If you are beginning your journey with Senzing, please start with Senzing Quick Start guides.
You are in the Senzing Garage where projects are "tinkered" on. Although this GitHub repository may help you understand an approach to using Senzing, it's not considered to be "production ready" and is not considered to be part of the Senzing product. Heck, it may not even be appropriate for your application of Senzing!
An AWS Lambda Python program for checking a token for authentication.
The instructions show how to generate a package that is loaded onto AWS S3 and used by https://github.com/senzing-garage/aws-cloudformation-ecs-poc-simple AWS Cloudformation.
- Preamble
- Related artifacts
- Architecture
- Demonstrate using Command Line Interface
- Demonstrate using Docker
- Develop
- Advanced
- Errors
- References
At Senzing, we strive to create GitHub documentation in a "don't make me think" style. For the most part, instructions are copy and paste. Whenever thinking is needed, it's marked with a "thinking" icon 🤔. Whenever customization is needed, it's marked with a "pencil" icon ✏️. If the instructions are not clear, please let us know by opening a new Documentation issue describing where we can improve. Now on with the show...
- 🤔 - A "thinker" icon means that a little extra thinking may be required. Perhaps there are some choices to be made. Perhaps it's an optional step.
- ✏️ - A "pencil" icon means that the instructions may need modification before performing.
⚠️ - A "warning" icon means that something tricky is happening, so pay attention.
- https://github.com/senzing-garage/aws-cloudformation-ecs-poc-simple AWS Cloudformation
The following is an architecture showcasing how the websocket API gateway interacts with the aws lambda cognito authorizer.
- Visit the AWS Console for API Gateway.
- On the left hand navigation bar, choose the APIs tab.
- Click on a Websocket API Gateway that you want to attach a Cognito Authorizer.
- On the bottom left hand navigation bar, choose the Authorizers tab.
- Click on the "Create New Authorizer" button.
- In the "Create Authorizer" pane:
- Set the Authorizer name.
- Set the Lambda Function to the Cognito Authorizer.
- Set Identity Sources to the request parameters used for authorization. In the example below, we used the request parameter token.
- Once done, click on the "create" button.
- On the bottom left hand navigation bar, choose the Routes tab.
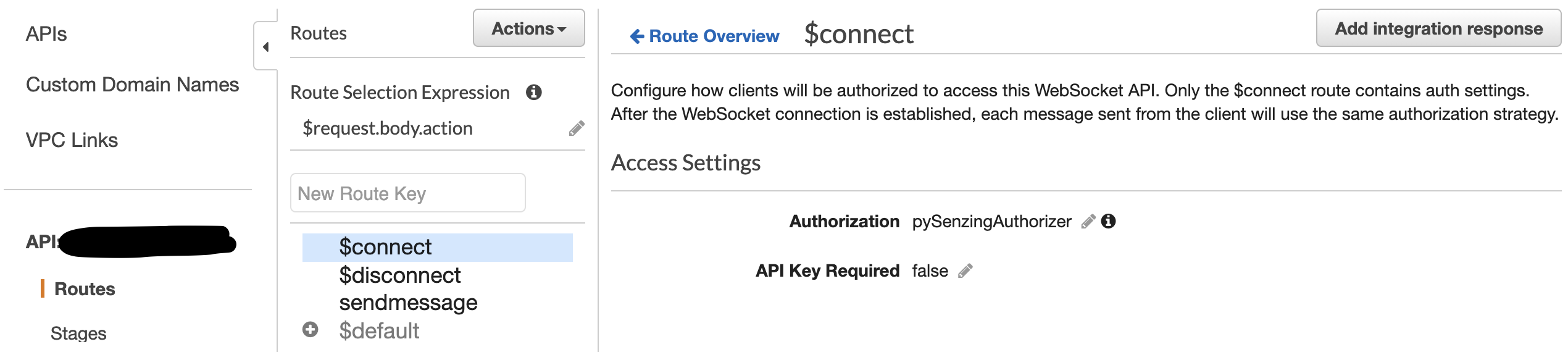
- In the Routes pane, choose the $connect route.
- In the $connect pane, click on Route Request.
- Change the authorization to the cognito authorizer lambda function.
- Click on Route Overview and if it looks like the example below, you have successfully added the cognito authorizer to your Websocket API gateway.
🤔 The following tasks need to be complete before proceeding. These are "one-time tasks" which may already have been completed.
- Install Python dependencies:
- See requirements.txt for list
-
Get a local copy of cognito_authorizer.py. Example:
-
✏️ Specify where to download file. Example:
export SENZING_DOWNLOAD_FILE=~/cognito_authorizer.py -
Download file. Example:
curl -X GET \ --output ${SENZING_DOWNLOAD_FILE} \ https://raw.githubusercontent.com/Senzing/aws-lambda-cognito-authorizer/main/cognito_authorizer.py
-
Make file executable. Example:
chmod +x ${SENZING_DOWNLOAD_FILE}
-
-
🤔 Alternative: The entire git repository can be downloaded by following instructions at Clone repository
-
Run the command. Example:
${SENZING_DOWNLOAD_FILE}
🤔 The following tasks need to be complete before proceeding. These are "one-time tasks" which may already have been completed.
