The goal of this assignment was to create a WordPress server to find and exploit vulnerabilities. Through Vagrant I successfully created a working server with an IP of 192.168.33.100 which was reachable by my Kali Linux machine.
Several attacks could be discovered such as:
- XSS
- SLQI
- User Enumeration
- Privilege Escalation
Admin rights were previously granted by Codepath. After logging into the admin panel, I started tinkering with some of the settings to see how WordPress works. I noticed that there was a section to create users so I created two users, Tom Riddle & Harry Potter.
Before logging out I tested for any Insecure Direct Object Reference (IDOR) on url http://wpdistillery.vm/wp-login.php? but it was unsuccessful. Whilst researching I learned about two WordPress vulnerability scanners, WPScan & WPSekku.
WPScan was used with the following commands and parameters:
wpscan --url 192.168.33.10 -e u, vp --api-token KTpzJJ3dlGP1tLHsDh3g19bmMmIAx3jF35B1lDO0lw8Parameters legend:
-e u Enumerate Users
-vp Plugins
--api-token An API token was required before the scan, said token can be obtained by registering on wpscan.com. The scan returned several vulnerabilities and at the bottom, it found the users I had recently created.
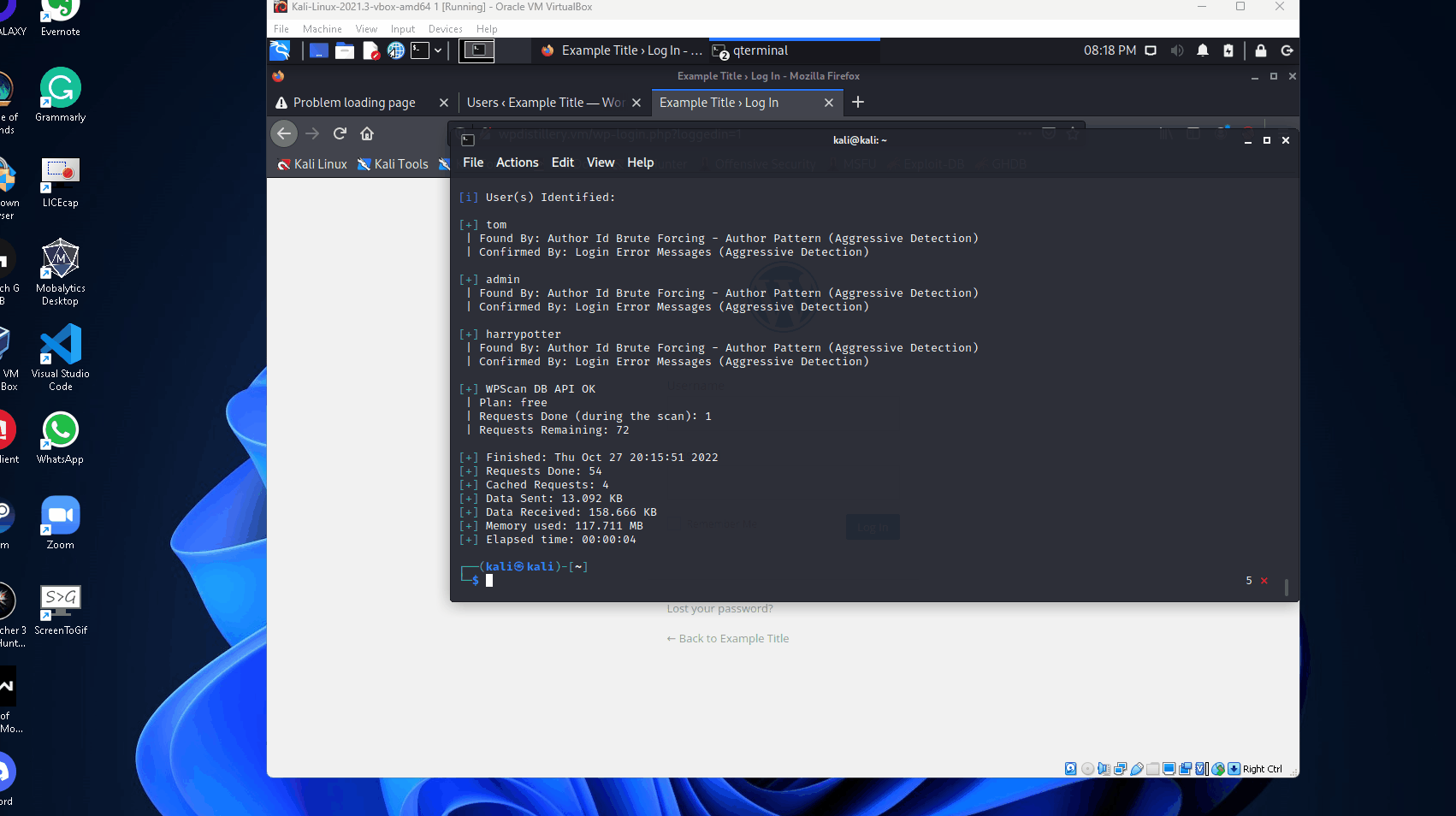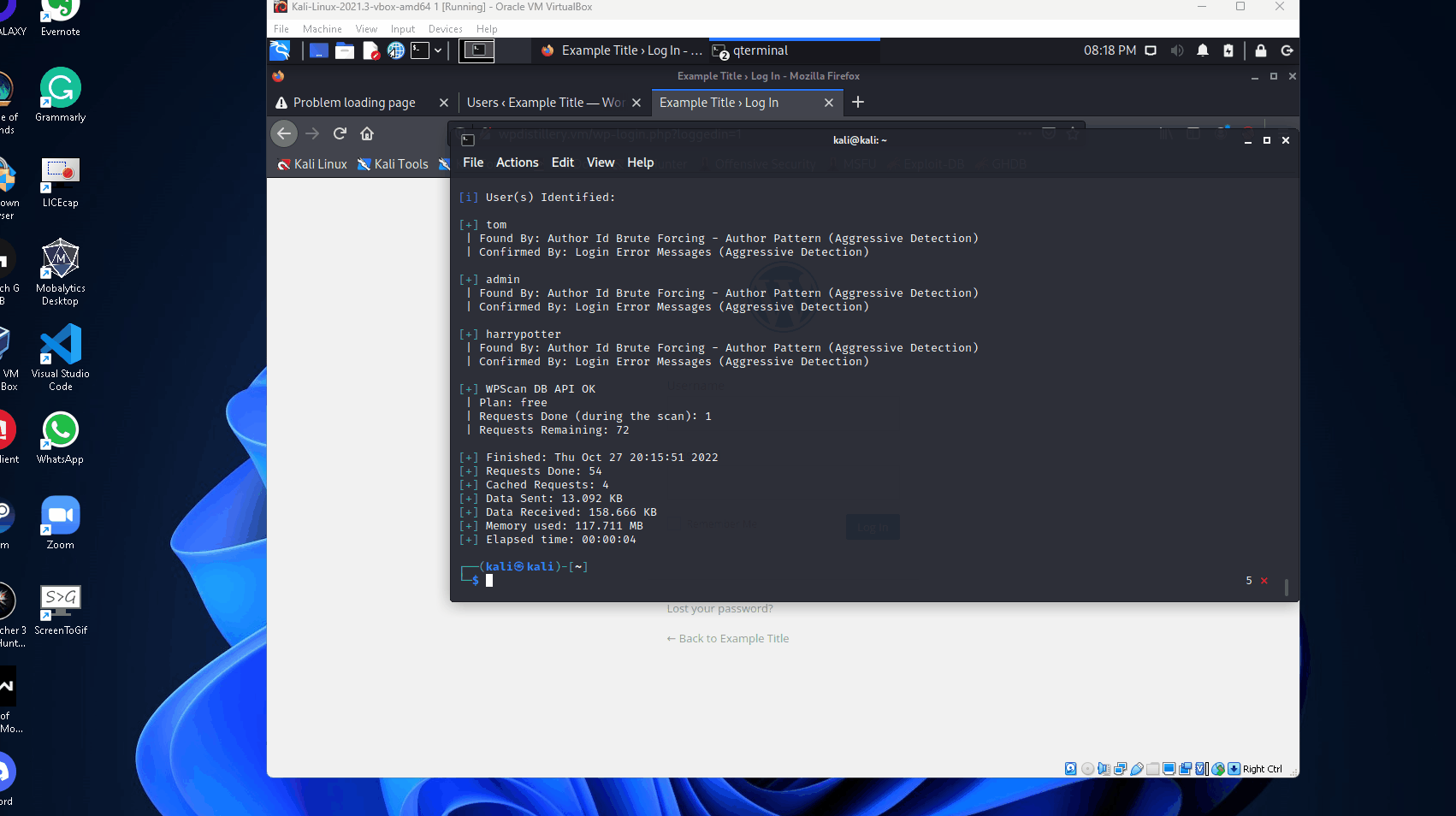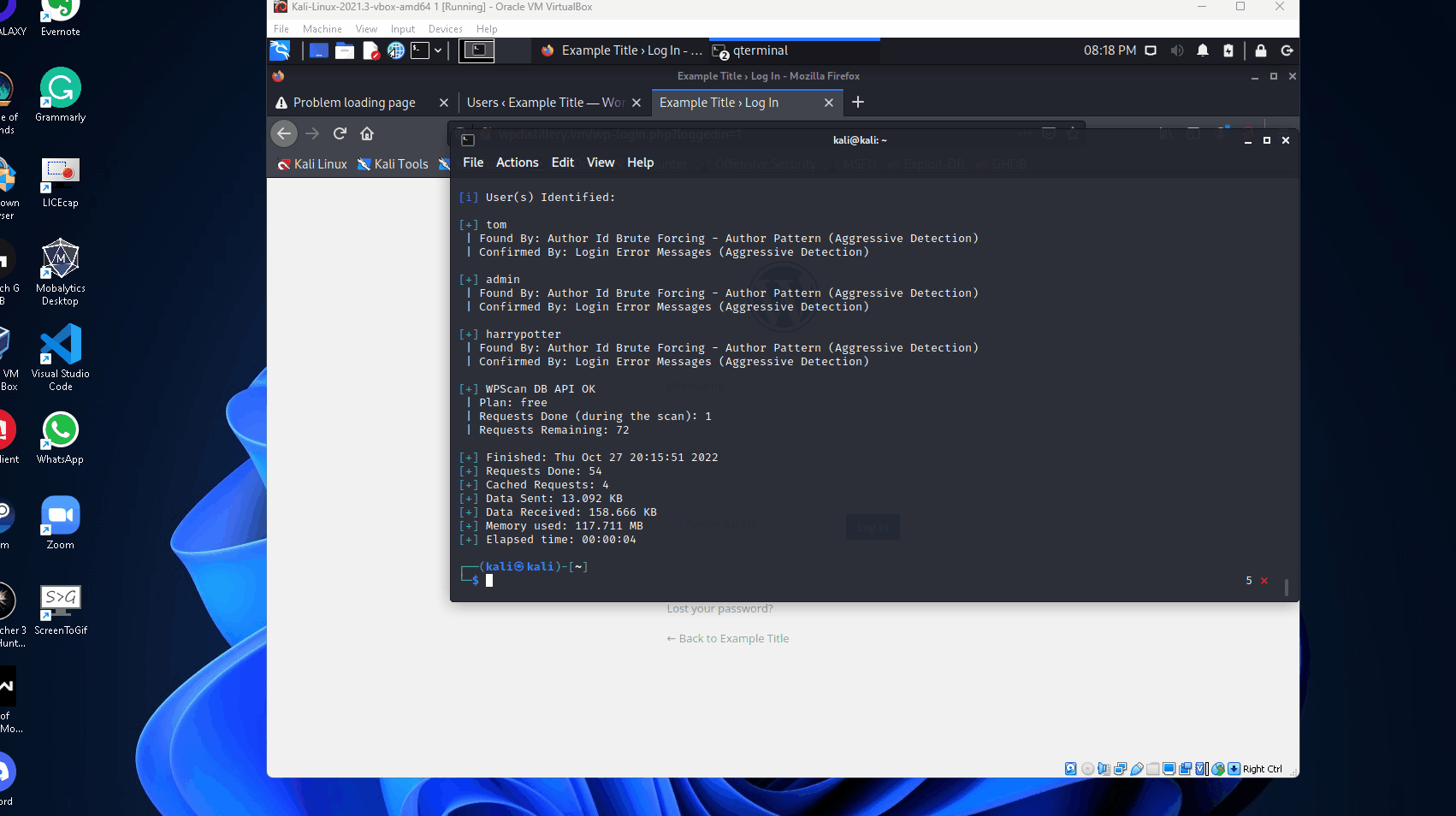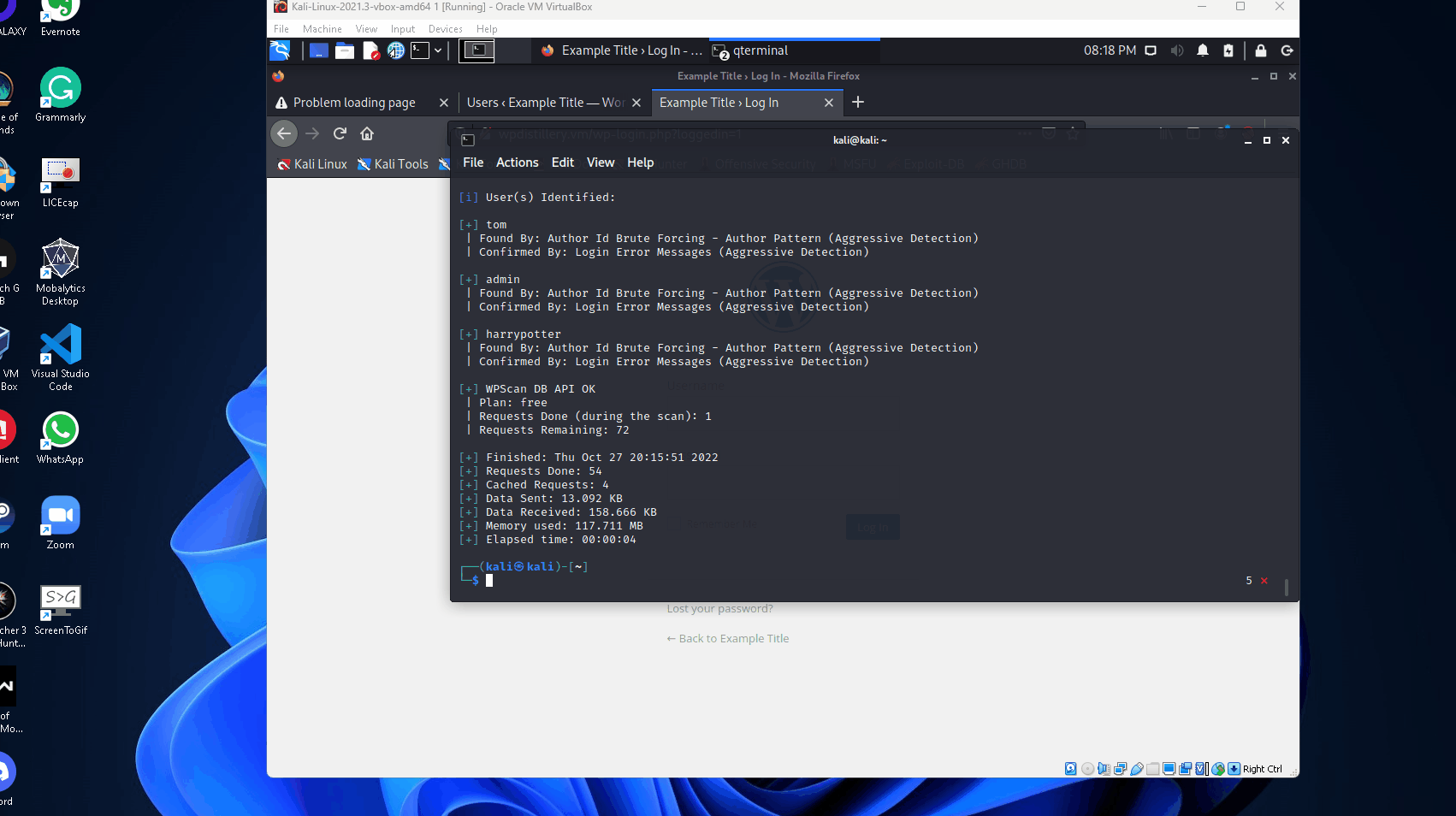
After performing the scan, I noticed that XML-RPC was left enabled for this WordPress server.

I then visited the page in question '192.168.33.10/xmlrcp.php' to which it responded with: " XML-RCP Server accepts POST request only"

From there I loaded up Burp Suite and sent the GET request to Repeater and changed the request method to POST.
Upon submitting the POST request I was fed the following response:
XML can be inserted into the POST request as seen below.

The following request revealed all available services on the server:

After some trial and error with some services, I noticed that wp.getUserBlogs could be fed username and password parameters that could be exploited for user authentication. There were no time-outs despite the number of login attempts made.
The GIF below demonstrates how XML-RPC can be exploited to obtain user credentials. Admin credentials are confirmed by the (user) as isAdmin and the boolean check is set to 1.
Sources used for exploits:
WPScan
http://codex.wordpress.org/XML-RPC_Pingback_API
https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
External:
https://codex.wordpress.org/XML-RPC/system.listMethods#Availability
https://www.javatpoint.com/xml-example


