- Docker
- Docker Compose
- Docker Content Trust (for signing images)
- Docker Scout (security scanning)
- Flask
- Ubuntu 24.04 LTS
1. Create a simple Flask web application and Dockerfile that runs as a non-root user
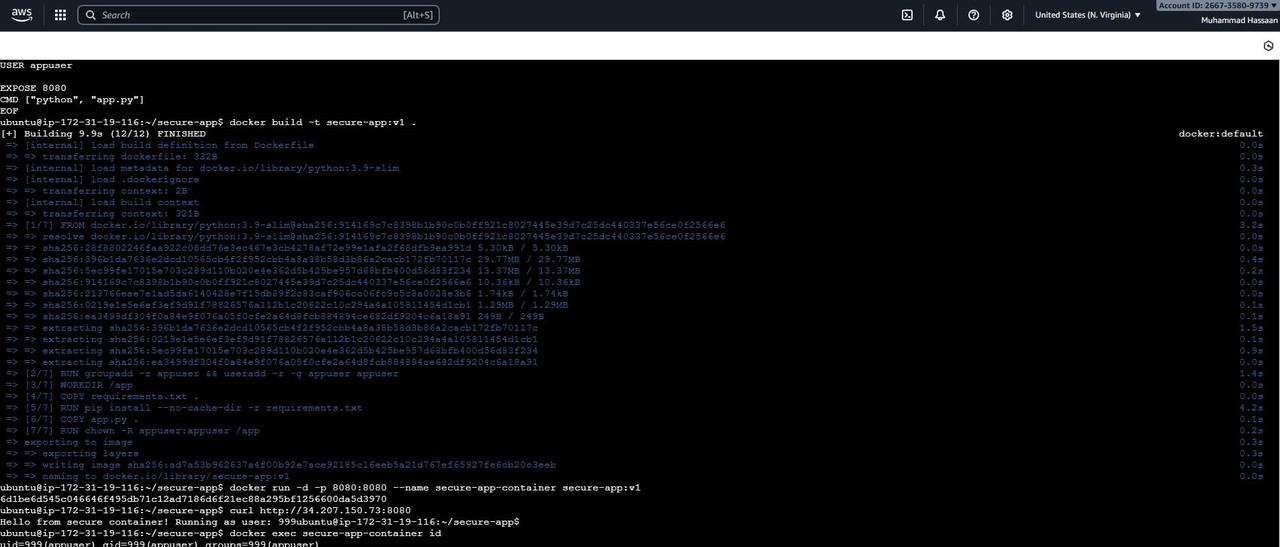
2. Enable Docker Content Trust, generate signing keys, and sign your Docker image
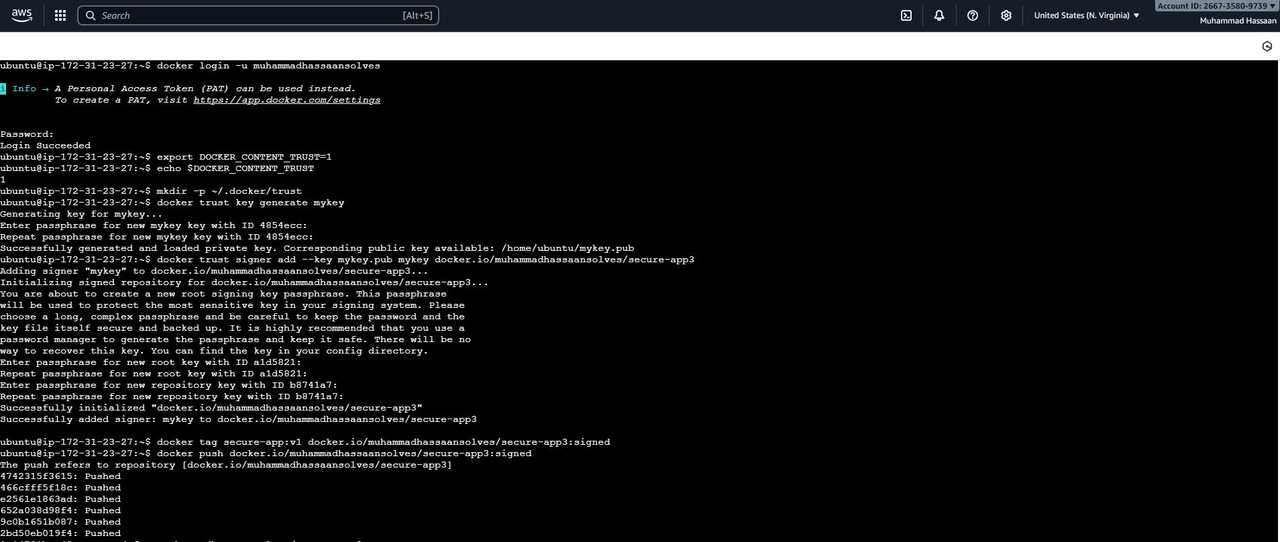
3. Scan the signed image for vulnerabilities using Docker Scout and review the results

4. Harden the container by dropping unnecessary Linux capabilities and using security options.

5. Run the container with a read-only file system, allowing writes only where needed
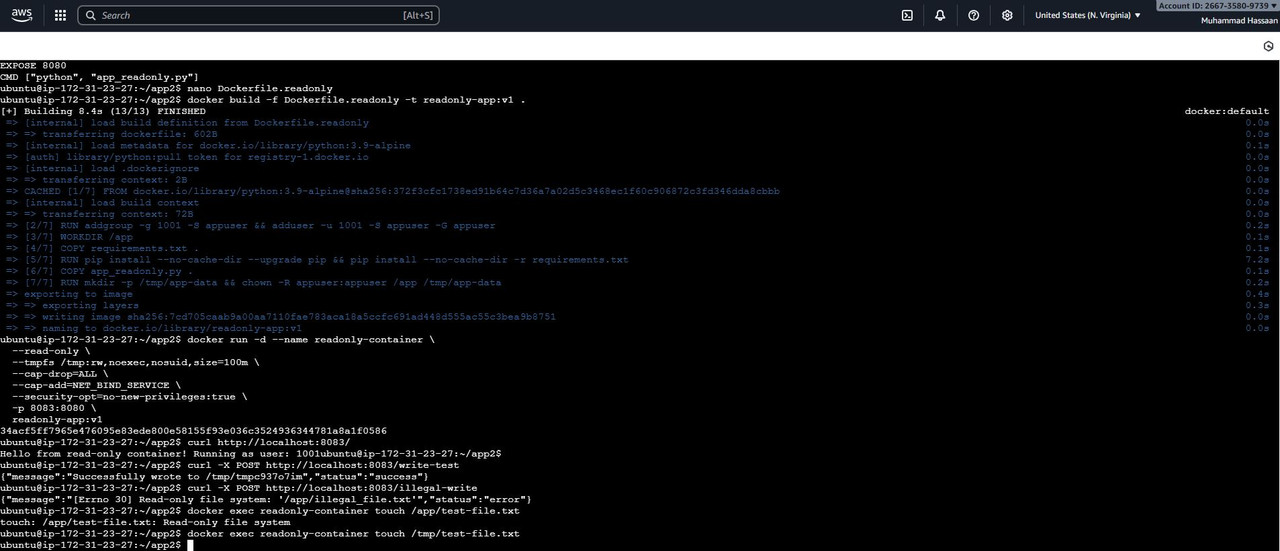
6. Deploy the secured container using Docker Compose with all security layers enabled
