-
Notifications
You must be signed in to change notification settings - Fork 173
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
chore: add ut and docs for sidecar injector (#1035)
* chore: add ut and docs for sidecar injector Signed-off-by: seeflood <zhou.qunli@foxmail.com> * chore: add ut and docs for sidecar injector Signed-off-by: seeflood <zhou.qunli@foxmail.com> * chore: add ut and docs for sidecar injector Signed-off-by: seeflood <zhou.qunli@foxmail.com> * chore: add ut and docs for sidecar injector Signed-off-by: seeflood <zhou.qunli@foxmail.com> * chore: add ut and docs for sidecar injector Signed-off-by: seeflood <zhou.qunli@foxmail.com> * chore: add ut and docs for sidecar injector Signed-off-by: seeflood <zhou.qunli@foxmail.com> * fix: CI errors * fix: CI errors --------- Signed-off-by: seeflood <zhou.qunli@foxmail.com>
- Loading branch information
Showing
8 changed files
with
292 additions
and
2 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,66 @@ | ||
| # Layotto sidecar injector | ||
| Sidecar injector can inject the Layotto sidecar to your pods automatically. | ||
|
|
||
| ## Prerequisites | ||
| This Layotto state SDK client demo requires you to have the following installed on your machine: | ||
|
|
||
| - [kubectl](https://kubernetes.io/docs/tasks/tools/) | ||
| - A Kubernetes cluster, such as [Minikube](https://minikube.sigs.k8s.io/docs/start/), [Kind](https://kind.sigs.k8s.io/docs/user/quick-start/) | ||
| - [Helm v3](https://helm.sh/docs/intro/install/) | ||
|
|
||
| Remember to change your current directory to `${project_path}/demo/state/k8s`. | ||
|
|
||
| ## Step 1 - Setup Layotto sidecar injector on your Kubernetes cluster | ||
| 1. Use Kind to quickly build a local Kubernetes cluster | ||
|
|
||
| ``` | ||
| kind create cluster --name layotto-cluster | ||
| kubectl config use-context kind-layotto-cluster | ||
| ``` | ||
|
|
||
| 2. Install the layotto sidecar injector chart on your cluster in the layotto-system namespace | ||
|
|
||
| ``` | ||
| helm install injector oci://docker.io/layotto/injector-helm --version v0.5.0 -n layotto-system --create-namespace --wait | ||
| ``` | ||
|
|
||
| ## Step 2 - Use Helm to deploy Redis on your Kubernetes cluster | ||
| `Redis` is an open source, advanced key-value store. It is often referred to as a data structure server since keys | ||
| can contain strings, hashes, lists, sets and sorted sets. | ||
|
|
||
| Here we use `Redis` to persist and retrieve state. | ||
|
|
||
| ``` | ||
| helm repo add bitnami https://charts.bitnami.com/bitnami | ||
| helm repo update | ||
| helm install redis bitnami/redis --set image.tag=6.2 --set auth.enabled=false | ||
| ``` | ||
|
|
||
| ## Step 3 - Deploy the layotto state client with the Layotto sidecar | ||
| 1. Create a ConfigMap named `layotto-config` and populate its data from the `config.json` file | ||
|
|
||
| ``` | ||
| kubectl create configmap layotto-config --from-file=./config.json | ||
| ``` | ||
|
|
||
| 2. Deploy Layotto state SDK client App | ||
|
|
||
| ``` | ||
| kubectl apply -f ./state-sdk-demo.yaml | ||
| ``` | ||
|
|
||
| Let's take a look at the important annotations in state-sdk-demo.yaml | ||
| - `layotto/sidecar-inject: "true"` - this tells the Layotto sidecar injector to inject a sidecar to this deployment. | ||
| - `layotto/config-volume: "layotto-config-vol` - this tells the Layotto sidecar injector which config Volume resource to | ||
| mount into layout container. | ||
|
|
||
| The `layotto-config` ConfigMap is mounted as a volume, and all contents stored in its `config.json` entry are mounted into | ||
