- You need to create a new Okta developer acount
- Once you have a developer acount, log into it and above the Okta logo on the top left corner you should see
< > Developer Console, hover over it and you should be able to see Classic UI. Switch to Classic UI. - Once in classic UI go to applications and add applications -> create new application.
- Select the following
- Name your app
- SAML options
- Replace the sso/recipient/destination URL with the url for your app
- Once your app is setup go to sign on page and read the instructions. Click the button to view setup instructions
- You need all the info in the setup instructions,
- Identity Provider Single Sign-On URL, x.509 certificate, idp issuer.
- Set the IDP SSO URL from step 9 to SAML_ENTRY_POINT in your .env
npm installnpm start- If your app is running on localhost this process won't work, try tunneling using ngrok or localtunnel that should be the url to use in step 6.
-
XML based
-
SP - Service Provider (the app)
-
IDP - Identity Provider (entity providing the identities. Eg: Okta)
-
SAML request/Authentication Request (request made by SP to IDP to request authentication)
-
SAML response/assertion - generated by IDP, contains actual assertion of the authenticated user. May contain additional information.
-
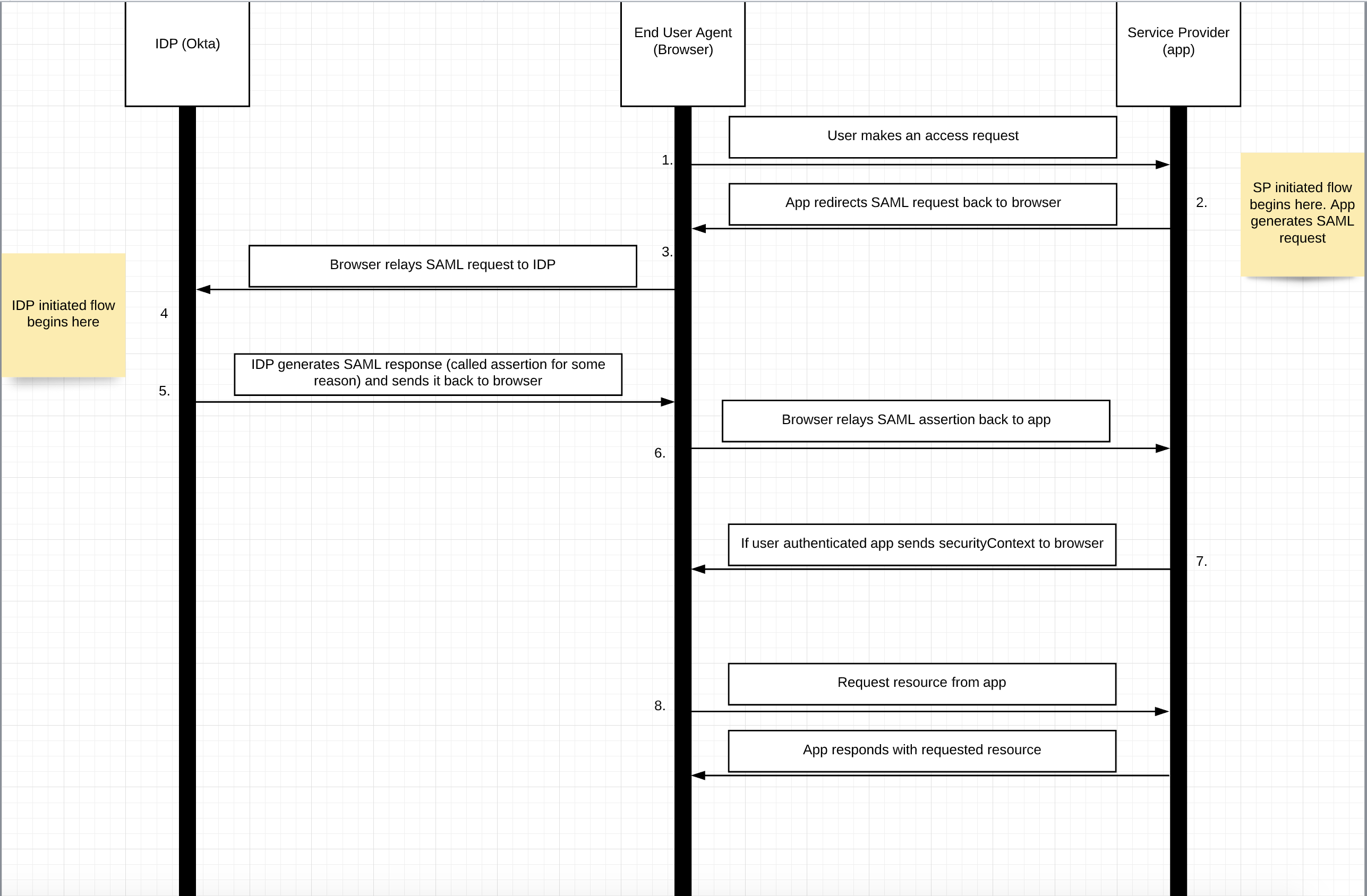
SP never directly interacts with IDP
-
SP needs to know which IDP to redirect to before it knows who the user is
-
SP does not know who the user is until SAML assertion comes back from the IDP
-
SAML authentication flow is asynchronous, no state maintained by IDP
-
In order to know that the assertion came from a valid IDP the app needs
-
Certificate: Get a public certificate from IDP to validate the signature. Store certificate server side.
-
ACS endpoint - Assertion consumer service URL - app login URL - this is where the saml responses will be posted. Need to provide to IDP (step 6 in the diagram below).
-
IDP login URL - This is the endpoint on the IDP side where SAML requests are posted (step 4 in the diagram below).
-
User tries to log on > app generates SAML request then sends to browser for deep links set RelayState value to redirect