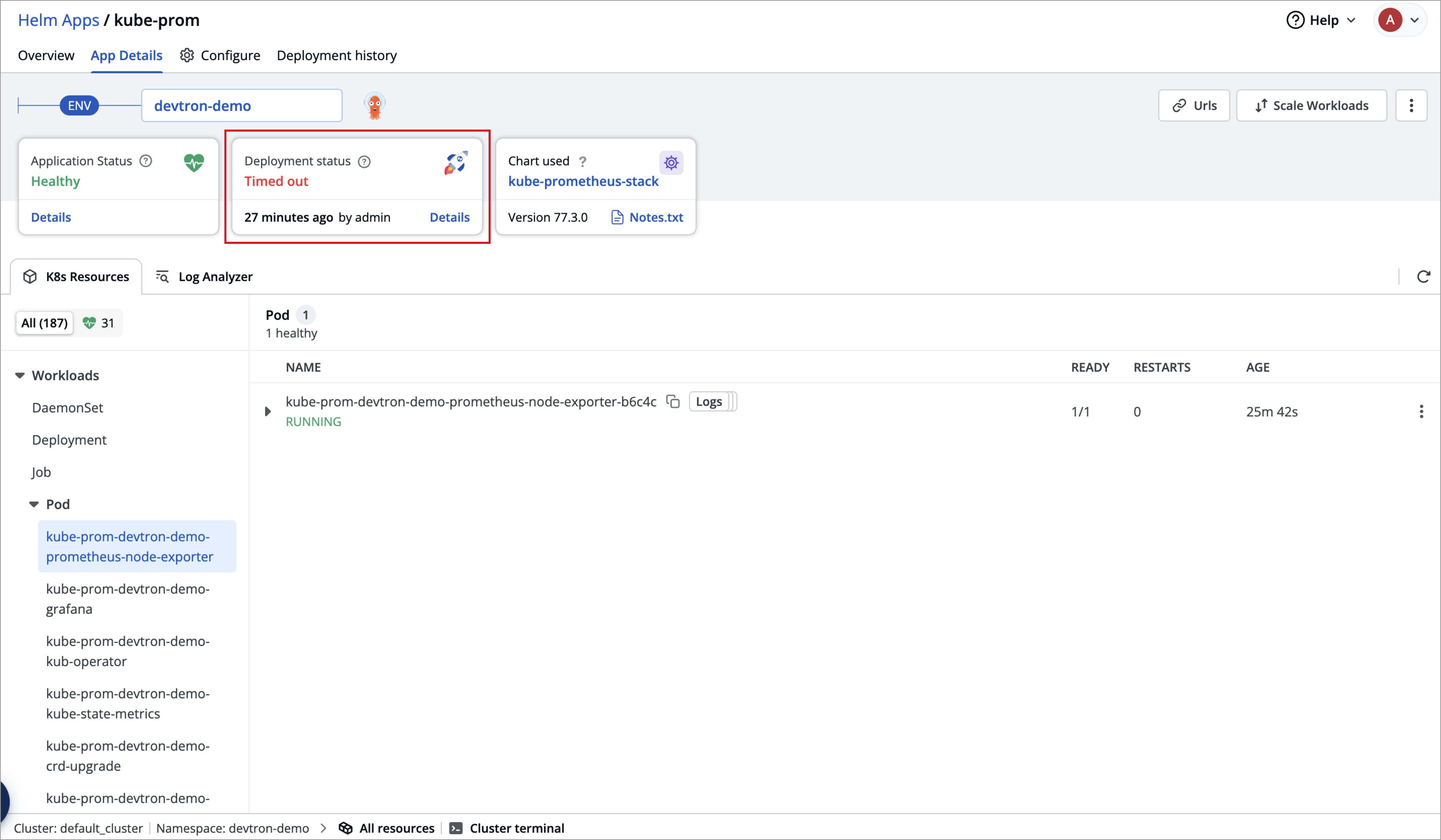
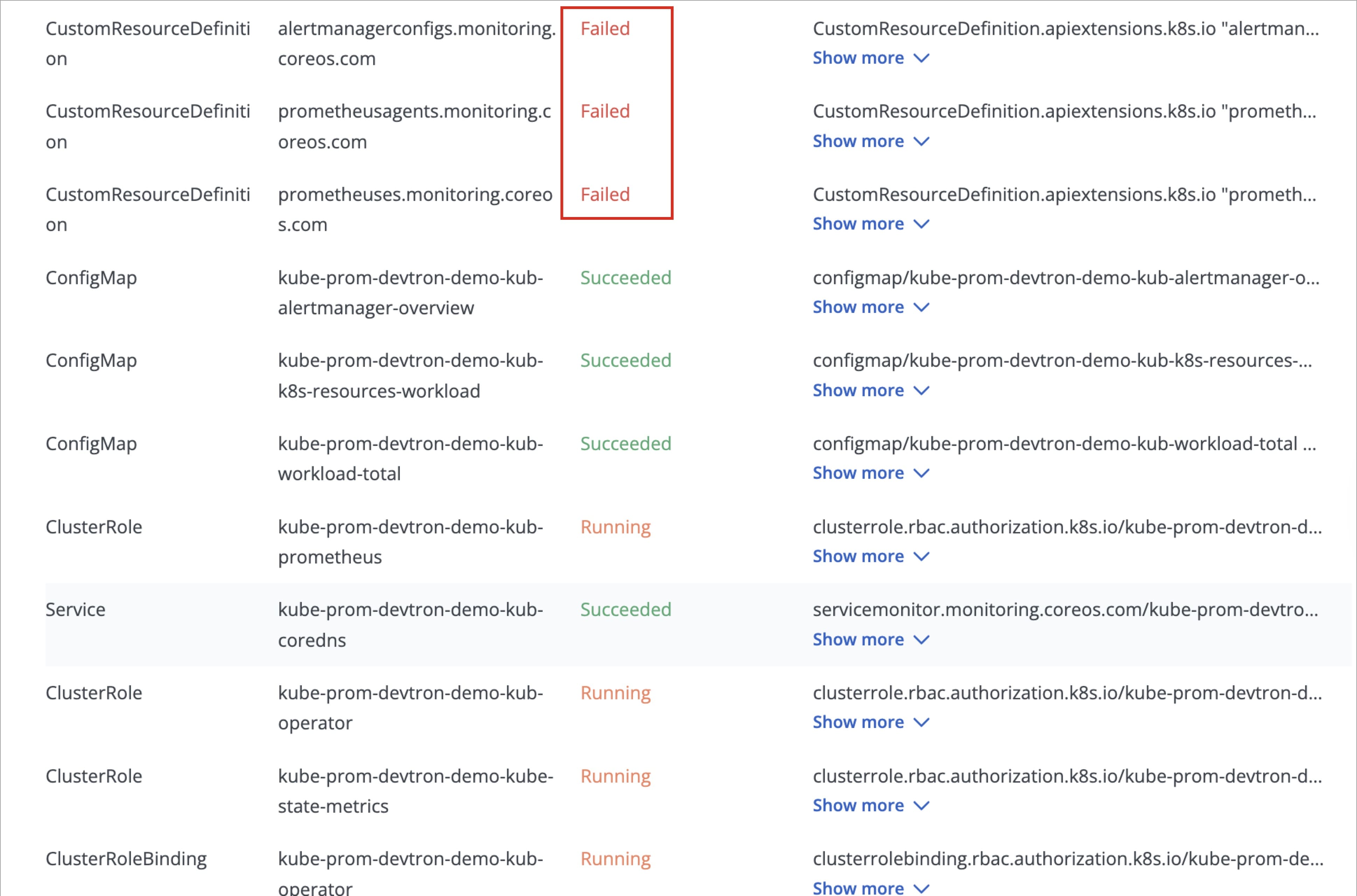
| While deploying `kube-prometheus-stack` chart, the deployment status may show as **Timed out**, and some CustomResourceDefinitions (CRDs) may appear as **Failed**. | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| **This behavior is expected and do not require any action from you.** | ||
|
|
||
| This occurs because certain Prometheus CRDs are large in size, which can lead to temporary sync issues during deployment, but, this does not impact the functionality of the Prometheus components. | ||
|
|
||
| ArgoCD handles such cases automatically and the `kube-prometheus-stack` will continue to function as expected. | ||
|
|
||
| {% endhint %} | ||
|
|
||
| 5. After the chart deployed successfully, you need to make the Prometheus endpoint exposed publicly. | ||
|
|
||
| {% hint style="info" %} | ||
| If you face any issues while enabling or configuring the **Cost Visibility** module, please contact the [Devtron Support Team](mailto:enterprise@devtron.ai) for assistance. | ||
| {% endhint %} | ||
Oops, something went wrong.
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
Uh oh!
There was an error while loading. Please reload this page.