| the layotto sidecar container at path `/runtime/configs`. The successfully mounted `config.json` file will be used as the configuration | ||
| file when Layotto starts. | ||
|
|
||
| ## View program running results | ||
| If the following information is printed, the demo succeeded: | ||
|
|
||
| 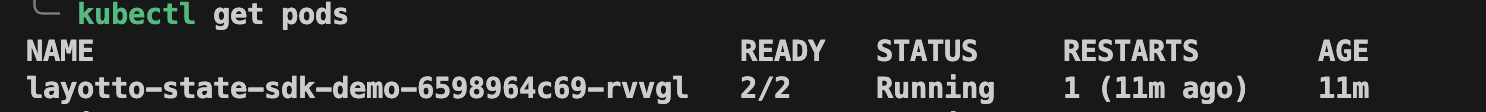 | ||
|
|
||
| 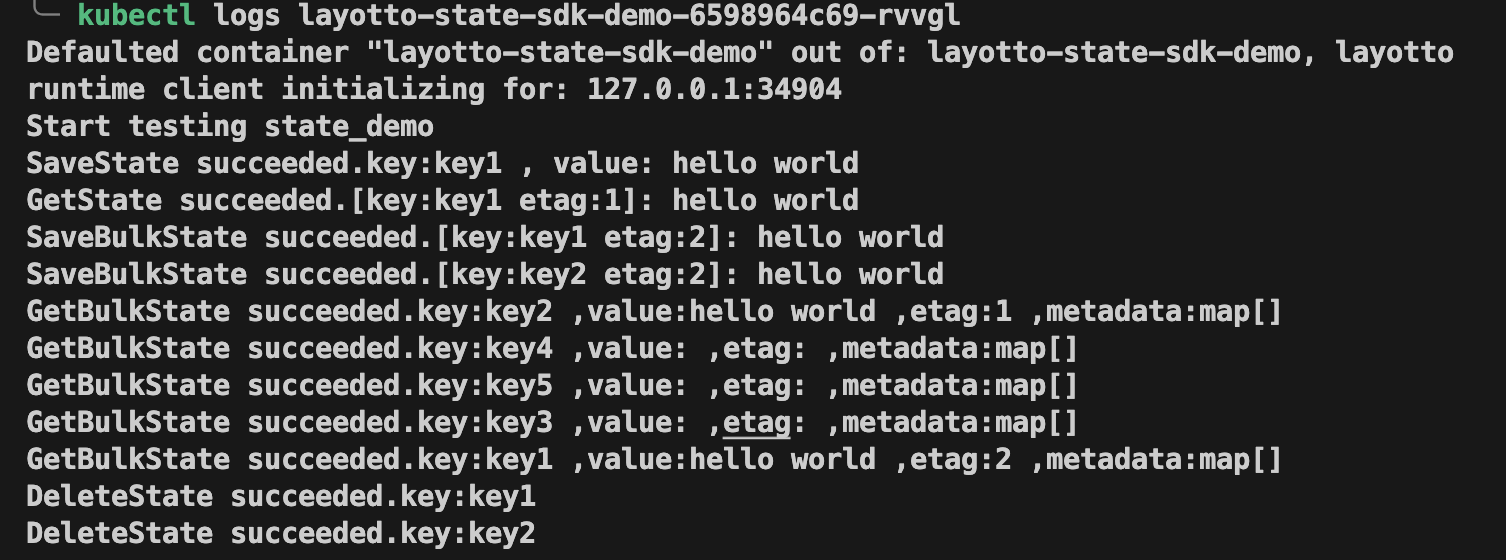 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,66 @@ | ||
| # Layotto sidecar injector | ||
| Sidecar injector can inject the Layotto sidecar to your pods automatically. | ||
|
|
||
| ## Prerequisites | ||
| This Layotto state SDK client demo requires you to have the following installed on your machine: | ||
|
|
||
| - [kubectl](https://kubernetes.io/docs/tasks/tools/) | ||
| - A Kubernetes cluster, such as [Minikube](https://minikube.sigs.k8s.io/docs/start/), [Kind](https://kind.sigs.k8s.io/docs/user/quick-start/) | ||
| - [Helm v3](https://helm.sh/docs/intro/install/) | ||
|
|
||
| Remember to change your current directory to `${project_path}/demo/state/k8s`. | ||
|
|
||
| ## Step 1 - Setup Layotto sidecar injector on your Kubernetes cluster | ||
| 1. Use Kind to quickly build a local Kubernetes cluster | ||
|
|
||
| ``` | ||
| kind create cluster --name layotto-cluster | ||
| kubectl config use-context kind-layotto-cluster | ||
| ``` | ||
|
|
||
| 2. Install the layotto sidecar injector chart on your cluster in the layotto-system namespace | ||
|
|
||
| ``` | ||
| helm install injector oci://docker.io/layotto/injector-helm --version v0.5.0 -n layotto-system --create-namespace --wait | ||
| ``` | ||
|
|
||
| ## Step 2 - Use Helm to deploy Redis on your Kubernetes cluster | ||
| `Redis` is an open source, advanced key-value store. It is often referred to as a data structure server since keys | ||
| can contain strings, hashes, lists, sets and sorted sets. | ||
|
|
||
| Here we use `Redis` to persist and retrieve state. | ||
|
|
||
| ``` | ||
| helm repo add bitnami https://charts.bitnami.com/bitnami | ||
| helm repo update | ||
| helm install redis bitnami/redis --set image.tag=6.2 --set auth.enabled=false | ||
| ``` | ||
|
|
||
| ## Step 3 - Deploy the layotto state client with the Layotto sidecar | ||
| 1. Create a ConfigMap named `layotto-config` and populate its data from the `config.json` file | ||
|
|
||
| ``` | ||
| kubectl create configmap layotto-config --from-file=./config.json | ||
| ``` | ||
|
|
||
| 2. Deploy Layotto state SDK client App | ||
|
|
||
| ``` | ||
| kubectl apply -f ./state-sdk-demo.yaml | ||
| ``` | ||
|
|
||
| Let's take a look at the important annotations in state-sdk-demo.yaml | ||
| - `layotto/sidecar-inject: "true"` - this tells the Layotto sidecar injector to inject a sidecar to this deployment. | ||
| - `layotto/config-volume: "layotto-config-vol` - this tells the Layotto sidecar injector which config Volume resource to | ||
| mount into layout container. | ||
|
|
||
| The `layotto-config` ConfigMap is mounted as a volume, and all contents stored in its `config.json` entry are mounted into | ||
| the layotto sidecar container at path `/runtime/configs`. The successfully mounted `config.json` file will be used as the configuration | ||
| file when Layotto starts. | ||
|
|
||
| ## View program running results | ||
| If the following information is printed, the demo succeeded: | ||
|
|
||
|  | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,139 @@ | ||
| // Copyright 2021 Layotto Authors | ||
| // Licensed under the Apache License, Version 2.0 (the "License"); | ||
| // you may not use this file except in compliance with the License. | ||
| // You may obtain a copy of the License at | ||
| // | ||