- The following software programs need to be installed:
-
Run Docker container. Example:
docker run \ --interactive \ --rm \ --tty \ senzing/cognito-authorizer
Note: Because this is built to run in an AWS Lambda environment, errors will be seen when running outside of that environment.
The following instructions are used when modifying and building the Docker image.
🤔 The following tasks need to be complete before proceeding. These are "one-time tasks" which may already have been completed.
For more information on environment variables, see Environment Variables.
-
Set these environment variable values:
export GIT_ACCOUNT=senzing export GIT_REPOSITORY=aws-lambda-cognito-authorizer export GIT_ACCOUNT_DIR=~/${GIT_ACCOUNT}.git export GIT_REPOSITORY_DIR="${GIT_ACCOUNT_DIR}/${GIT_REPOSITORY}"
-
Using the environment variables values just set, follow steps in clone-repository to install the Git repository.
Since the Docker image is based on public.ecr.aws/lambda/python:3.8,
logging into AWS Elastic Container Registry (ECR) is required.
-
Set AWS environment variables. Example:
export AWS_ACCESS_KEY_ID=$(jq --raw-output ".Credentials.AccessKeyId" ~/aws-sts-get-session-token.json) export AWS_SECRET_ACCESS_KEY=$(jq --raw-output ".Credentials.SecretAccessKey" ~/aws-sts-get-session-token.json) export AWS_SESSION_TOKEN=$(jq --raw-output ".Credentials.SessionToken" ~/aws-sts-get-session-token.json) export AWS_DEFAULT_REGION=$(aws configure get default.region)
-
Login Example:
aws ecr-public get-login-password \ --region us-east-1 \ | docker login \ --username AWS \ --password-stdin public.ecr.aws/senzing
-
Option #1: Using
dockercommand and GitHub.sudo docker build \ --tag senzing/template \ https://github.com/senzing-garage/aws-lambda-cognito-authorizer.git#main
-
Option #2: Using
dockercommand and local repository.cd ${GIT_REPOSITORY_DIR} sudo docker build --tag senzing/cognito-authorizer .
-
Option #3: Using
makecommand.cd ${GIT_REPOSITORY_DIR} sudo make docker-build
Note:
sudo make docker-build-development-cachecan be used to create cached Docker layers.
-
Download the AWS Lambda Runtime Interface Emulator and make executable. Example:
mkdir -p ~/aws-lambda-rie curl -Lo ~/aws-lambda-rie/aws-lambda-rie https://github.com/aws/aws-lambda-runtime-interface-emulator/releases/latest/download/aws-lambda-rie chmod +x ~/aws-lambda-rie/aws-lambda-rie
-
Set the required environment variables
export USERPOOL_ID=<insert user pool id> export APP_CLIENT_ID=<insert app client id> export AWS_REGION=<insert aws region e.g. us-east-1>
-
Run docker container to start a service. Example:
docker run \ --entrypoint /aws-lambda/aws-lambda-rie \ --interactive \ --publish 9001:8080 \ --rm \ --tty \ --env USERPOOL_ID=${USERPOOL_ID} \ --env APP_CLIENT_ID=${APP_CLIENT_ID} \ --env AWS_REGION=${AWS_REGION} \ --volume ~/aws-lambda-rie:/aws-lambda \ senzing/cognito-authorizer \ /var/lang/bin/python -m awslambdaric cognito_authorizer.handler
-
In a separate terminal window, call the lambda. Example:
curl -v -X POST \ http://localhost:9001/2015-03-31/functions/function/invocations \ --data-binary @- << EOF { "RequestType": "Create", "ResponseURL": "", "StackId": "", "RequestId": "", "LogicalResourceId": "" } EOF
Make sure that the python3 --version used to run the pip3 install command is the same
as the python version seen in the AWS Lambda definition (i.e. the Runtime: parameter).
If not the python packages may not be the correct version.
-
Install dependencies. Example:
cd ${GIT_REPOSITORY_DIR} pip3 install \ --requirement requirements.txt \ --target ./package
-
Compress dependencies. Example:
cd ${GIT_REPOSITORY_DIR}/package zip -r ../cognito-authorizer.zip .
-
Add
cognito_authorizer.pyto compressed file. Example:cd ${GIT_REPOSITORY_DIR} zip -g cognito-authorizer.zip cognito_authorizer.py
-
Upload
cognito-authorizer.zipto AWS S3 in multiple AWS regions.
- See docs/errors.md.