Detailed information about how to use, configure and extend this module can be found on our Wiki:
The Terraform Module for Cloud Adoption Framework Enterprise-scale provides an opinionated approach for deploying and managing the core platform capabilities of Cloud Adoption Framework enterprise-scale landing zone architecture using Terraform.
Depending on selected options, this module can deploy different groups of resources as needed.
This is currently split logically into the following capabilities:
These resources can be deployed to multiple Subscriptions by setting the Provider Configuration on the module block.
The following sections outline the different resource types deployed and managed by this module, depending on the configuration options specified.
The core capability of this module deploys the foundations of the Cloud Adoption Framework enterprise-scale landing zone architecture, with a focus on the central resource hierarchy and governance:
The following resource types are deployed and managed by this module when using the core capabilities:
| Azure Resource | Terraform Resource | |
|---|---|---|
| Management Groups | Microsoft.Management/managementGroups |
azurerm_management_group |
| Management Group Subscriptions | Microsoft.Management/managementGroups/subscriptions |
azurerm_management_group |
| Policy Assignments | Microsoft.Authorization/policyAssignments |
azurerm_management_group_policy_assignment |
| Policy Definitions | Microsoft.Authorization/policyDefinitions |
azurerm_policy_definition |
| Policy Set Definitions | Microsoft.Authorization/policySetDefinitions |
azurerm_policy_set_definition |
| Role Assignments | Microsoft.Authorization/roleAssignments |
azurerm_role_assignment |
| Role Definitions | Microsoft.Authorization/roleDefinitions |
azurerm_role_definition |
The exact number of resources created depends on the module configuration, but you can expect upwards of 200 resources to be created by this module for a default installation based on the example below.
NOTE: None of these resources are deployed at the Subscription scope, however Terraform still requires a Subscription to establish an authenticated session with Azure.
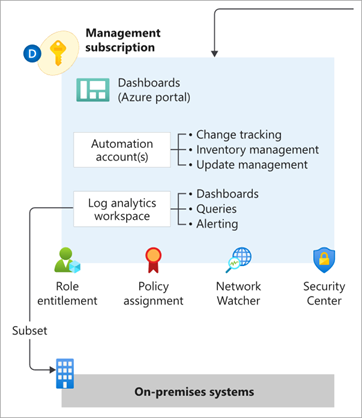
From release v0.2.0 onwards, the module includes new functionality to enable deployment of Management and monitoring resources into the current Subscription context.
This brings the benefit of being able to manage the full lifecycle of these resources using Terraform, with native integration into the corresponding Policy Assignments to ensure full policy compliance.
The following resource types are deployed and managed by this module when the Management resources capabilities are enabled:
| Azure Resource | Terraform Resource | |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Log Analytics Workspace | Microsoft.OperationalInsights/workspaces |
azurerm_log_analytics_workspace |
| Log Analytics Solutions | Microsoft.OperationsManagement/solutions |
azurerm_log_analytics_solution |
| Automation Account | Microsoft.Automation/automationAccounts |
azurerm_automation_account |
| Log Analytics Linked Service | Microsoft.OperationalInsights/workspaces /linkedServices |
azurerm_log_analytics_linked_service |
Please refer to the Deploy Management Resources page on our Wiki for more information about how to use this capability.
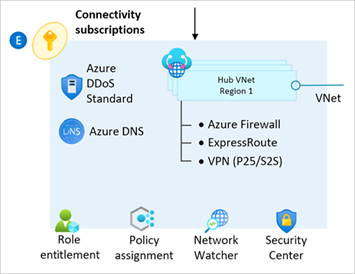
From release v0.4.0 onwards, the module includes new functionality to enable deployment of Network topology and connectivity resources into the current Subscription context.
This is currently limited to the Hub & Spoke network topology, but the addition of Virtual WAN capabilities is on our roadmap (date TBC).
NOTE: The module currently only configures the networking hub, and dependent resources for the
ConnectivitySubscription. To ensure we achieve the right balance of managing resources via Terraform vs. Azure Policy, we are still working on how best to handle the creation of spoke Virtual Networks and Virtual Network Peering. Improving this story is our next priority on the product roadmap.
The following resource types are deployed and managed by this module when the Connectivity resources capabilities are enabled:
| Azure Resource | Terraform Resource | |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Virtual Networks | Microsoft.Network/virtualNetworks |
azurerm_virtual_network |
| Subnets | Microsoft.Network/virtualNetworks/subnets |
azurerm_subnet |
| Virtual Network Gateways | Microsoft.Network/virtualNetworkGateways |
azurerm_virtual_network_gateway |
| Azure Firewalls | Microsoft.Network/azureFirewalls |
azurerm_firewall |
| Public IP Addresses | Microsoft.Network/publicIPAddresses |
azurerm_public_ip |
| DDoS Protection Plans | Microsoft.Network/ddosProtectionPlans |
azurerm_network_ddos_protection_plan |
| DNS Zones (pending) | Microsoft.Network/dnsZones |
azurerm_dns_zone |
| Virtual Network Peerings (pending) | Microsoft.Network/virtualNetworks/virtualNetworkPeerings |
azurerm_virtual_network_peering |
Please refer to the Deploy Connectivity Resources page on our Wiki for more information about how to use this capability.