| // http://www.apache.org/licenses/LICENSE-2.0 | ||
| // | ||
| // Unless required by applicable law or agreed to in writing, software | ||
| // distributed under the License is distributed on an "AS IS" BASIS, | ||
| // WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. | ||
| // See the License for the specific language governing permissions and | ||
| // limitations under the License. | ||
|
|
||
| package patcher | ||
|
|
||
| import ( | ||
| "testing" | ||
|
|
||
| corev1 "k8s.io/api/core/v1" | ||
|
|
||
| injectorConsts "mosn.io/layotto/pkg/injector/consts" | ||
| ) | ||
|
|
||
| func TestInjectRequired(t *testing.T) { | ||
| t.Run("returns true when sidecar injection is enabled and pod does not contain sidecar", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| SidecarInject: true, | ||
| pod: &corev1.Pod{ | ||
| Spec: corev1.PodSpec{ | ||
| Containers: []corev1.Container{ | ||
| {Name: "not-sidecar"}, | ||
| }, | ||
| }, | ||
| }, | ||
| } | ||
|
|
||
| if !config.injectRequired() { | ||
| t.Errorf("Expected true, got false") | ||
| } | ||
| }) | ||
|
|
||
| t.Run("returns false when sidecar injection is disabled", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| SidecarInject: false, | ||
| } | ||
|
|
||
| if config.injectRequired() { | ||
| t.Errorf("Expected false, got true") | ||
| } | ||
| }) | ||
|
|
||
| t.Run("returns false when pod already contains sidecar", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| SidecarInject: true, | ||
| pod: &corev1.Pod{ | ||
| Spec: corev1.PodSpec{ | ||
| Containers: []corev1.Container{ | ||
| {Name: injectorConsts.SidecarContainerName}, | ||
| }, | ||
| }, | ||
| }, | ||
| } | ||
|
|
||
| if config.injectRequired() { | ||
| t.Errorf("Expected false, got true") | ||
| } | ||
| }) | ||
| } | ||
|
|
||
| func TestGetPatch(t *testing.T) { | ||
| t.Run("returns nil when sidecar injection is not required", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| SidecarInject: false, | ||
| } | ||
|
|
||
| patch, err := config.GetPatch() | ||
| if err != nil { | ||
| t.Errorf("Unexpected error: %v", err) | ||
| } | ||
| if patch != nil { | ||
| t.Errorf("Expected nil, got %v", patch) | ||
| } | ||
| }) | ||
|
|
||
| t.Run("returns patch when sidecar injection is required", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| SidecarInject: true, | ||
| pod: &corev1.Pod{ | ||
| Spec: corev1.PodSpec{ | ||
| Containers: []corev1.Container{ | ||
| {Name: "not-sidecar"}, | ||
| }, | ||
| }, | ||
| }, | ||
| } | ||
|
|
||
| patch, err := config.GetPatch() | ||
| if err != nil { | ||
| t.Errorf("Unexpected error: %v", err) | ||
| } | ||
| if len(patch) == 0 { | ||
| t.Errorf("Expected patch, got nil or empty") | ||
| } | ||
| }) | ||
| } | ||
|
|
||
| func TestPodContainsSidecarContainer(t *testing.T) { | ||
| t.Run("returns true when pod contains sidecar container", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| pod: &corev1.Pod{ | ||
| Spec: corev1.PodSpec{ | ||
| Containers: []corev1.Container{ | ||
| {Name: injectorConsts.SidecarContainerName}, | ||
| }, | ||
| }, | ||
| }, | ||
| } | ||
|
|
||
| if !config.podContainsSidecarContainer() { | ||
| t.Errorf("Expected true, got false") | ||
| } | ||
| }) | ||
|
|
||
| t.Run("returns false when pod does not contain sidecar container", func(t *testing.T) { | ||
| config := &SidecarConfig{ | ||
| pod: &corev1.Pod{ | ||
| Spec: corev1.PodSpec{ | ||
| Containers: []corev1.Container{ | ||
| {Name: "not-sidecar"}, | ||
| }, | ||
| }, | ||
| }, | ||
| } | ||
|
|
||
| if config.podContainsSidecarContainer() { | ||
| t.Errorf("Expected false, got true") | ||
| } | ||
| }) | ||
| } |
Oops, something went wrong.