A threat actor may perform unauthorized functions belonging to another user with a higher privilege level.
Clone this current repo recursively
git clone --recursive https://github.com/qeeqbox/horizontal-privilege-escalationRun the webapp using Python
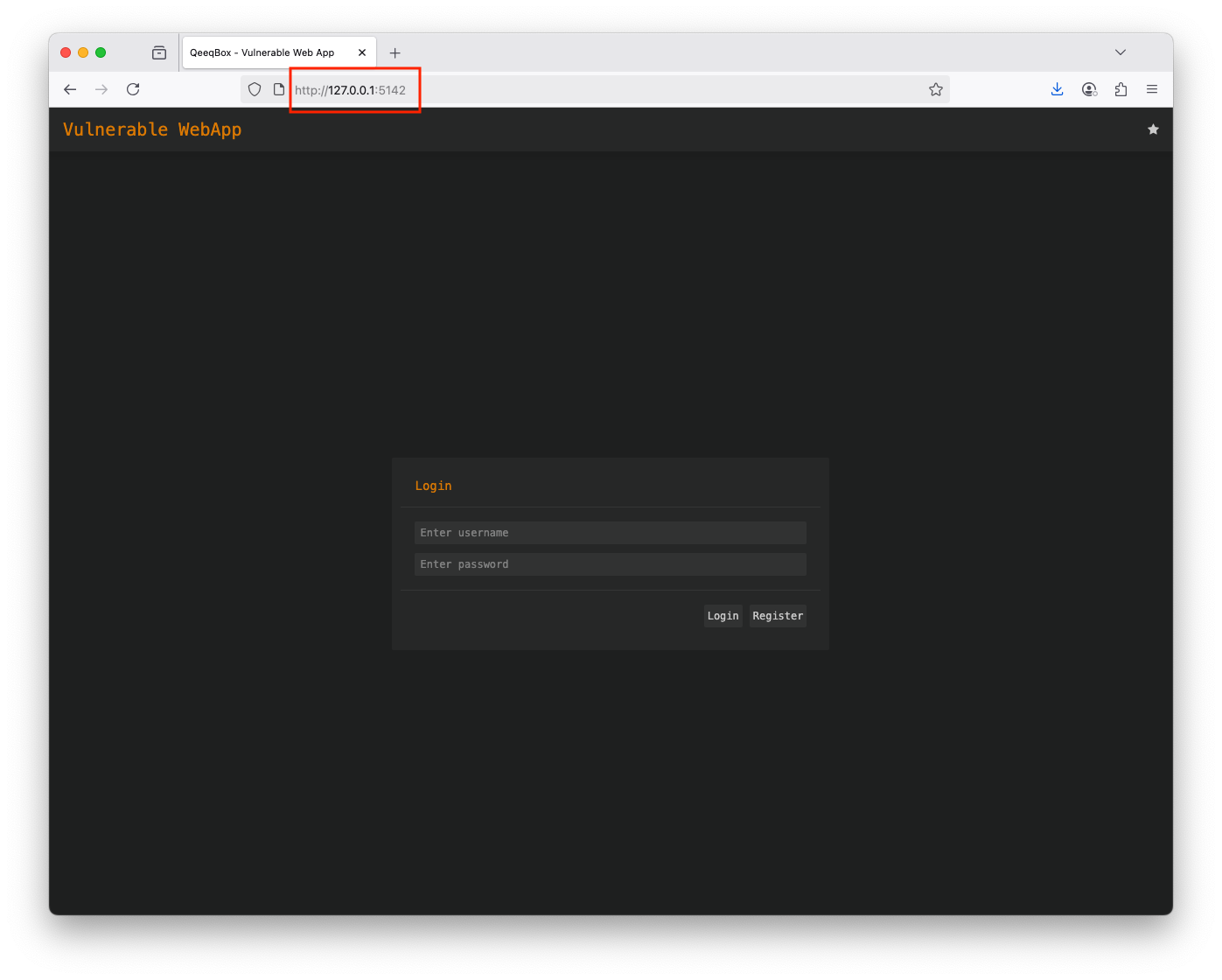
python3 horizontal-privilege-escalation/vulnerable-web-app/webapp.pyOpen the webapp in your browser 127.0.0.1:5142
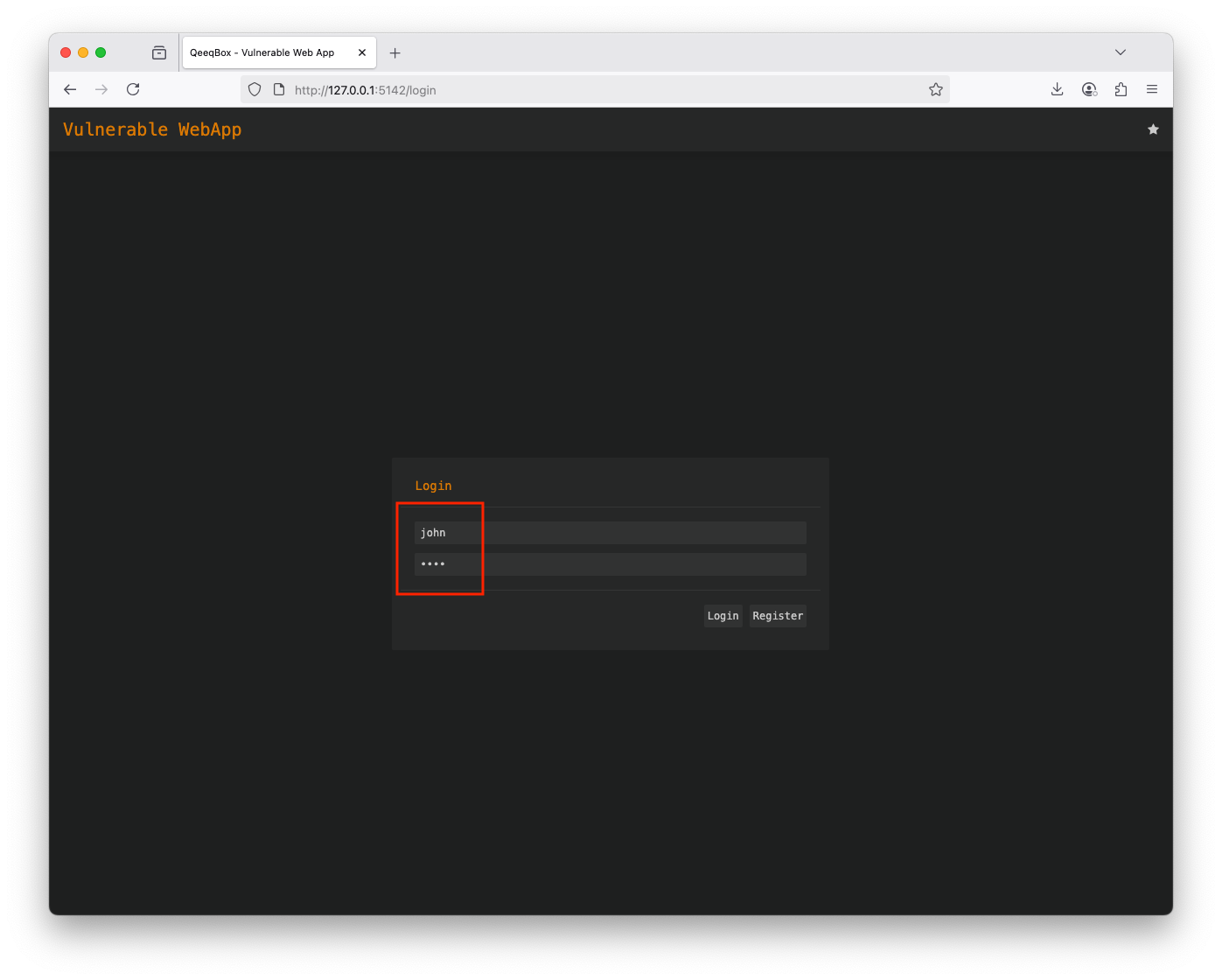
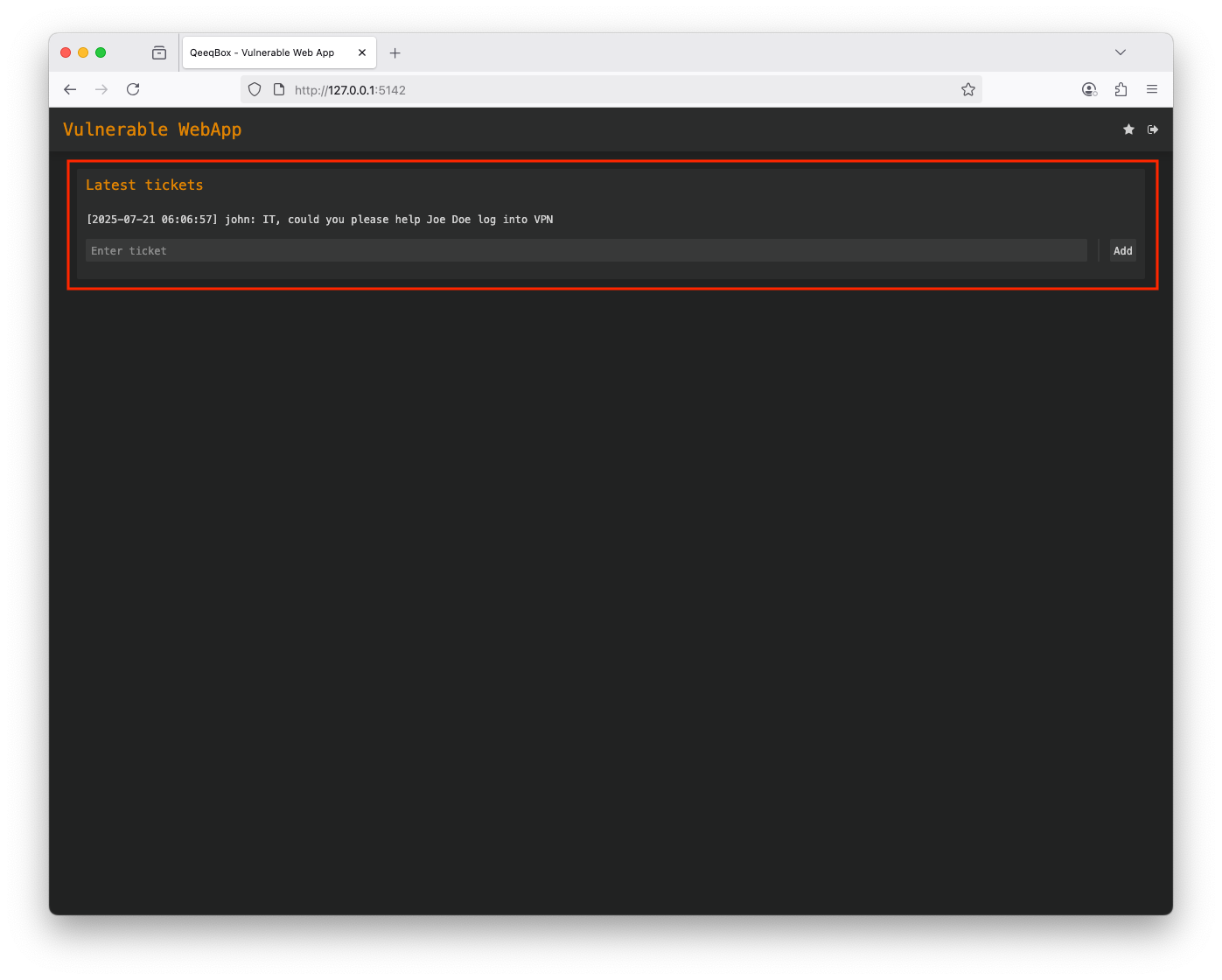
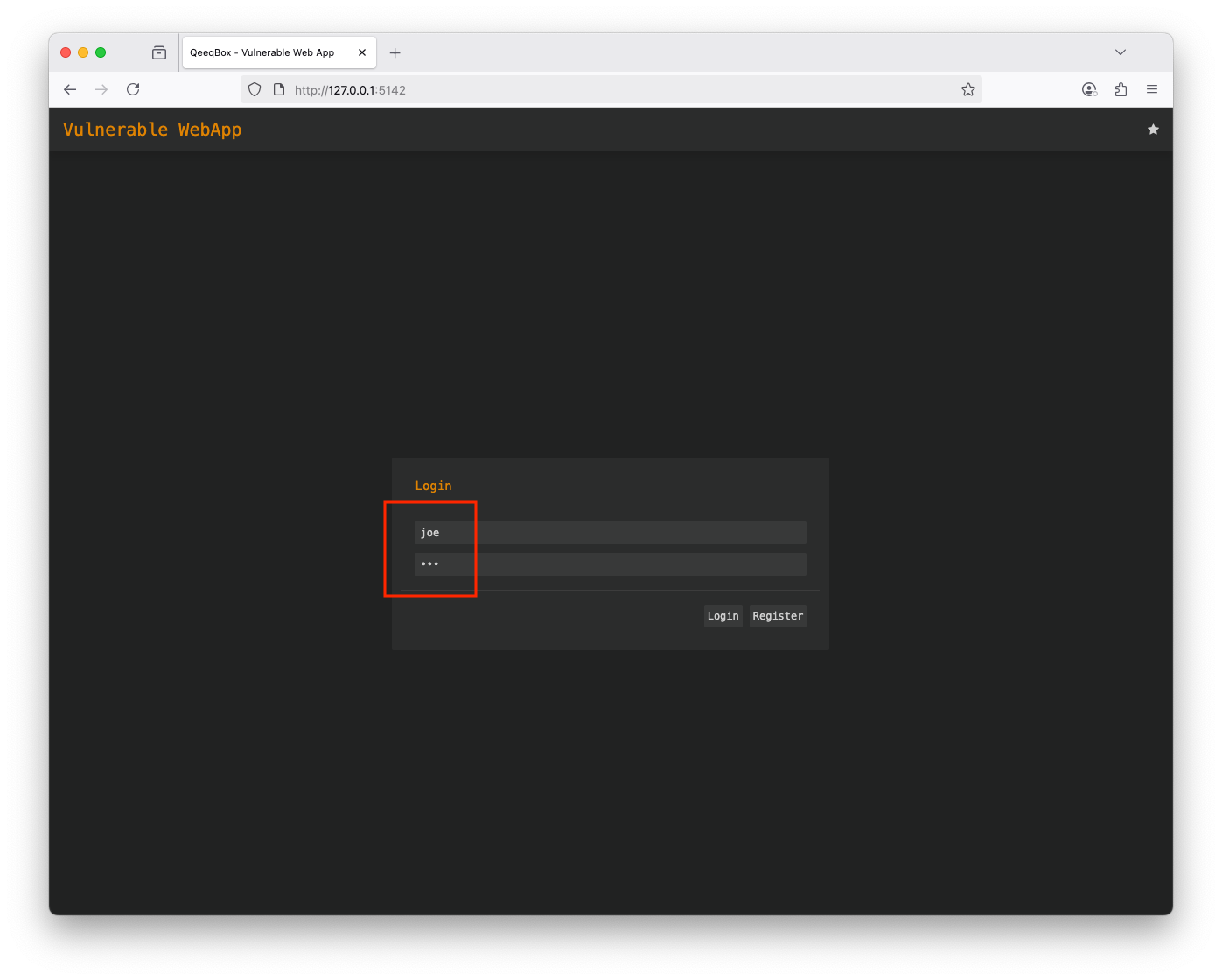
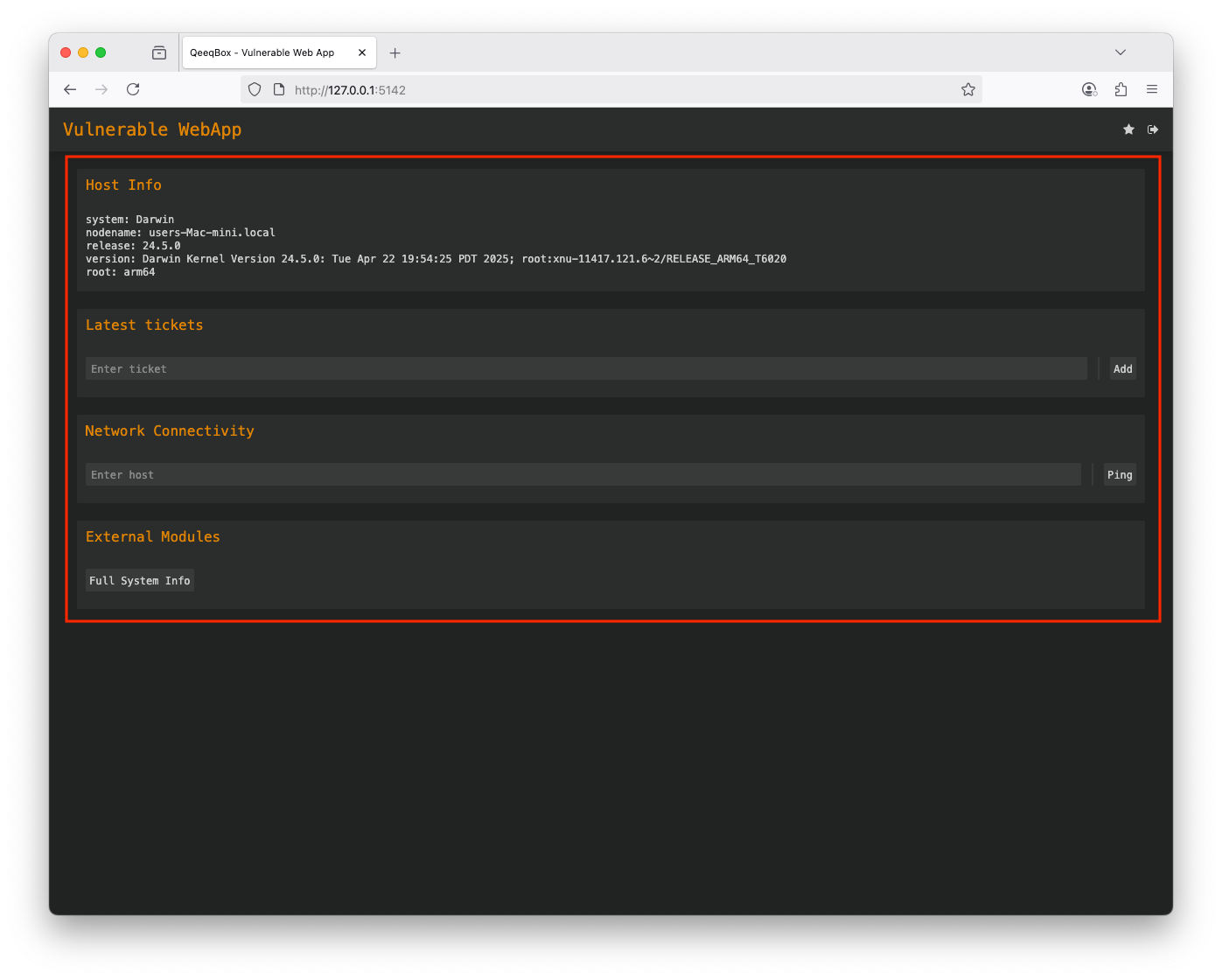
Login as John (username: john and password: john - The threat actor stole this account) John has access to the tickets only Logout Login as Joe (username: joe and password: joe - The threat actor stole this account) Joe also has access to the tickets and sysinfoThis logic checks if the user is logged in, then it renders sections based on the user's access
@logged_in
def render_home_page(self):
content = b""
cookies = SimpleCookie(self.headers.get('Cookie'))
if "access" in cookies:
for access in cookies["access"].value.split(","):
content += getattr(self, f"{access}_section" , None)()
return BASE_TEMPLATE.replace(b"{{body}}",content)Vary
- Session Hijacking
- Credential Theft
- Client input validation
- Output encoding
- Browser built-in XSS preveiton
cb251c97-067d-4f13-8195-4f918273f41b