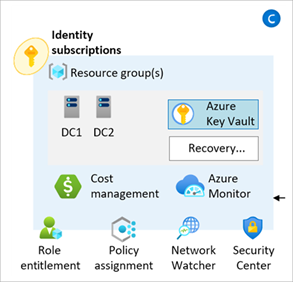
From release v0.4.0 onwards, the module includes new functionality to enable deployment of Identity and access management resources into the current Subscription context.
No additional resources are deployed by this capability, however policy settings relating to the Identity Management Group can now be easily updated via the configure_identity_resources input variable.
Please refer to the Deploy Identity Resources page on our Wiki for more information about how to use this capability.
This module has been tested using Terraform 0.15.0 and AzureRM Provider 2.77.0 as a baseline, and various versions to up the most recent at the time of release.
In some cases, individual versions of the AzureRM provider may cause errors.
If this happens, we advise upgrading to the latest version and checking our troubleshooting guide before raising an issue.
As a basic starting point, we recommend starting with the following configuration in your root module.
This will deploy the core components only.
NOTE: For production use we highly recommend using the Terraform Registry and pinning to the latest stable version, as per the example below. Pinning to the
mainbranch in GitHub will give you the latest updates quicker, but increases the likelihood of unplanned changes to your environment and unforeseen issues.
# Configure Terraform to set the required AzureRM provider
# version and features{} block.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = ">= 2.77.0"
}
}
}
provider "azurerm" {
features {}
}
# Get the current client configuration from the AzureRM provider.
# This is used to populate the root_parent_id variable with the
# current Tenant ID used as the ID for the "Tenant Root Group"
# Management Group.
data "azurerm_client_config" "core" {}
# Use variables to customize the deployment
variable "root_id" {
type = string
default = "es"
}
variable "root_name" {
type = string
default = "Enterprise-Scale"
}
# Declare the Terraform Module for Cloud Adoption Framework
# Enterprise-scale and provide a base configuration.
module "enterprise_scale" {
source = "Azure/caf-enterprise-scale/azurerm"
version = "1.1.1"
providers = {
azurerm = azurerm
azurerm.connectivity = azurerm
azurerm.management = azurerm
}
root_parent_id = data.azurerm_client_config.core.tenant_id
root_id = var.root_id
root_name = var.root_name
}For additional guidance on how to customize your deployment using the advanced configuration options for this module, please refer to our User Guide and the additional examples in our documentation.
Please refer to our Module Permissions guide on the Wiki.
For the latest examples, please refer to our Examples guide on the Wiki.
Release v1.1.1 introduces the following changes:
- Update regex logic for
root_idandscope_idinput variables onarchetypeschild module (Fixes #241) - Add
requried_versionto Terraform configuration to ensure only supported version of Terraform is used - Add documentation to Wiki for the configure_connectivity_resources and configure_management_resources input variables
No breaking changes identified.
Release v1.1.0 introduces the following changes:
- BREAKING CHANGE: Replaced
Deploy-ASC-ConfigurationPolicy Assignment withDeploy-ASCDF-Config, utilizing built-in policies and also adds support for Microsoft Defender for open-source relational databases.- Fixing Add Defender support for Open-source relational databases #131.
- Note: Will result in loss of policy compliance history.
- Consider making a copy of the removed policy templates to a custom
libfolder and using the archetype extension capability if you wish to retain the old Assignment to keep policy compliance history. - Requires an update to the
configure_management_resourcesinput variable:
{
settings = {
# (1 unchanged element hidden)
security_center = {
# (1 unchanged element hidden)
config = {
# (7 unchanged elements hidden)
enable_defender_for_oss_databases = true
# (4 unchanged elements hidden)
}
}
}
# (3 unchanged elements hidden)
}- Updates to Wiki documentation
- Multiple bug fixes covering:
- Fix "managed parameters" for
Enable-DDoS-VNETPolicy Assignment atlanding-zonesscope (no issue logged) - Changing root_parent_id results in Management Groups not being deployed #190
- Bug Report: Private DNS zone link in setting.connectivity.tf #204
- Incorrect enforcementMode setting on Enable-DDoS-VNET Policy Assignment #216
- Fix "managed parameters" for
For upgrade guides from previous versions, please refer to the following links: